- Introduction to Blockchain Security
- Core Principles of Blockchain Security
- Cryptography in Blockchain
- Consensus Mechanisms and Security Implications
- Smart Contract Vulnerabilities
- Real-World Blockchain Attacks
- Emerging Solutions and Best Practices
- Future of Blockchain Security
Introduction to Blockchain Security
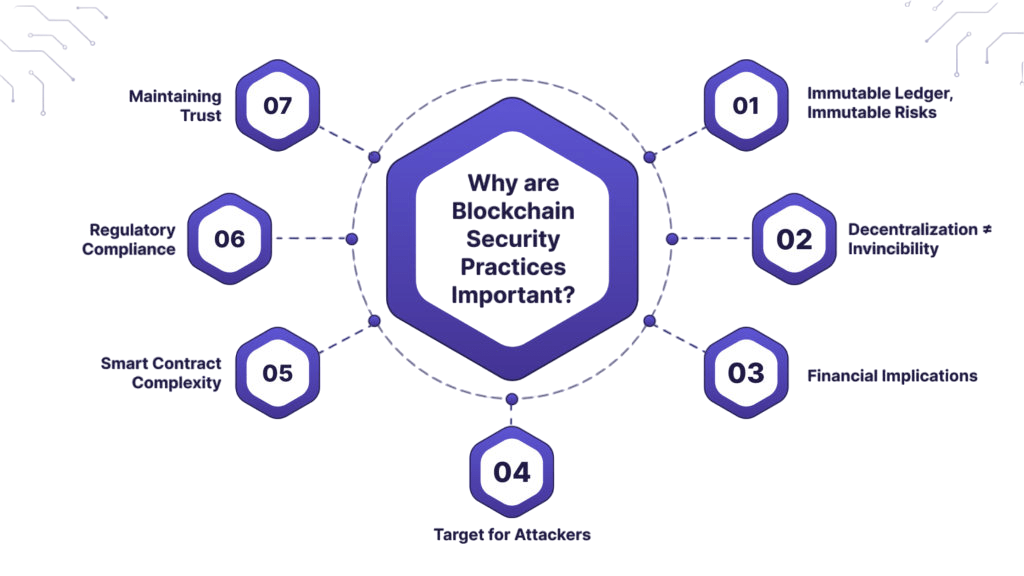
Blockchain and information security has emerged as one of the most groundbreaking innovations in the past decade. Initially designed as the underlying architecture for Bitcoin, blockchain has since expanded its reach into finance, supply chain, healthcare, governance, and more. At the heart of blockchain’s promise lies its security capabilities. Yet, as with any technology, it is not immune to vulnerabilities and attacks. This blog delves deep into the landscape of blockchain security technology, exploring its foundational principles, common threats, real-world attacks, and forward-looking defense mechanisms.
Are You Interested in Learning More About Database? Sign Up For Our Database Online Training Today!
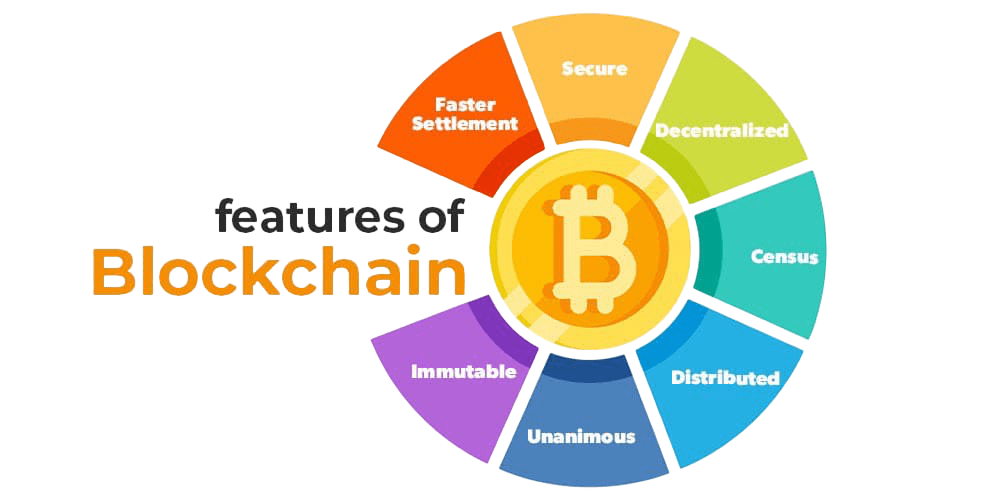
Core Principles of Blockchain Security
The blockchain security explained systems hinges on several key principles:
- Decentralization: Unlike centralized systems, blockchain distributes data across a network of nodes, reducing the risk of a single point of failure.
- Immutability: Once recorded, data on the blockchain cannot be altered retroactively, preventing unauthorized modifications.
- Transparency: Transactions are visible to all participants, fostering trust and accountability.
- Consensus: Blockchain relies on consensus mechanisms to validate and agree on the state of the ledger, ensuring that only legitimate transactions are recorded.
- Pseudonymity: While blockchain offers transparency, it also allows users to interact using public keys rather than revealing personal identities.
Together, these principles create a robust framework for secure digital interactions. However, implementation details and operational practices significantly influence actual blockchain and information security outcomes.
Cryptography in Blockchain
Cryptography is fundamental to blockchain security technology. It underpins data integrity, authentication, and confidentiality. Two main cryptographic techniques are commonly used:
- Hash Functions: These algorithms take an input and produce a fixed-size string of bytes. Popular hash functions like SHA-256 are used to link blocks securely.
- Public-Key Cryptography: This technique enables secure transactions. Each user has a pair of keys: a public key shared with others and a private key kept secret. Digital signatures created using private keys verify the authenticity of transactions.
Advanced cryptographic methods, such as zero-knowledge proofs, are now being explored to enhance privacy and scalability in blockchains.
To Explore Database in Depth, Check Out Our Comprehensive Database Online Training To Gain Insights From Our Experts!
Consensus Mechanisms and Their Security Implications
Consensus mechanisms determine how nodes in a blockchain network agree on the validity of transactions. Different mechanisms offer varying levels of blockchain and information security. Bitcoin’s Proof of Work (PoW) system requires miners to solve challenging mathematical puzzles in order to validate transactions. Despite being secure, this approach uses a lot of energy and is susceptible to 51% attacks. On the other hand, validators are chosen by Proof of Stake (PoS) according to how many tokens they possess and are prepared to stake. Although this method uses less energy, it may raise issues with reduced decentralization and wealth concentration. There are additional options, such as variations of Delegated Proof of Stake (DPoS) and Byzantine Fault Tolerance (BFT), each of which offers a unique trade-off between scalability, decentralization, and attack resistance. Understanding the security strengths and weaknesses of each consensus model is crucial for building resilient blockchain systems.Smart Contract Vulnerabilities
Smart contracts automate transactions and agreements on the blockchain security explained. However, they are only as secure as their code. Common vulnerabilities include: Criminals use reentrancy attacks to take advantage of smart contracts by repeatedly calling a function before the previous execution is complete. In the well-known DAO hack, this vulnerability was exploited. Integer overflow or underflow is another frequent problem, where arithmetic operations cause unexpected behavior by going over or under the variable limits. An additional risk is posed by unprotected functions, which an attacker could use to alter contract behavior if they don’t have adequate access control. Last but not least, contracts with loops that use excessive amounts of gas may go over the gas limit, which could result in transactions failing or getting stuck. Smart contract blockchain and information security demands rigorous code audits, formal verification, and safe development practices.
Several high-profile attacks have exposed weaknesses in blockchain security explained: These incidents highlight the importance of continuous monitoring, community vigilance, and evolving security practices. To bolster blockchain security technology, developers and researchers are exploring several innovative approaches: Community education and developer tools are also critical to ensuring secure blockchain ecosystems. Want to Learn About Database? Explore Our Database Interview Questions and Answers Featuring the Most Frequently Asked Questions in Job Interviews. The future of blockchain security will likely be shaped by several trends: In conclusion, while blockchain security explained offers powerful security advantages, it is not a panacea. Continuous innovation, vigilance, and collaboration across the ecosystem are essential to address emerging threats and unlock the full potential of decentralized technologies.Real-World Blockchain Attacks
Emerging Solutions and Best Practices
Future of Blockchain Security