
- Introduction to Network Security Keys
- What is a Network Security Key?
- Why Do You Need a Network Security Key?
- How Does a Network Security Key Work?
- Types of Network Security Keys
- Common Mistakes to Avoid
- Advantages of Network Security Keys
- Best Practices for Network Security Key Management
- How to Set Up a Network Security Key
- Conclusion
Network security keys are cryptographic keys used to secure communication within a network by ensuring that only authorized users or devices can access it. They play a vital role in protecting data from unauthorized access, tampering, and interception. The primary benefits of network security keys, as covered in Cyber Security Training Courses, include enhancing confidentiality, ensuring data integrity, and preventing unauthorized network access. Types of network security keys include WPA (Wi-Fi Protected Access) and WPA2 for wireless networks, which secure Wi-Fi connections, as well as SSL/TLS certificates for encrypting web traffic. Additionally, public and private key pairs in asymmetric encryption are commonly used for secure communications, such as in VPNs and email encryption.
To Earn Your Network Security Keys Certification, Gain Insights From Leading Cyber Security Experts And Advance Your Career With ACTE’s Cyber Security Online Training Today!
Introduction to Network Security Keys
In today’s connected world, securing a network is paramount to ensure the privacy and safety of your data. It may be your home Wi-Fi network or enterprise-level network, but protecting your digital information from unauthorized access is the need of the hour. Among the primary tools for securing any network is a Network Security Key. In this blog, we’ll explore what a network security key is, how it works, the different types, and how to manage it effectively to protect your data and prevent cyber threats, including DDoS Mitigation strategies to safeguard against distributed denial-of-service attacks.
What is a Network Security Key?
A network security key is a password or passphrase used to secure wireless networks, such as Wi-Fi. As you set up a wireless network, you may choose a security key that has to be entered by anyone attempting to connect to your network. The key is a gatekeeper that ensures only authorized devices join the network. In a nutshell, a network security key is a form of encryption that prevents unauthorized users from accessing your network and the sensitive data it transmits. It also protects the data being sent over the network by encrypting it so that even if someone intercepts it, they cannot easily read or manipulate it.
Why Do You Need a Network Security Key?
A network security key is important because it:
- It prevents unauthorized access One should make sure that people with the right key access your network and prevent many unauthorized devices to connect.
- It secures data transmission. Since encryption of data, the security key prevents intercepted or accessed data by evil performers. Understanding Hashing vs. Encryption is crucial in this context, as both methods protect data, but encryption ensures confidentiality, while hashing ensures data integrity.
- Protects Privacy With an effective network security key, it guards personal or business data and keeps it safe from cyber attacks, eavesdropping, hacking, or man in the middle.
- Without a robust network security key, anyone within your Wi-Fi signal’s range may be able to get into your network, thereby leading to some of the serious privacy and security risks. It can lead to stolen data, hacking, and compromising online activities.
How Does a Network Security Key Work?
A network security key encrypts communication between a device such as your laptop or smartphone and the router or access point. In other words, for any device trying to join a network, it needs to authenticate itself to the router with a security key. When it correctly inputs the key, it can join the network. The security key also encrypts the data transmitted over the network. If the communication gets intercepted, even the interceptor won’t be able to easily read it without the right decryption key. It ensures the secure encryption and decryption of both sender and receiver data, making sure that they have privacy and integrity.
Are You Interested in Learning More About Network Security Keys? Sign Up For Our Cyber Security Online Training Today!
Types of Network Security Keys
There are several forms of network security protocols, all providing different forms of protection to your wireless network. Here are the most commonly found types:
WEP-Wired Equivalent PrivacyWEP was the first security protocol that was employed to protect the Wi-Fi network. It is a protocol used to provide some form of security close to that of wired networks by encrypting data. However, WEP is already an outdated method and is not secure anymore.
- Strength: Weak security
- Encryption Type: RC4
- Vulnerabilities: WEP has serious vulnerabilities, including weak encryption and susceptibility to attacks that can quickly crack the encryption key.
Because of its weaknesses, WEP has been largely replaced by more secure protocols like WPA and WPA2. It is recommended to avoid using WEP for modern networks, as it is particularly vulnerable to attacks like the Dictionary Attack, where attackers can easily guess encryption keys based on common word combinations.
WPA (Wi-Fi Protected Access)WPA was made available to replace WEP, and it offered much more strenuous security to the Wi-Fi networks as compared to WEP. It uses an advanced encryption protocol known as TKIP (Temporal Key Integrity Protocol) to protect data.
Moderate Security- Encryption Types: TKIP
- Weaknesses: With WPA, even though attacks are way lesser than those of WEP; it is still not as safe as WPA2 and WPA3.
WPA was an important step towards Wi-Fi security but is outdated now and only used in limited situations.
WPA2WPA2 is the most commonly used wireless security protocol as of today, offering much greater security than both WEP and WPA. It uses an AES encryption mechanism that is highly robust.
- Strength: Strong Security
- Encryption Type: AES
- Vulnerabilities: Although WPA2 is much more secure than its predecessors, there have been some vulnerabilities found over time. However, it remains a solid choice for home and business networks.
WPA2 is the default choice for most modern routers, and it is highly recommended for securing your network.
WPA3WPA3 is the latest security protocol for Wi-Fi, which has better protection compared to WPA2. Some of the features include strong encryption, prevention against brute-force attacks, and greater privacy in open networks.
- Strength: Extremely secure
- Encryption Type: AES
- Vulnerabilities: WPA3 is the most secure protocol in terms of recent threats and attacks. It is still a relatively new technology, and its support is not seen on all devices or routers.
WPA3 is highly advised for the highest network security. It should be used when handling sensitive information.
Common Mistakes to Avoid
Avoid using simple or default passwords like “password123” or your router’s default key. These can be easily cracked. Ensure that your router’s firmware is updated regularly to patch any vulnerabilities. Always enable WPA2 or WPA3 encryption to protect your network and data from hackers. Cyber Security Training Courses teach best practices like these to help individuals and organizations secure their networks effectively.
Advantages of Network Security Keys
There are many advantages associated with a network security key, such as:
- Maximum Safety
- Prevention of Unauthorized Access
- Data Encryption
- Compliance with Security Standards
- Access Router Settings: Log into your router’s admin panel using its IP address (typically something like 192.168.1.1).
- Navigate to Wireless Settings: Find the section related to wireless or Wi-Fi settings.
- Select a Security Protocol: Choose WPA2 or WPA3 for the best security. Avoid using WEP or WPA if possible.
- Create a Strong Network Key: Provide a strong password or passphrase. The key should be at least 12-16 characters long and have a mix of letters, numbers, and special characters.
- Save and Connect: Save the settings, and your Wi-Fi network will now be protected by the newly set network security key.
A secure network key protects your Wi-Fi network by preventing unauthorized access. Only the devices that are furnished with the correct key can gain access to your network and help protect your data and networking infrastructure from cyber hackers.
A great network security key prevents anyone in the range of your Wi-Fi signal from hooking up to the network. That means reducing malicious attack possibilities, unauthorized usage of data, and even theft of private information.
Network security keys encrypt the information that is being transmitted over the network, thus securing data transmission. This means that even if data is intercepted, it cannot be read without the proper decryption key. Encryption secures sensitive data, such as passwords, credit card details, and personal communications.
Many businesses need their networks to meet certain standards of security, such as HIPAA, PCI-DSS, or GDPR. Using a secure network key, like WPA2 or WPA3, will go a long way toward ensuring your network is compliant.
Looking to Master Cybersecurity? Discover the Cyber Security Expert Masters Program Training Course Available at ACTE Now!
Best Practices for Network Security Key Management
To ensure the security of your network, it is important to use a long and complex password that includes a combination of letters, numbers, and special characters. This makes it much harder for attackers to guess or crack the password using brute-force methods. Additionally, regularly changing your security key enhances protection, ensuring that even if someone gains unauthorized access, they won’t retain access for long. It’s also crucial to be cautious about sharing your network key; only share it with trusted individuals and avoid writing it down in places where it can be easily discovered.
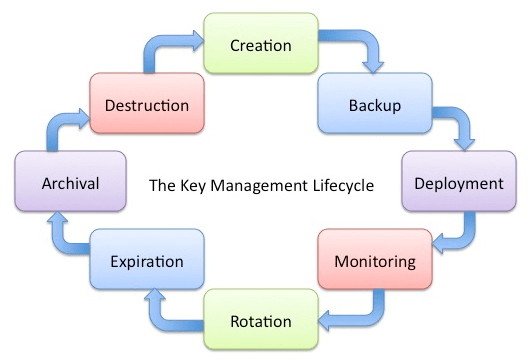
For added security, consider setting up a separate guest network with its own unique security key if you want to allow visitors to connect to your Wi-Fi. This helps limit potential exposure to Cryptanalysis, ensuring that any weaknesses in your main network’s encryption are isolated from guest users. This prevents guests from accessing sensitive areas of your network while still enabling them to use the internet. Keeping your primary network’s security key private and using a guest network for visitors reduces the risk of unauthorized access and maintains the integrity of your network’s security.
How to Set Up a Network Security Key
Configuring a network security key is often pretty straightforward and is usually found within your router settings. The following are the general steps, and it’s a good practice to perform VAPT on your network periodically to identify any potential security risks before they can be exploited.
Preparing for Cyber Security Job Interviews? Have a Look at Our Blog on Cyber Security Interview Questions and Answers To Ace Your Interview!
Conclusion
A network security key is an element that protects your Wi-Fi network and sensitive information from unauthorized access and cyber attacks. With proper security protocol set up, using WPA2 or WPA3, with best practices management and setup in your security key, you enhance the security on your network a lot and help keep your information safe. Remember, having a strong security key to protect your network is probably one of the easiest but very effective means by which to guard your personal and business life information from a probable attack. Cyber Security Training Courses emphasize the importance of strong security keys in safeguarding sensitive data and preventing unauthorized access. In addition to using strong and complex security keys, it’s important to stay informed about emerging threats and regularly update your security practices. As cyber threats evolve, so do the tools and techniques used to bypass weak security measures. Enabling features like automatic updates for your router’s firmware and ensuring that your network devices are up to date with the latest security patches are critical steps in keeping your network secure. Regularly auditing your security settings, monitoring network traffic, and educating everyone in your household or organization about safe network practices are also essential components of maintaining a robust defense against cyber attacks. By staying proactive and committed to good security hygiene, you significantly reduce the chances of a successful breach.





