
- What is Network Penetration Testing?
- Why is Network Penetration Testing Important?
- Types of Network Penetration Testing
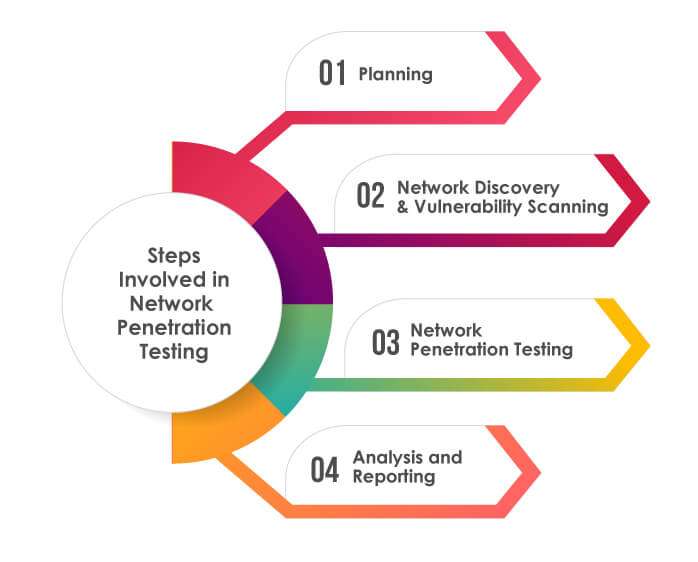
- The Penetration Testing Process
- Best Practices for Effective Penetration Testing
- Conclusion
Cyber threats have increased in recent times. Organizations must implement robust security measures to protect their networks. Among the essential cybersecurity strategies, penetration testing emerges as an essential aspect. This guide elaborates on security penetration testing, why it is important, the methodologies used during the process, and good practices. One crucial step in penetration testing is Enumeration in Ethical Hacking, which involves gathering detailed information about the target system or network. During this phase, ethical hackers identify open ports, services, and other potential vulnerabilities, laying the foundation for more in-depth testing and helping to pinpoint weaknesses before they can be exploited by malicious actors.
Are You Interested in Learning More About Network Penetration Testing? Sign Up For Our Cyber Security Online Training Today!
What Is Network Penetration Testing?
Pen testing, short for Network Penetration Testing, is an emulated Cyber Security Training Courses designed to test the computer network. Penetration testers can reproduce the tactics, techniques, and procedures associated with malicious actors, thereby discovering the vulnerabilities of a network’s infrastructure, including components such as servers, firewalls, routers, and endpoints. The most fundamental objective of penetration testing is the identification of weaknesses before real attackers use them.
With this approach, an organization can enhance security measures to avoid a highly vulnerable network environment. Network penetration testing provides organizations with valuable insights into security posture and incident response capabilities. Businesses can evaluate how effectively their security protocols and tools respond to threats by simulating real-world attacks. This helps pinpoint specific vulnerabilities and highlights areas where staff training and awareness may be lacking. Consequently, organizations can prioritize their security investments and develop more robust incident response plans, ultimately creating a more resilient defence against potential cyber threats.
Why is Network Penetration Testing Important?
- One of penetration testing’s biggest benefits is its ability to reveal any existing vulnerabilities in a system. Companies may contain unpatched software, misconfigured devices, or weak passwords that can be exploited.
- By exposing such issues, companies would be given the leeway to take action before a breach occurs. Through penetration testing, real attacks are simulated.
- One effective way to identify these vulnerabilities is through Vulnerability Scanning, which involves using automated tools to scan systems, networks, and applications for known security flaws.
- This is where weaknesses are detected. Once that is established, an organization can start working on the changes needed in its defences.
- This might involve applying software patches, strengthening authentication protocols, or improving firewall rules.
- Many organizations operate under regulatory policies that need to be reviewed periodically. Penetration testing helps organizations fulfil such needs and prevent resulting fines and lawsuits.
- This process advances organizations’ incident response capabilities, allowing them to recognize gaps in their response strategy and refine it to minimize damage from a real breach.
To Explore Network Penetration Testing in Depth, Check Out Our Comprehensive Cyber Security Online Training To Gain Insights From Our Experts!
Types of Network Penetration Testing
External Penetration TestingThis type focuses on the outside of the network, thereby checking the strength of external defences against harmful influences from the outside world. Testers simulate an attack on firewalls and try to exploit exposure in outwardly accessible services.
Internal Penetration TestingThis type of test involves simulating an attack from within the organization by an individual, usually done by an insider or an attacker who has already bypassed the external defences. It checks for all possible vulnerabilities that disgruntled staff may use or compromised accounts.
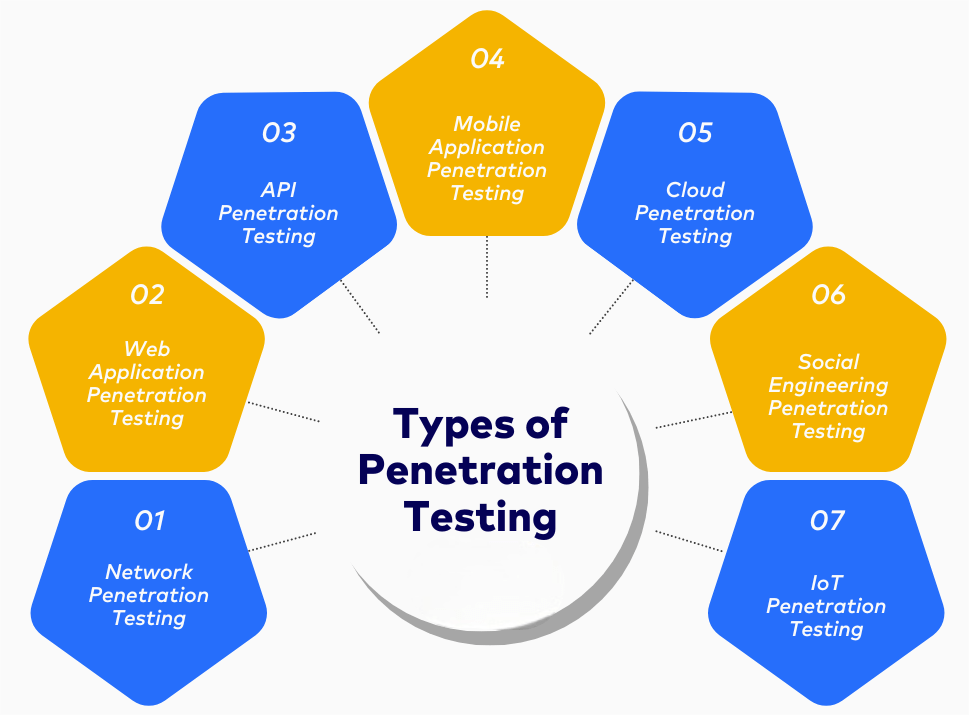
Blind testing involves giving the testing team a minimum of information about the network. In this type, the team performs the test from the perspective of a real attacker. This type tests the organization’s ability to detect and respond. During blind testing, tools like Firewall and Antivirus Software are crucial for defending the network.
Double Blind TestingNeither the testing team nor the organization’s IT staff is informed about the test. This helps understand how well the organization reacts to surprise attacks. The unawareness aspect simulates a real-world scenario where cyber attackers don’t provide any warning before launching an attack.
Targeted TestingTargeted testing is a combined effort of the penetration testers and the organization. It shares information about the network and aims at specific issues of concern. This method can be used to test the vulnerabilities identified in depth.
Web Application Penetration TestingThis testing is not restricted to networks but rather focuses on the web application that interacts with the network. Testers assess how the application safeguards against general web vulnerability.
The Penetration Testing Process
This penetration test definition phase also includes the scope and objectives of the test. As part of it, one identifies which systems to test and what methodologies need to be used for testing. Cyber Security Training Courses gather as much information as possible about the target network. There may or may not be active and passive reconnaissance in this step, including scanning for open ports, mapping the network, and scouring social media and public resources for information. Once all the data is collected, the testing team conducts vulnerability testing.
Are You Considering Pursuing a Cybersecurity Master’s Degree? Enroll For Cyber Security Expert Masters Program Training Course Today!
Known system vulnerabilities can be applied with automated tools and can be determined using the provided information. Once it has passed the network, it is measured how far into the system it can go. During this phase, it is determined to what extent an attacker would cause harm and what information they could access. The final step is forming a detailed report detailing outcomes from the penetration test. This report should include an executive summary, identified vulnerabilities, methods used and actionable recommendations for remediation.
Best Practices for Effective Penetration Testing
Clear ObjectivesOrganizations are required to clearly define their penetration test objectives before commencing such tests. This involved identifying the scope of the test and what is hoped to be achieved or attained.
Engage QualifiedPenetration testing requires specialized skills and careful planning. Hiring an experienced professional or reputable testing firm can ensure the test is performed ethically and effectively. One of the critical phases in penetration testing is Reconnaissance in Cyber Security.
Regular TestingCyber threats are constantly evolving, so penetration testing should ideally be conducted at regular intervals. Organizations should find the time to test at least yearly and whenever any major changes are made to the network.
Preparing for Cyber Security Job Interviews? Have a Look at Our Blog on Cyber Security Interview Questions and Answers To Ace Your Interview!
Keep CommunicationCommunication between the penetration testing team and the organization is also vital. The scope, methodologies, and possible impacts of the test should be discussed so that everyone is on the same page.
Implement Remediation MeasuresOnce vulnerabilities are identified, organizations must act rapidly to address them. This may involve patching systems, reconfiguring security protocols, or introducing new technologies.
Continuous MonitoringAfter penetration testing, a network needs to be continuously monitored for possible threats or vulnerabilities that could arise later. Implementing an Intrusion Prevention System (IPS) is crucial for this ongoing protection.
Conclusion
Network penetration testing should be an integral part of any all-rounded Cyber Security Training Courses strategy. This gives organizations the perfect opportunity to simulate attacks in the sense that it will provide hints on vulnerabilities, improve their security posture, and prepare for real threats. Indeed, for this reason, investing in penetration testing is not only a best practice but a necessity that organizations, in trying to protect their assets and maintain clients’ trust, cannot afford to ignore. By routinely testing their systems and having effective remediation measures, organizations will be one step ahead in this ever-evolving world of cybersecurity. This way, organizations can greatly reduce the risk to their networks and strengthen defences against a swelling tide of cyber threats by taking proactive approaches to network security. Regular Network Penetration Testing fosters a culture of security awareness within the organization. When employees understand the importance of identifying and mitigating vulnerabilities, they are more likely to adopt security best practices daily. This collective vigilance enhances the organisation’s security posture and empowers employees to recognize and report suspicious activities, creating a proactive defence mechanism.





