
- Importance of Cybersecurity Education
- Criteria for Book Selection
- Cybersecurity and Cyberwar by P.W. Singer
- The Art of Invisibility by Kevin Mitnick
- Hacking: The Art of Exploitation by Jon Erickson
- Network Security Essentials by William Stallings
- Security Engineering by Ross Anderson
- Blue Team Field Manual (BTFM)
Importance of Cybersecurity Education
In today’s digital-first world, the importance of cybersecurity education cannot be overstated. As cyber threats grow in complexity and frequency, it is essential for individuals, students, and professionals alike to understand the fundamentals of protecting sensitive data and digital infrastructure. Cybersecurity education equips learners with the knowledge to identify vulnerabilities, respond to incidents, and build secure systems, making it a critical component in both personal and professional development. For those starting their journey, exploring books for cyber security beginners offers a solid foundation in key concepts such as malware, phishing, ethical hacking, and serves as a valuable supplement to Enroll Our Cyber Security Training Additionally, delving into Network security books helps readers gain insight into securing communications, firewalls, and intrusion detection systems. For a more comprehensive understanding, many experts recommend diving into some of the Best Cyber Security Books that cover a wide range of topics from cyber law to advanced threat intelligence. These resources not only enhance technical skills but also foster a security-first mindset essential in today’s interconnected world. Whether you are pursuing a career in IT or simply aiming to protect your personal devices, investing time in cybersecurity education through trusted books is a smart and necessary step in safeguarding the future.
Interested in Obtaining Your Cybercrime Certificate? View The Cyber Security Online Training Offered By ACTE Right Now!
Criteria for Book Selection
- Author Expertise: Ensure the book is written by a trusted industry expert with real-world experience in safeguard cyber practices and threat mitigation.
- Up-to-Date Content: Cyber threats evolve rapidly; always opt for books with recent editions that reflect current trends in web security, defense strategies, and topics like What Is Cyber Trolling Internet safety to stay well-informed.
- Comprehensive Coverage: A good book should cover various areas such as network security, malware analysis, and risk assessment to provide a well-rounded perspective.
Choosing the right book to deepen your understanding of cybersecurity is essential, especially with the vast number of resources available today. Whether you’re a beginner or looking to expand your expertise, selecting the right Cyber Security E Book or printed guide requires thoughtful consideration. From web security books to titles focusing on network security and cyber awareness, the quality and relevance of your material can significantly impact your learning journey. Here are six key criteria to consider when selecting a cybersecurity book:
- Target Audience Fit: Choose books that match your skill level whether you’re a beginner or an advanced reader looking for in-depth cyber awareness insights.
- Practical Examples and Case Studies: Look for content that includes real-world scenarios to better understand how cybersecurity applies in practice.
- Reviews and Recommendations: Always check reviews or expert recommendations to ensure the Cyber Security E Book or print edition is credible and widely respected.
Cybersecurity and Cyberwar by P.W. Singer
Cybersecurity and Cyberwar by P.W. Singer and Allan Friedman is a compelling and accessible read that explores the complex world of digital threats, making it a standout among the Best Cyber Security Books available today. This book breaks down the technical jargon and presents real-world scenarios in a way that is easy to understand, making it one of the top Books for cyber security beginners. It provides a deep dive into how cyber conflicts impact global politics, national security, and individual privacy, offering readers an eye-opening look at the unseen battles happening across the internet, while also emphasizing essential practices like those found in a Guide To Multi-Factor Authentication. The authors blend expert insight with engaging storytelling, helping readers grasp the critical role of cybersecurity in modern society. Whether you’re interested in the evolution of cybercrime, government surveillance, or the vulnerabilities in digital infrastructure, this book covers it all. Its well-researched content also positions it as a valuable addition to any collection of Network security books, bridging the gap between technical detail and strategic understanding. Ideal for students, professionals, or anyone curious about the digital world’s hidden threats, Cybersecurity and Cyberwar equips readers with the knowledge and awareness needed to navigate and defend in an increasingly connected age.
To Explore Cybersecurity in Depth, Check Out Our Comprehensive Cyber Security Online Training To Gain Insights From Our Experts!
The Art of Invisibility by Kevin Mitnick
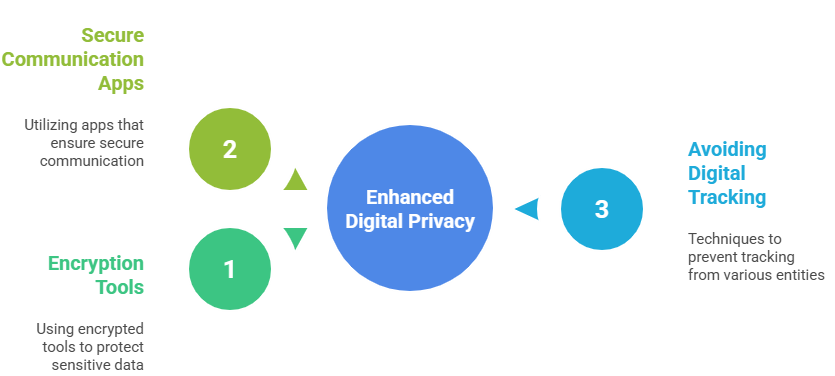
- Online Privacy Fundamentals: The book teaches how to mask your digital footprint, a critical skill in today’s surveillance-heavy environment.
- Using Encryption: Mitnick explains how to use encrypted tools and secure communication apps to protect sensitive data, making it a valuable addition to any cyber security training program.
- Avoiding Digital Tracking: It highlights techniques to avoid tracking from websites, advertisers, and even governments.
The Art of Invisibility by Kevin Mitnick, one of the world’s most famous former hackers, is a powerful guide to maintaining privacy and anonymity in the digital age. This Cyber Security E Book is essential reading for anyone concerned about data security, surveillance, and how to safeguard cyber identity in a world where every move online can be tracked. With practical tips and real-world examples, Mitnick offers readers actionable advice on achieving true cyber awareness. Here are six key takeaways from this insightful book:
- Securing Devices: The book provides tips on securing smartphones, computers, and home networks making it one of the most practical web security books available.
- Understanding Network Risks: Readers gain insight into how data can be exposed through unsecured connections, aligning it with top network security concerns.
- Empowering Cyber Awareness: Above all, the book raises awareness about how easily personal information can be exploited and how to proactively prevent it.
- Clear Conceptual Framework: The book presents the fundamentals of network security, including threats, vulnerabilities, and risk management, in an easy-to-understand format.
- Coverage of Key Technologies: It explores essential technologies like firewalls, intrusion detection systems, VPNs, and secure email, making it a practical guide among Network Security Books. The book also delves into the distinctions between Cybersecurity vs. Network Security, helping readers understand how broader digital protection strategies intersect with specific network defense mechanisms.
- Strong Focus on Cryptography: Stallings explains encryption techniques and digital signatures in detail, offering deep insights essential for any Best Cyber Security Books list.
- Real-World Examples: The book integrates real-world case studies that help readers connect theory with practical application ideal for Books for Cyber Security Beginners.
- Review Questions and Exercises: Each chapter includes exercises that reinforce learning, making it a hands-on educational resource.
- Well-Structured Learning Path: Its logical flow from basic to advanced topics supports continuous learning and growth in cybersecurity knowledge.
Hacking: The Art of Exploitation by Jon Erickson
Hacking: The Art of Exploitation by Jon Erickson is a highly respected Cyber Security E Book that delves deep into the technical side of hacking, making it a must-read for anyone serious about understanding how systems can be compromised and protected. Unlike many web security books that focus solely on defensive strategies, this book takes readers inside the hacker’s mindset, explaining how vulnerabilities are discovered and exploited. It covers key concepts such as buffer overflows, memory corruption, and shellcode, blending theory with practical code examples in C, Assembly, and Linux. Erickson’s approach not only enhances technical knowledge but also builds strong cyber awareness by showing how easily common mistakes can lead to security breaches. His work provides crucial insights into Understanding Cybercrime And Its Implications, emphasizing how even minor lapses in digital behavior can escalate into serious vulnerabilities, affecting individuals and organizations alike. This book is especially valuable for those wanting to safeguard cyber infrastructure by learning from the ground up how attackers think and operate. It’s also a great supplement to network security education, offering insights into protocol manipulation and system-level flaws. While not for absolute beginners, it serves as an excellent bridge between foundational knowledge and advanced exploitation techniques. Overall, Hacking: The Art of Exploitation is an essential resource for aspiring ethical hackers, cybersecurity professionals, and curious minds eager to explore the real mechanics behind system attacks and defenses.
Looking to Master Cybersecurity? Discover the Cyber Security Expert Masters Program Training Course Available at ACTE Now!
Network Security Essentials by William Stallings
Network Security Essentials by William Stallings is a foundational text that provides a clear and comprehensive introduction to the key principles of cybersecurity. Widely regarded as one of the Best Cyber Security Books for academic and professional learning, this book simplifies complex concepts and offers practical frameworks, making it especially useful for students and entry-level professionals. For those seeking trusted Books for Cyber Security Beginners, Stallings’ work is a top recommendation due to its structured approach and emphasis on both theory and application. It’s also one of the most referenced Network Security Books in classrooms and training programs. Here are six reasons why this book stands out:
Security Engineering by Ross Anderson
Security Engineering by Ross Anderson is a landmark work in the field of cybersecurity, offering an in-depth exploration of how security systems are built, attacked, and defended. Widely regarded as one of the Best Cyber Security Books ever written, this book goes far beyond the basics, making it ideal not just for professionals but also for dedicated learners aiming to expand their understanding of complex systems. Anderson covers everything from cryptography and secure hardware to system design, biometrics, and security policies, providing a comprehensive view of the discipline. While it may be more advanced than typical Books for Cyber Security Beginners, its clear explanations and real-world examples help bridge the gap between theory and practice. It also serves as a valuable resource for those pursuing credentials like Certified Cloud Security Professional, offering foundational insights that align with the knowledge areas covered in advanced cloud security certifications. It also serves as one of the most cited Network Security Books in academic circles and is frequently recommended in university courses and certification tracks. The book’s emphasis on the economics, psychology, and policy aspects of security adds a unique layer of insight not often found in other cybersecurity texts. For anyone serious about building or analyzing secure systems, Security Engineering is an essential read that equips readers with the analytical tools needed to think critically and defend effectively in a constantly evolving digital landscape.
Preparing for Cyber Security Job Interviews? Have a Look at Our Blog on Cyber Security Interview Questions and Answers To Ace Your Interview!
Blue Team Field Manual (BTFM)
The Blue Team Field Manual (BTFM) is a compact yet powerful Cyber Security E Book designed as a practical guide for defenders in the cybersecurity landscape. Focused on real-time incident response and defense tactics, this manual is ideal for security professionals who operate on the front lines of cyber defense. Unlike theory-heavy resources, BTFM delivers quick, actionable commands and procedures, making it a standout among web security books for hands-on use. Whether you’re managing threats in Windows, Linux, or cloud environments, the book provides step-by-step references that are essential for any blue team member and complement formal cyber security training. It’s also an excellent tool for improving cyber awareness, helping professionals and learners alike identify and mitigate security breaches effectively. As one of the most functional network security resources available, it outlines commands and configurations that can immediately safeguard cyber infrastructure, making it invaluable during emergencies. Though not a beginner’s textbook, it supports those already familiar with the basics by reinforcing defensive practices in a structured, concise format. With its pocket-sized convenience and high-value content, the Blue Team Field Manual is a must-have quick-reference companion for cybersecurity teams, system administrators, and anyone committed to building a stronger, more secure digital environment.




