
If you want to be an IT auditor, or are one now and don’t have a certification, then why not consider the Certified Information Systems Auditor (CISA) credential? This is among the 7 Top Security Certifications You Should Have in 2018, and is one of the key certifications employers look for when considering candidates for IT auditor and assurance positions worldwide.
The CISA certification program guides professionals through the knowledge needed to be in the profession and proves the presence of skills specific to the audit IS/IT function. IT audit leaders and professionals are assuming an increasingly integrated role in regard to technology initiatives in their organizations, and companies are actively looking for professionals who can prove their expertise to cover these key roles.
Become a Certified
Information Systems Auditor (CISA)

This learning path builds your knowledge of auditing information systems. Learning path components include:
⇒ Network infrastructure security
⇒ CISA practice exams
⇒ And more
What Is the CISA Certification?According to CareersinAudit.com, an IT auditor generally follows five steps in the process of an IT audit:
- Planning
- Studying controls and the evaluation of those controls
- Testing and reevaluating the controls
- Reporting findings
- Following up at a later date to ensure all is still well
The auditor, might just fill the gaps in helping complete a company’s incident response plan (IRP) that requires paying attention to the three Ps in auditing: policy, plan and the procedures.
Though there is no one path into the IS/IT audit profession, the CISA certification can help credential holders get a competitive edge on others without the designation. As ISACA explains, the CISA-certification showcases a professional’s audit experience, skills and knowledge, and demonstrates the ability to assess vulnerabilities, report on compliance, understand the internal controls structure and/or institute controls within a risk-based approach for security activities in order to mitigate increasing cyber threats. Auditors do play a significant role in an organization and that is why a forward-thinking corporation is likely interested in attracting and retaining top talent that can provide an accurate IT audit trail.
The CISA credential is governed by ISACA, one of the most trusted names in the information systems and security industry. It is ISACA’s oldest credential, dating back to 1978, and focuses on demonstrating your capabilities in every stage of the auditing process, from updates to a company’s policies to ensuring compliance with procedures and understanding how well an organization can assess vulnerabilities.
There are five CISA job practice areas on which candidates are examined:
Domain 1: The Process of Auditing Information Systems (21% of the Exam)Provide audit services in accordance with IS audit standards to assist the organization in protecting and controlling information systems.
This domain covers topics like executing effective risk-based IS audit strategies, following proper IS audit standards, communicating results and recommendations to stakeholders, and performing necessary audit follow-ups. This section tests the applicants’ knowledge of audit standards, tools and techniques; it also tests knowledge of risk assessment concepts, controls, applicable laws and regulations pertaining to audits affected by business processes. It also covers techniques relating to evidence collection, communication, quality assurance (QA) systems and frameworks, as well as types of audits.
Domain 2: Governance & Management of IT (16% of the Exam)Provide assurance the necessary leadership and organizational structures and processes are in place to achieve objectives and to support the organization’s strategy.
This domain looks at general IT strategies in an organization and evaluates the IT governance structure for effectiveness. It also covers the evaluation of a number of areas to check their alignment with the organization objectives as well as their efficacy. This includes IT human resources and organization, policies and procedures, portfolio management, business continuity plan as well as disaster recovery, in addition to key performance indicators. This section tests specific knowledge of IT governance and strategies, issues, process optimization techniques, enterprise risk management (ERM), quality management and quality assurance, scorecards, KPIs and topics related to business continuity.
Domain 3: Information Systems Acquisition, Development & Implementation (18% of the Exam)Provide assurance the practices for the acquisition, development, testing and implementation of information systems meet the organization’s strategies and objectives.
This domain covers topics related to selecting IT suppliers and contracts that can guarantee proper service levels; it also covers the managing of projects, from checking its progress according to plans to proper documentation of all phases. It also touches on systems implementation, testing and evaluation. Knowledge tested includes topics like feasibility studies, business cases, total cost of ownership (TCO) and return on investment (ROI), as well as project management and project risk management, project requirements analysis, success criteria and post-implementation issues. It also covers secure coding and specific knowledge of system development methodologies and tools, such as agile, rapid application development (RAD) and object-oriented design techniques.
Domain 4: Information Systems Operations, Maintenance & Service Management (20% of the Exam)Provide assurance the processes for information systems operations, maintenance and service management meet the organization’s strategies and objectives.
This domain covers the evaluation of IT practices to ensure they meet the stated service levels and the needed controls. It looks at the operations, maintenance requirements, database handling, incident management practices and the evaluation of business continuity and resilience of the organization IT infrastructure. It covers knowledge related to service management practices, enterprise architecture, systems resiliency, control techniques and performance monitoring. It also tests data backup, database management, data lifecycle, incident management practices and disaster recovery testing.
Domain 5: Protection of Information Assets (25% of the Exam)Provide assurance of the organization’s policies, standards, procedures and controls ensure the confidentiality, integrity and availability of information assets.
This domain is all about topics related to the protection of IT assets: the evaluation of policies and procedures as related to information security, physical and environmental controls, verification of material regarding their CIA (confidentiality, integrity and availability), along with storing, transportation and disposal of assets, as well as information security programs. The domain tests the candidates’ knowledge of a particular feature of the job, including:
- Privacy and information security laws and regulations
- Physical and environmental controls
- Identification, authentication and restriction of users
- BYOD and virtualization risks and voice communications security
- Encryption, PKI and digital signatures
- Data handling risks and proper procedures, attacks methods, detection and testing techniques
- Digital forensics
The job practice areas serve as the basis for the exam and requirements to earn the certification. The five domains are the result of a streamlining of the six domains previously identified by ISACA. A review of the test in 2016 triggered the removal of 50 questions (down from 200 to 150) on the exam. The domain weight percentage also changed: domain one went from 14% to 21%; domain two changed from 14% to 16%; domain three went from 19% to 18%; domain four dropped from 23% to 20%; and domain five had the biggest drop, going from 30% to 25%.
Who Should Earn the CISA?“The CISA credential is often a mandatory qualification for employment as an IS auditor,” says Frank Schettini, ISACA’s chief innovation officer. Such auditors have many job responsibilities and duties, including “work[ing] with a team of other IT professionals to create a secure environment for staff and the business as a whole […] after identifying security threats, a security auditor must be able to patch and secure each system including network, desktop and external software systems.” An information systems security auditor is just one of many career options in the field. In addition to IS/IT auditors, the CISA target market also includes those in other roles, such as:
- IS/IT consultants
- IS/IT audit managers
- Security professionals
- Non-IT auditors
The ISACA CISA certification is also a DoD-approved baseline certification under DOD 8570 (at IAT Level III, specifically related to CND auditing). Today, there are 31,000+ CISAs who are managers and consultants. There are also 2,800+ CISAs who fill CEO, CFO, CIO or CXO positions.
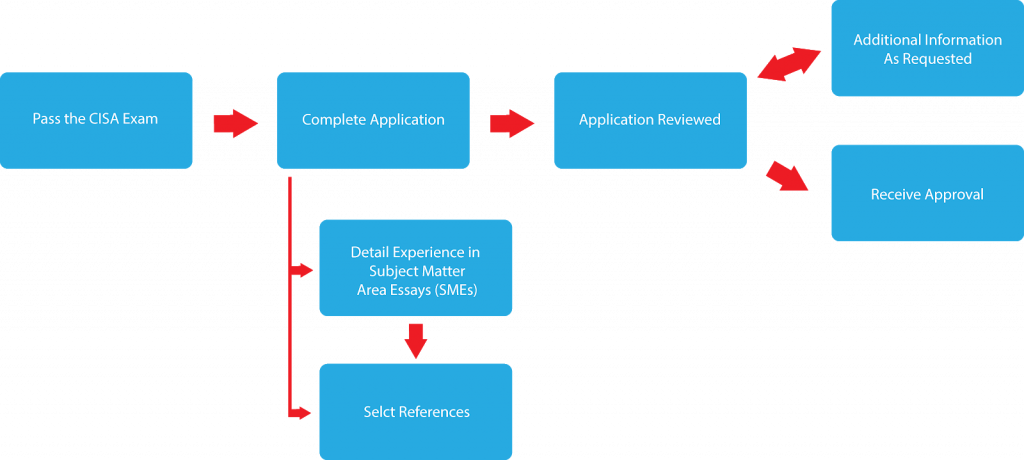
What Experience Do You Need to Apply for the CISA?ISACA’s globally recognized CISA certification requires all auditors to have some degree of technical expertise. In fact, five years of experience is required in IS auditing, control or security; up to a maximum of three years can be substituted by specific experience or college courses/degrees. The path to certification requires both understanding and familiarity of the five mentioned CISA domains in order to pass the exam.
Members of ISACA and/or holders of the CISA designation also need to agree to a Code of Professional Ethics and are required to follow a continuing professional education (CPE) program that requires maintenance fees and at least 20 contact hours of CPE annually, in addition to a minimum of 120 contact hours during a fixed three-year period. Plus, compliance with ISACA Information Systems Auditing Standards is also required.
The test is offered only during certain times of the year: February – May 24, 2018 and June – September 23, 2018 are the next testing window dates for exam registration. In preparation for the big day, be sure to check out this article on 10 Tips for CISA Exam Success.
Is the CISA Certification Worth the Effort?As mentioned in ISACA’s press release, the CISA certification was recognized as Best Professional Certification Program in the SC Awards 2017. Unsure what this means for career opportunities? ISACA’s interactive infographic, IT Audit Career Roadmap can provide some answers. “For some business and governmental agencies, CISA is even a prerequisite for information systems and information technology roles,” ISACA states. And many hiring managers look for CISA-certified candidates.
Beyond ISACA’s infomercial, the cert can truly add much value. It is globally recognized in the audit, control field and security of information systems. It can help candidates stand out from the crowd and can help professionals keep abreast with the latest changes in the field. CISA certificate holders also tend to earn more than any other IT audit career path (see: Average CISA Salary in 2018). The Certified Information Systems Auditor (CISA) is often listed among the top-paying certs worth considering.
What is the Best Way to Train for the CISA Exam?ISACA provides a CISA online review course which is a self-paced option for learners interested in preparing for the exam. They also offer a CISA self-assessment, a 50-question sample exam that focuses on IT and/or security related topics as well as general auditing principles.
In addition to the ISACA training solutions and CISA exam resources, InfoSec Institute offers a CISA Boot Camp, a five-day course exclusively focusing on the essential areas covered in the CISA exam. Also, Intense School offers IT audit training courses, including a boot camp focused on preparing students for the CISA examination through testing of knowledge and the ability to apply it to real world scenarios. To help build the candidates skillfulness, see CISA-The process of Auditing Information Systems prior to taking the exam to help improve your chances of passing it.
The CISA course is divided into 5-modules that cover the entire scope of IS Audits and review. Each module here with individual professional credits are displayed in your final certificate.
Module 1 — The Process of Auditing Information Systems
You gain knowledge of complying with the highest standards of information systems and provide the best practices of the audit. For companies, it means a thorough control and protection of their revenue cycles, business and information systems.
Module 2 — CISA’s Role in IT Governance
This module assists in developing sound IS control practices and management mechanisms and enterprises gain assurance of best practices which include policies, structures of monitoring, accountability and desired IT governance.
Module 3 — CISA’s Role in Systems and Infrastructure Lifecycle Management
The modern processes and methodologies that modern organizations employ while reinventing the infrastructure component of applications systems are learned in this module. This module trains you in your actual job-role as well.
Module 4 — CISA’s Role in IT Service Delivery and Support
You learn to review the processes and methods applicable to different IT systems. It will deliver knowledge of the IS audit in the event of a disruption. Businesses here gain by hiring professionals who can enact disaster recovery methods and timely consumption of database services and minimize the negative impact on various processes.
Module 5 — CISA’s Role in Protection of Information Assets
The key component of Module 5 enables a professional to be able to ensure the integrity, availability, and confidentiality of information assets while instituting physical and logical access controls and other security measures.
How Can I Earn CPEs to Maintain My CISA Certification?Like other ISACA certs, you will need to earn CPE credits to maintain your certification. Therefore, IT auditors can stay up-to-date by even attending conferences like the Institute of Internal Auditors (IIA) conferences or the 2018 General Audit Management Conference. Another event is the Women in Internal Audit Leadership Forum, which is geared towards advancing women in the profession. These events are usually offered each year.
Still, there’s ISACA’s 2018 North America CACS Conference for information systems audit, assurance, control, governance and security professionals, taking place in Chicago, Illinois. There, attendees can earn up to 39 continuing professional education (CPE) hours from participating in pre- and post-conference hands-on workshops. Other opportunities include IIA’s International Conference which is an important training and networking event for internal audit professionals worldwide at Dubai WorldTrade Centre Convention Centre in the United Arab Emirates. At this event, there will be 2,500+ audit industry practitioners and providers from 100+ countries present who want to keep up with the trends and emerging issues in the internal audit profession; it is a place to learn of new tools to enhance how auditors function with innovative practices. Then, there’s the 2018 All Star Conference held at the ARIA Resort & Casino in Las Vegas, NV. This event is sure to attract participants interested in knowing about the impact of the internal audit environment now and in the future. Attending conferences or hands-on workshops will give security auditors a chance to learn about the latest developments in IT audit field and keep their skills and knowledge up to date.





