
- Introduction
- What is Multi Factor Authentication (MFA)?
- How Multi Factor Authentication Works
- Why MFA Matters
- Types of Multi Factor Authentication
- Implementing Multi Factor Authentication
- MFA Challenges and Limitations
- Future of Multi Factor Authentication
- Conclusion
- Step 1: Authentication of User Credentials – Username and Password: This represents the user’s knowledge, such as a password or PIN. To enhance security, Whitelisting can be implemented, where only approved devices, IP addresses, or applications are allowed to access a system.
- Step 2: Authentication through the second factor – Once the password is inserted, a request to authenticate through another factor is prompted. This can be an OTP message sent to a user’s mobile device, a biometric scan, or an answer to an established security question.
- Step 3: Once both factors are authenticated, access to the system, application, or account is granted.
- Configuring MFA in organizations: An appropriate method should be chosen that would work for the needs of the users and security requirements. These include The best-suited method should be chosen for MFA. This could either be SMS, biometric or hardware tokens.
- Authentication policies should be configured, whether universally enforced for all users or selected ones for specified roles.
- This can further be integrated into login systems, applications, and VPNs. Test the configuration to confirm that users need only get it to work.
- Turning MFA on for personal accounts, such as email, social media, and banking websites, should be fairly simple for individual users. Many services will guide users through configuring MFA.
- Activate MFA on all high-value accounts: Use MFA for email, banking, cloud storage, and work-related systems.
- Activate multiple MFA authentication methods:The system should be available with various MFA methods, such as SMS, app, and biometric authentication in Cyber Security Training Courses.
- Educate users: Users should be informed of why Multi Factor Authentication is important and guided on how to implement it.
- Review and audit MFA configurations: MFA logs should be checked periodically to detect any suspicious activities and update configurations.
Introduction
In this digital world, where the smartest cyber thrusters rule and data breaches are rising, passwords will not be enough. A password alone has to be stolen, guessed, or phished to have your personal information and accounts assailed. However, in a Sandbox Environment, the risk of such breaches can be mitigated. With such weaknesses, a more secure alternative against this emerged in the form of Multi Factor Authentication. MFA Authentication adds yet another layer of safety for users to confirm their identity through something they know, something they have, and finally, something they are. This blog post will explore why MFA authentication is critical, how it works, the different varieties of mfa security, and how both organizations and individuals can implement it to strengthen security.
To Explore Multi Factor Authentication in Depth, Check Out Our Comprehensive Cyber Security Online Training To Gain Insights From Our Experts!
What is Multi Factor Authentication (MFA)?
As a security measure, Multi Factor Authentication (MFA) calls for presenting two different forms of identification to access an account, application, or system. This is contrary to two factor authentication, in which only a password or PIN is used. Adding additional layers decreases the chances of unauthorized access in MFA Cyber Security Training Courses.
MFA combines multiple authentication factors, making it much harder for hackers to impersonate someone else. These factors are usually categorized into something you know, such as a PIN, password, or security question response. Then, you have a physical device, like a smart card, mobile phone, or security token, and finally, something you are, such as biometric data fingerprints, face recognition, or voice patterns. Requiring several factors means that even if one of the factors is compromised, attackers would not be able to gain access to the system with the remainder of the verification factors.
How Multi Factor Authentication Works
Multi Factor Authentication generally works by following a step-by-step process to verify a user’s identity:
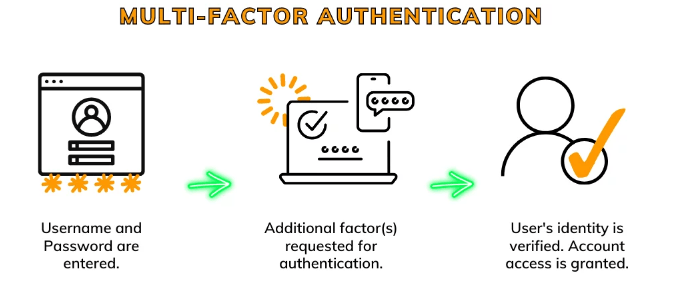
The second factor can be provided in several forms. These should depend on what method of MFA has been selected. Again, the goal is to attain that even if one factor-pwd, for example, is compromised, the additional factor will thwart the attacker.
Interested in Obtaining Your Multi Factor Authentication Certificate? View The Cyber Security Online Training Offered By ACTE Right Now!
Why MFA Matters
1. Protection Against Password Theft
Passwords are the easiest defence against cyber attacks. However, passwords need to be foolproof. Brute force attacks, phishing, and keylogging hacking techniques easily crack the security pass on to passwords. MFA adds a second layer, so the attacker still needs the second factor for access, even if the password might have been compromised.
2. Adding Layers of Defence
MFA creates multi-layered defence that significantly enhances security. The concept is simple: if one layer (password) is compromised, then there are additional barriers (phone, biometric scan, etc.) that the attacker needs to leap over to penetrate the account. This approach is essential in Web Application Security, where multiple layers of authentication (such as multi-factor authentication) are used to protect sensitive data and prevent unauthorized access.
3. Compliance with the Acts
In most industries, but particularly those dealing with customer information and data, MFA is more of a must than a best practice; businesses are subject to regulation and statute. There is PCI-DSS for payments, HIPAA for the healthcare industry, and GDPR related to data protection; these mandate that businesses strengthen their security to include MFA.
4. Phishing and Social Engineering Defence
One of the most popular techniques cybercriminals use to steal login credentials is phishing. The phishing attack involves impersonating a trusted entity, where an attacker tricks the user into revealing a password. But when MFA is implemented, even though an attacker can obtain the password, he will still require his second factor for access, hence lessening the capability of phishing attacks.
Implementing Multi Factor Authentication
1. MFA Configuration
2. Best Practices with MFA
Are You Considering Pursuing a Cybersecurity Master’s Degree? Enroll For Cyber Security Expert Masters Program Training Course Today!
Types of Multi Factor Authentication
MFA has many flavours, each with a compromise between security and convenience. The most common is described below:
1. SMS and Email-Based Authentication
In this type, a one-time passcode (OTP) is delivered to the user by email or SMS, and the user uses this OTP to complete the login process. Although this method is widely used simply because of its ease of implementation, it could be safer. The SMS may be tapped, and email accounts are frequently subject to phishing attacks.
2. Authenticator Apps
Authenticator apps include Google Authenticator, Authy, and Microsoft Authenticator, which produce time-sensitive codes that users enter to authenticate the login. Authenticator apps are safer than SMS because their contents are locally generated on the user’s device and cannot, therefore, be intercepted. In contrast, techniques like Google Dorking can be used to uncover sensitive information from publicly available data online, potentially exposing vulnerabilities that could be exploited by attackers. They do not also require an internet connection for functionality.
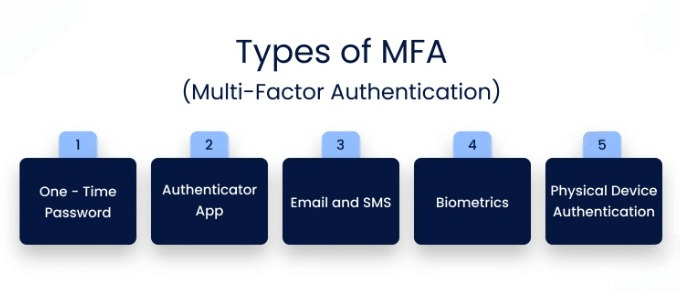
3. Biometric Authentication
Biometric authentication authenticates a user’s identity using unique physical features. The most popular are fingerprint recognition, facial recognition, and iris scanning. Thus, biometric authentication is very secure and is increasingly used on smartphones and other devices because of its convenience and accuracy.
4. Hardware Tokens
These tokens will add more layers of authentication on the physical sides, thus being comparable to the most widely used USB security key (e.g., YubiKey). They authenticate the user by allowing one-time passwords or by tapping the key physically. Hardware tokens are considered the most secure form of MFA since they contain the smallest chance of phishing and man-in-the-middle attacks.
Want to Learn About Cyber Security? Explore Our Cyber Security Interview Questions and Answers Featuring the Most Frequently Asked Questions in Job Interviews.
MFA Challenges and Limitations
1. User Experience and Adoption
MFA can sometimes be more of a pain-in-the-neck, especially when extended to several additional steps or requiring additional things a user needs to carry along-for example, hardware tokens. User-friendliness and flexible options help adoption.
2. Backup and Recovery
Accounts may not receive the second factor, such as a phone or hardware token, and users may not be able to access their accounts. Recovery options, such as backup codes or other verification methods, are required.
3. Cost and Implementation Complexity
Implementing MFA is expensive and complex for an organization, mainly when layered on top of existing systems. However, investing in Network Penetration Testing can help identify vulnerabilities in the network before they are exploited. Yet the security payback pays for this multiple times over, particularly in the light of the probable expense of a data breach.
Future of Multi Factor Authentication
The future of MFA will embrace even more advanced technologies in behavioural biometrics, continuous authentication, and passwordless authentication. This idea would be that authentication should be much more secure but still smooth for the user. Since cyber threats are perpetually changing, MFA would never be relevant to a cybersecurity strategy.
Conclusion
It is one of the most effective ways to protect online accounts, sensitive data, and digital systems from unauthorized access. MFA authentication achieves this by using more than one form of authentication to access the target account, making it highly difficult for hackers to breach accounts even in cases where login credentials have been stolen. However, being flawed, Multi Factor Authentication significantly enhances Cyber Security Training Courses in tandem with regulatory compliance. Whether a personal account needs to be secured or a business needs to secure data for customers, MFA is one important step toward building a robust security strategy. By embracing MFA, you’re taking an important step toward securing your digital world against the rising threat of cybercrime.





