
- Introduction to Password Authentication
- Evolution of Password Authentication
- How Password Authentication Works
- Strengths of Password Authentication
- Weaknesses and Vulnerabilities of Password Authentication
- Best Practices in Secure Password Authentication
- The Future of Password Authentication
- Conclusion
Safeguarding your online account and personal data has always been the crowning jewel of life in this digital age. Password authentication is one of the most widely used authorization methods to secure access to systems, sites, and services. Despite its frequent usage, it must be pointed out that password authentication has weaknesses when a user utilizes poor passwords or if the system offers limited cyber safety measures. As highlighted by Cyber Media, these vulnerabilities can leave systems open to attacks such as brute force, phishing, and credential stuffing. This blog covers password authentication, its history, strengths and weaknesses, and best practices for implementing strong and secure authentication protocols in cybersecurity law.
To Explore Password Authentication in Depth, Check Out Our Comprehensive Cyber Security Online Training To Gain Insights From Our Experts!
Introduction to Password Authentication
Password authentication verifies a user’s identity by requiring the input of a secret passphrase or password. It is one of the most common forms used to protect access to digital systems, from email accounts to online banking. Password authentication, with proper implementation, is a reasonable defence against unauthorized access. However, how safe it is depends on many variables, mainly the password’s strength and the system’s facility to handle password management and cyber protection.
The safety of Password Authentication is also influenced by factors such as encryption, multi-factor authentication (MFA), and secure password storage methods. When passwords are stored in plaintext or with weak encryption, they are vulnerable to breaches if a system is compromised. Strong password policies encouraging complex, unique passwords can reduce the likelihood of attacks like brute force or dictionary attacks. However, even with a strong password, using MFA significantly increases Cyber Security Training Courses by requiring an additional layer of verification, such as a one-time code sent to a user’s phone or an authentication program, reducing the likelihood of unwanted access.
Evolution of Password Authentication
Using passwords to authenticate access can trace its history back to the dawn of computing. The first practical application of the concept came at MIT in the 1960s for controlling access to computer systems. It has been decades with successive waves of technology, but password-based security’s basic structure remains unchanged. Early password systems were primitive, typically simple and guessable words or phrases. Today’s password is far more complex, yet users and organizations are still grappling with the challenge of strong security. With the rise in sophisticated threats to digital security, there is an increased trend towards using password authentication in combination with other identity verification methods, such as biometric authentication or hardware-based tokens.
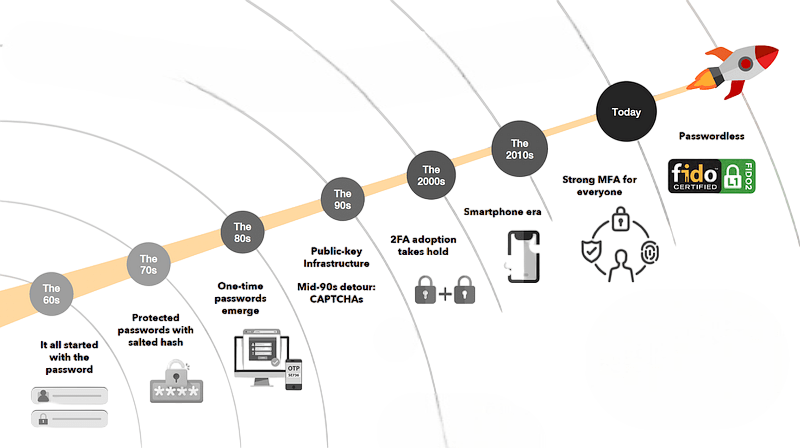
This shift to MFA has become necessary because attacks are getting smarter, and cyber malpractices use phishing, keylogging, and social engineering methods to penetrate passwords. With the rise of the Internet of Things, where everyday devices are interconnected, the potential entry points for attackers have multiplied, making it easier for them to exploit weak password systems. Biometric authentication implements something an individual has of them, such as fingerprints or facial recognition. In contrast, hardware-based tokens, such as security keys, offer a physical presence requiring the need to be ‘alive’ for the authentication process. While it has become much easier, managing passwords is still quite cumbersome for a user-they need to remember hundreds of unique passwords nowadays.
Are You Interested in Learning More About Password Authentication? Sign Up For Our Cyber Security Online Training Today!
How Password Authentication Works
Password Creation and Storage
For effective password authentication, users first need to create a password. This is normally done through some registration process where each user selects a unique password that will be stored in a database. However, storing passwords in plain text is very insecure. Modern systems use hashing algorithms to make passwords unreadable to avoid having their passwords breached. A user enters their password. The system hashes the input and compares it with the stored hash. If the hashes match, the user will be given access.
Authentication Process
User Login submits their username along with the password. Confirmation: The entered password is hashed by the system, which then compares it to the saved hash. Get in: The user is authenticated and given access to the system if the password matches. If it doesn’t match, then the request to access the system is denied. This is the fundamental process that most authentication procedures are based on, such as leveraging resources like the Google Hacking Database to identify potential vulnerabilities or weak spots in a system. This can help administrators bolster security and reduce the risk of unauthorized access.
Password Hashing and Salting
Salting is used in conjunction with hashing to further enhance the security of stored passwords. A salt is a random string of data added to a password before it is hashed. This ensures that even if two users choose the same password, their hashes will differ due to the unique salt associated with each password. Salting greatly reduces the risk of hash collisions and ensures that each password has a unique hash, adding a layer of security.
Strengths of Password Authentication
- Passwords are easy to understand and implement. Users know how they work and do not need peculiar hardware or software. Password-based systems are relatively inexpensive to set up and maintain. There is no need for additional devices, tokens, or biometric scanners.
- Password authentication is widely accepted and compatible with nearly all platforms and services. Although it is simple, when used in combination with other security measures, such as multi-factor authentication, it can be really effective.
- Passwords bring flexibility because the users-thus select the my can be set to an individual’s preference. They also provide a simple mechanism for access again by recovering passwords through security questions and even email verification.
- The biggest challenge is ensuring that the best practices are followed, such as using strong, unique passwords to safeguard against being easily exploited by attackers. Passwords are easily forgotten because one must remember numerous passwords to log in to several accounts.
- When combined with other technologies, such as password managers, users can easily store and keep track of complex passwords they do not necessarily have to remember. Although Cyber Security Training Courses is not foolproof, it remains a cornerstone of digital security when properly implemented with other safeguards.
Weaknesses and Vulnerabilities of Password Authentication
Brute Force Attacks
The brute force attack involves trying every possible combination of passwords sequentially to find the desired one. These attacks typically take a long time to execute due to their size when strong passwords are used; powerful computation may be leveraged to facilitate the attack. For this reason, a strong password policy must incorporate a mix of letters, numbers, and symbols, and login attempts should be limited to avoid such attacks.
Phishing and Social Engineering
Phishing attacks victimize users by tricking them into giving away their passwords with fake emails or websites. An attacker disguises themselves as a trusted party, such as a bank or a social networking website, to grab login credentials. This attack is hard to defend against, but one way to mitigate its impact is through Whitelisting. By allowing only trusted, verified sources to access sensitive systems or communications, whitelisting can help prevent attackers from reaching users with malicious links or websites, adding an extra layer of defense against phishing attacks.
Password Reuse
More often than not, many users use the same passwords in most of their sites. This can be one of the biggest security holes ever. If an attacker can break into one of the sites, they will automatically have access to all of a user’s accounts on other services, too. It’s very important, therefore, to encourage users to choose unique passwords for every service.
Poor Passwords
Many resort to weak, easily guessable passwords such as “123456” or “password.” Such passwords are vulnerable to quick brute-force attacks, and a weak password provides little protection when an intelligent attacker decides to target a user’s account.
Are You Considering Pursuing a Cybersecurity Master’s Degree? Enroll For Cyber Security Expert Masters Program Training Course Today!
Best Practices in Secure Password Authentication
Ensuring Strong Passwords
A good password is at least 12 characters long and includes a mix of uppercase and lowercase letters, numbers, and special characters. Strict policies for password implementation, which include complexity requirements and expiration dates, are effective in considerably reducing unauthorized access.
Multi-Factor Authentication (MFA)
MFA goes beyond simple password strength since it asks users to provide something they know, the password, but also for something they own and have with them (phone or hardware token) and even someday something they are, such as biometric verification. This makes it exponentially more difficult for hackers to gain access even if they know the password.
Password Managers
Since hard-to-remember complex passwords for each service require remembering different ones for each service, password managers can help with this job. These tools store securely and manage all necessary information to create a long string of strong, unique passwords for every account, which makes them easier to develop and use. Some added features include password sharing and encryption for increased security.
Secure Password Storage Techniques
Organizations should never store passwords in the cloud. Passwords should be hashed with one of the algorithms above, bcrypt, Argon2, or PBKDF2, making it virtually impossible for anyone to reverse-engineer back into an original password. Using a salt (random data) as part of a password before hashing makes it hard for attackers to break the passwords using precomputed hash tables, often called “rainbow tables.”
The Future of Password Authentication
It combines the real possibilities of biometric authentication, in the form of fingerprint or facial recognition, with hardware tokens such as security keys. The future of authentication lies somewhere between: passwords will no doubt remain a part of the authentication landscape for the foreseeable future, but sooner or later, they might be replaced or supplemented by more secure and user-friendly alternatives.A buzz around emerging technologies has focused on passwordless authentication based on technologies such as email-based magic links and one-time passcodes. For these methods to be truly effective, Cyber Awareness plays a crucial role. These entirely avoid risks connected to the use of passwords, such as password reuse, weak passwords, or a phishing attack on credentials. While passwordless authentication technologies offer promising advantages, they have their challenges. For instance, relying on email-based magic links or one-time passcodes can introduce new vulnerabilities, such as email account compromises or the interception of codes during transmission. Additionally, these methods may only sometimes be as widely adopted across all platforms, requiring systems to integrate new infrastructure and processes.
Preparing for a Cyber Security Job Interview? Check Out Our Blog on Cyber Security Interview Questions and Answers
Conclusion
Password authentication, though a very important security mechanism, remains the foundation of digital access control to date. Its effectiveness varies significantly as a function of the password’s strength and methods adopted to protect it. Strong policy enforcement of passwords, multi-factor authentication, and proper storage techniques should all be employed to provide robust protection. In an era where passwords are not likely to be the only means of authentication, it is an important element in securing online systems. Best practices and continuous vigilance to emerging threats enable users and organizations to protect their accounts and data in this complex digital world. As we move towards more sophisticated security systems, the role of Cyber Security Training Courses may evolve, but it will likely be around for a while. Integrating multi-factor authentication (MFA) and the rise of passwordless solutions can help mitigate the inherent weaknesses of traditional passwords. Still, they also introduce their challenges and complexities. Users must adapt to new technologies, and systems must be built to balance convenience with robust security. The key to future digital security will lie in a layered approach, where passwords, biometrics, hardware tokens, and other verification methods work together to create a more resilient defence against cyber threats.





