
- Introduction
- The Growing Threat Landscape
- The Impact of Cybersecurity Breaches
- The Role of Cybersecurity in Protecting Sensitive Data
- Cybersecurity Measures and Best Practices
- Cybersecurity in Different Industries
- The Evolution of Cybersecurity
- Building a Cybersecurity Culture
- Conclusion
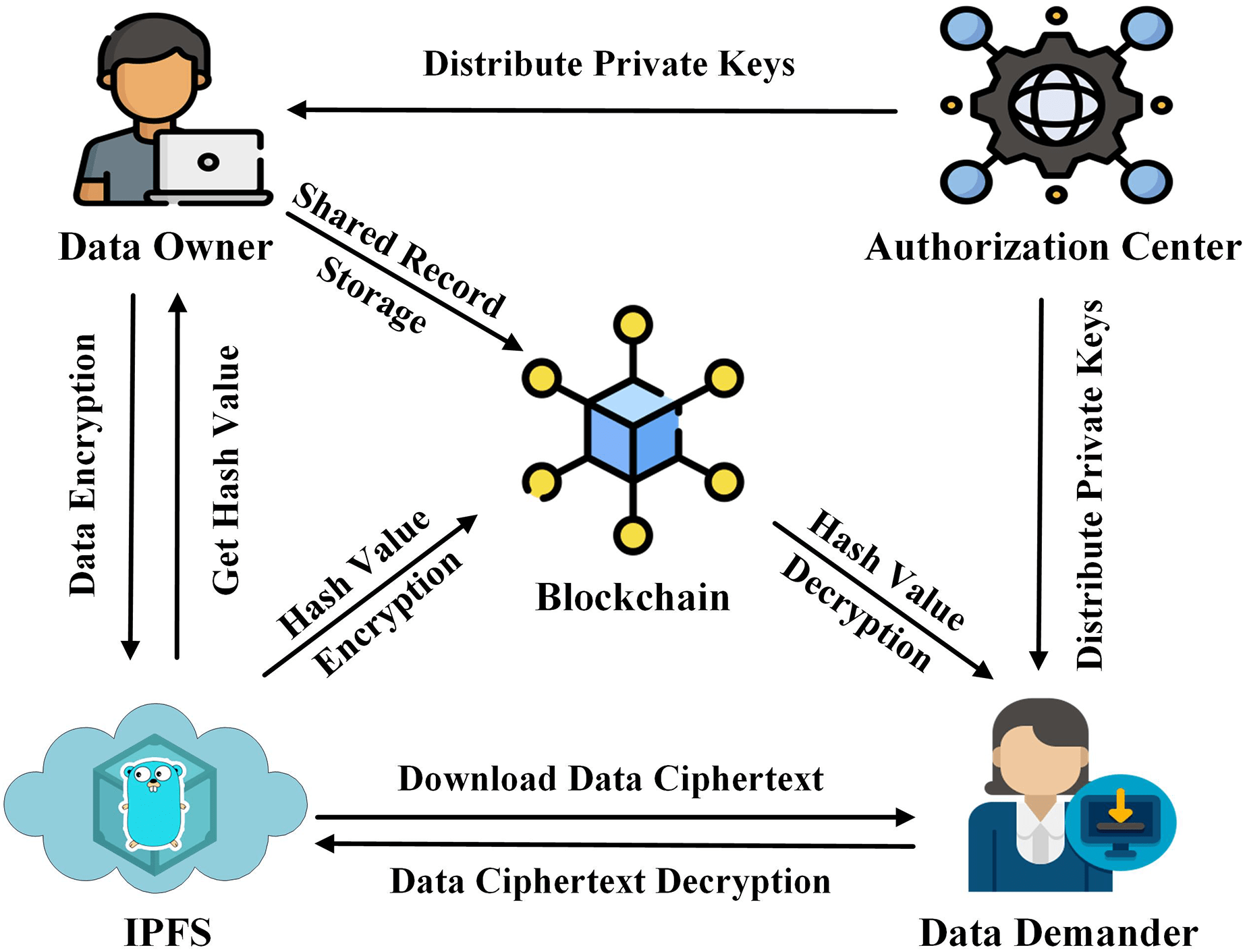
In today’s digital era, cybersecurity has become crucial as the threat landscape continues to expand with sophisticated cyberattacks. The impact of breaches can be devastating, leading to financial losses, data theft, and reputational damage. Protecting sensitive data requires strong Cybersecurity Training Courses, including encryption, firewalls, and multi-factor authentication. Various industries, from healthcare to finance, rely on tailored security strategies to safeguard critical information. Over time, cybersecurity has evolved with advanced technologies like AI-driven threat detection and zero-trust architectures. However, technical solutions alone are not enough—building a strong cybersecurity culture is essential for organizations to stay resilient. Educating employees, enforcing policies, and proactive monitoring play a key role in strengthening security. As cyber threats continue to evolve, a proactive and adaptive cybersecurity approach is necessary to mitigate risks and ensure digital safety.
Sign up for ACTE Cyber Security Online Training and get a head start in your career cyber security.
Introduction
Cybersecurity is the practice of safeguarding computer systems, networks, and data from cyber threats, including unauthorized access, attacks, and damage. In today’s digital age, where nearly every aspect of life is connected online, cybersecurity has become crucial. The goal is to protect sensitive information, ensure system reliability, and prevent malicious activities that can disrupt business operations or compromise personal data. As the Internet Security and technologies evolve, so do the methods and tactics used by cybercriminals. Every organization, from small startups to large enterprises, needs a comprehensive cybersecurity strategy to mitigate risks. With increasing reliance on digital systems, businesses must consider the importance of continuous monitoring and regular updates to defend against emerging threats. Effective cybersecurity is a proactive process requiring constant adaptation to the ever-changing landscape of digital threats.
The Growing Threat Landscape
Cybersecurity threats have grown exponentially over the years, with attackers using increasingly sophisticated methods to exploit vulnerabilities in systems. These threats include malware, phishing, ransomware, and denial-of-service (DoS) attacks, all of which can lead to significant harm. Cybercriminals can infiltrate networks, steal sensitive data, disrupt business operations, or even hold data hostage for Maze Ransomware Overview and Impact. Moreover, cyberattacks are becoming more targeted, using social engineering tactics to manipulate individuals into revealing confidential information. With the rise of remote work, there is an added layer of complexity as employees access networks from different locations, often on less secure devices. Nation-state actors are also becoming more involved in cyberattacks, engaging in espionage or attempting to destabilize governments and economies. The growing frequency of these threats makes cybersecurity more critical than ever before, as both individuals and organizations need to be constantly vigilant.
The Impact of Cybersecurity Breaches
- A cybersecurity breach can have devastating effects on businesses, individuals, and even nations.
- Financially, companies can face massive losses due to theft of funds or loss of productivity as systems are compromised.
- Breaches can also lead to hefty fines and legal consequences, especially if customer data is exposed, violating regulations like GDPR or CCPA.
- Reputational damage is another significant consequence, as customers lose trust in a company’s ability to protect their information.
- This erosion of confidence can lead to a decline in business relationships, a drop in sales, and a long-term recovery period.
- Personal impacts of breaches can include identity theft, financial fraud, and emotional distress.
- For governments, cyberattacks can undermine national security, disrupt critical infrastructure, and erode public confidence.
- The damage from such breaches often extends far beyond immediate financial losses, making robust cybersecurity practices essential for mitigation.
- To defend against cyber threats, organizations must implement a variety of cybersecurity measures.
- Firewalls act as a barrier between internal networks and external threats, blocking unauthorized access.
- Antivirus software detects and removes malicious programs that can compromise system integrity.
- Regular software updates and patches fix known vulnerabilities, making it harder for attackers to exploit outdated systems.
- Encryption secures sensitive data, both in transit and at rest, ensuring its confidentiality.
- Implementing strong password policies, such as requiring complex passwords and multi-factor authentication, significantly reduces the likelihood of unauthorized access.
- Security monitoring tools can alert administrators to suspicious activity, enabling a swift response.
- Additionally, user education and training are crucial to cybersecurity; employees should be aware of common threats like phishing and how to avoid falling victim to them.
- By combining these measures, organizations can build a solid defense against a wide range of cyberattacks.
- Cybersecurity has had to adapt continuously to keep up with rapidly evolving technology and threats.
- In the past, traditional methods such as Packet Filtering Firewall and antivirus software were sufficient for basic protection, but modern cyberattacks have become much more sophisticated.
- Emerging technologies, such as artificial intelligence (AI) and machine learning, are now used to predict and detect cyber threats in real time.
- AI can analyze vast amounts of data, identifying patterns and anomalies that may indicate a breach, allowing for quicker responses.
- Blockchain technology is also being explored for secure data storage and transaction verification, offering a tamper-resistant layer of protection.
- With the advent of quantum computing, cybersecurity is facing new challenges as quantum computers could break traditional encryption methods.
- As these technologies advance, the future of cybersecurity will likely involve even more complex, adaptive, and innovative solutions to combat increasingly sophisticated cyber threats.
Are you curious to know more about Cybersecurity ? Take advantage of our comprehensive online Cyber Security Online Training .
The Role of Cybersecurity in Protecting Sensitive Data
Sensitive data, such as personal information, financial records, and proprietary business data, is often targeted by cybercriminals. Without proper protection, this data can be exposed or stolen, leading to severe consequences. Cybersecurity ensures that such information remains confidential and is only accessible to authorized individuals. Encryption plays a vital role in protecting data during transmission or storage, ensuring that even if data is intercepted, it remains unreadable to unauthorized parties. Secure storage methods, such as utilizing encrypted Database Security, also reduce the risk of data theft.Furthermore, implementing strict access controls, such as multi-factor authentication and role-based access, ensures that only the right people have access to sensitive data. Regular audits and monitoring also help detect suspicious activity before it escalates. By prioritizing cybersecurity, individuals and businesses can safeguard critical data and prevent its misuse, reducing the likelihood of breaches and associated risks.
Leverage Cyber Security to Unlock the Future! Enroll in the Cybersecurity Expert Masters Program Training Course Program at ACTE Right Away.
Cybersecurity Measures and Best Practices
Cybersecurity in Different Industries
Different industries face unique cybersecurity challenges, and tailored approaches are essential for effective protection. In healthcare, protecting patient records and medical histories is paramount to maintaining privacy and trust. A breach in this sector can lead to identity theft or the misuse of sensitive health data. In the financial industry, securing transactions and preventing fraud is critical to safeguarding customer assets. Banks and financial institutions invest heavily in cybersecurity measures, such as real-time fraud detection systems, to protect against Cybersecurity Training Courses. Government organizations dealing with sensitive national security information face threats from nation-state actors seeking to disrupt critical infrastructure. In e-commerce, protecting customer data, including payment information, is vital to avoid financial losses and reputational damage. Each sector requires industry-specific strategies, regulatory compliance, and ongoing vigilance to ensure robust cybersecurity and protect stakeholders from the evolving threat landscape.
The Evolution of Cybersecurity
Building a Cybersecurity Culture
A cybersecurity culture is essential for an organization’s long-term security posture. Employees must understand the risks associated with cybersecurity and how to prevent them. Regular training sessions can educate staff about the latest threats, such as phishing scams or Social Engineering attacks, and how to recognize warning signs. By fostering a culture of awareness, companies ensure that cybersecurity is everyone’s responsibility, not just that of the IT department. Organizations should also implement clear policies that define how to handle sensitive data, password requirements, and incident reporting procedures. Encouraging a proactive approach, where employees feel empowered to report suspicious activity, can help detect threats early. Leadership plays a crucial role in setting the tone and prioritizing security initiatives. By integrating cybersecurity into daily operations and company values, organizations can build a resilient defense against cyber threats.
Preparing for Cyber Security job interviews? Check out our Cyber Security Interview Questions and Answers now!
Conclusion
In today’s interconnected world, robust cybersecurity is not just a best practice but a necessity. The increasing frequency and sophistication of cyberattacks highlight the importance of proactive defense mechanisms. Cybersecurity Training protects sensitive data, ensures business continuity, and fosters trust among customers and partners. With threats becoming more complex and widespread, individuals and organizations must remain vigilant, continuously updating their security practices to keep pace. While no system is entirely invulnerable, implementing layered security strategies significantly reduces the risk of breaches. Building a cybersecurity-aware culture, investing in advanced technologies, and prioritizing data protection are all vital steps toward safeguarding digital assets. As cyber threats continue to evolve, so too must our efforts to protect ourselves and our systems from potential harm. Robust cybersecurity is essential to maintaining the integrity, security, and success of the digital world we live in.





