
- Definition and Importance
- How MFA Works
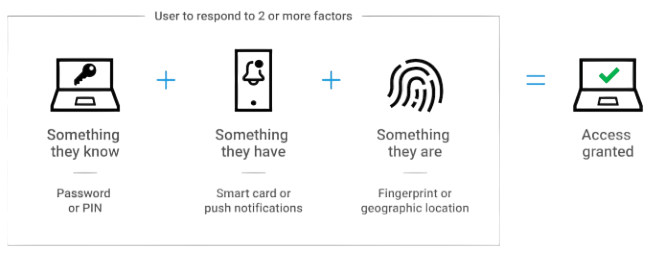
- Factors Used in MFA
- MFA vs 2FA
- Common MFA Methods
- MFA in Cloud and Enterprise Environments
- Benefits of Using MFA
- Conclusion
Definition and Importance
Multi-Factor Authentication, commonly known as MFA, is a security method used to verify a user’s identity by requiring two or more independent credentials from different categories. These credentials fall into three primary types: something the user knows, something the user has, and something the user is. The first category, something the user knows, typically includes passwords, PINs, or answers to security questions. The second category, something the user has, consists of physical devices such as security tokens, smart cards, or mobile devices that generate one-time passcodes. The third category, something the user is, involves biometric factors like fingerprints, facial recognition, or iris scans in Cyber Security Training. By combining these different types of credentials, MFA adds multiple layers of security that make it much more difficult for unauthorized individuals to gain access to user accounts or sensitive systems. The importance of MFA lies in its ability to reduce the risk of account compromise significantly. If a malicious actor manages to obtain one factor, such as a password through phishing or other means, they would still be unable to access the account without the additional authentication factors. This extra step greatly improves security compared to relying solely on passwords, which can be stolen, guessed, or reused across different sites. MFA is widely adopted across various industries and is especially critical for protecting sensitive information, financial systems, and enterprise networks. It also helps organizations comply with regulatory requirements and cybersecurity best practices. As cyber threats continue to increase in complexity, implementing MFA is an essential part of a comprehensive security strategy, providing strong protection against unauthorized access and safeguarding both personal and organizational data.
Are You Interested in Learning More About Cyber Security? Sign Up For Our Cyber Security Online Training Today!
How MFA Works
The basic functioning of Multi-Factor Authentication (MFA) revolves around a series of identity verification steps designed to enhance security beyond traditional password-only systems. When a user attempts to log in to a system or application, the first step typically requires them to enter their username and password in Top Ethical Hacking Certifications. This initial step confirms something the user knows, but by itself, it is often insufficient to prevent unauthorized access because passwords can be compromised through phishing, brute force attacks, or data breaches. To address these vulnerabilities, MFA introduces additional layers of verification, requiring users to provide at least one more form of identification before access is granted. After successfully entering the username and password, the system prompts the user for a second factor.
This second factor can take various forms depending on the MFA setup. One common method is a one-time password (OTP) generated by an authenticator app or sent via SMS to the user’s mobile device. This OTP is valid only for a short period and can be used only once, which greatly reduces the risk of interception or reuse by attackers. Another method involves biometric authentication, such as fingerprint scanning, facial recognition, or voice recognition, which relies on unique physical characteristics of the user. Some systems may also use hardware security keys or smart cards that the user must physically possess. Only after the user successfully provides and validates all the required authentication factors does the system grant access to the requested resource or account. This layered defense strategy significantly increases security by making it much more difficult for cybercriminals to bypass multiple barriers, protecting sensitive information and systems from unauthorized access even if one factor is compromised.
Factors Used in MFA
- Something You Know: This includes passwords, PINs, or answers to security questions. It is the most common form of authentication but also the most vulnerable, as it can be guessed, stolen, or leaked.
- Something You Have: This refers to physical objects the user possesses, such as a smartphone, hardware token, smart card, or USB security key. These are used to generate or receive one-time codes or digital certificates for authentication.
- Something You Are: This factor uses biometric characteristics unique to the individual, such as fingerprints, facial recognition, iris scans, or voice patterns in Tips to Clear Certified Ethical Hacker CEH Exam.
- Somewhere You Are: This factor considers the geographic location of the user, determined by GPS or IP address. Access may be restricted based on whether the login is occurring from a trusted location or region.
- Something You Do: This behavioral factor includes patterns such as typing speed, mouse movement, or how a user typically interacts with a device. It adds a layer of continuous authentication by monitoring user behavior.
- Time-Based Factors: Access may be granted or denied based on the time of day. For example, login attempts during normal working hours might be allowed, while after-hours access may trigger additional verification.
- Risk-Based or Adaptive Factors: These systems analyze context, such as device reputation, login history, or network used, to assess risk and decide if additional authentication steps are necessary.
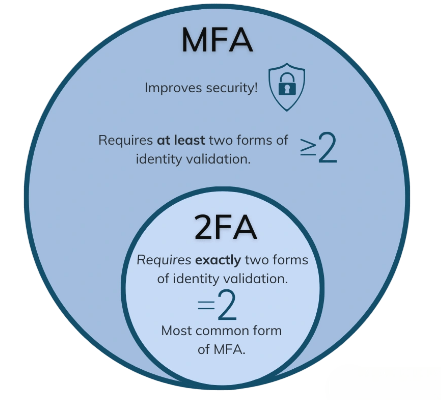
- Definition of 2FA: Two-Factor Authentication (2FA) involves using exactly two different authentication factors to verify a user’s identity. These factors typically come from two separate categories such as something you know and something you have.
- Definition of MFA: Multi-Factor Authentication (MFA) is a broader term that refers to using two or more different factors to authenticate a user in Cyber Security Training. While 2FA is a type of MFA, MFA is not limited to only two factors.
- Example of 2FA: A common example of 2FA is logging in with a password (something you know) followed by a one-time passcode (OTP) sent to a mobile device (something you have).
- Example of MFA: MFA may involve three or more layers, such as a password, an OTP, and a biometric scan like a fingerprint. This combination adds extra layers of protection, especially for sensitive systems or data.
- Security Strength: While 2FA significantly improves security over single-factor authentication, MFA offers a more robust defense by adding additional authentication steps, reducing the risk of unauthorized access even further.
- Use Cases: 2FA is commonly used for consumer applications like email, banking, and social media. MFA is often required in high-risk environments such as corporate networks, healthcare systems, and government platforms.
- Key Distinction: All 2FA is a form of MFA, but not all MFA is 2FA. MFA allows for more than two factors, offering a higher level of security and flexibility depending on the risk profile and organizational needs.
- Rising Dependence on Cloud Services: As businesses increasingly migrate their operations and data to cloud platforms, ensuring secure access becomes a top priority. Cloud computing has expanded the threat landscape, making strong authentication essential.
- Need for Stronger Authentication: Cloud environments are often accessible from anywhere, which increases exposure to potential cyber threats. Multi-Factor Authentication (MFA) adds a critical layer of protection beyond traditional passwords.
- Integration with Major Platforms: Leading cloud service providers such as Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform (GCP) offer built-in MFA features. These are used to secure user logins, admin consoles, and high-privilege accounts.
- Protection for Admin Access: Admin accounts hold elevated permissions and are frequent targets for attackers in Cyber Security Career Path. Enabling MFA on these accounts helps prevent unauthorized access and protects sensitive infrastructure configurations.
- Enterprise Applications and Services: In a business setting, MFA is widely used to secure access to virtual private networks (VPNs), internal tools, file storage, and enterprise email systems like Microsoft 365 or Google Workspace.
- Support for Remote Work: With remote work becoming standard, MFA ensures that employees logging in from various locations and devices are properly verified. This helps maintain a consistent security posture regardless of where users are located.
- Regulatory and Policy Compliance: MFA is often a requirement under security standards and compliance frameworks such as ISO 27001, NIST, and CIS Controls. It helps organizations meet these guidelines and reduce overall risk.
To Explore Cybersecurity in Depth, Check Out Our Comprehensive Cyber Security Online Training To Gain Insights From Our Experts!
MFA vs 2FA
Common MFA Methods
Multi-Factor Authentication (MFA) employs various methods to verify a user’s identity by requiring multiple forms of authentication. Among the most widely adopted MFA methods are one-time passwords, biometrics, push notifications, hardware tokens, and smart cards. One-time passwords, or OTPs, are temporary codes sent to users via SMS, email, or generated through authenticator apps such as Google Authenticator or Microsoft Authenticator. These codes typically expire after a short time and are valid for a single use, providing a secure way to confirm identity beyond just a password. OTPs are popular because they are easy to implement and use, though their security depends on the delivery method and device protection. Biometric authentication methods rely on unique physical traits of the user to verify identity in Why is Cybersecurity Important. Common biometric factors include fingerprint scanners found on many smartphones, facial recognition technologies, voice recognition systems, and iris scans. These methods provide strong security because biometric traits are difficult to replicate or steal, and they offer a convenient, user-friendly experience without the need to remember additional passwords or carry extra devices. Push notifications represent another popular MFA method. When a login attempt is made, the user receives a prompt on their registered mobile device asking them to approve or deny access. This method allows users to quickly confirm their identity with a single tap, making it both secure and convenient. Hardware tokens are physical devices that generate time-based codes, usually changing every 30 to 60 seconds. Users enter these codes during login as an additional authentication factor. Similarly, smart cards embedded with chips are inserted into readers to verify the user’s identity. These are commonly used in corporate environments for secure access to buildings and computer systems. Each MFA method offers different advantages, and many organizations combine several to balance security with ease of use.
Want to Pursue a Cyber Security Master’s Degree? Enroll For Cyber Security Expert Master Program Training Course Today!
MFA in Cloud and Enterprise Environments
Benefits of Using MFA
Multi-Factor Authentication (MFA) offers a wide range of advantages that make it an essential component of modern cybersecurity strategies. One of the primary benefits is enhanced security. By requiring users to provide multiple forms of identification, MFA significantly reduces the chances of unauthorized access to sensitive systems and data. Even if one factor, such as a password, is compromised, the additional layers of authentication act as strong barriers against cybercriminals. This added protection is especially important in today’s environment, where password breaches and phishing attacks are common. Another key advantage of MFA is compliance with regulatory requirements. Many data protection laws and industry standards, such as the General Data Protection Regulation (GDPR), the Health Insurance Portability and Accountability Act (HIPAA), and the Payment Card Industry Data Security Standard (PCI-DSS), mandate the implementation of strong access controls in Hash in Python. MFA helps organizations meet these requirements by providing documented, robust authentication processes that reduce risk and demonstrate due diligence during audits. MFA also plays a vital role in reducing fraud. By requiring more than one authentication factor, it helps prevent identity theft and financial fraud, which can have severe consequences for both individuals and businesses. Users benefit from increased confidence in the security of the systems they access, fostering trust and encouraging safer online behavior. In addition, MFA supports the enablement of remote work and Bring Your Own Device (BYOD) environments. As workforces become more distributed, securing access from various locations and devices is critical. MFA safeguards these flexible working arrangements by ensuring that only authorized users can gain entry, regardless of their location or device. Overall, MFA strengthens security, supports compliance, and enhances user trust across multiple contexts.
Are You Preparing for Cyber Security Jobs? Check Out ACTE’s Cyber Security Interview Questions and Answers to Boost Your Preparation!
Conclusion
Multi-Factor Authentication (MFA) has become a critical component of modern cybersecurity strategies due to its ability to provide a strong layer of defense against unauthorized access and data breaches. Unlike traditional authentication methods that rely solely on passwords, MFA requires users to verify their identity through multiple independent factors. This approach greatly reduces the risk of account compromise, as attackers would need to bypass several security barriers rather than just one. With the increasing frequency and sophistication of cyber threats such as phishing, credential stuffing, and ransomware attacks, organizations are recognizing that passwords alone are no longer sufficient to protect sensitive information and systems. Moreover, the regulatory landscape is evolving to reflect these security challenges in Cyber Security Training. Laws and standards including GDPR, HIPAA, PCI-DSS, and others are placing greater emphasis on the implementation of strong access controls to safeguard personal and financial data. As a result, MFA adoption is rapidly shifting from being an optional security enhancement to a mandatory requirement for many organizations, especially those operating in regulated industries. This shift highlights the importance of MFA not only for improving security but also for maintaining compliance and avoiding costly penalties. Despite its benefits, organizations must carefully balance security with user experience to ensure that MFA does not become a barrier to productivity or convenience. Selecting the right combination of authentication factors and keeping pace with emerging technologies such as biometric verification, adaptive authentication, and risk-based access controls are crucial for achieving this balance. By investing in MFA and continuously updating their security practices, organizations can better protect their digital assets, build user trust, and stay resilient against the ever-changing threat landscape.




