
- Types of Privileged Accounts
- PAM Architecture
- Benefits of PAM
- Challenges in Implementation of PAM
- PAM in the Context of Compliance
- Core Components of PAM
- Trends in PAM over the Future
- Case Studies
- Conclusion
PAM is a security practice that involves tracking and monitoring who, with what, and when accesses critical systems, applications, and data of elevated privilege. Such users, including system administrators, have access well beyond the ordinary users, and thus, their accounts are desirable for attackers. Cyber Security Training Courses helps reduce the risks involved in these privileged accounts by controlling, securing, and auditing access. Generally speaking, pam security includes binding and managing credentials, introducing stringent access controls, along monitoring user activity against such security standards. Its objectives are to prevent unauthorized access, detect suspicious activity, and reduce the consequences of a possible violation. Organizations can take better security measures to protect their sensitive information, remain compliant with their regulatory requirements, as well as defend against insider and external security threats through PAM cybersecurity.
Types of Privileged Accounts
- Administrator Accounts: Such accounts have full access to the system’s configurations and settings. They usually apply to IT staff when they manage and maintain systems, servers, and networks.
- Service Accounts: Used by applications or services to get access to systems and execute jobs on behalf of users or systems. Service accounts are often automated and have to be elevated in permission to access essential resources. Root Accounts are the most powerful accounts within Unix/Linux systems. They provide complete control over all the pam system files, configurations, and commands and are generally essential for managing the system.
- Superuser Accounts: Similar to root accounts, superuser accounts have full access to PAM system resources but are used in different operating systems or contexts. They are normally utilized in system administration for particular environments.
- Privileged User Accounts: These accounts are assigned more permissions in certain areas, like database management, application maintenance, or Network Topology setup, but they cannot have access across the whole system.
- Privileged Access: Management architecture is an approach designed to control, secure, and monitor spam account access. The spam system integrates some key elements to protect sensitive systems and data.
- Centralized Management Console: The centralized privileged identity management console is the nub of all privileged access that gets managed throughout the organization. It allows administrators to define policies, monitor access, and manage credentials from one interface that unifies everything.
- Credential Vaults: Credential vaults are safe places where privileged account credentials such as passwords and keys are managed and stored. They use strong encryption to protect sensitive data so that no one except authorized users or system administrators can access it.
- Access Gateways: Access gateways play the role of a Web Application Security check but for what is accessed by privileged accounts. They enforce access policies like the protocol and constraints. It only allows authorized unauthorized access to sensitive resources.
- Session Management: This will track and monitor all sessions started by privileged accounts. It tracks the work done in the session and records the activities for audit purposes. It provides real-time monitoring with appropriate measures against suspicious behavior.
- Audit and Compliance Tools: Audit and compliance tools provide on-the-spot tracking and reporting of least privilege access activity in PAM systems. This allows organizations to maintain records or evidence regarding their use of privileged accounts and meet the corresponding regulatory requirements.
- Authentication Systems: Privileged account management integrates with authentication systems, like multi-factor authentication (MFA), to heighten security. MFA adds an additional verification step, ensuring that only authorized persons can access pam accounts, no matter how compromised the password has been.
- Authorized with Other Security Tools: PAM solutions are often integrated with other security technologies, such as Security Information and Event Management (SIEM), privileged identity management and Access Management (IAM), and Intrusion Detection Systems (IDS). This integration ensures comprehensive monitoring and threat detection across the organization.
- Policy Enforcement Engine: The organization engine is responsible for validating each access request against the organization’s security policies before granting access. These organizations have rules applicable to the organizations, such as RBAC, time restrictions, and organization-based policies.
- PAM cybersecurity minimizesizes the risks of data breaches, and minimizes them by strictly controlling and monitoring PAM accounts, which are usually targeted in attacks.
- Pam security can mitigate or prevent insider threats, maliciou minimizeidental, since strict access controls that monitor activities performed by privileged users take place.
- PAM organizations adhere to industry regulations HIPAA, and SOX and provide audit trails together with access restrictions, which makes it easier to pass security audits.
- Privileged account management streamlines privileged accounts management, reducing the overhead of administrators and allowing the use of autonomic password rotation, which can enhance productivity while maintaining Web Security.
- Privileged account management provides real-time monitoring of activities related to privileged users; organizations are on alert to suspect organizational remedial measures.
- It reduces the chances of unauthorized privilege escalation and enforcing unauthorized persons to access critical systems and data, therefore reducing overall business risk.
- PAM solutions store and manage sensitive credentials securely, thus reducing risks such as password theft and passwords that are robust and frequently changed.
- Identifying Privileged Accounts: Identifying and tracking all privileged accounts through various systems proves difficult, especially for large or complex systems. Unaccounted, unmanaged accounts allow serious security vulnerabilities into your environment.
- Ease of Interoperability: The interoperability of PAM solutions with existing systems, applications, and legacy infrastructure may prove difficult to achieve. It often requires extensive customization over an extended period. Ministrators may resist Pam account management implementation because they are worried about added complexity, disruptions to current workflows, or need additional training.
- Scalability Issues: As the number of users and Pam accounts increases with expansion, it’s becoming increasingly hazardous security solutions to ensure security and performance. The full-featured PAM solution has high initial deployment costs, including software, training, and maintenance. In fact, this is more expensive, particularly for small organizations.
- Continuous Maintenance: The efforganizations of a PAM system will change without continued monitoring, updates, and audits. Resource- and time-intensive and will require dedicated teams for regular upkeep. Finding that perfect balance between very secure controls and operational efficiency is challenging. Excess Database Security can negatively impact productivity, while lack of security may leave systems open to risk.
- Adapting to Regulatory Changes: Compliance should also be a challenge in keeping pace with the needs of changing compliance regulations such as GDPR, HIPAA, or SOX; PAM solutions must be in line with these ever-changing standards and, therefore, require many updates.
- PAM Best Practices: Some of the best practices in implementing PAM security include using least privilege, with some conducting regular audits, enforcing MFA for users utilizing least privilege access, and using privileged sessions to detect suspicious activities.
- Adherence to Regulation
PAM security helps companies adhere to critical regulations such as GDPR, HIPAA, SOX, and PCI-DSS that require tough controls and monitoring on access to sensitive data and critical systems of Malware Attack.
- Audit Trail
PAM systems produce a detailed audit log of the activities of the privileged user, providing for compliance auditing and the verification of appropriate implementation of access controls.
- Access Control
The principle of least privilege, which focuses access on just what is necessary, minimizes exposure to sensitive organizations and minimizes to compliance with privacy and data protection regulations.
- Secure Password Management
PAM tools securely manage and rotate privileged passwords to ensure they meet regulatory standards for strong password practices and secure storage. Least Privilege access can be monitored continuously by organizations, thus detecting non-compliance in real-time, preventing unauthorized access, and ensuring compliance.
- Unauthorized Duties
PAM cybersecurity enforces separation of duties. No one should possess excessive control over sensitive systems or data a critical necessity of meeting a large number of compliance requirements.
- Credential Vaulting:Credential vaulting stores and manages the access credentials of privileged accounts (passwords, API keys, SSH keys, etc.) in a highly secure manner. It ensures that the sensitive credentials are encrypted and protected funauthorizedized access.
- Access Control: The unauthorized policy defines and enforces who can gain privileged access and under what conditions. It includes role-based access controls, time-based access restrictions, and other measures to ensure that authorized individuals gain access.
- Sessioauthorizedng and Recording:PAM systems monitor and record the activities of users accessing PAM accounts. This allows for real-time auditing of user actions so that suspicious behaviour can be quickly detected and held accountable.
- Password Management: Pam Security manages privileged passwords automatically, comprising scheduled password changes, enforcing secure policies, and avoiding any form of password reuse. This ensures that credentials are always safe and up to date.
- Audit and Reporting: PAM cybersecurity logging and reporting about privileged identity management user activities is also another critical feature. These logs are helpful in maintaining compliance with regulatory standards and offer more visibility into how accounts are being used, thereby aiding in identifying potential security risks.
- Least Privilege Enforcement: The least privilege principle ensures that users are only accorded the minimum access they need to perform job functions. Limiting unnecessary privileges increases the chances of exposure to sensitive data.
- Multi-Factor Authentication (MFA): PAM cybersecurity integrates MFA to enhance security. This means that even if a password has fallen into the wrong hands, illegal access is still denied in the Two Factor Authentication .
- Integration with Other Security Solutions: PAM systems are built to integrate with other security tools, such as SIEM (Security Information and Event Management) and IAM (Identity and Access Management) solutions, for comprehensive visibility and control over least privilege access across organizations.
To learn about different Privileged Access Management techniques, sign up for our Cyber Security online training right now!
PAM Architecture
Sign up for ACTE Cyber Security online training and get a head start in your career Privileged Access Management
Benefits of PAM
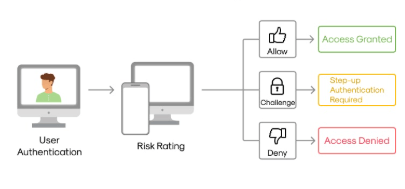
Challenges in Implementation of PAM
PAM in the Context of Compliance
Leverage Privileged Access Management to Unlock the Future! Enroll in the cybersecurity expert masters program Program at ACTE Right Away.
Core Components of PAM
Trends in PAM over the Future
Organizational trends are shaping the future of Cyber Security Training Courses. AI and Machine Learning-integrated PAM solutions will better spot threats in real-time through improved threat detection and anomaly identification capabilities. The Zero Trust security model will be more prominent, with continuous verification of user identities and access rights, implying no user or system is inherently trusted. Cloud adoption will increase the prevalence of cloud-native PAM solutions in a scalable, secure access management platform for cloud environments. It will be integrated more closely with IAM systems for both privileged and non-privileged access for more streamlined processes. Analytics-driven PAM cybersecurity will provide a deeper insight into user behaviour and least privilege access activities for better visibility and detection of potential threats. Privileged account management will also benefit from automation, such as password rotation and session monitoring, with less human error and increased consistency in security practices. These trends represent more intelligent, automated, and scalable PAM solutions addressing new security challenges emerging.
Preparing for a job Interview? Check out our blog on Cyber Security Interview questions and answers !
Case Studies
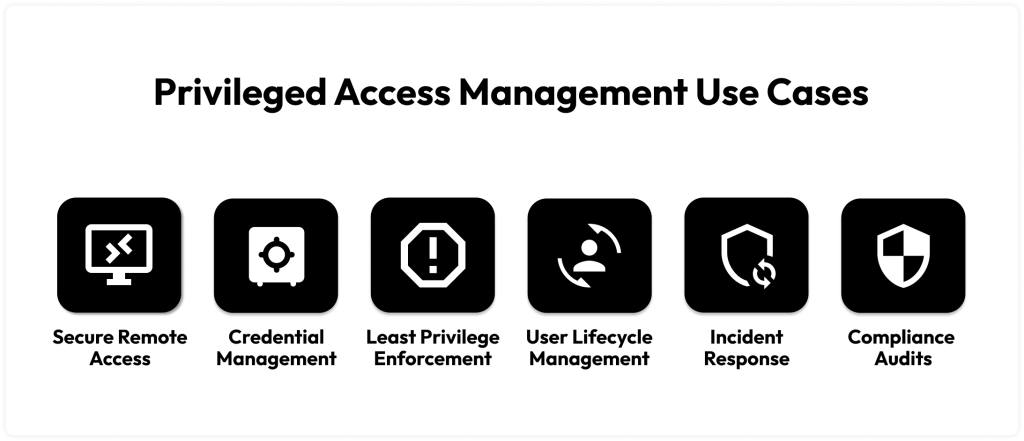
Case studies from industries show that PAM cybersecurity effectively protects sensitive systems. In the healthcare segment, a provider used PAM to gain control over access to patient data and achieve compliance with HIPAA by lessening insider threats. In the financial services industry, a firm implemented PAM to manage privileged accounts, automate password management, and enforce MFA to meet compliance with SOX while strengthening its security. In retail, PAM was used to protect point-of-sale systems, detect suspicious activity, and prevent fraud by a global company. For its part, PAM helped a manufacturing company secure access to industrial control systems and reduce the risk of cyber threats impacting production. Case studies thus illustrate how PAM has resulted in enhanced E-mail Security , supported compliance, and reduced risks across various sectors.
Conclusion
PAM is one of the most important elements of an organization’s security strategy, organizations and key systems from internal and external threats. Best practices, the use of the right tools, and compliance with industry regulations are all powerful elements in helping diminish the risk of unauthorized access to services and potentialunauthorizedes. The capability of the emerging landscape shall be further enhanced through advanced technologies like AI, machine learning, and Zero Trust frameworks for Cyber Security Training Courses.





