
- Penetration Testing: Strengthening Cybersecurity Through Ethical Hacking
- Benefits of Penetration Testing
- Skills Required for a Pen Tester
- Frameworks and Methodologies in Penetration Testing
- Tools Used by Penetration Testers
- Career Path of a Penetration Tester
- Top Certifications for Penetration Testers
- Challenges in Penetration Testing
- The Future of Penetration Testing
- Conclusion
Penetration Testing: Strengthening Cybersecurity Through Ethical Hacking
As businesses rely more heavily on digital systems, cyberattacks have become one of the greatest threats of the modern age. Every organization—whether a multinational corporation, a government agency, or a small startup—faces the risk of ransomware, phishing, and data theft. That’s where penetration testing, also known as ethical hacking guide, comes in. penetration testing tools is a deliberate and controlled simulation of cyberattacks. It’s a process designed to identify security weaknesses before real attackers do. Ethical hackers act as “friendly adversaries,” probing systems to reveal flaws in applications, networks, devices, and human behavior. Their insights allow organizations to patch vulnerabilities, comply with regulations, and strengthen their overall security posture. The importance of penetration testing cannot be overstated. A successful test can prevent million-dollar breaches, safeguard customer data, and protect an organization’s reputation. By understanding how hackers operate, pen testers help companies turn weaknesses into strengths. The Penetration Tester’s Role Attacking and defending are two aspects of a penetration tester’s job. They act completely legally and with moral purpose, yet they take on the attitude of a malevolent hacker. Their task is to uncover vulnerabilities, demonstrate how they can be exploited, and recommend actionable solutions to close those gaps.
Core Responsibilities:
- Conduct simulated attacks on systems, networks, and web applications.
- Evaluate vulnerabilities found in configurations, firewalls, databases, and software.
- Document each step of the attack chain to demonstrate potential risks.
- Develop remediation strategies and guide organizations in implementing fixes.
- Maintain strict ethical and legal standards throughout the testing process.
- Pen testers often specialize in one or more domains:
- Assessing the resilience of servers, APIs, and apps is known as network and web application testing.
- Testing for wireless and cloud penetration involves making sure that virtual machines, cloud storage, and Wi-Fi are configured securely.
- Social engineering is the evaluation of the human factor by means of psychological manipulation or phishing.
- Finding data breaches, unsafe APIs, and incorrect permission setups are all part of mobile app security.
- These experts play a vital role in maintaining compliance with frameworks like GDPR, HIPAA, PCI DSS, and ISO 27001, which require regular security assessments.
- Proactive Cyber defense: Identifying vulnerabilities before malicious actors do helps prevent costly breaches.
- Risk Mitigation: Enables businesses to assess the severity and potential impact of discovered vulnerabilities.
- Regulatory Compliance: Many industries require regular penetration tests to satisfy legal and compliance obligations.
- Business Continuity: Preventing attacks ensures uptime, data availability, and operational stability.
- Enhanced Trust: Clients and stakeholders gain confidence knowing their data is safeguarded by rigorous testing.
- Incident Readiness: Pen tests help internal teams prepare response plans for real-world attacks.
- Improved Security Culture: Regular testing fosters awareness and encourages employees to adopt safer digital practices.
- Operating Systems: Mastery of Windows, Linux, and macOS.
- Networking: Deep understanding of TCP/IP, DNS, DHCP, VPNs, firewalls, and routing.
- Programming & Scripting: Proficiency in Python, Bash, PowerShell, and JavaScript to automate tasks and develop custom exploits.
- Security Fundamentals: Knowledge of cryptography, authentication protocols, and Vulnerability testing exploitation techniques like SQL injection, XSS, CSRF, and buffer overflows.
- Critical Thinking: Ability to analyze complex systems and identify non-obvious weaknesses.
- Communication: Writing clear, professional reports that both executives and engineers can understand.
- Ethics & Integrity: Handling sensitive information responsibly and operating within legal boundaries.
- Continuous Learning: Staying current with evolving threats, zero-day vulnerabilities, and emerging tools.
- OSSTMM (Open Source Security Testing Methodology Manual): Focuses on measurable operational security.
- OWASP Testing Guide: Industry gold standard for web and API security testing.
- NIST SP 800-115: U.S. government technical guide for information security testing skills.
- PTES (Penetration Testing Execution Standard): Comprehensive coverage from pre-engagement through post-testing reporting.
- Network Penetration Testing: Detects weaknesses in firewalls, routers, and internal systems.
- Web Application Testing: Identifies vulnerabilities like SQL injection, cross-site scripting (XSS), and insecure authentication.
- Wireless Testing: Ensures Wi-Fi networks use proper encryption and aren’t exposed to rogue devices.
- Social Engineering: Evaluates employee awareness through phishing emails, phone scams, or in-person deception.
- Cloud & Mobile Testing: Protects data in cloud environments and mobile applications.
- Physical Penetration Testing: Assesses the strength of physical access controls, locks, and facility security.
- Nmap: Network discovery and port scanning.
- Metasploit Framework: Exploitation and payload testing.
- Burp Suite: Web application scanning and interception.
- Wireshark: Deep packet inspection and traffic analysis.
- Aircrack-ng: Wireless network auditing and password cracking.
- Hashcat: Fast password recovery and brute-force testing.
- Nessus and OpenVAS: Automated Vulnerability testing scanning and risk assessment.
- Planning & Reconnaissance: Define scope, permissions, and gather intelligence about the target.
- Scanning & Enumeration: Identify active hosts, open ports, and services.
- Exploitation: Execute controlled attacks to access systems and data.
- Privilege Escalation: Attempt to gain higher-level access or administrative control.
- Post-Exploitation: Demonstrate impact by accessing sensitive data or maintaining persistence.
- Reporting: Present findings in an actionable format, including severity rankings, proof-of-concept exploits, and remediation steps.
- Security Engineer / Architect
- Incident Response Analyst
- Cybersecurity Consultant
- Red Team Lead
- Chief Information Security Officer (CISO)
- Certified Ethical Hacker (CEH): A foundational course covering tools, exploits, and methodologies.
- Offensive Security Certified Professional (OSCP): Hands-on certification known for its difficulty and industry respect.
- GIAC Penetration Tester (GPEN): Focuses on advanced techniques and exploit development.
- CompTIA PenTest+: Vendor-neutral certification bridging entry to mid-level expertise.
- Certified Penetration Testing Specialist (CPTS): Practical, scenario-driven credential designed for real-world problem solving.
- Rapidly Evolving Threats: New vulnerabilities appear daily, requiring constant learning.
- Limited Testing Scope: Legal or contractual constraints may restrict specific actions.
- False Positives/Negatives: Automated tools can produce misleading results.
- Time Constraints: Projects often have tight deadlines.
- Legal and Ethical Risks: Testers must ensure all actions remain within the approved scope.
- AI-Powered Testing: Artificial intelligence will automate reconnaissance and vulnerability detection, allowing human testers to focus on strategic analysis.
- Cloud and IoT Expansion: As more data moves to the cloud and smart devices proliferate, pen testers will specialize in distributed and interconnected ecosystems.
- Purple and Red Team Collaboration: The fusion of offensive (Red Team) and defensive (Blue Team) efforts into Purple Teams is creating stronger, adaptive security practices.
- Post-Quantum Testing: Preparing for quantum computing’s potential to break traditional encryption methods.
Areas of Specialization:
Want to learn more about Cybersecurity ? Enroll in our Complete Cyber Security Online Training Online!
Benefits of Penetration Testing
penetration testing tools offers multifaceted benefits that extend across technical, operational, and strategic levels. For organizations, it serves as both a diagnostic tool and a long-term investment in resilience.
In short, penetration testing is not just a technical necessity—it’s a strategic move that protects brand reputation and customer confidence.
Skills Required for a Pen Tester
To succeed as a penetration tester, one needs a blend of technical mastery, analytical thinking, creativity, and ethical discipline. The role demands not only knowledge of technology but also an understanding of the psychology of attackers.
Technical Expertise:
Analytical & Soft Skills:
A successful pen tester combines logic with creativity—seeing systems not as they are meant to work, but as they might fail.
Frameworks and Methodologies in Penetration Testing
A structured methodology ensures accuracy, consistency, and credibility in results. Pen testers follow globally recognized standards such as:
These frameworks establish best practices, ensuring each test is well-documented, reproducible, and compliant with legal and ethical boundaries.
Types of Penetration Testing
Each type of penetration testing tools serves a different security purpose:
By combining multiple security testing skills types, organizations gain a holistic understanding of their security landscape.
Tools Used by Penetration Testers
Tools form the backbone of penetration testing, enabling efficient scanning, exploitation, and reporting.
Expert testers know that tools are just instruments; true skill lies in interpreting the data and crafting creative attack strategies based on human insight.
Phases of Penetration Testing
A well-structured penetration test typically follows six distinct phases:
Preparing for a job interview in cybersecurity ? Examine our blog post about Cybersecurity Interview Questions and Answers to get the most of your employment experience!
Comprehensive reports are a hallmark of professionalism, bridging technical findings with business implications.
Enroll in ACTE’S Cyber Security Online Training if you want to become an expert in cyber security field and have a prosperous career.
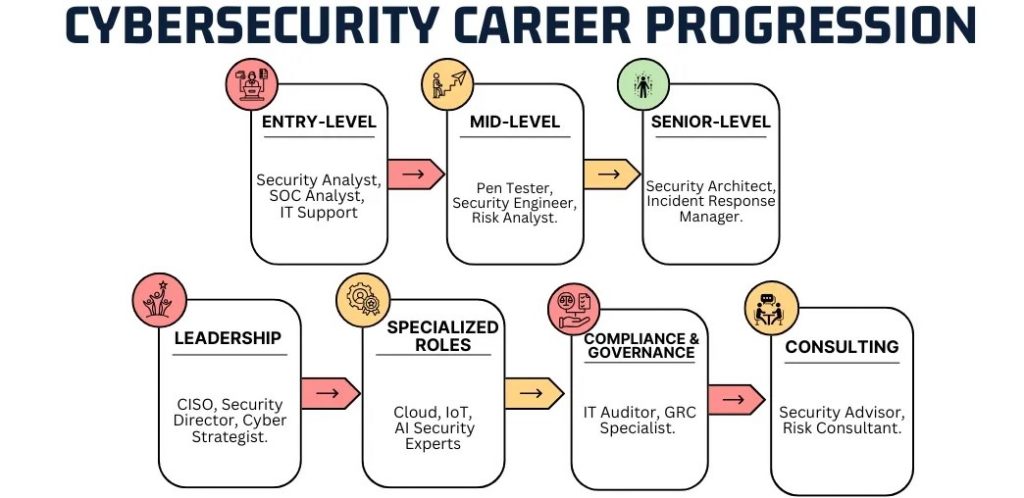
Career Path of a Penetration Tester
The penetration testing career is dynamic, rewarding, and constantly evolving. Professionals often start as junior Vulnerability testing analysts or security interns, gaining hands-on experience through labs and simulations. With time, they move into intermediate penetration tester roles, tackling complex exploitations and advanced penetration testing tools methodologies. Senior testers may lead Red Teams, coordinate large-scale attack simulations, or transition into security consulting and leadership roles.
Career Growth Opportunities:
As cybersecurity threats escalate worldwide, skilled penetration testers enjoy excellent salaries, flexible remote work options, and job security across all industries—from finance and healthcare to Cyber defense and cloud computing.
Top Certifications for Penetration Testers
Certifications are crucial for validating expertise and boosting credibility. Popular certifications include:
Holding certifications signals dedication to ethical practice and continuous improvement—essential qualities in cybersecurity.
Want to Take the Lead in Cyber Security ? Enroll in ACTE’s Cybersecurity Expert Masters Program Training Course Program to Begin Your Adventure Now.
Challenges in Penetration Testing
Despite its appeal, penetration testing tools is not without challenges:
To succeed, penetration testers need discipline, adaptability, and relentless curiosity. Staying updated through bug bounty programs, capture-the-flag competitions, and continuous study is key.
The Future of Penetration Testing
The future of ethical hacking guide is deeply intertwined with emerging technologies. As systems become more complex, testing methodologies are evolving to match new challenges.
The next decade will see penetration testers blending human creativity with machine intelligence—creating an era of smarter, faster, and more predictive cybersecurity.
Penetration testing lies at the heart of modern cybersecurity. Ethical hackers are the silent defenders who uncover weaknesses, prevent data breaches, and protect digital ecosystems from chaos.
The career of a penetration tester is not just about exploiting systems—it’s about responsibility, curiosity, and purpose. It requires continuous learning, innovation, and ethical hacking guide integrity. With demand for Cyber defense experts soaring globally, the opportunities in this field are vast and rewarding.
For those drawn to technology, problem-solving, and ethical challenges, becoming a penetration tester offers not only a lucrative career but also the chance to make a real difference in securing the digital world.
Conclusion





