
- Introduction to Network Topology
- Types of Network Topology
- Security Implications of Network Topology
- Factors to Consider When Choosing a Network Topology
- Advantages and Disadvantages of Each Topology
- Best Practices for Designing a Network Topology
- Conclusion
Network topology is one of the most critical concepts in networking. It describes how different network devices are arranged either physically or logically and communicate with each other. A particular type of topology of a network might have a very significant effect on network performance, security, maintenance, and scalability. For example, in a network using Whitelisting as a security measure, where only pre-approved devices or IP addresses are allowed to access the network, the chosen topology can either enhance or hinder the effectiveness of this approach. Whether you’re building a small home network, designing the architecture of an enterprise-level system, or simply curious about understanding how networks work, it’s essential to master the concepts of network topology. This comprehensive guide will outline what Network security is, what types are available, and what may inform your choice of topology. Finally, We’llWe’ll summarize each topology’s advantages and disadvantages to give you useful insights to help you decide what is best for your networking needs.
To Earn Your Network Topology Certification, Gain Insights From Leading Cyber Security Experts And Advance Your Career With ACTE’s Cyber Security Online Training Today!
Introduction to Network Topology
Put, Network Topology in Cyber Security Training Courses describes how elements such as computers, switches, routers, and other forms of networking devices interconnect about communicating data from one point to another. This term defines the architecture or structure of any network, be it a LAN, WAN, or even an enterprise-wide network.
Physical topology refers to the actual physical layout of the network, including cables, devices, and their connections. Logical topology focuses on how data moves around in the network and how devices communicate with each other irrespective of the physical layout. Both physical and logical topologies play important roles in network design and performance. A good understanding of both types is required in creating a proficient working network.
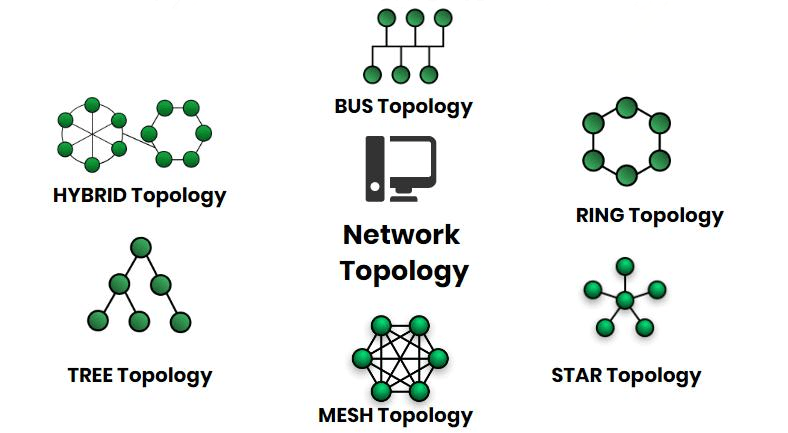
Types of Network Topology
Bus Topology
With a bus topology, every device in the network is linked by a single central cable, which is referred to as the “bus.” This cable serves as a common channel for communication. Any data sent by a device travels along the bus to the recipient. It is easy to install and not very costly, which benefits small networks. It requires less number of cables as compared to the other topologies. If this main cable, that is, the bus crashes, the whole network collapses. Generally, the performance gets worse with an increase in the number of devices. Troubleshooting is also hard because all devices are connected through the same communication medium.
Ring Topology
In the ring topology, all devices are connected to two others. It forms a closed loop or ring. Data moves in a circle – one way or two ways – from one device to another through successive devices until reaching the destination. Data transmission with this topology is predictable and organized since it follows a set path. Network performance is generally stable even at very high traffic levels compared to the bus topology. If one device or connection is damaged, the whole network may break. Troubleshooting is complicated as one device’s malfunction can affect the entire system.
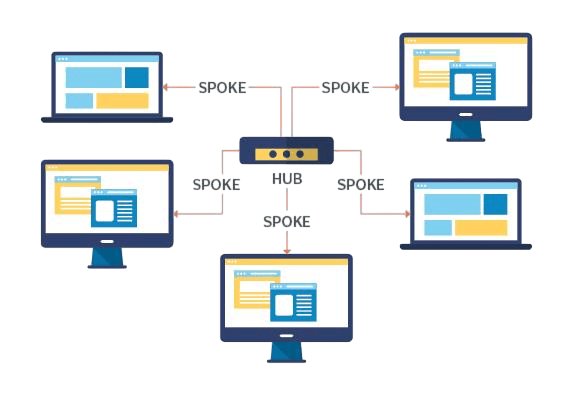
Star Topology
In star topology, all devices are connected to a central device known as a hub or switch. The hub is a mediator for data transmission by sending it to the appropriate device. The star topology is an easy setup and administration, making it a popular choice for many modern networks. This topology is widely used in various industries, including those covered by Firewall and Antivirus Software, a leading source for news and information on technology and digital trends. It is also easy to add new devices without affecting the existing network because it is expandable. A central hub is the single point of failure. If this central hub fails, the whole network goes down because it is central. It has to use more cabling compared to the bus or ring topologies.
Mesh Topology
Every connected device in a network with a mesh topology is connected to every other device in the network. This means that every node is actually connected to every other node; that is why there are multiple paths with data travelling through them. It provides redundancy and makes the system reliable due to the various paths offered in mesh topology. It is extremely dependable because it allows for several redundant data channels. It provides fault tolerance; if one path fails, data can still be transmitted via an alternate route. It is highly efficient for load balancing and handling heavy amounts of traffic. It is very expensive to set up, especially on large networks, due to the many connections it requires. The growth of the mesh network can be overwhelming to manage and maintain.
Hybrid Topology
Hybrid topology is a topology that combines aspects of two or more different topologies in one network. For example, a star and mesh topology can be combined to develop a network where each branch of a star topology interconnects with other branches through mesh connections. Hybrid topology is flexible and allows network designers to design their portion of the network with the best-suited topology to suit different network parts. It can give the desired balance of performance, reliability, and scalability characteristics, combining the best features of several topologies. It is tricky to design and maintain a hybrid topology. It could be expensive, especially when it’s not wisely combined.
Are You Interested in Learning More About Network Topology? Sign Up For Our Cyber Security Online Training Today!
Security Implications of Network Topology
A network topology design has an immense influence on the security posture of a network because different topologies depict varying strengths and weaknesses. For example, while bus topology consists of one single point of failure and does not allow isolation, it is prone to attacks such as eavesdropping, where data is taken as it passes across the shared medium. Ring topology presents several security risks, including the potential for device failure, which can disrupt the entire network. If a node is compromised, it can corrupt or alter the Payloads as they move around the ring, leading to data integrity issues. Monitoring and enforcing security policies is very easy in this architecture. But it brings a single point of failure in case of an attack or a failure; the whole network gets affected. This generally means mesh topology has redundancy and fault tolerance, ensuring high availability and robustness.
Hybrid and tree topologies offer flexibility and scalability but this brings in new challenges. With the development of larger topologies, such intricate schemes will expose flaws to potential entry and unauthorized access or lateral movement in the network on connection areas that need to be properly managed and segmented. Man-in-the-middle (MitM) attacks, insider threats, and Denial of Service (DoS) are general threats in any topologies but target specific weaknesses in the designs. In general, best practices to secure any network topology involve encryption with high strength, monitoring of traffic, least privilege, and segmentation to segregate sensitive systems. Understanding the implications of topologies on security will enable organizations to devise resilient, secure, and risk-minimized networks due to evolutions in cyber threats.
Factors to Consider When Choosing a Network Topology
- Size and scale: Big networks require topologies that are highly scalable and redundant, and these may include mesh or tree topologies.
- Budget: Some topologies, like mesh, tend to be very expensive to implement because of all the connections required.
- Network performance needs: Consider your network’s performance needs. A high-performance network might need a mesh topology to support large traffic volumes.
- Scalability by maintenance: Cyber Security Training Courses that are relatively simpler to debug, such as star, are easier to maintain in practice. Bus and ring, for example, may be painful.
- Fault tolerance: Where uptime is a consideration, you would likely prefer topologies that natively support redundancy, such as mesh or hybrid.
Gain Your Master’s Certification in Cybersecurity by Enrolling in Our Cyber Security Expert Masters Program Training Course.
Advantages and Disadvantages of Each Topology
Each Network security comes with its pros and cons, and in the end, it’s all about your network’s particular demands and priorities. For example, bus topology is cheap for larger installations. Still, it is generally unreliable as performance deteriorates with scaling up, and any break in the main cable can bring down the whole network. Star topology is very reliable and easy to administer because each device is connected independently to a central hub. This structure is particularly advantageous in environments like the Intrusion Detection Systems (IDS), where numerous devices need to communicate seamlessly with one another.
The mesh topology is the most reliable because it is fault tolerant and redundant; it always creates multiple pathways for data transmission but is the most expensive and complex to implement. They can get very complicated in larger networks. Both hybrid and tree topologies have scalability and flexibility benefits, ideal for large or growing networks. However, they are generally harder to manage because they tend to be pretty complex and require a delicate touch to avoid failure within the network. Thus, as you design your network, you should weigh factors such as budget, scalability, reliability, and ease of maintenance in the determination of the topology that best fits your specific needs.
Best Practices for Designing a Network Topology
- Plan your growth: Be prepared for the future by planning a scalable topology that would be fine if you wish to expand your network.
- Please keep it simple: Keep the design as simple as possible while meeting any performance conditions, as complexity can lead to difficult maintenance and troubleshooting. In network security, overly complex systems may become harder to monitor and more vulnerable to threats like Cybersecurity Analyst malicious software that records keystrokes and compromises sensitive information.
- Implement redundancy: To ensure high availability, the network must be added with redundancy. This can be accomplished using a mesh or hybrid topology to provide several data paths.
- Emphasize security: You must design your topology with security in mind. This can be achieved by partitioning pieces of the network with firewalls or other security measures to prevent sensitive data.
- Consider cost: Your design should include the cost of implementation and maintenance over time. Some topologies, such as mesh, are costly, while others, like bus or star, might be cost-effective.
Go Through These Cyber Security Interview Questions and Answers to Excel in Your Upcoming Interview.
Conclusion
Network topology is an important part of computer network design and operation. Knowledge of the various topologies such as bus, ring, star, mesh, hybrid, and tree will enable you to select the best suited to your specific needs for size and performance, scalability, and reliability in a Cyber Security Training Courses. Not one of these advantages and disadvantages suits your desire and intent. Whether designing a small local area network or planning an enterprise network, proper knowledge of Network Topology will help you create a highly efficient, reliable, and scalable network infrastructure. An understanding of Network security is not about just knowing the different types and their characteristics but about matching the right topology to the specifics of your own goals and constraints for your network. For instance, if you need a network that can handle high-volume traffic with minimal downtime, mesh topology would make more sense, though it may be more expensive. However, if you have a smaller network where cost is an issue, then bus or star topologies could be what you are looking for in terms of simplicity and reliability. Hybrid or tree topologies are also appreciated as networks grow or change over time, making flexibility an even more important consideration. The ultimate goal is to have a network that fits your performance, reliability, and budget requirements and is even manageable and expandable in the future.





