
- What is Sniffing?
- Types of Sniffing Attacks
- Active Sniffing
- Passive Sniffing
- What is Spoofing?
- Different types of Spoofing attacks
- Difference between Sniffing and Spoofing
- Comparing IP Sniffing and IP Spoofing
- Protection against Sniffing and Spoofing
- Conclusion
What is Sniffing?
Sniffing is constantly tracking and recording all information packets that transit through a community. Network or device directors rent sniffers to reveal and troubleshoot community traffic which can be learned in Cybersecurity Training Courses. Hackers use sniffers to seize information packets containing touchy information including passwords and account information. Attackers set up sniffers as hardware or software programs inside the device.
Types of Sniffing Attacks
- Active Sniffing: Active Sniffing is sniffing inside the transfer. It is a community tool that connects points. This transfer video displays units the MAC addresses on every port, which guarantees that information is exceeded handiest to the right destination. To sniff the visitors among targets, sniffers should actively inject visitors into the LAN.
- Passive Sniffing: The technique of Sniffing through the hub is known as passive Sniffing. All machines on an un-bridged or non-switched community phase could be capable of seeing any visitors passing through it. They perform at the information hyperlink layer of the community. A Ethical Hackers Toolkit transmits a community packet throughout the LAN, in which it reaches each gadget linked to it. Attackers can passively seize information via means of sending sniffers. Active Sniffing entails infesting the transfer content material to cope with memory (CAM) desks with decision protocols (ARPs). Consequently, the attacker sniffs information from the transfer by redirecting valid visitors to different ports. There are numerous energetic Sniffing techniques, together with Spoofing, DHCP, and DNS poisoning.
To become a certified cyber security, have a look at our Cyber Security Online Training right now.
What is Spoofing?
Using a spoof to symbolize a conversation coming from a recognized and depended-on supply is Spoofing. It may be as easy as email Spoofing, telecell smartphone Spoofing, internet site Spoofing, or extra technical which includes a pc Spoofing an IP address, ARP, or DNS server. The motive of a Spoofing assault is to benefit from entry to too touchy records or records via means of posing as a sincere supply. Spamming may be completed through websites, emails, telecell smartphone calls, texts, IP addresses, and servers.
Different Types of Spoofing Attacks
-
Caller ID Spoofing
- Spoofing takes region when the caller ID is modified via means of the use of fake statistics. To disguise their identity, telecell smartphone scammers use Caller ID Spoofing to make it not possible to dam a number. In a few cases, scammers will use your location code to hide the decision as being local. Scammers frequently use Voice over Internet Protocol (VoIP) to spoof caller ID via means of growing faux telecell smartphone numbers and names. Scammers will try to get crucial statistics from the decision recipient after they solve the telecell smartphone. Email Spoofing
- Scammers use faux sender addresses to damage your pc, scouse borrows your statistics, or infect your pc with Malware Analysis through email Spoofing. Such emails appear like they got here from a chum or co-worker. This is so you may be fooled into questioning that the emails are legit. Using opportunity numbers or letters to appear barely distinct from the authentic gets you this result, or disguising the “from” subject to come to be a deal with that belongs to a person to your touch list. Website Spoofing
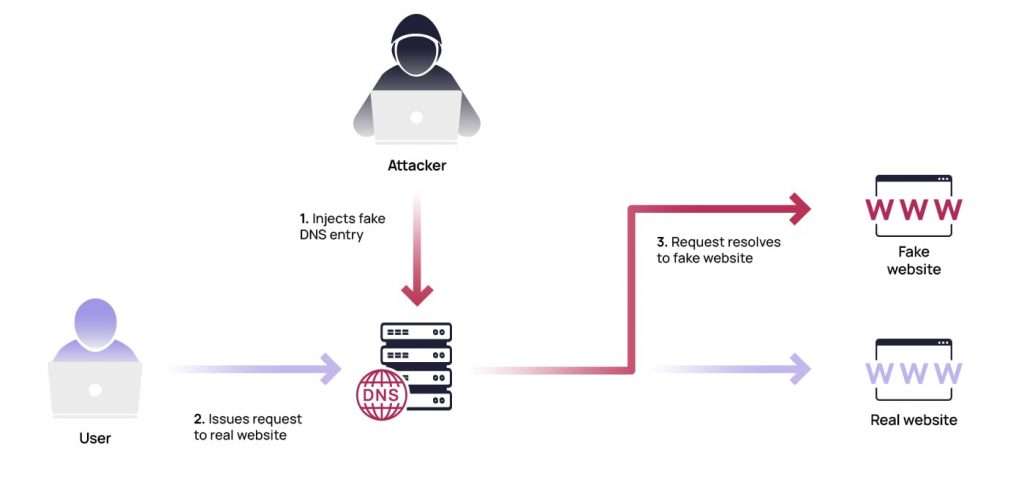
- Scammers use valid fonts, colors, and symbols to make a risky internet site look like a steady one. Scammers reflect a reliance on internet sites so that customers go to a phishing or malicious site. Most of those copied websites’ appearance actually at the beginning look because of the same internet site addresses. Nevertheless, their number one reason is to acquire tourist statistics. DNS Server Spoofing DNS Spoofing, additionally referred to as cache poisoning, is the procedure of rerouting visitors to a distinct IP deal. Malicious websites might be redirected to this page. Scammers try this via means of changing the DNS server`s IP addresses with their own.
- A GPS Spoofing assault happens while faux alerts resemble actual alerts and are broadcast to idiot GPS receivers. Essentially, scammers faux to be in a single place, while, in reality, being in any other place. Scammers use this sort of assault to intervene with GPS alerts of ships, buildings, or aircraft along with to pressure them to incorrect addresses. Apps that depend on the area statistics from a phone are probably liable to this sort of assault. ARP Spoofing
- ARP Spoofing is to control and scouse borrowing statistics in addition to hijack sessions. As a result, spammers will join their media and get entry to manipulate the IP Security deal to get entry to the statistics belonging to the proprietor of that deal. Man-in-the-Middle (MitM) assault
- MitM assaults arise while scammers hack a Wi-Fi community or create the same counterfeit community to intercept internet site visitors among parties. This permits scammers to reroute credit score card numbers or login statistics to themselves. Text Message Spoofing
- The exercise of Spoofing texts happens when scammers use any other person’s telecell smartphone quantity to ship a textual content message. Scammers use alpha-numeric sender IDs to mask their identity, and they generally hyperlink to phishing or malware downloads. Make sure you are acquainted with cell safety tips, in case you worry your statistics are being compromised. Extension Spoofing
- Extension Spoofing is utilized by scammers to mask malware extension folders. These hacker documents are frequently renamed as filename.txt.exe, and feature malware hidden inside. The bug that runs while a record seems to be a textual content report is a textual content report.
Are you curious to know more about Cybersecurity ? Take advantage of our comprehensive online Cyber Security Online Training
GPS Spoofing
Difference Between Sniffing and Spoofing
- Sniffing takes place when an attacker collects statistics packets that skip over a community by making use of packet sniffers and statistics site visitors withinside the community.
- In the assessment of Sniffing, Spoofing occurs when an attacker steals a consumer’s rights and makes use of them to gather valid consumer admission to a gadget to execute assaults towards community hosts, thieve statistics, distribute malware, or steer clear of getting admission to controls.
- Spoofing is when an attacker creates TCP/IP the usage of every other person’s IP address. A sniffer software program is located among interactive endpoints in packet Sniffing, wherein the attacker pretends to be one cease of the relationship to the goal and snoops on statistics dispatched among the 2 points.
Leverage Cyber Security to Unlock the Future! Enroll in the Cybersecurity Expert Masters Program Training Course Program at ACTE Right Away.
Comparing IP Sniffing and IP Spoofing
To apprehend what IP Sniffing and IP Spoofing are, it’s far first vital to apprehend what those phrases mean. The attacker manipulates legal readers to collect treasured records with the aid of falsifying them, so one can experiment with prison tags. Attackers who spoof a machine seem like legal and reliable operators. Spoofing assaults are duplicating elements due to the fact the machine`s legal customers carry out equal action. As against counterfeiting or Sniffing, Spoofing strategies are wonderful for those different kinds of assaults in this Cybersecurity Training Courses . First, allow us to outline packet Sniffing and packet Spoofing earlier than gaining knowledge of their differencesThe method of gathering, collecting, and logging a few or all packets transiting throughout a laptop community is referred to as packet Sniffing. Every packet, or a decided choice of packets, may be collected in this way for the next analysis. As a community administrator, you can make use of the obtained statistics for numerous responsibilities inclusive of bandwidth and visitor monitoring.
Hackers use the IP Spoofing method to hide their places after they ship or request statistics online. By impersonating an IP address, a laptop may be misled into believing that records are being dispatched to it far from a formally legal supply, and malicious content material may be dispatched through A packet sniffer is a software program or approach for taking pictures of community packets without converting them in any way. In easy phrases, packet Sniffing is listening in on different people`s communications. Packet Spoofing is the dynamic presentation of faux community visitors that impersonates a person else.Packet Sniffing is a passive assault when you consider that attackers can’t mutilate the machine in any way.Attackers get the right of entry to the tool or machine that directs visitors inside the packet and perform packet Spoofing assaults with the aid of sending packets with fake supply addresses, i.e., converting routing tables. Encryption is a not unusual place method that is used to combat in opposition to Sniffing, at the same time as virtual signatures are the only approach to fight Spoofing.
Get interview-ready with our collection of Cybersecurity Interview Questions and Answers Questions.
Protection Against Sniffing and Spoofing
The improvement of the era brings increasingly new cyber threats, so staying knowledgeable about safety measures is vital if you want to fight and shield against unlawful hackers. We have indexed some factors that you may comply with to hold your gadgets secure from hackers.
-
Protection towards sniffing
- Set up a robust antivirus for your device
- Secure your records with a VPN
- Avoid travelling unencrypted websites
- Avoid the use of public Wi-Fi
- Do now no longer use unencrypted messaging apps
- Verify the authenticity of customers and systems
- Use Spoofing detection software
- Implement encrypted and authenticated Internet Protocol Address
Conclusion
Sniffing and spoofing are huge cybersecurity threats that take advantage of community vulnerabilities to compromise records’ integrity and confidentiality. Sniffing entails intercepting community site visitors to get admission to touchy records like passwords, usernames, or monetary details, regularly without the user’s knowledge. Spoofing, on the other hand, manipulates records or impersonates relies on entities to lie to customers, probably mainly to unauthorized admission to or malicious actions. Both strategies are typically utilized in superior in Cybersecurity Training, which include phishing or man-in-the-center attacks.





