
- Introduction
- What is Web Security?
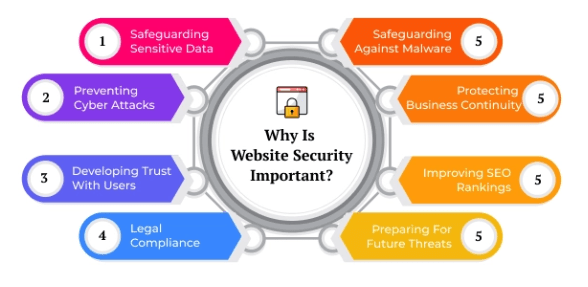
- Why Web Security is Critical
- Types of Web Security Threats
- Web Security Best Practices
- Popular Web Security Tools
- Role of Web Security in SEO and Trust amongst Users
- Challenges in Web Security
- The Future of Web Security
- Conclusion
- Data encryption during the transmission.
- Authentication so that only authorized people can have access to services.
- Regular updates and patches, as these fix known vulnerabilities.
- There must be monitoring and logging for suspicious activities with swift responses.
- Protection of Sensitive Data: Your website contains sensitive data such as usernames and passwords, payment details, and personal information. If these data are breached, it may lead to identity theft, financial loss, and great damage to your reputation.
- Maintaining Business Reputation: Company reputations are damaged along with customer trust. Due to cyberattacks, data leaks, and website downtime, reputations suffer the loss of customers and revenue.
- Regulatory Compliance: An organization that possesses or processes personal data has obligations to comply with legislation like GDPR, PCI-DSS, and HIPAA regarding stringent security best practices. Non-compliance will attract enormous fines and legal proceedings.
- Loss Prevention: A DDoS or ransomware attack can incur severe financial loss, either through theft or recovery and damage control.
- Stored XSS: The client-side script is stored on the server and loaded whenever the user opens the page.
- Reflected XSS: URL parameters reflect The client side script to the user from the server.
- DOM-based XSS: This attack is where the attacker manipulates the Document Object Model in the client’s browser.
- Evolving Threats: Cyberattacks evolve rapidly, making it increasingly difficult to predict what is next. To combat this dynamic threat landscape, Firewall and Antivirus Software are essential tools in any security strategy.
- Resource Limitations: The resources or people experienced enough to implement the necessary security measures are only available for most companies.
- Third-Party Risk: Websites rely heavily on third-party services and plugins. This introduces vulnerabilities if not properly secured.
Introduction
The digital world is expanding rapidly, and more than ever, it calls for information security measures for websites and cyber network security. From internet banking and shopping to social media and healthcare, the internet is a treasure trove of sensitive personal and financial information frequently targeted by cybercriminals. To protect this data, Web Application Security plays a crucial role in safeguarding online platforms from attacks such as SQL injection, cross-site scripting (XSS), and other vulnerabilities. In this blog post, we are going to talk about the basics of web security, why it matters so much, and review common threats, best practices, and tools that you can use to help protect web applications. Whether you are a business owner, a developer, or an IT computer network security professional, knowing how to secure websites is essential for user safety and the kind of trust built within the organization.
Are You Interested in Learning More About Web Security? Sign Up For Our Cyber Security Online Training Today!
What is Web Security?
Web security in network security is a practice that protects websites, web applications, and online services from various Cyber Security Training Courses. It also secures infrastructure, proper authentication, user data protection, and closing vulnerabilities in both server-side and client-side code.
A safe website ensures that the information is shared between the users and the server and the platform is protected. That ranges from encrypting sensitive information to access control over a website’s backend systems. The main parts of web security include:
Why Web Security is Critical
Types of Web Security Threats
Web applications are prone to many different security attacks. Among common types of website attacks, the following categories are worth mentioning: SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF). Additionally, Ransomware in Cybersecurity has become an increasingly prevalent threat, where attackers encrypt sensitive data and demand a ransom for its release.
1. Cross-Site Scripting (XSS)
Cross-site scripting, known as XSS, happens when malicious code is injected onto a webpage by an attacker executed on the browser of all users who view the pages embedding malicious scripts. This may result in session cookie stealing, man-in-the-middle attacks where data is modified, or redirect victims to malware websites. XSS attacks are generally categorized into
2. SQL Injection
SQL injection (SQLi) occurs when the attacker injects the web application with malicious SQL code in its input field. This will enable access to or modification of the site’s database. The criminal can steal sensitive data, remove records, or gain full control of the database. Practices to evade SQLi include parameterized queries, prepared statements, and input validation.
3. Cross-Site Request Forgery (CSRF)
Cross-Site Request Forgery Cross-site request Forgery (CSRF) tricks users into making unintended actions on a site they’ve already authenticated to. The attack type can, for example, be carried out by changing an account setting, making unauthorized transactions, etc., without the user’s consent. CSRF should thus be prevented. This is achieved by implementing anti-CSRF tokens, using secure HTTP methods such as POST, and validating requests properly.
Interested in Obtaining Your Web Security Certificate? View The Cyber Security Online Training Offered By ACTE Right Now!
4. Man-in-the-Middle Attacks
An MITM attack occurs when the hacker intercepts and alters communications between a user and a web server. This may expose sensitive data or compromise transactions. The best way to stop this MITM attack is to ensure that proper encryption is used to transmit the data over HTTPS.
5. Distributed Denial-of-Service (DDoS) Attacks
DDoS attacks create an excessive traffic overflow on the server, making the website inaccessible to its users. Such attacks lead to downtime, loss of revenues, and damage to the company’s reputation. Protecting against such DDoS attacks typically involves measures like anti-DDoS services, rate limiting, and load balancing, which manage the amount of traffic received by the site.
Web Security Best Practices
To minimize the opportunities of a successful attack, web developers and companies should adopt a list of best practices aimed at securing their websites:
1. Use HTTPS
Everyone visiting a website always communicates in a way that is encrypted with the website instead of HTTP. Using HTTPS, this form of protection against an attack on data being sent so that it would not be intercepted and altered by any attacker can be provided. You must have SSL/TLS certificates to enable HTTPS on your website.
2. Use Strong Authentication
Authentication is very important to deny access to certain website sections only for valid users. MFA involves a combination of more than a password for logging in to the system. Furthermore, using strong passwords and properly managing secure sessions exist, and not using default credentials should be avoided altogether. Strong authentication includes all these aspects. In addition, adopting Zero Trust Security is crucial.
3. Input Validation
Poor input validation results in many security vulnerabilities, such as SQL injection and XSS. Validate and sanitize all user inputs to prevent malicious code or unexpected data from getting into the application. Whitelisting, escaping characters, and strict type checks will also prevent malicious input from being processed.
4. Regular Software Patching
Most vulnerabilities occur due to old software and non-patched systems. To prevent attackers from using known vulnerabilities, you must update all aspects of your application to prevent attackers from using servers. Schedule periodic updates and patches for your website.
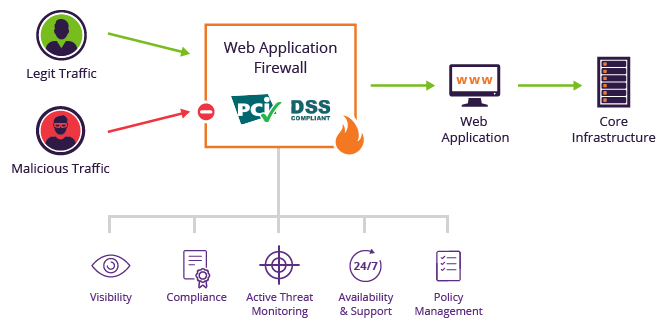
5. Web Application Firewalls (WAF)
A WAF can filter and monitor HTTP traffic, blocking malicious attacks such as SQL injections, XSS, and DDoS attacks. Inbound traffic is inspected against the web server; a WAF will block harmful requests and prevent attacks.
Popular Web Security Tools
1. OWASP ZAP
OWASP ZAP is a free, open-source security tool for identifying flaws in web applications. It supports both automated scanning and manual testing, making it one of the great penetration testing tools.
2. Burp Suite
Burp Suite is integrated with a suite of tools that perform web application security testing. It features scanning, crawling, and vulnerability analyzers, and it ranks among the most used tools by security researchers and penetration testers. In the context of Vulnerability Management, Burp Suite helps identify, assess, and prioritize vulnerabilities within web applications, allowing organizations to address security weaknesses before they can be exploited by attackers.
3. The Wireshark
A network protocol analyzer called Wireshark records and analyzes all computer network traffic. It moves data along a network to detect unprotected traffic and vulnerabilities.
Role of Web Security in SEO and Trust amongst Users
Web security guards against Cyber Security Training Courses but is also significant for SEO rankings and user trust. Websites that set up HTTPS and are concerned with the security of users’ data will rank better on the Web, given that Google values security as part of its ranking algorithm. Moreover, users would be more trusted to use websites that display features such as SSL certificates and secure login procedures.
Are You Considering Pursuing a Master’s Degree in Cybersecurity? Enroll in the Cyber Security Expert Masters Program Training Course Today!
Challenges in Web Security
Despite all the good practices and tools, web security is undoubtedly one of the most challenging areas to be caught up with, particularly:
Future of Web Security
Using cutting-edge technology like artificial intelligence and machine learning and the increase in the demand for Zero-Trust Security models, future web security will surely turn the tables. Stronger, more proactive security strategies will be in greater demand as cyber threats become sophisticated. Expect AI-based tools for threat detection to be much more widespread; authentications further strengthened, and better communication protocols.
Preparing for a Cyber Security Job Interview? Check Out Our Blog on Cyber Security Interview Questions and Answers
Conclusion
As lifestyles incorporate the Web, securing your website and web applications is no longer optional but a must. You will be able to protect your users and businesses from Cyber Security Training Courses once you know the common threats and best practices against them and use the right tools. Proper measures will allow you to build a safer, more trustworthy online presence and ensure that your website’s functionality will continue serving its users securely for years to come.





