
- What is a Firewalls
- Importance of Firewalls in Security
- Types of Firewalls
- Packet Filtering Firewalls
- Stateful Inspection Firewalls
- Proxy Firewalls
- Next-Gen Firewalls (NGFW)
- Hardware vs Software Firewalls
- Advantages of Firewalls
- Limitations and Challenges
- Best Practices for Using Firewalls
- Future of Firewall Technology
- Conclusion
What is a Firewalls
In the digital age, cybersecurity is one of the most critical aspects of both personal and organizational infrastructure. With the growing number of cyberattacks, data breaches, and unauthorized access attempts, protecting digital assets is a necessity. One of the most widely used and fundamental security mechanisms is the firewall. A firewall can be defined as a network security device or software that monitors, filters, and controls incoming and outgoing network traffic based on predetermined security rules. To build deeper expertise in such protective technologies and stay ahead of evolving threats, explore Cyber Security Training a hands-on program that equips professionals with the skills to safeguard digital assets, implement robust defenses, and respond effectively to cyber incidents. It acts as a barrier between trusted internal networks and untrusted external networks such as the internet. The concept of a firewall originates from physical barriers designed to contain fires; in computing, it prevents malicious data from spreading into secure systems. Firewalls have been around since the late 1980s when early internet communication protocols were still evolving, and security was minimal. Over time, they have evolved significantly, transitioning from simple packet filtering systems to intelligent next-generation firewalls (NGFWs) that integrate features like intrusion prevention, malware detection, and deep packet inspection. Whether deployed in homes, enterprises, or data centers, firewalls remain a core component of cybersecurity architecture.
Importance of Firewalls in Security
The importance of firewalls in modern security cannot be overstated. Without a firewall, computer networks would be exposed to direct attacks from malicious actors, automated bots, and malware spreading across the internet. Firewalls serve as the first line of defense, preventing unauthorized access and enforcing security policies. They help reduce the attack surface of a system by allowing only necessary and legitimate traffic to pass through while blocking suspicious or malicious data. For organizations, firewalls protect sensitive data such as financial information, intellectual property, and customer records. To further safeguard this information at rest and in transit, explore Effective Data Encryption Techniques a detailed guide that covers symmetric and asymmetric encryption, hashing algorithms, and best practices for securing digital assets across enterprise environments. For individuals, they safeguard personal data, online transactions, and private communications. Firewalls are also crucial in regulatory compliance frameworks such as HIPAA, PCI-DSS, and GDPR, where secure handling of data is mandated. They provide visibility into network traffic, making it easier to detect anomalies and respond to threats proactively. Moreover, firewalls play a role in network segmentation by dividing a large network into smaller, isolated zones. This prevents lateral movement of attackers within the network and confines any potential breach to a limited area. As cyberattacks grow more sophisticated, firewalls continue to evolve to address advanced threats, making them indispensable for modern security infrastructures.
Interested in Obtaining Your Cyber Security Certificate? View The Cyber Security Online Training Offered By ACTE Right Now!
Types of Firewalls
Firewalls can be categorized based on their deployment, functionality, and inspection methods. Broadly, they can be divided into traditional firewalls and next-generation firewalls. The main types include: packet-filtering firewalls, stateful inspection firewalls, proxy firewalls, and application-layer firewalls. To understand how these components fit into a holistic security strategy, explore CyberSecurity Framework a structured guide that outlines key security layers, governance models, and best practices for building resilient digital infrastructures.
- Packet Filtering Firewalls
- Stateful Inspection Firewalls
- Proxy Firewalls (Application-Level Gateways)
- Next-Generation Firewalls (NGFWs)
- Cloud Firewalls (emerging category)
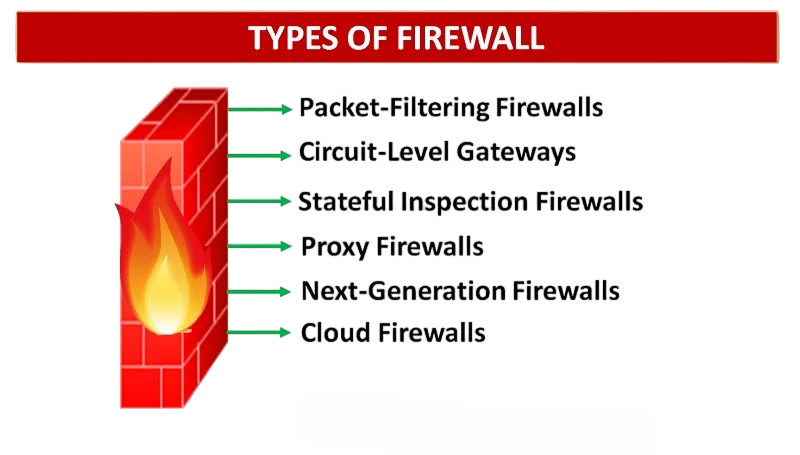
Each type offers different levels of security, performance, and complexity. The choice depends on the network environment, organizational needs, and the nature of threats being mitigated.
To Explore Cybersecurity in Depth, Check Out Our Comprehensive Cyber Security Online Training To Gain Insights From Our Experts!
Packet Filtering Firewalls
The earliest and simplest type of firewall is the packet filtering firewall. This firewall examines packets (the smallest unit of network communication) and allows or blocks them based on rules such as IP addresses, port numbers, and protocols. For example, an administrator may configure a rule to block all traffic from a specific IP address or deny access to certain ports commonly exploited by attackers. While packet filtering is lightweight and efficient, it lacks deep inspection capabilities. To understand how malicious code bypasses such defenses and how to counter it effectively, explore Guide to Malware Analysis a detailed resource that covers static and dynamic analysis techniques, reverse engineering fundamentals, and threat behavior profiling for robust cybersecurity defense. It cannot analyze the payload of packets or determine whether traffic that appears legitimate is actually malicious. As a result, it is vulnerable to sophisticated attacks that disguise harmful content within seemingly safe packets. Despite its limitations, packet filtering remains useful in scenarios requiring basic traffic control with minimal resource consumption.
Stateful Inspection Firewalls
To address the shortcomings of packet filtering, stateful inspection firewalls were introduced. These firewalls maintain a state table that tracks active connections and ensures that only legitimate traffic related to an established session is allowed. For example, if a user inside a network initiates a web browsing session, the firewall allows responses from the web server but blocks unsolicited traffic. To understand and implement such protective protocols effectively, explore Cyber Security Training a specialized program that equips professionals with the skills to configure firewalls, manage network defenses, and safeguard digital environments against evolving threats. Stateful firewalls provide a balance between security and performance. They prevent certain types of attacks like IP spoofing and unsolicited access, making them more secure than packet filters. However, they still lack application-level awareness, meaning they cannot differentiate between malicious and legitimate traffic within the same application protocol.
Looking to Master Cybersecurity? Discover the Cyber Security Expert Masters Program Training Course Available at ACTE Now!
Proxy Firewalls
Proxy firewalls, also known as application-level gateways, act as intermediaries between users and the internet. Instead of allowing direct communication, the proxy firewall receives requests from clients, evaluates them, and forwards them on behalf of the user if deemed safe. This process masks the internal network from external entities, adding an additional layer of anonymity and security. To ensure data integrity alongside network protection, explore Cyclic Redundancy Check a foundational technique used to detect accidental changes in raw data, widely implemented in storage devices, communication protocols, and error-checking systems across secure digital infrastructures. Proxy firewalls can inspect traffic at the application level, meaning they can analyze content such as HTTP requests or FTP commands. This enables them to detect malicious activities hidden in higher-level protocols. They also provide caching, content filtering, and user authentication features. However, because they analyze traffic in greater detail, proxy firewalls can be resource-intensive and may introduce latency.
Preparing for Cyber Security Job Interviews? Have a Look at Our Blog on Cyber Security Interview Questions and Answers To Ace Your Interview!
Next-Gen Firewalls (NGFW)
Next-generation firewalls (NGFWs) represent the modern evolution of firewall technology. They combine the traditional packet filtering and stateful inspection features with advanced capabilities such as:
- Deep Packet Inspection (DPI)
- Intrusion Prevention Systems (IPS)
- Application Awareness and Control
- Advanced Malware Protection
- Integration with Threat Intelligence Feeds
NGFWs are designed to combat today’s complex threats, including zero-day attacks, ransomware, and advanced persistent threats (APTs). They can identify and control applications regardless of port or protocol, making them particularly effective in environments with heavy cloud and mobile usage.
Hardware vs Software Firewalls
Firewalls can also be classified based on their deployment form:
- Hardware Firewalls: These are dedicated physical devices installed at the network perimeter. They provide robust performance, high throughput, and are often used in enterprise environments. Hardware firewalls are harder to tamper with and offer centralized protection for multiple devices.
- Software Firewalls: Installed on individual computers or servers, software firewalls offer protection tailored to a specific machine. They are flexible and easier to configure but consume system resources. They are widely used in personal computers and smaller networks.
In many organizations, a combination of hardware and software firewalls is deployed to achieve layered security.
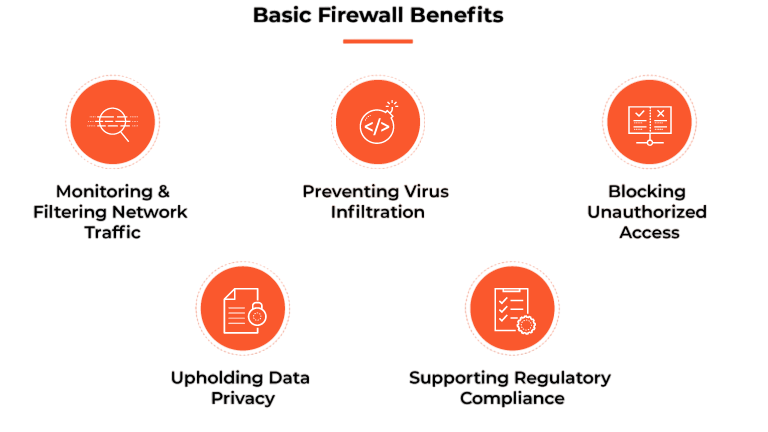
Advantages of Firewalls
The advantages of firewalls include:
- Access Control: They regulate who can access network resources.
- Threat Prevention: Firewalls block malware, unauthorized access, and suspicious traffic.
- Network Segmentation: Isolating critical zones minimizes breach impact.
- Monitoring and Logging: Firewalls provide detailed logs for analysis and compliance.
- User Protection: They safeguard individuals from phishing sites, unsafe downloads, and hacking attempts.
- Policy Enforcement: Firewalls enforce organizational security policies consistently.
Limitations and Challenges
While firewalls are key parts of network security, they have notable weaknesses. These advanced defense tools face complex cybersecurity issues today. They often have trouble dealing with insider threats and inspecting encrypted traffic. Misconfiguration is a constant risk, which can expose networks or block legitimate communications. Additionally, firewalls frequently struggle with new zero-day exploits and can slow down performance in high-speed environments. To enhance visibility and response capabilities across these challenges, explore Tools and Platforms of Threat Intelligence a strategic overview of threat feeds, SIEM integrations, behavioral analytics, and automated response systems that empower organizations to detect, analyze, and neutraliz Acknowledging these limitations highlights the need for a solid, multi-layered security approach that goes beyond traditional firewall protections. This ensures a stronger and more flexible defense for networks.
Best Practices for Using Firewalls
To maximize the effectiveness of firewalls, organizations should adopt best practices such as:
- Regularly updating firewall rules and firmware.
- Implementing least privilege access, allowing only necessary traffic.
- Combining firewalls with intrusion detection and prevention systems.
- Monitoring firewall logs for unusual activity.
- Enforcing strong authentication for administrative access.
- Conducting regular penetration tests to identify weaknesses.
A firewall should always be viewed as one component of a defense-in-depth strategy.
Future of Firewall Technology
As cyber threats evolve, so too will firewall technology. The future of firewalls is expected to be shaped by AI-driven threat detection, adaptive filtering, and deeper integration with endpoint protection systems. To stay ahead of these advancements and understand how attackers think, explore Ethical Hacking a career-focused guide that equips learners with penetration testing skills, vulnerability assessment techniques, and real-world strategies for securing modern digital infrastructures.
- AI and Machine Learning: Automated detection of anomalies and adaptive security.
- Cloud-Native Firewalls: Protection for cloud applications and SaaS environments.
- Zero Trust Architecture: Firewalls will integrate with zero trust policies to verify all connections continuously.
- Integration with SIEM and SOAR: Centralized threat detection and automated response.
- 5G and IoT Protection: Firewalls tailored for high-speed networks and billions of connected devices.
The traditional perimeter-based firewall model is giving way to distributed, intelligent firewalls that secure users, devices, and applications regardless of location.
Conclusion
Firewalls remain one of the most crucial elements of cybersecurity infrastructure. From their early beginnings as packet filters to modern next-generation systems powered by AI, firewalls have consistently adapted to the changing threat landscape. They are essential for controlling access, monitoring traffic, and preventing unauthorized activities in networks. However, they must be complemented by other security solutions and best practices to achieve comprehensive protection. To build a layered defense strategy and master modern security protocols, explore Cyber Security Training a practical course designed to equip professionals with the tools and techniques needed to secure networks, detect threats, and implement end-to-end protection frameworks. The future of firewall technology is promising, with innovations targeting cloud environments, AI-driven threat detection, and support for IoT and 5G ecosystems. For both individuals and organizations, adopting strong firewall strategies will continue to be a cornerstone of robust cybersecurity defense.




