
- The Importance of IPsec in Ensuring Secure Network Communications
- Why IPsec Is Needed
- Components of IPsec
- Authentication Header (AH)
- Payload Encapsulation Security (ESP)
- Modes of IPsec
- IPsec-based VPNs
- Real-world Applications
- IPsec will be in network security in the future
- Conclusion
The Importance of IPsec in Ensuring Secure Network Communications
In today’s hyperconnected world, the Internet has become the backbone of communication, commerce, and business operations. Organizations, governments, and individuals rely on digital networks to share sensitive information, conduct financial transactions, and maintain operational continuity. But there are serious concerns associated with increased reliance on digital security networks. Strong network security is crucial, as cyberattacks, data breaches, eavesdropping, and unauthorized access are becoming increasingly common. Cryptographic protocols are used to secure communications and mitigate these hazards. One of the most widely adopted and practical frameworks for securing IP-based communications is Cyber security Training. Developed by the Internet Engineering Task Force (IETF), IP security is a suite of protocols that protects IP traffic at the network layer, providing VPN security services such as encryption, authentication, and integrity. Unlike application-level protocols such as HTTPS or SSL/TLS, which secure specific applications, IPsec protects all traffic between IP-enabled devices, making it a versatile and foundational digital security solution. IPsec can be used to secure communications between individual computers, between corporate networks, and between users and cloud services. By operating at the network layer, it provides a transparent security solution that does not require modifications to existing applications.
Why IPsec Is Needed
The Internet Protocol (IP), which underlies nearly all modern networking, was initially designed for reliable data delivery, not security.
Standard IP packets lack mechanisms for encryption or authentication, making them vulnerable to a variety of attacks:
- Packet sniffing: Attackers can capture data in transit, potentially exposing sensitive information like passwords, personal details, or financial transactions.
- Spoofing: Cybercriminals can impersonate trusted devices or users to gain unauthorized access to systems or data.
- Replay attacks: Attackers can capture valid data packets and resend them to disrupt communications or gain illicit access.
- Data tampering: Misinformation or damaged data may result from packets being altered while in transit.
- Confidentiality: Encrypts data to prevent unauthorized access.
- Integrity: Ensures that transmitted data is not altered in transit.
- Authentication: Confirms the identity of the sender and receiver.
- Replay protection: Prevents the reuse of captured packets in an attack.
>By implementing these data protection, IP security enables secure and trustworthy communications over inherently insecure networks.
Interested in Obtaining Your Cybercrime Certificate? View The Cyber Security Online Training Offered By ACTE Right Now!
Components of IPsec
IPsec is not a single protocol but a framework of multiple components working together. Its modular design allows organizations to select and configure security features based on their needs.
The key components include: Protocols
- Authentication Header (AH): Ensures authentication and integrity but does not encrypt data.
- Encapsulation security Payload (ESP): Provides encryption, authentication, integrity, and replay data protection.
- Encryption: AES (Advanced Encryption Standard), 3DES (Triple Data Encryption Standard)
- Integrity and authentication: SHA, MD5, HMAC-SHA1, HMAC-SHA256 By combining these components, IP security provides a flexible, scalable, and robust mechanism for securing IP traffic across diverse environments.
- Authentication: Confirms that packets originate from a trusted source.
- Replay protection: Prevents the reuse of captured packets using sequence numbers.
- How AH works: AH adds a header to each IP packet containing a cryptographic checksum. The receiving device recalculates the checksum and compares it with the one in the packet. If they match, the packet is authentic and has not been tampered with.
- Limitations: AH does not provide encryption, so data remains visible to anyone intercepting the traffic. As a result, AH is less commonly used in practice compared to ESP, which offers broader security features.
- Confidentiality: The payload is encrypted traffic to prevent unauthorized parties from reading it.
- Integrity & authentication: Uses HMAC algorithms to ensure data authenticity.
- Replay protection: Prevents attackers from reusing captured packets. ESP supports various encryption algorithms, such as AES and 3DES, as well as hashing algorithms, such as SHA-1 and SHA-256.
- ESP can operate in two modes: transport and tunnel.
- Transport mode: Encrypts only the payload; the IP header remains intact. Ideal for end-to-end communication between two hosts.
- Tunnel mode: Encapsulates the entire IP packet, including the header, inside a new IP packet. Commonly used for site-to-site VPNs, providing stronger security and protecting internal network structures.
- Transport Mode Encrypts only the IP packet payload.
- The original IP header remains unchanged, allowing routers to forward packets normally.
- Used for host-to-host communication, such as client-to-server connections.
- Tunnel Mode Encrypts the entire IP packet, including headers.
- The packet is encapsulated inside a new IP packet with a new header.
- Used for site-to-site VPNs connecting entire networks over untrusted networks like the Internet. Provides stronger digital security and better data protection for network topology information. Tunnel mode is more common in practice due to its enhanced security for network-to-network communications.
- Quicker rekeying and key negotiation
- Improved functionality for authentication and encryption
- Improved assistance for situations involving mobility and remote access
- In contemporary network contexts, IPsec maintains its security, scalability, and resilience through effective key management.
- VPNs for remote access allow individual users to connect safely from far away.
- Site-to-Site VPNs: Link complete networks, including branch and corporate offices.
- All sent data is encrypted traffic, authenticated, and shielded from manipulation thanks to IPsec.
- IPsec-based VPNs are extensively utilized in government, healthcare, financial, and corporate settings.
- Strong security: Provides encryption, integrity, authentication, and replay protection.
- Transparency: Functions independently of apps at the network layer.
- Flexibility: Supports multiple cryptographic algorithms, modes of operation, and key management options.
- Scalability: Suitable for both small-scale deployments and large enterprise networks.
- VPN security integration: Provides a reliable foundation for secure data remote access and site-to-site VPNs.
- Interoperability: Open standards ensure broad support across vendors and devices.
- Complexity: Setting up IPsec can be difficult and calls for knowledge of both cryptography and networking.
- Performance overhead: Processing power is used for encryption and encapsulation, which may result in a decrease in network performance.
- Compatibility concerns: Interoperability issues may arise from variations in vendor implementations.
- Firewall and NAT traversal: Network Address Translation (NAT) devices might make it difficult for IPsec to function; however, NAT-T extensions can help.
- Maintenance: Careful planning and observation are needed to manage keys, policies, and configurations across big networks.
- Corporate VPNs: Secure remote employee access and branch office communications.
- Government and military networks: Protect sensitive communications across global networks.
- Financial services: Ensure secure online banking and interbank communications.
- Healthcare: Secure electronic health records (EHRs) and patient data exchange.
- Cloud security: Connect on-premises data centers to cloud environments through Cyber Security Training .
- Combining Zero Trust Architectures with Integration: Threats can be stopped from moving laterally using IPsec by protecting network micro-segments.
- Cloud-native security: Ongoing development to accommodate multi-cloud and hybrid settings.
- Using post-quantum cryptography strategies to combat new threats from quantum computing will strengthen cryptography.
- Enhanced performance is achieved through hardware acceleration and software implementations that are tuned to minimize overhead Because of its versatility, IPsec will remain essential for network security in the years to come.
Security Associations (SA) Security associations are agreements between devices that define how digital security will be applied. An SA includes details such as which algorithms to use for encryption and hashing, the keying material, and the duration of the association.
Key Management Protocols Manual key management is impractical for large networks. IP security uses the Internet Key Exchange (IKE) protocol to automate the negotiation and distribution of cryptographic keys. IKE ensures that security associations are established securely without human intervention.
Cryptographic Algorithms
IPsec relies on strong cryptography to secure data:
To Explore Cybersecurity in Depth, Check Out Our Comprehensive Cyber Security Online Training To Gain Insights From Our Experts!
Authentication Header (AH)
The Authentication Header (AH) protocol is a core component of IPsec that provides: Integrity verification: Ensures that data has not been altered in transit using cryptographic hashes.
Payload Encapsulation Security (ESP)
The reason ESP is the most popular IP security protocol is that it offers complete security, which includes:
Looking to Master Cybersecurity? Discover the Cyber Security Expert Masters Program Training Course Available at ACTE Now!
Modes of IPsec
IPsec supports two main modes of operation, each designed for different scenarios:
IPsec Key Management
For IPsec communications to be secure data, cryptographic keys are necessary. IPsec uses Internet Key Exchange (IKE) because manual key management is not feasible for big networks.
IKE Phases
Phase 1: Uses public key cryptography or pre-shared keys to create a safe and verified communication connection.
Phase 2: Creates security relationships and negotiates IPsec parameters, such as encryption and integrity methods.
The most recent iteration of IKE, IKEv2, has a number of advantages over IKEv1:
Preparing for Cyber Security Job Interviews? Have a Look at Our Blog on Cyber Security Interview Questions and Answers To Ace Your Interview!
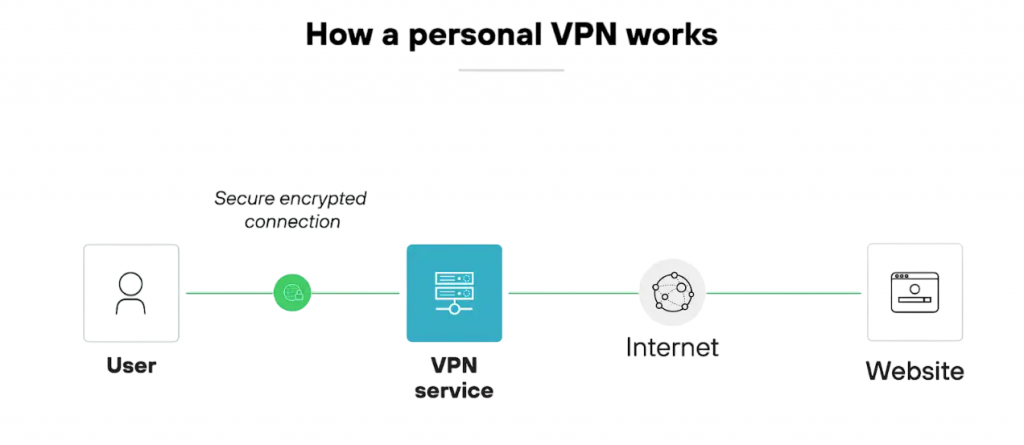
IPsec-based VPNs
One of IPsec’s most significant applications is in Virtual Private Networks (VPNs). By building secure data tunnels across public networks, virtual private networks (VPNs) enable branch offices or remote users to safely access main corporate networks.
IPsec VPN security types
IPsec’s benefits
IPsec offers numerous benefits that make it a cornerstone of modern network security:
By offering these advantages, IPsec enables organizations to protect their data while maintaining operational efficiency.
Restrictions and Difficulties
IPsec has certain drawbacks despite its advantages:
Organizations need to balance security requirements with performance and complexity when deploying IPsec.
Real-world Applications
IPsec plays a critical role in securing modern network communications. Key applications include:
IPsec can be utilized in practically every situation where private, trusted communication is required because of its versatility and strong security.
Cybersecurity Sample Resumes! Download & Edit, Get Noticed by Top Employers! DownloadIn the future, network security will use IPsec
As long as cyber dangers continue to develop, IPsec will continue to be an essential part of network security.:
Important future trends include:
Conclusion
In an era where digital communication drives business, governance, and daily life, securing IP-based networks has never been more critical. Cyber Security Training IPsec addresses this need by providing a comprehensive framework for protecting data in transit. Its combination of encryption, authentication, integrity checks, and replay protection ensures that sensitive information remains confidential, untampered, and trustworthy.
IPsec can secure everything from small host-to-host connections to extensive corporate or governmental networks thanks to its versatility, which includes a range of protocols, modes, and key management techniques. It is essential for businesses looking to protect their communications across public and private networks, thanks to its seamless integration with VPNs, cloud infrastructure, and remote access tools.
NAT traversal, speed overhead, and configuration complexity are some of IPsec’s disadvantages, but they are well exceeded by its benefits. It is a dependable option for a variety of network contexts because of its open standards and cross-vendor support, which guarantee wide compatibility.
In the future, IPsec will develop in tandem with cutting-edge technologies like post-quantum cryptography, cloud computing, and zero-trust architectures, solidifying its place as a fundamental component of contemporary network security.
Take the example of two businesses sharing confidential or financial data online. Any malevolent actor could intercept and read the data if it weren’t encrypted traffic. Without authentication, attackers might hijack communications by impersonating a company. These weaknesses may lead to severe financial losses, reputational damage, or legal repercussions.
To mitigate these concerns, IPsec offers:




