
- Describe DNS hijacking?
- How was DNS hijacked?
- What causes the hacking of DNS servers?
- Types of DNS Hijacking Attacks
- How Can DNS Hijacking Be Prevented?
- Instruments for DNS Hijacking
- Conclusion
DNS Hijacking, an assault called DNS hijacking, makes use of DNS queries to ship customers to nefarious websites or pop-up ads. People who aren’t online criminals make use of DNS Names. In order to reroute your visitors for their very own purposes, ISPs can also additionally probably hijack your DNS. Not lengthy ago, DNS hijacking was believed to be gone. Numerous agencies and establishments were in the situation of Domain Name System hijacking, including Gmail, Netflix, and PayPal.There are moderate versions of how those attacks are carried out, regardless of the reality that all of them perform at the equal underlying idea of Domain DNS name exploitation. We’ll speak more approximately those wonderful assault types below. The entire URL that we kind into our browser is called a completely certified area call (FQDN)
Describe DNS hijacking.
Each of those factors serves as a stand-in for a DNS server that takes components inside the system Domain Name Server request process. To find out the region of the area, your browser first sends a question to the DNS Names resolver. The DNS server for the TLD gets this request from the resolver, which then directs it to the DNS server for the website. Any hyperlink in this “chain” will be taken over. Currently, your ISP will robotically configure and install your DNS settings (or Google). These corporations can use those alternatives to power you to websites and content material with the intention to earn them, acquire records, and both. In a Domain DNS hijacking assault, Malware Attack compromise DNS servers or gadgets to modify System Domain Name Server facts or settings. This permits them to intercept and redirect customers` net visitors to faux websites designed to scouse borrow touchy records, set up malware, or perform phishing schemes.
There are 3 additives to this call: a top-degree area (TLD), a sub-area, and a host. These additives stand in for a DNS server that participates in the DNS request procedure. Your browser first queries the Domain name and server resolver to decide the region of the area. The resolver then forwards this question to the DNS server for the TLD, which, in flip, requests the DNS server for the website. Any step alongside this “chain” is open to hijacking. Currently, your DNS Names settings may be robotically configured and setup via way of means of your ISP (or Google). These agencies can direct you to websites and clothes with the intention of taking advantage of them in addition to gathering records via way of means of the usage of those alternatives. This call is made of 3 parts: a host, a sub-area, and a top-degree area (TLD).
Become an expert in Domain Name System . Enroll in thisCyber Security Course now to acquire the knowledge you need.
How is DNS Hijacked?
Cybercriminals are conscious that the area called the machine of your internet site is a particular, straightforward protocol and that many businesses overlook to test their websites for malicious activities. They may be capable of efficient behaviour in quite a number of attacks in opposition to the company’s Domain Name System . Domain name and server is a carrier that adjustments Internet Protocol (IP) addresses from sentient URLs. Internet customers can use it to seek queries to pertinent websites as a result. Every internet-related tool is assigned a numerical IP address. Website proprietors and customers can use particular net addresses due to the fact the NDS is obliged to synchronize hostnames with IP addresses.
What causes the hacking of DNS servers?
There are numerous methods to hack a Domain DNS server. The Session-hijacking would possibly rent it for phishing or pharming, which includes displaying customers’ marketing and marketing so that you can make money (redirecting customers to a bogus model of your internet site so that you can scouse borrow information or login information).ISPs additionally rent area redirection to manipulate consumers` System Domain Name Server requests so that you can assemble person information. Other groups additionally rent area hijacking to dam customers or reroute them to one-of-a-kind websites.
DNS hijacking can arise in numerous ways, such as:
- Router-primarily based totally hijacking: The attacker profits get entry to the victim’s router and adjustments its DNS name settings.
- Man-in-the-center attacks: The attacker intercepts and modifies Domain name and server requests during transmission.
- Compromised DNS servers: The attacker at once manipulates DNS servers to redirect visitors.
Preventing DNS hijacking includes using strong passwords, updating firmware and software, permitting Domain DNS protection Resolution Protocol like DNSSEC, and tracking suspicious domain names and DNS server activities.
Types of DNS Hijacking Attacks
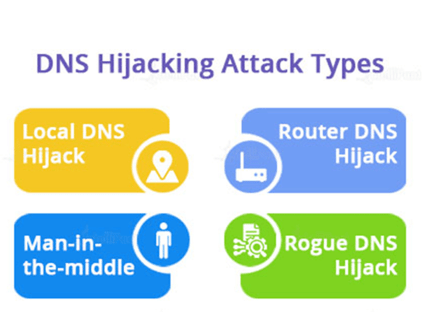
- Local DNS Hijack: When a web crook installs a Trojan virus on an internet site person`s machine, they make use of this Cybersecurity DNS hijacking technique. This trojan poses as straightforward software. When it grew to become one, it offered hackers admission to community system domains. It gave them the danger of scouse borrowing records and altering Domain Name Server settings to reroute customers to phoney websites.
- Router DNS Hijack: Using a domain name and DNS server router is prone to be overridden and reconfigured, hackers behaviour a domain Domain name and server attack (a hardware tool utilized by area provider companies to hyperlink their domains to equal IP addresses). The perpetrators will then weigh down the internet site with site visitors and reroute it to every other malicious internet site, blockading the person from getting admission to the authentic internet site.
- DNS Man-in-the-Middle Hijacking: This takes place while hackers save you, a community person, from speaking with a DNS server, in the end rerouting the person to an unidentified vacation spot IP deal with main to malicious websites. It is likewise called DNS Name spoofing.
- Rogue DNS Hijack: An attacker hijacks the DNS server, and alters the information it has saved, after which redirects any resulting system Domain Name Server requests to their malicious websites.
How Can DNS Hijacking Be Prevented?
Install malware-blocking software Additionally, domain DNS hijackers attempt to attain users` login information. To prevent online crooks from exposing your passwords, deploy antivirus software programs on your computer. Use the simplest, stable digital personal networks to decrease your threat of facts exposure. To similarly stable your credentials, create tough passwords and alternate them frequently. Check the domain Domain name and server settings at the router may be attacked, and hijackers take gain of this vulnerability to prey on unsuspecting victims. For security, test and double-test the Cybersecurity DNS Names settings in your Network Topology
Additionally, its passwords need to be stored as much as date. The Domain Account Registry Lock feature must be enabled. Using a registry lock towards cyber threats is any other manner to prevent Cybersecurity DNS hijacking. An area-call registry can perceive illegal area modifications, transfers, and removals with the aid of using the use of a carrier known as a registry lock. Look for a web website hosting company that gives this feature if yours still needs to. Turn on two-thing authentication to your area account as an additional degree of security.
To learn about different DNS Hijacking techniques, sign up for our Cyber Security Course right now!
Instruments for DNS Hijacking
- ZoneWatcher
Automation of domain name and DNS server device tracking, reporting, and backup is the purpose of ZoneWatcher. With this programme, you may continually have a backup replica of your Cybersecurity DNS statistics in case something is going incorrect; otherwise, you want to get over a sudden change in the System Domain. You can have a look at the whole records of adjustments for the entire sector in its great changelog. If you use it with several clients, ZoneWatcher, that’s more often than not designed for expert use, permits you to reveal domain names from numerous providers. The potential to divide the tracking personnel into groups in step with the managed entity is another function of this device. The information can be exported as sector documents or notified through a REST API, and the indicators may be added through email.

- StatusCake
The StatusCake area checking device indicators you when it’s time to resume your location in order that squatters don’t take over your internet site and damage your commercial enterprise in case you overlook signing in on time. You can maintain music of adjustments in your DNS Names statistics through Web Security . Three plans are to be had from StatusCake, the preliminary of which is unfastened with some regulations and a 5-minute sampling window. Free trials are also supplied for top-rate offerings that consist of more functions such as SMS notifications, 30-2nd assessment intervals, and collaboration tools.
- AppNeta
Despite being bendy to any community architecture, AppNeta’s DNS tracking technique is, in particular, properly applicable for agencies who are inside the technique of migrating to the cloud. The records that AppNeta gathers are saved on a report for 12 months at no cost. You can see how domain Cybersecurity DNS decision impacts the consumer enjoy of your software through studying that information. Deteriorating developments in overall performance, in addition to styles in overall performance spikes, can each be identified. The software context is brought to the tracking service’s reviews to assist IT personnel in discovering DNS decision problems connected to software problems.
Preparing for a job interview in ethical hacking? Examine our blog post about Cyber Security Interview to get the most of your employment experience!
Conclusion
Hackers and deceivers have used many techniques to retrieve personal records because of the internet’s beginnings, including DNS hijacking. Many techniques are solely beneficial for the domain name and DNS server-associated problems. DNS hijacking is a considerable cyber danger that may result in extreme results for people and agencies, along with unauthorized get admission to touchy records, monetary losses, and compromised device integrity. This assault manipulates the Domain Name System (DNS) to redirect customers to malicious websites or services, frequently without their knowledge. To mitigate such dangers, agencies need to undertake sturdy cybersecurity practices, along with using DNSSEC ( Security Extensions), common updates to Cybersecurity DNS server software, and tracking domain names and DNS server hobbies for suspicious behaviour. Educating customers approximately phishing and making sure stable community configurations similarly enhance defences. Proactive measures and vigilance are important to guard towards the developing dangers related to DNS hijacking.





