
- Introduction
- What is Social Engineering?
- Types of Social Engineering Attacks
- How Social Engineering Works
- Practical Applications of Social Engineering
- How to Protect Against Social Engineering Attacks
- Conclusion
Social engineering is a psychological manipulation technique used by cybercriminals to deceive individuals into divulging confidential information or performing actions that compromise security. Cybersecurity Training Courses exploits human behavior and trust rather than relying on technical vulnerabilities. Common types of social engineering attacks include phishing, pretexting, baiting, and tailgating, each using different methods to gain unauthorized access to sensitive data or systems. These attacks often involve impersonation, manipulation, or creating a sense of urgency to trick the victim. Social engineering techniques Practical applications of social engineering can be seen in various sectors, where attackers target employees, customers, or organizations to gain financial, personal, or corporate information. Protecting against these threats involves awareness, training, and implementing robust security measures, such as multi-factor authentication and strong verification processes. In conclusion, understanding and recognizing social engineering tactics are crucial in safeguarding against these deceptive and potentially damaging attacks.
Are You Interested in Learning More About Cybersecurity? Sign Up For Our Cyber Security Online Training Today!
Introduction
In the digital age, cyber threats are becoming more sophisticated and varied, with one of the most dangerous methods of attack being Social engineering prevention. This psychological manipulation technique exploits human behavior rather than relying on technical vulnerabilities, making it difficult to detect. Social engineering Cyber Awareness often gain access to sensitive information from people, unauthorized entry into a system, or makes them do things that result in breaches or loss of finances. Here, in this blog, we will see what is social engineering; kinds and how it works; real-time applications; and, ways to safeguard ourselves as well as our organization from such attacks.
What is Social Engineering?
Social engineering is the term used in reference to a variety of malicious acts that are carried out through human relationships. Here, cybercriminals take advantage of people’s trust, curiosity, and naivety in manipulating them into executing actions that compromise their security. Unlike technical hacking methods that exploit software vulnerabilities, social engineering attacks target people to make them reveal confidential information or allow unauthorized access to restricted systems or Network Access Control Lists. The psychology of human behavior is being used by social engineers. These operations depend more on the emotional feelings of fear, urgency, and greed within a person. There are many types of such attacks, which the attackers carry out both online as well as offline.
Types of Social Engineering Attacks
There are various techniques that fall under the broad category of social engineering. Each technique relies on manipulating individuals in a unique way.
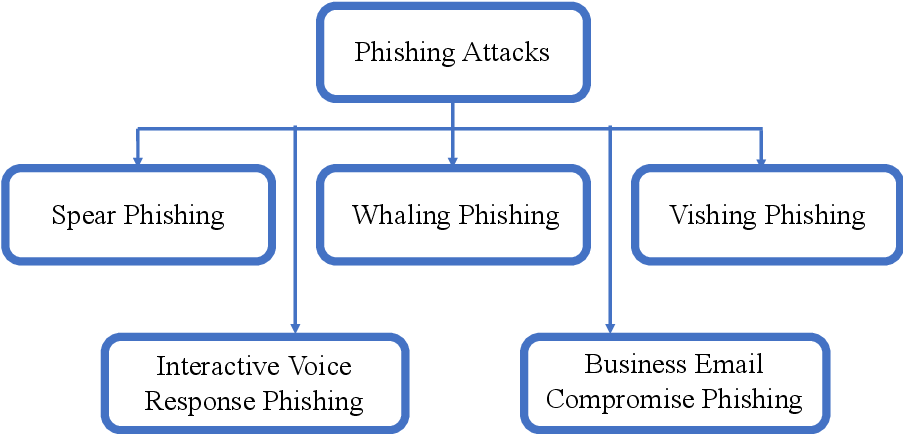
The most common types of social engineering attacks are discussed below:- Phishing The most known social engineering type is phishing. During a phishing attack, an attacker takes the form of a genuine organization or individual in order to extract sensitive information, including usernames and passwords, credit card numbers, or any other confidential data from the target. In general, phishing attacks occurs via deceptive emails or through fake websites that seem to come from a trusted source. For instance, a malicious message from an email supposedly coming from your bank will send you to a website to enter a login so you can “confirm” that account. But, this login redirects to an unsuspecting lookalike for the real banking site and swipes your ricted systems or Password Authentication.
- Vishing Vishing, or voice phishing, is similar to the method of phishing, but it takes place through voice communication, such as over the phone. A vishing attack occurs when a person pretends to be someone else, usually a bank representative or a government official, to trick the victim into giving sensitive information over the telephone. A typical example of vishing is when a caller presents himself as your bank’s fraud department and requests you to verify your account details to save your money. These calls can be very convincing, especially if the attacker has obtained personal information about the victim.
- Baiting Baiting falls under the realm of social engineering attacks, where something worthwhile is offered as bait to convince the victim of taking a specified action. Often, the offered free software will be in form of a downloadable or a present that seems unmissable and too good an offer to forgo. For instance, an Baiting attacks could offer free download of a movie on some rogue website or on an infected USB drive offering free content. As soon as the victim clicks on the link or inserts the USB, malware gets installed into their system, providing the attacker access to their personal data or their system. 3.4 Pretexting. In a pretexting attack, the attacker fabricates a story or scenario, which is known as the pretext, in order to gain the target’s confidence and surreptitiously elicit sensitive information from them. Frequently, the attacker masquerades as an HR representative, an IT support technician, or law enforcement officer, all with a seemingly valid reason for needing the information.
- Tailgating Tailgating is a physical type of social engineering in which an unauthorized individual accesses a secured area by entering behind an authorized person through an entry point of the building, or a security checkpoint. For instance, an attacker may wait for an employee to swipe his ID card to enter a building and then follow closely behind him, pretending to be a legitimate visitor. This type of Tailgating security attack relies on the target’s reluctance to challenge others or their desire to be polite.
Are you curious to know more about Cybersecurity ? Take advantage of our comprehensive online Cyber Security Online Training .
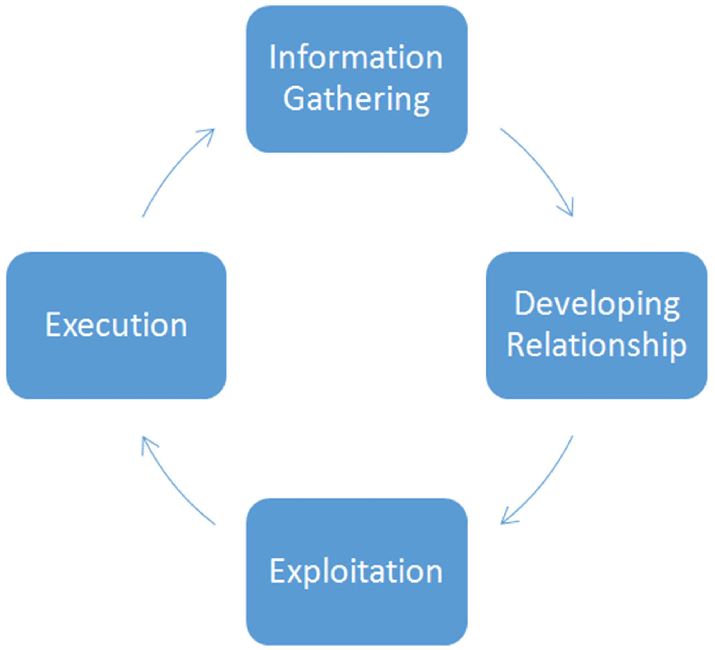
How Social Engineering Works
Social engineering attacks target human psychology instead of computer system vulnerabilities in Cybersecurity Training Courses . Emotions such as fear, urgency, greed, or curiosity are manipulated to coerce the victim into doing what the attacker wants. The reason why such attacks are successful is that they bypass traditional security measures, like firewalls or antivirus software, and target the human weakness. The success of social engineering often hinges on the speed with which an attacker can develop trust and generate a sense of urgency.
Attacker tactics might include:- Impersonation of a trusted figure: It is common for attackers to present themselves as being someone the victim is familiar with and trusts – such as a manager, a colleague, or service provider.
- They create a sense of urgency: The attackers may mention that there’s an immediate action required (suspension of the account, system failure, etc.), putting pressure on the victim to react without much thinking.
- They try to exploit the emotions: With fear, empathy, or greed, the attackers can make their victim do exactly what they have asked for.
Leverage Cyber Security to Unlock the Future! Enroll in the Cybersecurity Expert Masters Program Training Course Program at ACTE Right Away.
Practical Applications of Social Engineering
Attacks with social engineering can be used for economic, reputational, and loss of information or even financial gains.
- Corporate Espionage: Using social engineering, attackers may illicitly use their access to confidential business information and intellectual property or trade secrets. They may impersonate an employee or a business partner and gather information or infiltrate a company’s network.
- Identity Theft: Social engineering is one of the methods used to steal personal information such as Cybersecurity Framework, credit card details, and bank account information for further fraudulent activities.
- Data Breaches: Social engineering is one of the most common reasons for data breaches, where hackers gain unauthorized access to an organization’s internal systems by deceiving employees into providing login credentials or installing malicious software.
- Financial fraud: Using social engineering to persuade people to do something which is likely to move money or even credit card numbers, access your financial account. For example, they will present themselves as your bank representative, government agent.
Get interview-ready with our collection of Cybersecurity Interview Questions and Answers Questions.
Defense against Social Engineering
To safeguard both yourself and your organization against these attacks requires the combination of being aware and watchful plus following security procedures. Educate the Employees Teach the employees about social engineering and how to act when suspicious. Instruct them What is a Phishing Attack, vishing, and pretexting risks. Validate the Requests Always validate sensitive information requests via email, phone, or person. Use an official communication channel to verify whether the request is valid or not. Be wary of unsolicited offers never trust unsolicited offers, especially those that sound too good to be true. Never click on links or download attachments from unknown sources. Enable Multi-Factor Authentication (MFA) this adds an extra layer of security and makes it much harder for attackers to gain access even if they obtain login credentials. Limit Access to Sensitive Information Restrict access to sensitive data based on roles and responsibilities. The fewer people who have access to critical information, the harder it is for attackers to exploit.
Conclusion
Social engineering attacks exploit human psychology, preying on emotions like trust, fear, and curiosity to manipulate individuals into divulging sensitive information or performing actions that compromise security. Cybersecurity Training are particularly dangerous because they bypass technological defenses by targeting the weakest link in any security system people. Techniques like phishing, pretexting, baiting, and tailgating are commonly used in social engineering to deceive individuals into revealing login credentials, financial information, or granting unauthorized access to systems. Because these attacks rely on human error, they are often difficult to detect and prevent with traditional cybersecurity measures alone. To defend against social engineering, education and awareness are key, as individuals must recognize the signs of manipulation and respond appropriately.





