
- Malware: What is it?
- Malware analysis: what is it?
- Types of Analysis of Malware
- Tools Utilized in Analysis of Malware
- Analysis of Malware Process
- Challenges in Analysis of Malware
- Trends in Analysis of Malware
- Conclusion
Malware is studying and understanding malicious software, more commonly known as malware, in terms of its behaviour, functionality, and impact on infected systems. The key aim is understanding how malware works and spreads, what systems it affects, and how it can be defended against. Accordingly, it has become a crucial component of cybersecurity and ever-growing sophistication concerning Ransomware in Cybersecurity . Cyber Defender helps ensure organizations’ networks, devices, and sensitive information remain intact and secure by detecting, preventing, and rapidly responding to attacks.
Are you curious to know more about Cybersecurity ? Take advantage of our comprehensive online Cyber Security Online Training .
Malware: What is it?
Malware is any malicious software developed to harm or exploit the functions of computer malware systems, networks, or devices. It could include viruses, worms, trojans, ransomware virus, spyware, adware, and other malicious programs. Malware is put to work to steal sensitive data network security, interrupt system operations, and trespass into networks to gain financial, political, or personal profit. There are numerous vectors by which malware can spread- from email attachments to malicious websites, infected software downloads, and even compromised USB devices. When a system is infected, malware may steal personal information, lock the user out of their system (as in the ransomware virus attacks), track browsing activities, or even open “backdoors” for hackers to retain control over infected systems. Malware can be minor, like pop-ups with unwanted ads, serious cyber security breaches and financial losses or a full-scale disruption of services. Since it is malicious, malware poses the biggest Malware Attack . malware detection, prevention, and removal of malware constitute an essential part of the digital defence.
Malware analysis: what is it?
It is the study and examination of malicious software to determine how it functions, acts, and might impact a system or network. The general goal of Cybersecurity Training Courses is to understand how malware works, where it comes from, which vulnerabilities it exploits, and the extent of the damage it might do. Analysis of Malware allows security intelligence professionals to decide on methods of malware detection, mitigation, and prevention of future malware infections.There are thousands, and malware runs the whole spectrum from viruses and worms to trojans and ransomware virus, spyware and adware, and rootkits. All of these include software aimed at disrupting or damaging a computer malware system and also gaining unauthorized access to the latter. Defending against malware threats is of prime importance to understanding how computer malware, whether for individuals, organizations, or network entities.
Want to learn more about Malware Analysis ? Enroll in our Complete Cyber Security Course Online!
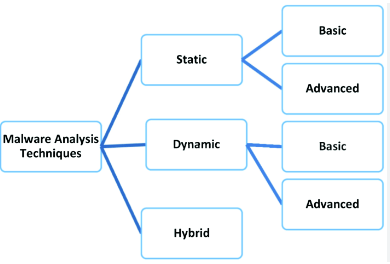
Types of Analysis of Malware
- Analysis of Static Malware:This malware investigation looks for indications of evil intent in files. It is not necessary to have malware code running to do a simple static analysis. It is helpful for exposing libraries, packaged files, or malicious infrastructure. Technical signs such as file names, hashes, and strings like IP addresses, domains, and file header data network security are found in this type of malware investigation.
- Analysis of Dynamic Malware: In dynamic malware analysis, a sandbox, a secure environment, is used to run suspected dangerous code. Because this isolated virtual machine is a closed system, Payloads professionals can watch the malware attentively in activity without worrying about infecting the system or network. This strategy makes a deeper awareness of the threat and its actual nature possible.
- Analysis of Hybrid Malware: Since sophisticated malware can occasionally evade malware detection by sandbox technology, we already know that basic static analysis is unreliable when the infection includes more complex code. Hybrid analysis may extract many more IOCs by statically and previously undiscovered code and uncover buried harmful code. It can identify undiscovered dangers, even from the most advanced viruses.
Tools Utilized in Analysis of Malware
Static Analysis Tools: Static analysis is an important stage in analysis since it involves scanning malicious code without actually operating the code. This methodology helps in the nondestructive examination of malware structure, code, and metadata for some possible malware threats involved.
- IDA Prodisassembler and debugger are the most popular tools. These help to break down malware code to reverse engineer and understand its functionality.
- Ghidra The NSA developed this free reverse engineering software. It helps analyze binary files by enabling disassembly and decompilation.
- PEiD A packer, crypto, and other protection technique detector that identifies the techniques employed to obfuscate malicious code.
- Hex Editors is one of many hex editors that allow an analyst to view and edit the raw byte-level content of a file to reveal embedded strings or encrypted regions of malware.
- Wireshark is a network Cryptojacking that captures traffic between malware and external servers. This information is very useful in understanding how malware communicates.
- Procmon is a system monitor tool that tracks and logs process and file system activities so that analysts can see which processes are interplaying with the system.
- x64dbg robust debugger of Windows-based malware analysis, enabling analysts to step through code execution to know how the computer malware operates.
- Sample Collection:The malware sample is first collected. This may be directly acquired from an infected system; honeypots predisposed to attract attackers, or malware distribution channels like phishing emails or infected websites.
- First analysis and superficial inspection:After the sample has been acquired, preliminary analysis checks if the sample has a file name, details about it in the ‘Attachment’ name, and if it is a step further from the legitimate state of execution. File type: What is it, virus, trojan, ransomware virus or something else? File hash: Make the file a unique hash, for example, MD5, SHA256, to check whether it has ever been analyzed or identified. Strings Observe the file’s string and look for suspicious patterns and IP addresses.
- Static Analysis: Analyzing the malware without running its code: Reverse disassemblers reverse the disassembled code to review its structure. Their analysis will look for known signatures or possible obfuscation techniques.
- Dynamic Analysis:The malware is run in a safe environment, like a sandbox or virtual machine. The activities change files, modify the system, and create network activity. They capture all communicated data network security to external servers-known as the command and control server-for analysis purposes.
- Memory Analysis:Sometimes, malware can run code in memory, preventing it from being caught by traditional malware detection mechanisms primarily based on scrutinizing file-based components. The analysis is at the time of malware execution, which provides analysts with a feel of the system’s state for malicious code buried in system memory.
- Report and Documentation:Once the analysis is done, a report is generated. The report normally includes indicators of compromise (IOCs) like IP addresses, URLs, file hashes, and registry keys associated with the malware. Mitigation techniques would help defend against the attack. Suggestions for recovery and incident response are also included.
- Attribution (Optional):In some cases, research on malware helps determine the source of the attack. This is often resolved by identifying common TTPs the malware uses or tracing it back to known groups of threat actors.
- AI and ML are changing the way malware takes place. These are offering incredibly powerful tools to automate the detection and analysis processes. Since the quantity and complexity of malware grows daily, more than manual analysis is required to tackle the demands. The following are how AI and ML are employed in malware analysis. AI and ML use in malware will grow because these make the analysis processes of complex malware threats faster and extremely efficient.
- The inclusion of threat security intelligence into the malwareworkflows is an undertaking that aims to add contextual context to the comprehension of malicious activities. Firewall And Antivirus Software teams will be able to see potential insights into known families of malware, attack techniques, and IOCs that improve the time for detection and response through threat security intelligence feeds.
- Malware authors are becoming very sophisticated as they develop evasion techniques to thwart the analysis efforts. Such techniques conceal or delay the malicious behaviour of malware so that it is not detected through traditional analysis methods.
- Modern malware techniques nowadays promote a significant emphasis on the use of behavioural analysis in addition to more conventional signature-based methods that are becoming weaker in detecting new or polymorphic malware.
- Two trends, malware attribution and threat hunting, complete post-infection analysis. An attribution process aims to identify the threat actor behind a malware campaign, while threat hunting refers to actively searching for hidden malware threats in a data network security.
Transform Your Career with Cyber Security Knowledge Enroll in ACTE’s Cybersecurity Masters Program Training Course Today!
Dynamic Analysis Tools: An open-source automated malware tool is called Cuckoo Sandbox. That runs the malware in a controlled virtual machine and reports its behaviour, changes in its file system and network activities.
Analysis of Malware Process
Challenges in Analysis of Malware
Malware represents a significant part of cyber security, enabling an organization to identify, detect, and defend against malicious software. However, this field of malware is marred by innumerable challenges since the complexities of attack techniques and Cybersecurity Training Courses Malware analysis are rising every day. Malware is no longer static or simple but highly dynamic, adaptive, and created to evade typical cyber security systems. In this respect, one must mention that analysts are exposed to a number of obstacles in a bid to analyze and control malware risks. Modern malware has resorted to polymorphing and metamorphism to avoid getting detected by antivirus software and traditional antimalware defences. In both of these strategies, the form or format of malware code is changed without changing its functional content. Malware authors are fully aware of the tools and techniques employed by malware analysts. They often create their malware so that it can evade detection when analyzed. Evasion techniques are specially designed to defeat malware analysts by making the malware “aware” of the analysis environment and adapting its behaviour to be inconspicuous. Malware these days is leveraging more and more encryption and anti-tampering techniques to provide itself with better camouflage from analysis.
Preparing for Cyber Security Job Interviews? Check Out Our Cyber Security Interview Questions and Answers .
Trends in Analysis of Malware
Conclusion
Malware is an integral tool in today’s cyber landscape, providing insight into malware’s behaviour, structure, and impact. In a world where seemingly inescapable and alarming levels of cyberattacks become more sophisticated and pervasive daily, the need for effective analysis has never been greater. Analyzing malware using static or dynamic techniques translates to analyzing threats that security intelligence professionals can easily identify, understand, and mitigate well before these threats can inflict harm. Cybersecurity Training has changed in complexity and more advanced evasion tactics in behaviour over time. In such light, the tools and techniques used in the analysis process also took a stride forward.





