
- The Google Hacking Database: What is it?
- The GHDB Importance
- Some practical applications for the GHDB include
- Types of GHDB
- Ethical Issues
- Limitations of Google Hacking
- GHDB for Enhanced Online Security
- Conclusion
The Google Hacking Database, or GHDB, comprises advanced search queries or Google dorks that security experts and white hat hackers employ to identify vulnerabilities, misconfigurations, and exposed sensitive information on websites. The database you’re referring to is likely Exploit-DB, a resource that catalogs various exploits, vulnerabilities, and security-related information. Google Dorking refers to the practice of using advanced search operators in Google Search to find sensitive or vulnerable information online, such as exposed databases, configuration files, or other potentially dangerous security issues. While Google is a useful search interface for accessible information, it can actually be used to find IT securityvulnerabilities and misconfigurations of online systems. GHDB lists a variety of search queries or dorks that abuse advanced features of Google, such as intitle, inurl, filetype, and site. Dorking could likely reveal sensitive information, hidden login pages, servers with vulnerabilities, as well as unprotected files.
To Explore Google Hacking Database in Depth, Check Out Our Comprehensive Cyber Security Online Training To Gain Insights From Our Experts!
The Google Hacking Database: What is it?
The Google Hacking Database (GHDB) contains a collection of sophisticated search techniques, operators, and queries. This makes it possible for both ordinary users and cybersecurity professionals to identify Cyber Security Training Courses vulnerabilities and possible dangers. In essence, GHDB permits ethical hackers, penetration testers, and security researchers to work toward increased online safety.The GHDB is a knowledge base that leverages the capabilities of Google’s search engine rather than being a typical database. It consists of meticulously constructed search terms, or “dorks,” to find particular data types or possible security vulnerabilities.
The GHDB Importance
- Enhanced Security Awareness:The GHDB allows people and organizations to learn more about potential computer security threats and cybercriminals’ tactics. One crucial aspect of addressing these vulnerabilities is through Ethical Hacking. Ethical hackers, also known as penetration testers or white-hat hackers, use tools like Google Dorking as part of their security assessments.
- Exposure identification and repairing: The GHDB makes finding weaknesses in network infrastructure, web apps, and other electronic systems easier. It assists security experts in identifying vulnerabilities early on, allowing for prompt patching and lowering the possibility of possible cyber threats.
- Penetration Tests and Ethical Hacking: To mimic actual cyberattacks, ethical hackers and testers for penetration use the GHDB. Security professionals may evaluate an organization’s protection capabilities and offer insightful recommendations for bolstering security measures by utilizing the database’s sophisticated search strategies and queries.
- Vulnerability Scan
- Penetration Testing
In penetration testing, Google dorks serve as a channel for scouting information about the target. This information assists the ethical hacker in determining possible attack vectors and assessing any organization’s security posture.
- Threat Intelligence:
The GHDB notifies the analysts about exposed data, which perhaps malicious people may use for their malicious actions. At this point, organizations will take corrective measures based on the compromised information.
- Incident Response:
In the event of an attack, as the incident responder continues to scan more exposed data or research into breach depth, they can utilize Google hacking to produce even more exposed data.
- Exposed Sensitive Files:Files with no business being exposed, from configuration files and password files to database backups or other classified documents.
- Misconfigured Web Servers:Misconfigured servers contain areas and directories of files or server information in plain view for attackers to exploit. This includes, but is not limited to, default pages, error messages, or misconfigured directory listings
- Database Server Information:Databases with file backups, unsuspecting database dumps, or configurations exposing sensitive information such as usernames, passwords, server settings, etc.
- Open Directory: Directories are listed openly in the web servers that show contents. They may harbour confidential data or application files that should be kept confidential from unlawful users in Cyber Security Training Courses.
- Exposed Admin Panels and Login Pages: Administrative or login portals are exposed and potentially vulnerable to brute force attacks, credential stuffing, or misconfigurations that allow unauthorized access.
- Vulnerable Web Applications:Applications or systems left exposed to the internet with known vulnerabilities or outdated versions available for exploitation. This includes vulnerable CMSs like WordPress or Joomla, file management systems, or other platforms exposed in their default settings.
- Backup and Temporary Files: Backup files, such as.bak,.zip, or.tar files, or even temporary files containing PII, including old versions of databases, configurations, or user information.
- Data Availability Google hacking depends fully on the presence of publicly indexed data. If the targeted sensitive information is not available in the public domain or has been sufficiently secured, then it won’t yield results. Organizations can limit access to certain data types or utilize security measures to prevent sensitive data from being indexed by search engines.
- Search Engine Updates Algorithm Evolution From time to time, Google’s algorithms evolve significantly enough to change search rankings and the indexibility of pages. Hence, information that had formerly been easily accessed may now be unavailable, unknown or harder to find. Policy Evolution Other than the algorithm evolution, Google may also evolve its policies about what is indexed, which can reduce the effectiveness of some of the Google dorks in the long term.
- Legal Issues Access without Authorization Google hacking will enable unauthorized access or exploitation of information, which is strictly prohibited and may attract serious legal implications in most jurisdictions. Most jurisdictions have enacted strict laws against unauthorized access to information systems. Risk of Liability is an important consideration for ethical hackers, particularly when engaging in activities such as Network Penetration Testing. A good ethical hacker should be careful to avoid any actions that could lead to legal consequences or incur liability.
- Over-reliance on Automated Searches Limited Visibility With a reliance on Google dorks, limited focus will likely be given to surface-level vulnerabilities. Comprehensive Comprehensive security assessment calls for digging deeper than a simple automated search. Human Expertise is sought. Effective vulnerability assessment often requires human insight and expertise to analyze the findings correctly and appreciate the larger security context.
- Counter-Search Techniques Organizations can use a countermeasure such as robots.txt files that deny specific pages or directories to crawl from the search engines. It will be a counter to Google hacking. Security Improvements Over time, security practices advance and what was once exposed would become tough to access for future hacking attempts. Past Google, dorks would lose their utility
- Potential for Abuse Google hacking can be used for valid and malicious purposes. Hence, it involves the possibility of potential misuse by malicious actors. This may lead to dilemmas of ethical behaviour and trust in the community. Scrutiny of the Community Ethical hackers need to understand the perception and scrutiny of the general public and the organizations they are helping and not compromise their integrity.
Are You Interested in Learning More About Google Hacking Database? Sign Up For Our Cyber Security Online Training Today!
Some practical applications for the GHDB include
Security experts use the GHDB to scan for vulnerabilities within their systems or in their clients’ systems. They can then take proactive measures to seal security holes by searching for misconfigured servers or sensitive files exposed to the system.
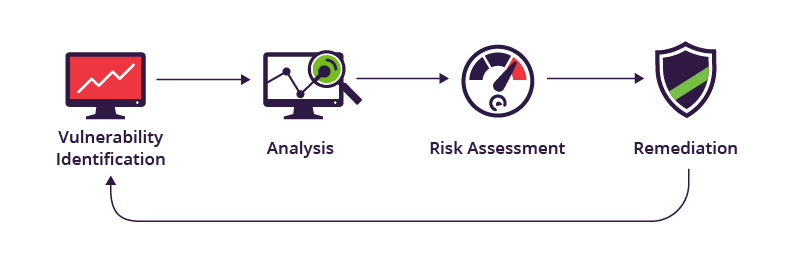
Types of GHDB
Ethical Issues
Permission Always get permission before performing penetration testing or vulnerability assessments on third-party systems. Otherwise, unauthorized access can have an adverse effect in the form of legal complications and result in undue damage to the trust relationship between security professionals and organizations. Responsible Disclosure is an essential practice in the field of Cyber security. When vulnerabilities are discovered, it is crucial to follow responsible disclosure practices to ensure that security risks are addressed before they can be exploited by malicious actors. This means disclosing the problem to the organization at risk and then allowing them time to correct the flaw before making such findings known. Open communication in this process develops cooperation and trust. Intended to Use Google Dorks mainly for educational purposes, security research, and improving defences. One should not use this technique for malicious purposes, as hacking is about the defence and enhancement of security rather than how one can exploit vulnerabilities to gain personal benefits.
Are You Considering Pursuing a Cybersecurity Master’s Degree? Enroll For Cyber Security Expert Masters Program Training Course Today!
Limitations of Google Hacking
GHDB for Enhanced Online Security
The GHDB’s capacity to assist users in locating sensitive, exposed data is one of its main advantages. Cybersecurity experts can use certain search terms to find documents or web pages that inadvertently reveal private information. Passwords, login information, credit card numbers, and private data may fall under this category. For instance, log files containing plaintext passwords can be found using a search query such as “filetype:log password.” When such vulnerabilities are found, people and organizations can act quickly to protect the data and stop illegal access. One useful resource for identifying susceptible network devices is the GHDB. For example, CCTV with default login information can be found using a search query such as “inurl:/login.html intext:admin.” Device owners can be alerted by this information, which will help them put stronger security measures in place and stop such breaches.
Finding open webcams and Internet of Things (IoT) devices that are reachable online can be aided by the Google Hacking Database (GHDB). Cybersecurity experts can use specific search terms and operators to find unprotected cameras or gadgets that need to be adequately secured. This process of gathering publicly available information to identify vulnerabilities is a key component of Open Source Intelligence (OSINT). For instance, a search query such as “inurl:/view.shtml” can locate publicly accessible cameras. To increase awareness of privacy threats, this information is essential. By altering default settings, creating secure passwords, and turning on encryption, it encourages users to protect their devices. The GHDB’s capacity to assist in locating vulnerable files and directories on websites is another useful feature. Security experts can find files with sensitive data, configuration files, backups, or source code by employing sophisticated search strategies.
Preparing for Cyber Security Job Interviews? Have a Look at Our Blog on Cyber Security Interview Questions and Answers To Ace Your Interview!
Conclusion
The Google Hacking Database is a formidable challenge in the face of Cyber Security Training Courses analysts, who may use advanced search techniques to uncover vulnerabilities and other sensitive information that have accidentally found their way into an online presence. The use of Google dorks, therefore, enhances the reconnaissance activities of the ethical hacker. It will provide knowledge of where vulnerabilities exist in a security posture, thus enabling the organization to fortify its defence. However, although this database has numerous advantages over the other databases, making use of the GHDB requires a great deal of ethical sense. Some of the considerations are that the right permissions exist, responsible disclosure practices are followed, and what laws apply while accessing possibly sensitive information.





