
- Introduction to Cyclic Redundancy Check (CRC)
- Understanding the Importance of CRC in Data Integrity
- How CRC Works: A Detailed Explanation
- CRC in Error Detection: Applications and Use Cases
- Types of CRC Algorithms
- Disadvantages of Using CRC
- Conclusion
Once data integrity is ensured in digital communication, the most reliable error detection method is the Cyclic Redundancy Check. It is a key technique for verifying whether data remains incorrupt during transmission or storage. We will learn about the fundamentals of CRC, its many uses, its operation, and why it is the most crucial component of modern computer systems in Cybersecurity Training Courses. CRC guarantees accurate data transmission and reduces errors in embedded devices and networking. Let’s now take a closer look into CRC to see how it improves the dependability of data management.
To become a certified cyber security, have a look at our Cyber Security Online Training right now.
Introduction
Data integrity while being transmitted is of utmost importance in computer networks and digital communications. This is where Cyclic Redundancy Check comes into the picture. CRC is a technique for detecting errors in Database Security. It is very useful in scenarios where data is transmitted or stored across different mediums, such as hard drives, networks, and other forms of communication.A CRC is a checksum or hash function that uses polynomial division to detect changes in raw data. It is one of the most widely used methods for error detection, especially in network communication protocols, storage systems, and disk systems. The CRC value, also called CRC checksum or CRC code, is attached to the data being transmitted or stored. When the data is received or read, the CRC is recalculated and compared with the original CRC. If the values match, the data is assumed to be error-free; otherwise, an error is detected.
Understanding the Importance of CRC in Data Integrity
The importance of CRC cannot be overstated when it comes to ensuring data integrity. Data can be corrupted in transit due to various causes, including noise, signal degradation, or hardware failures. For example, data sent over a Network Topology can be changed by external interference; without a mechanism to validate the received data, these kinds of problems would go undetected, leading to errors, malfunctioning systems, or security breaches. CRC plays a very important role in addressing these concerns by providing a fast and efficient way to ensure that data has not been tampered with or corrupted during transmission or storage. It is a relatively simple and cost-effective technique, making it suitable for high-speed error detection applications. Moreover, CRC provides error detection capabilities that are far superior to traditional checksum methods, especially when it comes to catching burst errors.
Are you curious to know more about Cybersecurity ? Take advantage of our comprehensive online Cyber Security Online Training
How CRC Works: A Detailed Explanation
- Step 1: Select the Polynomial The process begins with selecting a generator polynomial or a divisor. This is a fixed polynomial the sender and receiver use to generate and check the CRC. Common polynomials include CRC-16, CRC-32, and CRC-64, depending on the level of error checking required.
- Step 2: Data Representation The data to be transmitted or stored is represented as a binary number. For example, a text string or a file is converted to binary format.
- Step 3: Divide the data, represented as a binary number, by the generator polynomial through binary division. The critical difference between traditional and CRC divisions is that the former doesn’t involve carrying or borrowing operations while performing division. In contrast, in the case of binary division, XOR bitwise is used.
- Step 4: CRC as Remainder After the division process, the remainder is the CRC value in Vulnerability Management . This CRC value is appended to the original data, creating a “message” for transmission or storage. This message contains both the original data and the CRC checksum.
- Step 5: Error Checking When the data is received, the same division process is applied. If the remainder is zero, the data is likely error-free. If the remainder is non-zero, it suggests that the data has been altered or corrupted.The beauty of CRC lies in its ability to detect even minor changes in the data quickly. Since it operates on the binary form of the data, CRC can spot bit-level errors that may go unnoticed by other methods.
At its basic level, CRC works on a principle of polynomial division. Here’s a simple outline of how it works:
Want to Take the Lead in Cyber Security ? Enroll in ACTE’s Cybersecurity Expert Masters Program Training Course Program to Begin Your Adventure Now.
CRC in Error Detection: Applications and Use Cases
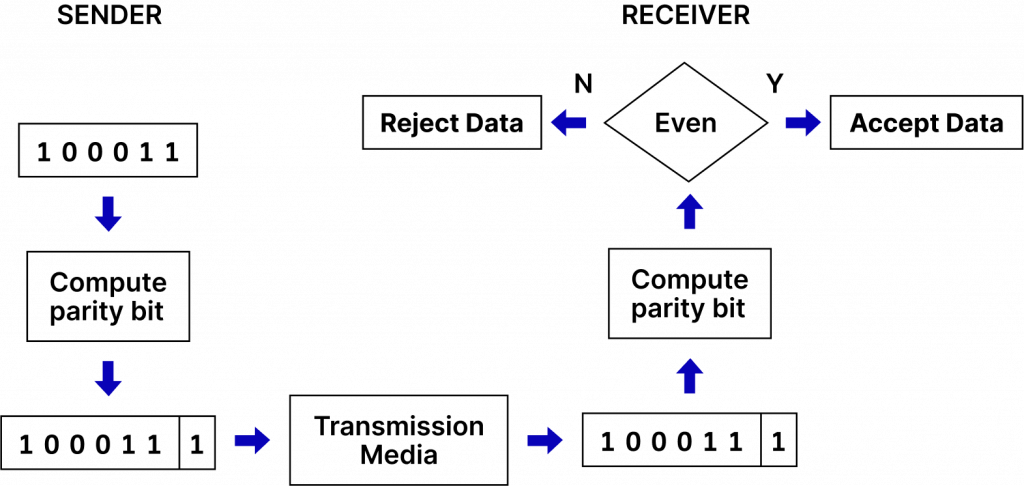
Cyclic Redundancy Check (CRC) is widely applied across multiple domains, making it a versatile and reliable method for detecting errors. In network protocols like Ethernet, Wi-Fi, and HDLC, CRC helps ensure the integrity of packets during transmission over potentially noisy channels. It is also critical in disk and storage systems, such as hard drives, CDs, and DVDs, where CRC checks guarantee that data hasn’t been corrupted during storage or retrieval. In Cybersecurity Training Courses in digital communication systems like satellite, radio, and mobile networks, CRC is used to detect and correct errors in transmitted signals. Embedded systems, especially in IoT devices, rely on CRC to ensure data integrity during interactions between sensors, devices, and central servers. CRC is also commonly applied in software like file compression and archiving tools (e.g., ZIP files) to confirm that files remain unchanged or uncorrupted during transfer or storage. Additionally, CRC plays a crucial role in data transfer protocols such as Frame Relay, ATM, and PPP, verifying the accuracy of data transmission. The benefits of CRC include its high error detection capability, efficiently identifying a wide range of errors, including random, burst, and single-bit errors. It can be computed and verified quickly, making it suitable for high-speed communication systems. CRC is easy to implement in both hardware and software, ensuring its applicability across diverse platforms. Its polynomial-based structure makes CRC reliable and resistant to random errors in digital communication, enhancing overall system integrity.
Preparing for Cyber Security Job Interviews? Have a Look at Our Blog on Cyber Security Interview Questions and Answers To Ace Your Interview!
Types of CRC Algorithms
There are several CRC algorithms, each designed for specific applications and offering different levels of error detection capability in Threat Intelligence . Some of the most common CRC algorithms include:
- CRC-16: It is a 16-bit CRC used in Serial Communication (RS-232, Modbus) and USB protocols. It has an appropriate balance between performance and error-detection capability.
- CRC-32: It is the 32-bit CRC that is extensively used in Ethernet and digital storage technologies such as ZIP files and CD/DVD. CRC-32 is also recognized for detecting errors over longer data streams.
- CRC-64: A 64-bit CRC used in high-accuracy data applications, including file systems (e.g., ZFS) and certain network protocols. It provides more robust error detection but requires more processing power.
- CRC-8: A shorter, 8-bit CRC, often used in embedded systems and simpler communication protocols.
Disadvantages of CRC
Monitoring and logging tools are used to track and record events in real-time, starting from system activities, monitoring user behaviour, and security in encryption in network security. These tools are very effective in detecting, diagnosing, and responding to security incidents toward maintaining operational integrity and compliance by organizations.
Key Features of the CRC:- Limited Error Correction: Although CRC is great at detecting errors, it does not correct them. If the errors are detected, the system has to request retransmission or perform some other corrective measure.
- Complexity with Longer CRCs: With the increase in the length of CRC (e.g., CRC-64), the computational overhead will also increase. This becomes a problem in resource-constraint environments such as in embedded systems.
- Vulnerability to Certain Errors: Although CRC is strong against many errors, it cannot be taken as a failure-proof method. In extremely rare cases, CRC can fail to detect some kinds of mistakes, especially those that are not random or burst errors.
Conclusion
Because of its ease of use, efficacy, and efficiency in identifying data corruption, Cyclic Redundancy Check, or CRC, is one of the most popular error detection techniques in contemporary computing. It is essential for maintaining data integrity in a variety of applications, including storage, embedded systems, networking, and digital communication. Because it offers a dependable and effective way to verify the integrity of data that is saved or sent, CRC is crucial to modern technology. As digital systems develop and expand, Cybersecurity Training will remain a crucial tool for preserving data accuracy and avoiding mistakes in a variety of computing, storage, and communication contexts.





