
- What does the term “cipher” mean?
- What is the operation of a Cipher Encryption?
- Cybersecurity encryption
- What Are Ciphers Used for?
- Cipher Types
- Cipher Examples
- Conclusion
Generally, cyphers are labelled consistent with how they are characteristic and the way their key’s used for encryption and decryption. While circulation cyphers rent a regular circulation of symbols, block cyphers organization symbols right into a fixed-length message (the block). When the usage of a symmetric key method or cypher, each asymmetric encryption and decryption uses the equal key; asymmetric key algorithms or SSL cyphers use an awesome key for double encryption and decryption in Database Security .
To learn about different Cybersecurity techniques, sign up for our Cyber Security Online Training right now!
What does the term “cipher” mean?
Cipher is an often-used set of rules in cryptology, a topic concerning the look at of cryptographic algorithms. It is a way of encrypting and decrypting statistics. The adoption of a symmetrical cypher will decide the name of the game or symmetric key Cyber Security Training Courses . The symmetric set of rules applies the equal double encryption key and cypher to the statistics inside the equal way. Symmetric cyphers are the muse of symmetric key encryption, extensively known as mystery key encryption. The intention is to convert simple textual content to ciphertext or vice versa. By reworking plaintext letters or different facts into ciphertext, cyphers remodel statistics. It is exceptional to specify the ciphertext as random facts. The additive cipher the authentic and plaintext statistics to generate ciphertext that appears to be random statistics. The equal asymmetric encryption secrets carried out to statistics, inside the equal way, the usage of symmetric asymmetric encryption methods, whether or not the intention is to transform plaintext to ciphertext or ciphertext to plaintext.
What is the operation of a Cipher Encryption
- Symmetric cyphers utilize a Web Application Security encryption method to transform plaintext, which is a legible communication, into ciphertext, which appears to be a random string of letters.
- Cyphers are now and again known as circulation additive cyphers because they encrypt or decode bits in a circulation.
- They might also employ block symmetric cyphers, which process ciphertext in consistent blocks of a fixed number of bits.
- Present-day cypher implementations utilize the present-day cypher implementations using a key to adjust information whilst iwhileles encrypted.
- Longer keys (measured in bits) make ssl ciphers greater resilient towards brute-pressure assaults.
- The greater brute-pressure assaults that should be used to discover the plaintext, the longer the key.
- Although the key duration isn’t continually correlated with cypher strength, specialists advocate that present-day cyphers be constructed with keys of at least 128 bits or greater, relying on the set of rules and use case.
- In real-international additive cipher, the kkey is stored secret instead of the approach because a key is a key aspect of a Cyber Security Training procedure.
- Strong asymmetric encryption strategies are designed so that, even though a person is acquainted with the procedure, decoding the ciphertext without the specified key ought to be challenging.
- This approach states that in order for a cypher to work, both the sender and the receiver want to own a key or set of keys.
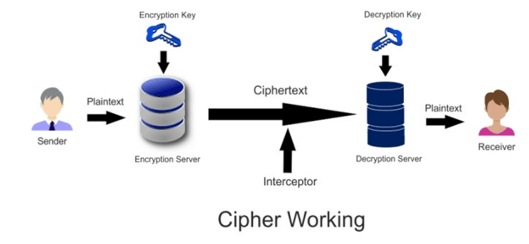
Cybersecurity encryption
In cybersecurity encryption, the equal key encrypts and decrypts statistics; at the same time as in uneven asymmetric encryption, keys (a public and a non-public key) are used, improving cybersecurity encryption. Cyphers can function by substituting characters with others or by rearranging them in step with a selected system. For example, substitution symmetric cyphers update characters with specific ones primarily based totally on a hard and fast pattern, at the same time as transposition SSL cyphers modify the order of characters. More complicated additive cipher, like AES or RSA, use problematic algorithms to offer robust asymmetric encryption resistant to trendy computing attacks. Once encrypted, the ciphertext may be transmitted or saved securely, and the simplest people with the appropriate key can revert it to its unique form, retaining statistics confidentiality.
Sign up for ACTE Cyber Security Online Training and get a head start in your career in cyber security.
What Are Ciphers Used for?
Cyphers are crucial equipment for securing data throughout diverse applications, making sure that touchy statistics stay exclusive and guarded against unauthorized access. They are extensively utilized in virtual communications, which include emails, on-the-spotaneous messaging, and online banking, to encrypt data earlier than it’s despatched in its networks, safeguarding it from capacity eavesdroppers. SSL cyphers additionally play a crucial function in statistics storage, shielding non-public and organizational statistics, along with economic records, clinical data, and highbrow property. In e-trade and online transactions, symmetric cyphers allow stable statistics trade with the aid of encrypting charge details, fostering consideration and protection in online interactions with double encryption.
The maximum used additive ciphers for securing net conversations are symmetric ones. They are also included in numerous facts-sharing community protocols. For example, Secure Sockets Layer and TLS use cyphers to encrypt facts on the software layer, especially while blended with HTTP Secure (HTTPS). Virtual non-public Network Topology that hyperlink faraway people or branches to company networks use protocols the usage of symmetric key strategies to steady facts transmission. Symmetric cyphers are normally utilized in Wi-Fi networks, online banking and shopping, and cellular telecellsmartphone offerings to shield the privacy of personal facts. Several protocols appoint uneven cryptography to authenticate and encrypt endpoints.The alternate of symmetric keys for the asymmetric encryption of consultation facts is also included in the usage. These requirements consist of the following:
Leverage Cyber Security to Unlock the Future! Enroll in the Cybersecurity Expert Masters Program Training Course Program at ACTE Right Away.
- HTTP
- TLS
- secure Shell
- Secure/Multipurpose Internet Mail Extensions
- Open Pretty Good Privacy
- Block cyphers: Block cyphers encrypt facts in similarly sized blocks.
- Stream cyphers: Stream cyphers may be used on facts streams, which are regularly obtained and transferred through a network.
- When applied with a 160-bit key, ECC can also additionally offer the equal degree of protection as a conventional cypher, consisting of the only used inside the RSA (Rivest-Shamir-Adleman) cryptosystem, which makes use of a 1,024-bit key.
- Advanced asymmetric encryption algorithms are intended to live to tell the tale attacks even if the culprit is aware of the cypher being hired.
- Since plaintext became manually encrypted, the use of SSL cyphers had been historically much less steady in opposition to assault, given that they can be directly inspected and damaged by the use of pc power.
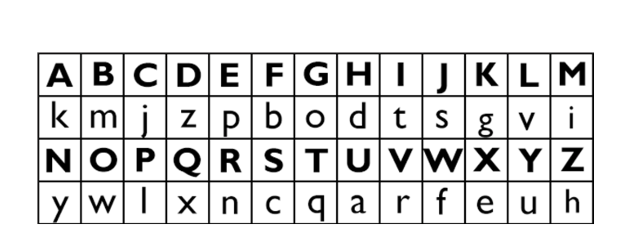
- Caesar
This cypher is a concept utilized by Julius Caesar to transit together with his people soundly. Every of the plaintext letters is moved a positive quantity of positions down the alphabet on this honest substitution cypher. Caesar is meant to have laboured 3 shifts. Substitution symmetric cyphers are regularly applied with the aid of placing down the plaintext alphabet, observed with the help of using the ciphertext alphabet, and shifted with the aid of using the quantity agreed upon with the assistance of using the ones talking through Google Dorking . A 3-letter shift locations the letter D over the plaintext A, E above B, and so on. A primary shape of a secret is the quantity of characters moved.
- Atbash
This asymmetric encryption is a replacement additive cypher that forces the alphabet of plaintext back onto itself. To position it another way, plaintext letter A is translated into ciphertext Z, plaintext letter B into ciphertext Y, plaintext letter C into ciphertext X, and so on. Atbash is known after the Hebrew alphabet’s first alphabet’s letters. It is assumed to have been used for millions of years.
- Simple substitution
This one has been used for many years as well. It replaces every plaintext letter with a brand new ciphertext individual, resulting in a 26-individual key. It varies from the Caesar cypher in that the enciphering alphabet is absolutely scrambled instead of moved to a positive quantity of positions.
- Vigenere
This Cipher makes use of many substitute alphabets and is a polyalphabetic substitution cypher, which means it’s far primarily based totally on substitution. The Vigenère asymmetric encryption makes use of a chain of interwoven symmetric cyphers, which are mainly based totally on the letters of a keyword. The supply of textual content is scrambled by the use of the Vigenère rectangular or table.
Symmetric encryption is less secure than public key cryptography but requires more computer power. For improved performance, protocols typically encrypt consultation facts using symmetric key strategies.
Cypher Types
Two picks for additive cypher are elliptical curve cryptography or traditional keys, which are immediately hired to Keylogger the ciphertext
Preparing for Cyber Security job interviews? Check out our Cyber Security Interview Questions and Answers now!
Cypher Examples
Conclusion
The Cipher is a method for encrypting communications as a result. It interprets a message with the aid of reworking the information that represents the message’s phrases and characters through the usage of the cipher algorithm. It is easy to automate and apply the cypher algorithm, and cyphers can be created fast. Ciphercypher is an important device in cryptography, remodelling readable statistics into an unreadable layout to steady records in opposition to unauthorized access in double encryption. By substituting or rearranging characters, SSL cyphers defend touchy statistics, making sure of confidentiality and privacy in virtual communications. From simple substitution techniques, just like the Caesar Cipher, to complicated contemporary-day algorithms, which include AES and RSA, cyphers play a pivotal function in each private and organizational cybersecurity encryption. The effectiveness of a cypher, in large part, relies upon the secrecy and complexity of the Cyber Security Training Courses key, making key control a critical element of records cybersecurity encryption.





