
- What is an Intrusion Prevention System (IPS)?
- Why is IPS Important?
- How Does IPS Work?
- Types of Intrusion Prevention Systems
- Best Practices for Implementing an IPS
- Conclusion
Cybercrime is not a new phenomenon in the evolving landscape of cybersecurity. It is one of the common threats that most organizations face when performing different operations. The one tool that can assist in safeguarding security architecture strongly is the Intrusion Prevention System or IPS. This blog outlines and explains what an IPS is, why it is significant, how it works, the different types, and best practices. Alongside an IPS, Firewall and Antivirus Software also play crucial roles in defending against cyber threats by offering perimeter security and protecting systems from malware.
Interested in Obtaining Your Cyber Security Certificate? View The Cyber Security Online Training Offered By ACTE Right Now!
What is an Intrusion Prevention System (IPS)?
An Intrusion Prevention System (IPS) is a network security technology that monitors network and/or system activities for malicious actions and policy violations. An IPS can take action to prevent detected threats, which makes it one of the most important tools in defence against Cyber Security Training Courses. An IPS typically examines network traffic to determine suspicious pattern types or known attack signatures and can automatically block or alert administrators about potential intrusions. The IPS protects computer infrastructure but, at its core, is a monitoring tool and a barrier.
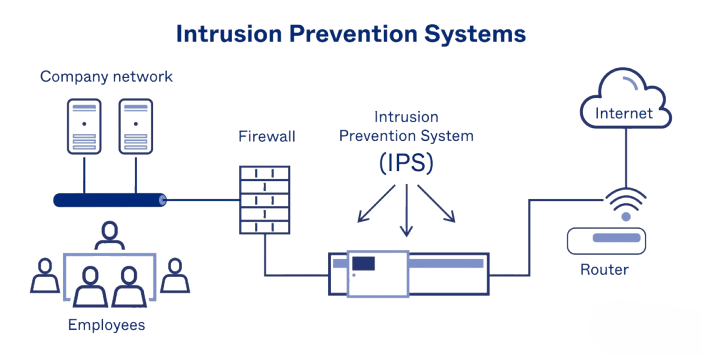
Threat detection and prevention, an IPS can also enhance overall network performance and efficiency. By filtering out malicious traffic before it reaches critical systems, the IPS helps reduce the burden on network resources, allowing legitimate traffic to flow more freely. This optimizes bandwidth usage and improves the responsiveness of applications and services running on the network. Furthermore, with advanced analytics and machine learning capabilities, modern IPS solutions can adapt to emerging threats and attack vectors, providing organizations with a dynamic defence mechanism that evolves alongside the ever-changing cybersecurity landscape. This adaptability ensures that organizations maintain a strong security posture in the face of new and increasingly sophisticated cyber threats.
Why Is IPS Important?
Real-Time Threat PreventionWith IPS, threats can be detected and responded to in real time. Unlike traditional firewalls that block unauthorized access, an Intrusion Prevention System can identify and respond to threats as they emerge, thus removing the risk of successful attacks.
Protection from Known as well as Unknown AttacksAn IPS can detect known attack signatures by storing a threat intelligence database. In addition, advanced systems employ anomaly detection methodologies wherein threats can be identified based on their anomalies from normal behaviours, thus assisting in detecting new or unknown threats.
Compliance and Risk ManagementMost industries have regulations that are quite stringent about protecting data and privacy. An IPS installation helps organizations achieve this mandate by offering needed security controls and documentation for auditing purposes. In addition, Vulnerability Management is a key process that complements the functionality of an IPS.
Improved Incident ResponseIPS can automatically react to threats, such as blocking bad IP addresses or shutting off particular services. This significantly improves the speed and efficiency of incident response, which reduces the volume of damage an attack may inflict.
Visibility and ReportingIPS solutions provide detailed logs and reports of activity in your network. These help security teams investigate incidents, understand attack vectors, and thus modify their security strategy correspondingly.
To Explore Cybersecurity in Depth, Check Out Our Comprehensive Cyber Security Online Training To Gain Insights From Our Experts!
How does IPS Work?
An IPS continually monitors network traffic for potential suspicious activities. It captures packets, analyzes them against predefined security policies, and determines the activities that must be stopped. It compares traffic patterns to known attack signatures in a database. On finding a match, the IPS can carry out predefined actions on that traffic, like blocking it. Anomaly detection sets up a baseline of normal network behaviour to pick deviations from it. It can capture even zero-day attacks or newly discovered threats. An Intrusion Prevention System plays a critical role in incident response and forensics by providing detailed logs and alerts documenting network activity. These logs are invaluable for Cyber Security Training Courses teams as they investigate incidents, allowing them to trace the events leading up to a potential breach. By analyzing these records, organizations can gain insights into attack vectors, identify vulnerabilities, and improve their defensive measures. Moreover, integrating an IPS with other security tools, such as Security Information and Event Management (SIEM) systems, enhances the overall security framework, enabling a more coordinated and efficient response to threats.
Types of Intrusion Prevention Systems
Network-Based Intrusion Prevention System (NIPS)NIPS is a network-level deployment that tracks every single movement in the whole network. It reads the packets being passed through routers and switches and finds efficacy in protecting multiple devices.
Host-Based Intrusion Prevention System (HIPS)In HIPS, the deployment is installed on individual devices or servers. It tracks events and activities on the host and pinpoints suspicious behavior. HIPS protects particular points of entry from attacks that may target such points. Similarly, Intrusion Detection Systems play a complementary role in cybersecurity by monitoring network traffic for signs of malicious activity.
Are You Considering Pursuing a Master’s Degree in Cybersecurity? Enroll in the Cyber Security Expert Masters Program Training Course Today!
Wireless Intrusion Prevention System (WIPS)WIPS secures wireless networks. It detects threats to wireless communications, such as unauthorized access points, rogue devices, and other threats, and thus ensures the integrity of wireless connections.
Cloud-Based Intrusion Prevention SystemCloud services are increasing, and cloud-based IPS adoption is also increasing. Cloud-based systems monitor and protect cloud environments, reflecting flexibility and adaptability in handling security management.
Hybrid Intrusion Prevention SystemsThese are systems that merge network-based and host-based systems. The result is an infrastructure that offers comprehensive protection across multiple layers.
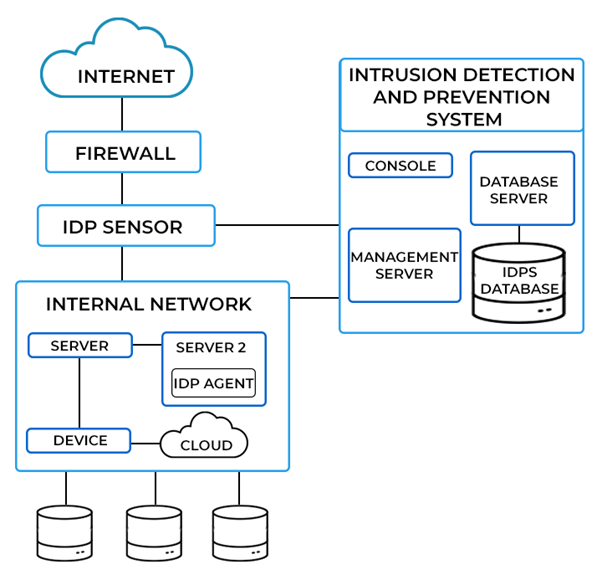
Best Practices for Setting Up an IPS
- Clearly Define Security Policies: Define security policies regarding normal and abnormal network behaviours. Such policies will help fine-tune the IPS for better detection and response.
- Update IPS Signature Databases: To defend against new threats, the IPS signature databases should be updated periodically. This includes new known attack signatures and the algorithm’s updates for anomaly detection. By integrating Threat Intelligence feeds, the IPS can receive real-time information on emerging threats and vulnerabilities.
- Monitor the Impact on Performance: Monitor that an IPS may impact network speed and resource usage. System performance should be scrutinized and settings optimized to balance security and performance.
- Regular Audits and Testing: Periodically evaluate the effectiveness of the IPS through penetration testing and security audits. This will help highlight any gaps in security and ensure that the IPS is working as intended.
- Integration with Other Security Solutions: When planning a comprehensive security strategy, the IPS can be integrated with all other security measures, such as firewalls, antivirus solutions, and SIEM systems. This will initiate a multi-layered defence strategy.
- Training the Security Personnel: Security teams should be trained to use and manage the IPS. These should be knowledgeable about alert logs, response protocols, and maintenance practices about the IPS.
Go Through These Cyber Security Interview Questions and Answers to Excel in Your Upcoming Interview.
Conclusion
An IPS is an important part of a complete cybersecurity plan. Such a system provides real-time monitoring, threat detection, and automated response capabilities, keeping networks safer within an organization from contemporary cyber threats. An IPS can never be overemphasized with the ever-increasing prevalence of complex Cyber Security Training Courses that are common today. By implementing a best practice-based IPS, organizations can bring much-appreciated strength to the security posture, protect sensitive data, and keep their business aligned with regulation requirements. With threats still morphing, organizations will find greater significance in security solutions like IPS to stay ahead of the risks. An effective Intrusion Prevention System serves as a frontline defence mechanism and generates valuable insights through detailed logging and reporting of network activities. These insights allow security teams to analyze attack patterns, understand potential vulnerabilities, and refine their security strategies over time. By integrating the IPS with other security measures, such as firewalls and threat intelligence platforms, organizations can create a holistic security environment that enhances their ability to detect, respond to, and recover from attacks. As cyber threats evolve and become more sophisticated, adapting and strengthening security measures will be crucial for organizations aiming to safeguard their assets and maintain trust with customers and stakeholders.





