
- Introduction
- What exactly is a Man in the Middle attack?
- The most frequent MITM attacks
- The different kinds of MITM attacks
- Man in the Middle Attack Tools and techniques
- Preventing Man in the Middle Attacks
- Conclusion
A Man in the Middle (MitM) attack occurs when an attacker intercepts and potentially alters communication between two parties without their knowledge. The attacker can eavesdrop on sensitive data, inject malicious content, or impersonate one or both parties to gain unauthorized access to information. There are various types of MitM attacks, including packet sniffing, session hijacking, and SSL stripping, each exploiting different vulnerabilities in network security. Cyber Security Training Courses are essential for educating individuals on how to recognize and prevent these attacks, teaching them best practices to secure communication channels and protect sensitive data from malicious actors. Tools commonly used in MitM attacks include Wireshark for packet capturing, Cain and Abel for password sniffing, and SSLStrip for bypassing secure HTTPS connections. MitM attacks pose significant risks, especially in unencrypted or poorly secured communication channels, and can lead to data breaches, financial loss, and privacy violations.
Interested in Obtaining Your Cyber Security Certificate? View The Cyber Security Online Training Offered By ACTE Right Now!
Introduction
In today’s increasingly digital world cybersecurity threats are evolving with one of the most significant being the Man-in-the-Middle (MITM) attack. This type of cyberattack allows malicious actors to secretly intercept and manipulate communications between two parties, posing a serious threat to the confidentiality and integrity of sensitive information. Network Segmentation can help mitigate such attacks by isolating critical systems and data, making it more difficult for attackers to access and exploit sensitive communications. Whether it’s on unsecured public Wi-Fi through DNS spoofing or by impersonating legitimate websites MITM attacks are widespread and can have devastating consequences including identity theft fraud and unauthorized access to personal or financial data.
What exactly is a Man in the Middle attack?
A Man in the Middle (MITM) assault is a form of cyberattack prevention in which a malicious actor secretly intercepts and manipulates the verbal exchange among events without their knowledge. The attacker positions themselves inside the verbal exchange path, effectively “listening in” or changing the records exchanged. This form of assault is especially risky because it permits the attacker to scouse borrow touchy Cyberattack data like login credentials, monetary details, or non-public records. MITM assaults can arise in numerous forms, together with eavesdropping on unsecured Wi-Fi networks, DNS spoofing, or the usage of faux websites to seize consumer records. For instance, on an unencrypted Wi-Fi network, an attacker could intercept data transmitted between a user and a website, gaining access to sensitive information. Network Topology plays a crucial role in securing communications, as a well-designed network can help isolate critical systems and limit the exposure of sensitive data to potential attackers. Attackers may additionally inject malicious content, redirect customers to faux websites, or impersonate one of the speaking events. The number one defenses in opposition to MITM assaults consist of encrypting verbal exchange channels the usage of protocols like HTTPS security for Transmitting sensitive information using steady authentication mechanisms, and warding off public or unsecured networks.
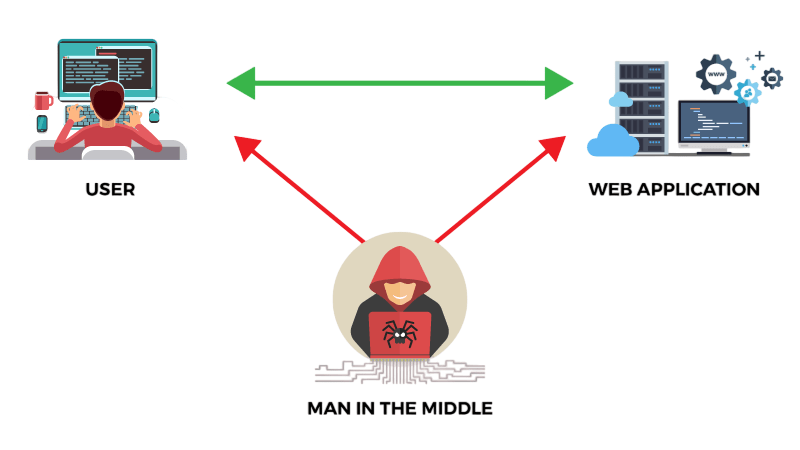
Man inside the Middle assault (MITM assault) is a form of assault in which a domain or man or woman collects your or your organizations records for malicious motives. Usually, such malicious motives are willing to finance Fraud prevention. With the boom of cyber threat technology, different events impersonate famous websites to benefit your trust. After gaining your trust, they subsequently get entry to your records. In this assault, usually, your login credentials and card details, majorly credit score card details, are targeted. The assault is initiated via way of means of manipulating community visitors. Network visitors are manipulated via way of means of putting assault equipment among interactions. The man inside the Middle assault equipment creates a deceivingly comparable community. In some other methodologies, the authentic interplay community is compromised. By hijacking the community, and at present authentication is eliminated to get entry to your records. Generally, the assault occurs on e-trade web websites in which supplying personal records, together with residential deals and social media login data, is a norm and requirement.
Are You Interested in Learning More About Cybersecurity? Sign Up For Our Cyber Security Online Training Today!
The Most frequent MITM attacks
Interception of dataInterception of information occurs through redirecting or directing you to a website this is deceivingly just like the kind of web page which you begin with clicked or searched; your information can be gathered through a 3rd birthday birthday celebration on the same web page. This is carried out by putting in a packet sniffer to your network.
Attack on financial institution accountOne of the maximum not unusual varieties of assault in recent times is the assault on financial institution accounts. This is initiated by contacting you over the telephone or Encryption message. The different birthday celebration poses as a consultant of your financial institution. Usually, throughout the communication, the handiest matters that the opposite birthday celebration is aware of are your call and the call of the financial institution. The communication commonly hovers around your financial institution information being compromised through a few third-party parties. Cyber Security Training Courses are essential in educating individuals on how to protect sensitive information and recognize the signs of potential breaches involving third parties. The communication is observed through a promissory notice that by imparting your login statistics, you may guard your financial institution account immediately. When you offer your login statistics to the opposite birthday celebration, they’ll touch your financial institution, commonly impersonating you, mentioning that they would like to get entry to your account.
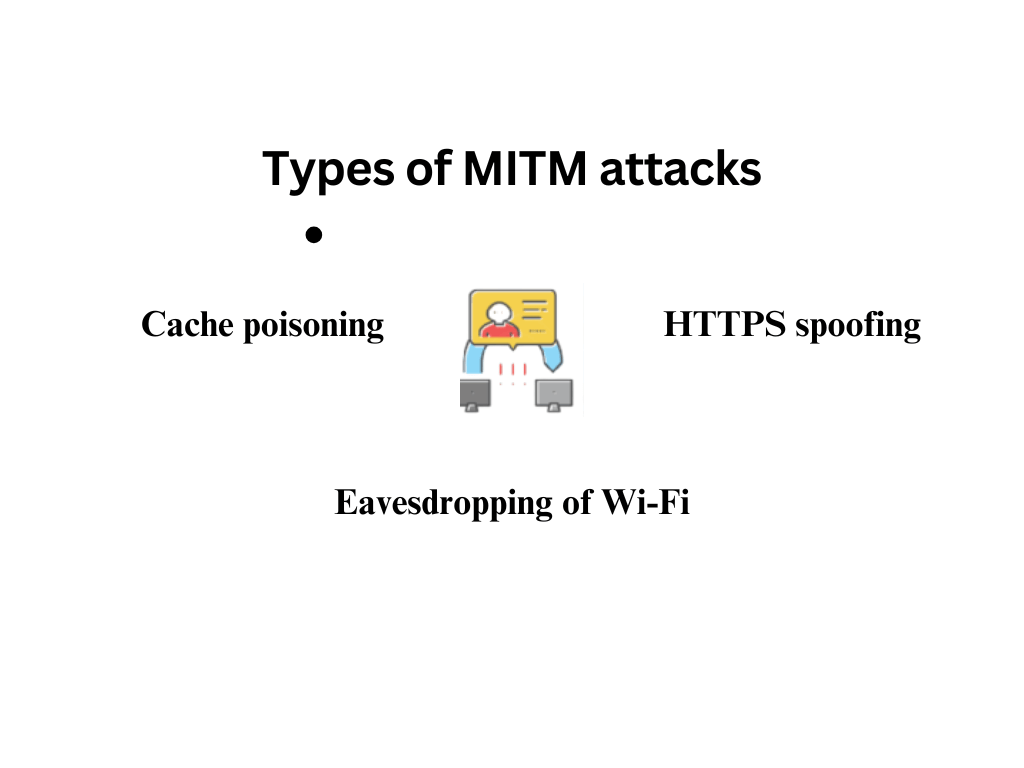
The different kinds of MITM attacks
- Cache poisoning: In this sort of assault your community machine is compromised via way of means of manipulating your device cope with. By changing your device cope with right into a nearby IP community, your pc proceeds with the relationship to cope with constant via way of means of the opposite celebration. This way you may assume that the connection is established to the webpage you chose, but in reality, the other party might have diverted the connection to a location where data can be gathered easily. Since the new connection is deceivingly similar to the one selected by you, it would take some time to discover the difference. Container Security Tools can help mitigate such risks by securing and monitoring the environments in which applications run, ensuring that data communications are protected from potential interception or diversion.
- HTTPS spoofing: This Man Inside the Middle assault is sort of much like the only one noted above. The distinction is that the web web page commonly has a minor alternate of syllable, phonetic alteration of syllables, or both. Though there won’t be a redirection, as inside the preceding case, the deceivingly comparable web page commonly receives your interest whilst you’re searching for a selected web page. This takes place due to the strategic advertising of the web page via way of means of the opposite celebration. As a result of such advertising practices, the same web page is commonly the equal web page because the unique web page inside the seek engine consequences web page (SERP.) On clicking at the 1/3-celebration web web page, you may be supplied with an authentication certification. On downloading the authentication certificate, the 1/3 celebration may be capable of getting the right of entry to your facts.
- Eavesdropping of Wi-Fi: Have you ever stumbled upon loose Public Wi-Fi? If yes, then this phase is probably of significance to you. For the welfare of the overall public, cybersecurity specialists commonly recommend you keep away from loose Wi-Fi networks.
- Common tools in Man-in-the-Middle (MITM) attacks intercept, monitor, or manipulate communication, enabling data theft and network manipulation, often on unsecured Wi-Fi or LANs.
- Similarly, in a Watering Hole Attack, attackers compromise a trusted website that the target frequently visits, making it easier to infect the victim’s system with malware once they access the site. Both attacks exploit vulnerabilities in network security to gain unauthorized access to sensitive information.
- Packet sniffer, Ettercap, dSniff, and Cain and Abel are commonly used to intercept verbal exchanges among hosts. The noted gear is extra powerful and green whilst utilized in LAN community environments.
- Proxy gear is used to govern HTTP protocol. The Man Inside the Middle assault proxy gear consists of OWASP, WebScarab, Paros, Burp Proxy, ProxyFuzz, and Odysseus.
- Enable VPN security connectivity for all of your devices. This helps protect against threats like Cryptojacking, where attackers secretly use your device’s processing power to mine cryptocurrencies without your consent, often without you noticing until it’s too late. A VPN can add an extra layer of security, shielding your devices from such malicious activities.
- Employ an attention marketing campaign or any application of such nature in which your personnel can apprehend diverse obligatory ideas which include not unusual place cyberattacks and cyberthreats.
- Enable extra cybersecurity measures with the aid of imposing PGP/GPG encryption gadgets in your non-public and painting mail IDs.
- Update your cybersecurity gadget frequently by the Packet sniffer.
Looking to Master Cybersecurity? Discover the Cyber Security Expert Masters Program Training Course Available at ACTE Now!
Man in the Middle Attack Tools and techniques
Preventing Man in the Middle Attacks
The following segment will assist you in apprehending special approaches to shield your facts from MITM assaults.
Are You Preparing for Cyber Security Jobs? Check Out ACTE’s Cyber Security Interview Questions and Answers to Boost Your Preparation!
Conclusion
In conclusion, a Man in the Middle (MITM) assault is a vast change in cybersecurity, focused on the integrity and confidentiality of virtual verbal exchange. By intercepting and doubtlessly changing facts exchanged among parties, attackers can thieve touchy sensitive information, compromise consumer accounts, or manage transactions. This kind of assault underscores the significance of sturdy protection practices in the virtual age. Preventing MITM assaults calls for an aggregate of technological safeguards and consumer attention. Cyber Security Training Courses are crucial in educating users on recognizing potential threats and understanding the best practices for securing their devices and communications to avoid falling victim to these types of attacks. Encryption protocols like HTTPS security Transmitting sensitive information and steady verbal exchange practices function as the primary line of defense, making sure facts are confidential. Additionally, customers need to keep away from the use of Public Wi-Fi networks without protection, which includes a VPN security and stay vigilant for symptoms and symptoms of suspicious activity, which include sudden login activates or altered URLs. Organizations should prioritize imposing and preserving up-to-date HTTPS security features to shield their networks and customers from this evolving change. Since the Fraud prevention of man-inside-the-middle assaults is higher than the cure, it’s far recommended to continually be up to date on the present-day cyber threats happening inside the enterprise or groups around you. In this way, you could mitigate Man Inside the Middle assaults and shield your facts effectively.





