
- Ethical Hacking
- Why Learn Ethical Hacking?
- Prerequisites
- Ethical Hacking Phases
- Tools for Beginners
- Footprinting & Reconnaissance
- Scanning & Enumeration
- Gaining Access
- Maintaining Access
- Conclusion
Ethical Hacking
In today’s digital-first world, cyber threats are evolving at a rapid pace, targeting individuals, organizations, and even governments. As the attack surface grows, so does the demand for professionals who can identify vulnerabilities and secure systems. Ethical hacking, also known as penetration testing or white-hat hacking, plays a critical role in safeguarding digital infrastructures. These professionals simulate real-world attacks to identify vulnerabilities before malicious actors can exploit them. To develop the skills needed for such proactive defense, explore Cyber Security Training a hands-on program that covers ethical hacking methodologies, network security, vulnerability assessment, and certification pathways for aspiring cybersecurity experts. Unlike malicious hackers, ethical hackers use their skills legally and responsibly to strengthen security systems. Learning ethical hacking from scratch gives you a structured approach to understand how systems can be attacked and, more importantly, how they can be protected. For beginners, the field may seem overwhelming, but with the right guidance, roadmap, and practice, anyone can start developing ethical hacking skills.
Why Learn Ethical Hacking?
There are multiple compelling reasons to learn ethical hacking from scratch. First, cyberattacks are becoming more frequent and sophisticated, costing organizations billions each year. Ethical hackers are in high demand across industries, including IT, finance, healthcare, and defense. Second, ethical hacking provides a unique skill set that not only enhances employability but also opens doors to specialized roles such as penetration tester, security analyst, or cybersecurity consultant. To build hands-on expertise with the tools used in real-world assessments, explore Kali Linux Tutorial a practical guide that walks you through reconnaissance, exploitation, and reporting techniques using one of the most widely adopted platforms in offensive security. Another reason is personal empowerment knowing how hackers think equips individuals to better protect their own digital presence. For those with curiosity about how technology works, ethical hacking offers a hands-on and problem-solving experience that is both challenging and rewarding.
Interested in Obtaining Your Cyber Security Certificate? View The Cyber Security Online Training Offered By ACTE Right Now!
Prerequisites
Before diving into ethical hacking, certain foundational skills are required. Beginners should have a good understanding of computer networks, as hacking often involves exploiting weaknesses in communication systems. Basic knowledge of operating systems, particularly Linux, is also crucial since most hacking tools are developed for Linux environments. A solid grasp of programming languages like Python, C, or JavaScript helps in writing scripts, automating tasks, and understanding exploits. To master the command-line techniques that power these tools, explore Kali Linux Commands Every Hacker Must Know a tactical guide that covers essential commands for reconnaissance, privilege escalation, network scanning, and exploit execution in ethical hacking workflows. Familiarity with databases, firewalls, and system administration is equally useful. Beyond technical prerequisites, patience, critical thinking, and persistence are key qualities, as ethical hacking often involves trial and error. Fortunately, even beginners without a tech background can start with online courses, labs, and guided tutorials to build these skills gradually.
To Explore Cybersecurity in Depth, Check Out Our Comprehensive Cyber Security Online Training To Gain Insights From Our Experts!
Ethical Hacking Phases
Ethical hacking is not a random process but a structured methodology, typically consisting of five main phases: reconnaissance, scanning, gaining access, maintaining access, and covering tracks. To understand how these phases often intersect with malware analysis and system compromise, explore What is a Computer Virus a foundational guide that explains how malicious code spreads, infects systems, and disrupts operations, often serving as the entry point for deeper exploitation during penetration testing.
- Footprinting & Reconnaissance: Gathering information about the target.
- Scanning & Enumeration: Identifying open ports, services, and potential vulnerabilities.
- Gaining Access: Exploiting weaknesses to enter systems.
- Maintaining Access: Establishing persistence to understand the extent of compromise.
- Clearing Tracks: Erasing evidence of testing to avoid detection.
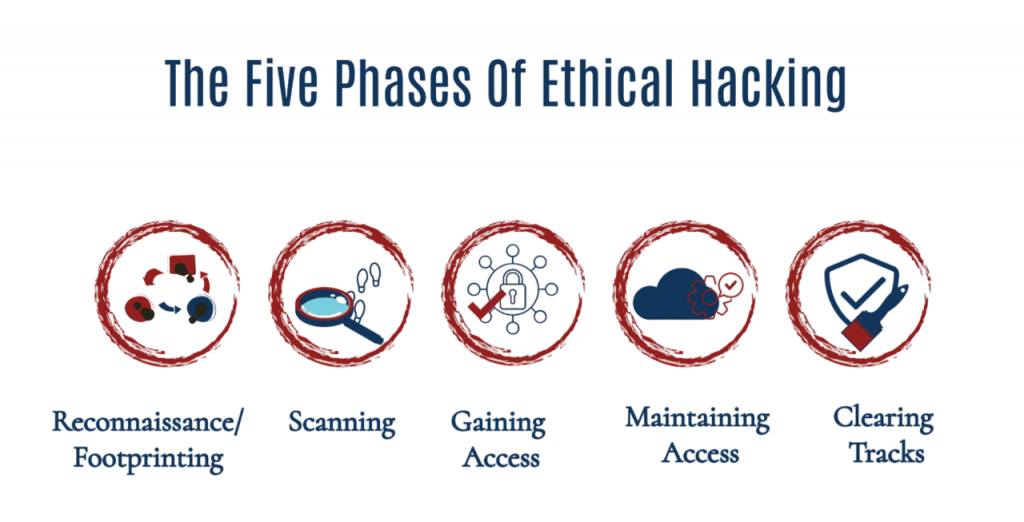
Following these phases ensures that ethical hackers simulate real-world attack scenarios while adhering to legal and professional standards.
Tools for Beginners
Ethical hacking is important and uses different tools that make tasks easier while teaching you about system weaknesses. If you’re new to this, here are some basic tools to get you started. Nmap is a strong network scanner. It helps you find devices, open ports, and services on a network. Wireshark is also useful. It’s a network protocol analyzer that lets you look at data packets as they move, which helps you understand network traffic. Metasploit is a penetration testing framework that helps you exploit known weaknesses. To master these tools and apply them in real-world scenarios, explore Cyber Security Training a hands-on curriculum that covers packet analysis, vulnerability exploitation, and lab-based simulations designed to build practical skills for aspiring cybersecurity professionals. It’s a key tool for ethical hackers who want to check security. Burp Suite is great for testing web applications and finding problems like SQL injection and cross-site scripting (XSS). If you’re interested in wireless security, Aircrack-ng is important.
Looking to Master Cybersecurity? Discover the Cyber Security Expert Masters Program Training Course Available at ACTE Now!
Footprinting & Reconnaissance
Footprinting is the first and one of the most critical steps in ethical hacking. It involves collecting as much information as possible about the target before launching an attack. Reconnaissance can be active (direct interaction, such as pinging a server) or passive (using publicly available data like WHOIS records). Common techniques include DNS footprinting, WHOIS lookups, social media profiling, and Google hacking. To understand how these techniques are also used to navigate hidden networks and uncover illicit activities, explore What Is the Dark Web a foundational guide that explains the structure, access methods, and investigative relevance of anonymous online ecosystems beyond the surface web. For example, by analyzing a company’s website, an ethical hacker might discover server details, employee emails, or outdated technologies that can later be exploited. The goal of this phase is to build a complete profile of the target’s infrastructure.
Preparing for Cyber Security Job Interviews? Have a Look at Our Blog on Cyber Security Interview Questions and Answers To Ace Your Interview!
Scanning & Enumeration
- Scanning phase: After gathering information, scanning identifies live systems, open ports, and running services.
- Common tools: Nmap and Angry IP Scanner are widely used for this purpose.
- Enumeration phase: Goes deeper by extracting details like usernames, shared folders, and system data.
- Purpose: Helps ethical hackers map the attack surface and rank vulnerabilities.
- Example: Finding an open port with an outdated FTP service could be a direct vulnerability.
- Caution: Aggressive scans may trigger intrusion detection systems (IDS) and raise security alerts.
Gaining Access
- Gaining access phase: Focuses on exploiting discovered vulnerabilities to infiltrate the target system.
- Nature of work: Practical and hands-on stage of ethical hacking.
- Common techniques: SQL injection, buffer overflow attacks, and weak authentication exploits.
- Popular tools: Metasploit and Hydra are frequently used for controlled exploitation.
- Simulation goal: Mimics a real attacker’s actions data theft, configuration changes, or privilege escalation.
- Ethical distinction: Ethical hackers record all actions and ensure no actual harm is done.
- Purpose: Demonstrates the potential real-world consequences of vulnerabilities to stakeholders.
Maintaining Access
In real-world cyberattacks, hackers don’t simply exploit a system once; they establish persistence to ensure continued control. To prevent such long-term compromise, organizations must continuously monitor, assess, and remediate weaknesses. Explore Vulnerability Management Explained a strategic guide that outlines how systematic vulnerability tracking, prioritization, and patching can disrupt attacker footholds and reinforce enterprise security posture.
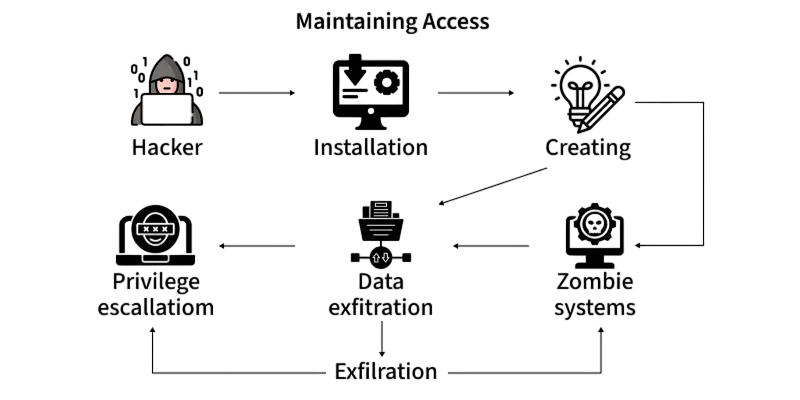
Ethical hackers also test this capability by attempting to create backdoors, install rootkits, or use Trojan-like mechanisms. The purpose is to evaluate how well a system can detect and remove unauthorized access. For example, an ethical hacker may simulate advanced persistent threats (APTs), where attackers remain undetected within a network for months. By understanding persistence mechanisms, organizations can enhance their monitoring and incident response capabilities.
Conclusion
Learning ethical hacking from scratch is a journey that requires curiosity, patience, and continuous practice. It is not just about using tools but also about developing a hacker mindset thinking like an attacker to defend systems effectively. Beginners can start with basic networking and Linux skills, gradually progress to tools and techniques, and eventually pursue certifications to validate their knowledge. To follow a structured learning path from foundational concepts to advanced practices, explore Cyber Security Training a step-by-step program designed to build core competencies, introduce essential tools, and prepare learners for industry-recognized certifications in ethical hacking, network defense, and digital forensics. Ethical hacking is more than a career it is a mission to make the digital world safer. With increasing cybercrime, the demand for skilled ethical hackers will only continue to grow, offering exciting opportunities for those willing to learn and adapt.




