
- What is Spear Phishing
- How It Differs from Phishing
- Attack Process and Techniques
- Research and Targeting Phase
- Examples of Spear Phishing Emails
- Case Studies (APT Groups)
- Email Authentication Techniques
- Mitigation Strategies
- Role of Security Awareness Training
- Technological Defenses (Spam Filters, DMARC)
- Legal Actions and Compliance
- Summary
What is Spear Phishing
Spear phishing is a highly targeted and deceptive cyberattack technique in which attackers send fraudulent emails or messages to specific individuals or organizations. Unlike generic phishing campaigns that target large groups with the same message, spear phishing is personalized, making it more convincing and dangerous. Attackers often pose as trusted contacts such as a colleague, manager, or vendor and craft messages that appear legitimate, aiming to trick recipients into revealing sensitive information or performing actions like transferring money or clicking malicious links. Learn how to recognize and respond to these social engineering tactics with Cyber Security Training. Spear phishing is commonly used in corporate espionage, data breaches, and advanced persistent threats (APTs). The term “spear phishing” stems from the precision of the attack, much like a spear is targeted at a specific fish. It contrasts with broader phishing attacks, which are akin to casting a net to catch as many victims as possible. Spear phishing attacks rely on information that the attacker gathers about the target, often from publicly available sources or previous data breaches. The personalized nature of these attacks makes them harder to detect and more effective than traditional phishing attempts. As businesses adopt more digital tools, the attack surface expands, increasing the risk of spear phishing campaigns.
Interested in Obtaining Your Cyber Security Certificate? View The Cyber Security Online Training Offered By ACTE Right Now!
How It Differs from Phishing
While spear phishing and phishing share similar goals namely, to steal information or install malware they differ significantly in execution. Phishing attacks are generally broad and automated, often sent to thousands of recipients with a generic message (e.g., claiming to be from a bank or online service). Spear phishing, on the other hand, is precise, targeted, and customized to a specific person or organization. To understand how different security domains address such threats, explore Cybersecurity vs Network Security. This level of personalization makes spear phishing emails more credible and significantly increases the likelihood of success. For example, while a phishing email might say “Dear user,” a spear phishing email might address the target by name and reference recent company activities.
Attack Process and Techniques
Spear phishing attacks typically follow a well-defined process:
- Reconnaissance: The attacker gathers information about the target through social media, public records, company websites, and data breaches.
- Email Crafting: Based on collected information, a realistic and tailored email is created, often mimicking the tone and style of a trusted source.
- Payload Delivery: The email may contain malicious attachments, spoofed links, or requests for sensitive information.
- Exploitation: When the target interacts with the payload such as entering credentials or downloading malware the attacker gains access to systems or data.
- Post-Exploitation: The attacker may maintain access, move laterally within networks, or extract valuable information over time.
Common techniques include email spoofing, domain impersonation, and the use of malware-laced documents or fake login pages.
To Explore Cybersecurity in Depth, Check Out Our Comprehensive Cyber Security Online Training To Gain Insights From Our Experts!
Examples of Spear Phishing Emails
Spear phishing emails often resemble legitimate communications. Here are a few examples:
- CEO Fraud: An employee receives an email that appears to come from the CEO, requesting an urgent wire transfer for a confidential business deal.
- Vendor Impersonation: The finance department gets an email that looks like it’s from a regular supplier, asking for payment to a new bank account. Recognizing and responding to such threats requires a strong foundation in phishing detection, risk analysis, and incident response learn more through Key Skills Required for Cybersecurity Professionals.
- HR Spoofing: An employee receives an email from what appears to be the HR department, asking them to click a link to view their updated benefits policy.
- Credential Harvesting: A staff member is asked to reset their password through a link that leads to a spoofed login page that captures their credentials.
These emails typically include familiar branding, correct names, and tone of voice to reduce suspicion.
Research and Targeting Phase
A critical component of spear phishing is the initial research phase. Attackers often spend significant time gathering intelligence on their targets. They may use LinkedIn to find job titles and work relationships, Facebook for personal interests, and company websites for organizational structure. In some cases, attackers purchase information from underground forums or use breached databases to build accurate profiles. Learn how to protect your data and recognize these advanced tactics through Cyber Security Training. The better the information, the more convincing the phishing attempt. For instance, referencing a recent company project or using a known manager’s email signature can significantly increase credibility.
Looking to Master Cybersecurity? Discover the Cyber Security Expert Masters Program Training Course Available at ACTE Now!
Case Studies (APT Groups)
A critical component of spear phishing is the initial research phase. Attackers often spend significant time gathering intelligence on their targets. They may use LinkedIn to find job titles and work relationships, Facebook for personal interests, and company websites for organizational structure. In some cases, attackers purchase information from underground forums or use breached databases to build accurate profiles. The better the information, the more convincing the phishing attempt. As cyber threats grow more sophisticated, so does the demand for skilled professionals who can detect, prevent, and respond to them. Explore Career Opportunities in Cybersecurity to discover how you can make a meaningful impact in this dynamic field. For instance, referencing a recent company project or using a known manager’s email signature can significantly increase credibility.
Email Authentication Techniques
To combat spoofed emails, several email authentication techniques have been developed:
- SPF (Sender Policy Framework): Validates that the sender’s IP address is authorized to send emails for the domain.
- DKIM (DomainKeys Identified Mail): Uses encryption to verify that the message content has not been altered.
- DMARC (Domain-based Message Authentication, Reporting & Conformance): Aligns SPF and DKIM results with domain policies to detect spoofed emails.
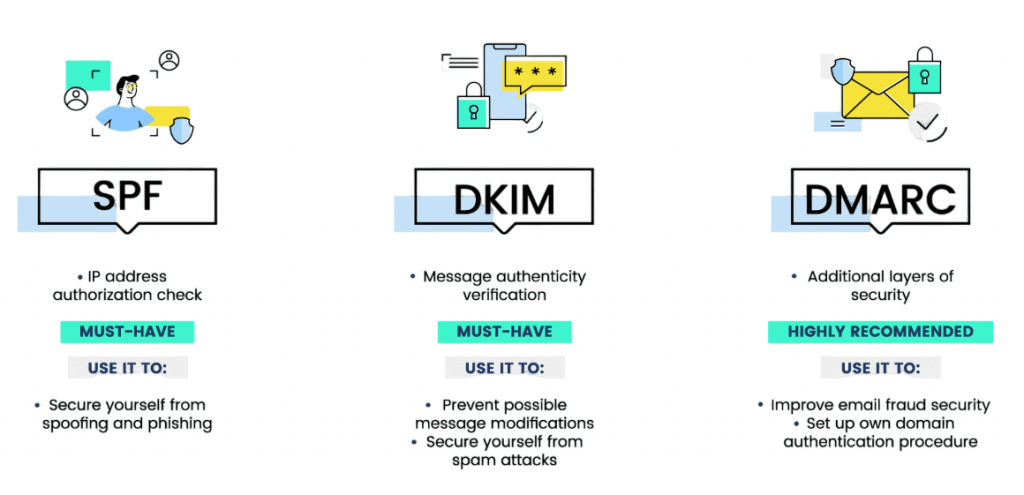
Implementing these protocols helps reduce the success rate of spear phishing by verifying legitimate email senders.
Mitigation Strategies
Mitigating spear phishing requires a multi-layered approach:
- Email Filtering: Use advanced email filters that flag suspicious content, links, and attachments.
- Link Sandboxing: Automatically open and test links in a secure environment before delivering the email to the user.
- Two-Factor Authentication (2FA): Adds an extra layer of security even if credentials are compromised.
- Behavior Monitoring: Use endpoint detection and response (EDR) tools to spot unusual user behavior.
- Regular Updates: Patch vulnerabilities in software to prevent malware installation from successful spear phishing attempts.
Preparing for Cyber Security Job Interviews? Have a Look at Our Blog on Cyber Security Interview Questions and Answers To Ace Your Interview!
Role of Security Awareness Training
One of the most effective defenses against spear phishing is educating users. Security awareness training equips employees to recognize suspicious emails and avoid falling for deceptive tactics. Training typically includes: In today’s digital environment, checking if emails are legitimate is vital for keeping organizations secure. To explore the essential skills, certifications, and career paths in this field, check out Steps to Become a Cybersecurity Professional. Employees need training to spot warning signs, like odd requests or messages full of grammatical mistakes, which often indicate phishing attempts. Running simulated phishing tests can help assess and improve how well staff respond to suspicious emails. It is also important to build a culture that supports open communication. Team members should feel safe reporting potentially harmful emails without worrying about punishment. By mixing proactive education, practical testing, and a clear reporting system, organizations can greatly improve their email security and lower the chances of successful cyber attacks. Well-trained employees act as a human firewall, reducing the likelihood of successful attacks.
Technological Defenses (Spam Filters, DMARC)
Technology plays a vital role in detecting and blocking spear phishing attempts. Spam filters are often the first line of defense, analyzing metadata, content, and attachments to identify threats. More advanced defenses include:
- AI-Powered Detection: Machine learning algorithms that adapt to evolving phishing tactics.
- Secure Email Gateways: Platforms that inspect emails before they reach the inbox.
- DMARC Enforcement: Ensures that only authenticated emails are delivered to users.
- Browser Isolation: Prevents malicious scripts from running by isolating browser activity.
Combining these tools helps organizations proactively protect against targeted email attacks.
Legal Actions and Compliance
Regulations are increasingly holding organizations accountable for preventing and responding to spear phishing attacks. Key frameworks include GDPR, HIPAA, and ISO 27001, which emphasize both technical and procedural safeguards. To understand how these frameworks apply across different domains, explore Information Security vs Cybersecurity.
- GDPR (General Data Protection Regulation): Requires organizations to protect personal data and report breaches within 72 hours.
- HIPAA (Health Insurance Portability and Accountability Act): Mandates secure handling of patient data in the healthcare industry.
- SOX (Sarbanes-Oxley Act): Enforces data integrity in financial reporting.
- CCPA (California Consumer Privacy Act): Grants California residents rights over their personal data.
Failure to comply with these regulations can result in significant penalties. Legal actions are also being taken against individuals and groups responsible for spear phishing campaigns, though attribution and prosecution remain challenging.
Summary
Spear phishing represents a growing and dangerous threat in the digital world. Its personalized nature makes it more effective and harder to detect than traditional phishing. By targeting specific individuals with convincing and tailored messages, attackers can infiltrate even the most secure organizations.Combating spear phishing requires a comprehensive approach that includes user education, email authentication, technological defenses, and regulatory compliance. Build your expertise in these areas through Cyber Security Training. As cyber threats evolve, staying informed and proactive is the best defense against spear phishing and similar attacks.




