
- Definition of a Bot
- Types of Bots (Good vs Malicious)
- How Bots Are Created
- Use Cases: Chatbots, Web Crawlers, Trading Bots
- Botnets and Their Impact
- Malicious Bots (Spam Bots, DDoS Bots)
- Detection of Bot Activity
- Legal and Ethical Implications
- Role in Automation
- Future of Bot Technology
Definition of a Bot
A bot, short for “robot,” is a software application designed to perform automated tasks over the internet or within a computer system. These tasks are often repetitive, time-consuming, or require high-speed execution, making bots highly efficient. Bots can interact with systems, process data, send messages, and even mimic human behavior. While many bots serve beneficial purposes, others are designed with malicious intent to disrupt, deceive, or steal data. The dual nature of bots makes them both a valuable tool and a potential threat in today’s digital landscape. Learn how to harness their benefits while mitigating risks through Cyber Security Training. A bot is a program or script that executes commands, interacts with websites or users, and completes tasks automatically without direct human intervention. Bots can range from simple scripts that automate form submissions to complex artificial intelligence (AI)-powered systems capable of natural language processing and decision-making. Depending on their design and intent, bots can operate independently or be part of a network of bots controlled by a central system. They are widely used in fields such as customer service, online marketing, data analytics, and cybersecurity.
Interested in Obtaining Your Cyber Security Certificate? View The Cyber Security Online Training Offered By ACTE Right Now!
Types of Bots (Good vs Malicious)
Bots can be broadly classified into two categories: good (beneficial) bots and malicious (harmful) bots.
Good Bots:
- Chatbots: Used in customer service to answer queries, guide users, and simulate human conversation.
- Web Crawlers: Employed by search engines like Google to index web pages for search results.
- Monitoring Bots: Track website uptime, performance, and availability.
- Trading Bots: Automatically execute financial transactions based on algorithms.
- Data Collection Bots: Extract data from websites for analytics or competitive analysis.
Malicious Bots:
In the digital landscape, malicious bots pose significant threats to online security and integrity. These automated programs operate with nefarious intentions, ranging from spam dissemination and credential theft to server disruption and data extraction. Spam bots indiscriminately flood platforms with unsolicited messages, while credential stuffing bots exploit stolen login credentials across multiple websites. Distributed denial-of-service (DDoS) bots systematically overwhelm servers, causing potential service interruptions, and scraper bots illegally harvest copyrighted or sensitive information. Additionally, click bots manipulate online advertising metrics by generating fraudulent clicks, ultimately leading to financial fraud and undermining the digital ecosystem’s trust and reliability.
How Bots Are Created
Creating a bot involves programming a set of instructions using a language such as Python, JavaScript, or Java. Bots can be built using frameworks or platforms that provide libraries for automation and AI integration. The bot development process includes multiple stages, each requiring secure practices. To ensure accountability and prevent denial of actions taken by bots, explore Non-Repudiation in Cyber Security.
- Identifying the Purpose: Defining the specific task the bot is designed to perform.
- Programming the Bot: Writing the logic and functionality.
- Testing: Ensuring the bot functions as expected and doesn’t cause errors.
- Deployment: Launching the bot on a server or cloud infrastructure.
- Monitoring and Maintenance: Keeping the bot updated and functional.
Advanced bots may use machine learning and natural language processing (NLP) to improve performance over time. They can also be integrated with APIs, databases, and web services for more complex operations.
To Explore Cybersecurity in Depth, Check Out Our Comprehensive Cyber Security Online Training To Gain Insights From Our Experts!
Use Cases: Chatbots, Web Crawlers, Trading Bots
- Chatbots: Widely used in customer service to handle inquiries, schedule appointments, and process basic transactions. They use AI and NLP to understand user queries and simulate human interaction. Learn how these technologies intersect with digital safety through Cyber Security Training.
- Web Crawlers: Also known as spiders, they systematically browse websites and index content for search engines. Enable platforms like Google and Bing to provide relevant search results.
- Trading Bots: Automate stock, cryptocurrency, or forex trades using predefined criteria or machine learning algorithms for rapid decision-making.
- Gaming Bots: Assist in automated gameplay, AI opponents, and performance testing in game development.
- Social Media Bots: Help schedule posts, track engagement metrics, and moderate content.
- eCommerce Bots: Used for price tracking, inventory updates, and order placements to enhance user experience.
Botnets and Their Impact
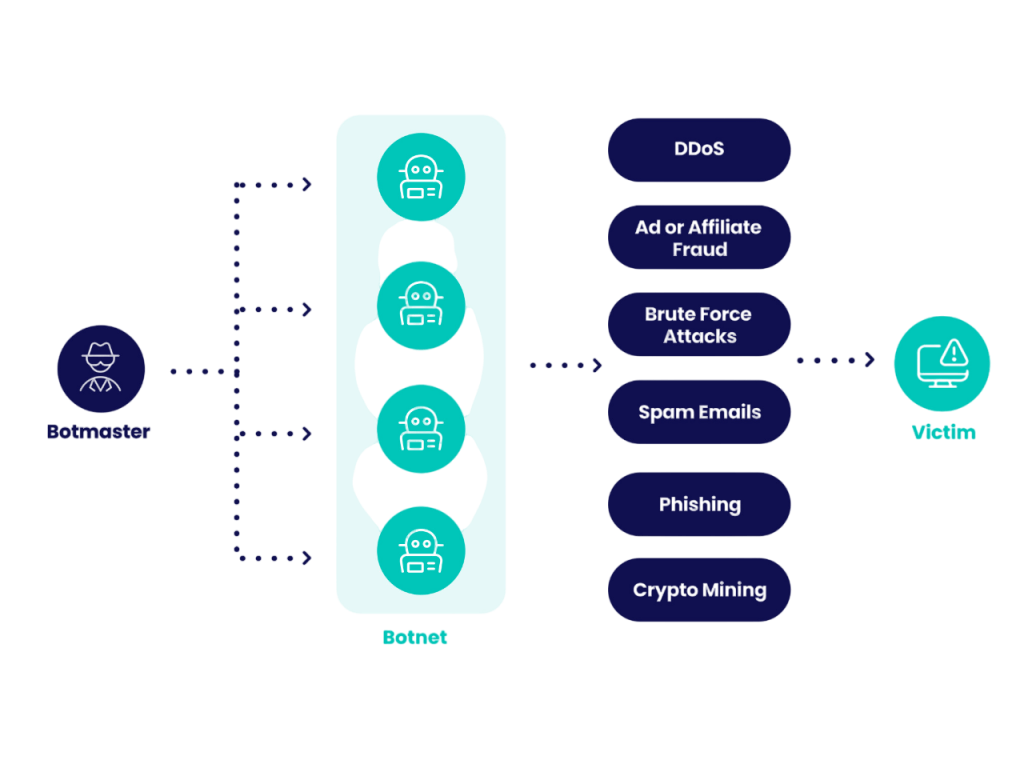
A botnet is a network of compromised devices or bots controlled by a hacker, often referred to as a “botmaster.” Botnets are used to conduct large-scale attacks such as DDoS, spamming, and data theft.
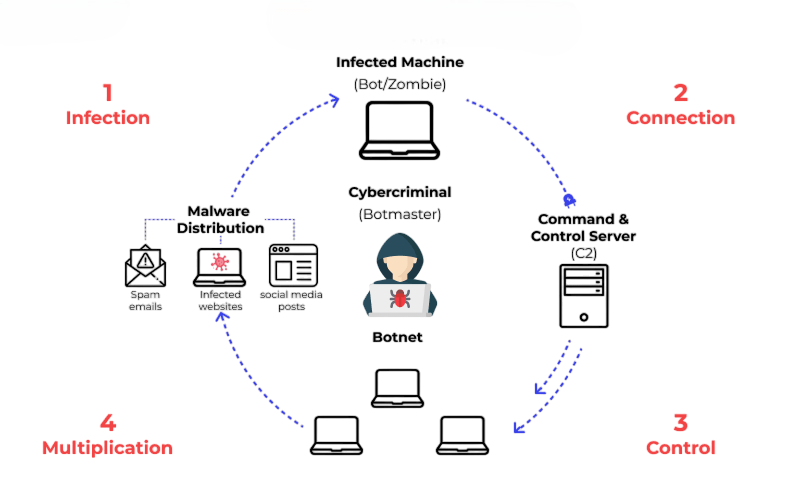
Infected devices operate without the knowledge of the owner and can be mobilized simultaneously to achieve the attacker’s goals. To explore how these threats evolve and impact individuals, businesses, and legal systems, check out Understanding Cybercrime and its Implications. Botnets like Mirai and Emotet have caused widespread disruption by targeting critical infrastructure and online services. The scalability and anonymity of botnets make them one of the most dangerous tools in cybercrime.
Looking to Master Cybersecurity? Discover the Cyber Security Expert Masters Program Training Course Available at ACTE Now!
Malicious Bots (Spam Bots, DDoS Bots)
Malicious Bots (Spam Bots, DDoS Bots): Malicious bots are designed to exploit vulnerabilities and carry out illegal or harmful activities.
- Spam Bots: Flood websites, forums, and comment sections with unwanted content or phishing links.
- DDoS Bots: Form part of botnets that send overwhelming traffic to a server, causing it to crash or become inaccessible.
- Credential Stuffing Bots: Use leaked credentials to access accounts across multiple platforms.
- Click Fraud Bots: Simulate clicks on online advertisements to defraud advertisers.
- Scraper Bots: Steal intellectual property or price data from competitors.
These bots can be extremely damaging to businesses, compromising data security, degrading performance, and leading to financial losses.
Detection of Bot Activity
Detecting bot activity involves monitoring unusual patterns in website traffic, user behavior, and system performance. Key indicators include:
- Sudden traffic spikes: Often originating from the same IP range or geographic location.
- Repeated failed login attempts: Cyber Security Tools may indicate credential stuffing or brute-force attacks. To detect and defend against these threats, explore Cyber Security Tools that specialize in monitoring login patterns and blocking unauthorized access.
- Unusually high bounce rates: Bots may access a page and exit immediately without interaction.
- Fast, repetitive mouse movements or keystrokes: Indicates automated behavior not typical of human users.
- Activity during odd hours: Or from unfamiliar or suspicious geolocations.
Security tools such as Web Application Firewalls (WAFs), bot management platforms, and machine learning algorithms can help detect and block bot traffic. CAPTCHA systems, rate limiting, and behavioral analytics also aid in identifying bots.
Preparing for Cyber Security Job Interviews? Have a Look at Our Blog on Cyber Security Interview Questions and Answers To Ace Your Interview!
Legal and Ethical Implications
The use of bots raises important legal and ethical questions. While beneficial bots are generally accepted, malicious bots often violate laws related to cybersecurity, data protection, and intellectual property. For instance: Unauthorized web scraping and related cyber activities carry serious legal risks. They can violate website terms of service, copyright laws, and data protection rules. Actions like credential stuffing and distributed denial-of-service (DDoS) attacks are viewed as serious crimes in most places. To understand how these attacks work and how to defend against them, Learn About DDoS Attacks. These activities can lead to heavy legal and financial penalties for those who commit them. Organizations and individuals should be careful and act ethically when using digital platforms to avoid legal trouble and protect their digital reputation. On the ethical side, bots can erode trust when they are used to spread misinformation, impersonate individuals, or manipulate markets. Transparency in bot usage and adherence to legal boundaries are essential for ethical bot deployment.
Role in Automation
Bots play a critical role in automation by streamlining repetitive tasks, enhancing productivity, and reducing operational costs. In business operations, bots handle tasks like:
- Customer Service (Chatbots): Provide instant responses and guide users through support queries.
- Data Entry and Validation: Ensure accuracy and speed in handling large data volumes.
- Social Media Posting: Schedule and publish content across platforms automatically.
- Email Sorting and Routing: Organize and prioritize communications for faster response times.
- Automated Testing in Software Development: Run test scripts continuously to identify bugs early in development.
Their ability to operate 24/7 without fatigue makes them ideal for high-volume, time-sensitive processes. As industries strive for efficiency, bot-driven automation is becoming increasingly integral to digital transformation.
Future of Bot Technology
The future of bots is poised for rapid advancement, driven by AI, machine learning, and natural language processing. We can expect bots to become more intelligent, conversational, and context-aware. Innovations in voice recognition, emotion detection, and adaptive learning will enable bots to provide personalized user experiences. In cybersecurity, bots will be used for threat detection, incident response, and vulnerability assessments. Meanwhile, regulation will likely become more stringent to address the misuse of bot technology. Stay ahead of evolving technologies and compliance standards with Cyber Security Training. As ethical frameworks and AI governance models evolve, the deployment of bots will need to align with societal values and privacy standards. In conclusion, bots are transformative tools that offer significant benefits when used responsibly. Understanding their capabilities, limitations, and risks is essential for leveraging their potential while safeguarding against malicious use.




