
- Introduction to DES (Data Encryption Standard)
- Historical Development
- Structure of DES (Feistel Network)
- Key Size and Rounds
- Encryption and Decryption Process
- Modes of Operation (ECB, CBC, etc.)
- Strengths of DES
- Weaknesses and Vulnerabilities
- DES vs AES
- Practical Applications
- Legacy Systems Still Using DES
- Summary
Introduction to DES (Data Encryption Standard)
DES is a block cipher algorithm that Data Encryption in 64-bit blocks using a 56-bit key. It was developed by IBM and later modified and adopted by the U.S. National Bureau of Standards (now NIST). In Cyber Security Training , it’s essential to understand that the algorithm uses a symmetric key approach, meaning the same key is used for both encryption and decryption. DES became the cornerstone of early data encryption systems and was widely implemented in commercial and governmental systems.The Data Encryption Standard (DES) is a symmetric-key algorithm used for the encryption of digital data. Developed in the early 1970s, DES became a standard for securing sensitive information and was officially adopted by the U.S. government in 1977. It works on a block cipher principle, Legacy Systems Still Using DES, XOR operations.meaning it encrypts data in fixed-size blocks. DES was one of the earliest data encryption standard algorithm to be widely adopted and laid the foundation for modern cryptographic standards. Though now largely obsolete, DES remains significant in understanding the evolution of data security.
Interested in Obtaining Your Cybercrime Certificate? View The Cyber Security Online Training Offered By ACTE Right Now!
Historical Development
The history of DES begins in the early 1970s when IBM developed the algorithm known as Lucifer, which was refined and submitted to the National Bureau of Standards. The U.S. government, with input from the NSA, modified Lucifer into what became DES. It was published as a federal standard in 1977 (FIPS PUB 46). At the time, DES was considered strong and reliable for protecting sensitive but unclassified data, particularly in relation to data security at the Presentation and Application layers of the OSI Model. However, over time, advances in computing power and cryptanalysis revealed its limitations, leading to its eventual deprecation.
Structure of DES (Feistel Network)
DES is based on a Feistel network structure, which divides each 64-bit block of plaintext into two 32-bit halves. It operates through 16 rounds of processing, each involving permutation and substitution steps.
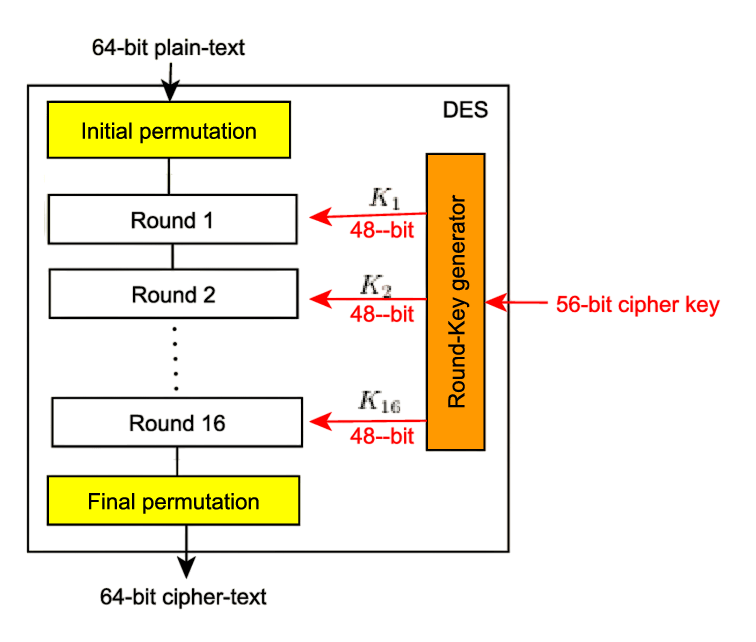
The Feistel structure ensures that decryption follows the same process as encryption, just in reverse order with the same key schedule. Cyber Security Training, learners discover that each round uses a round key derived from the original 56-bit key through a process called key scheduling. The fundamental operations include expansion, substitution (via S-boxes), permutation, and XOR operations.
To Explore Cybersecurity in Depth, Check Out Our Comprehensive Cyber Security Online Training To Gain Insights From Our Experts!
Key Size and Rounds
- DES uses a 56-bit key for data encryption and decryption.
- Although the actual key is 64 bits long, 8 bits are used for parity checking and are not involved in the encryption process.
- This relatively small key size, by today’s standards, is one of the main reasons DES is no longer considered secure.
- While studying Types of Malware Attacks in Cyber Security, it’s also important to understand encryption mechanisms like DES. The algorithm includes 16 rounds of encryption where the plaintext undergoes complex transformations through substitution and permutation steps to defend against unauthorized data manipulation.
- These rounds are designed to create confusion and diffusion, two essential properties of secure encryption algorithms.
Encryption and Decryption Process
The encryption process in data encryption standard algorithm starts with an initial permutation of the plaintext block. The block is then divided into two halves, and for each of the 16 rounds, the right half is expanded and combined with a subkey using XOR. In it’s taught that this result is then processed through S-boxes and a permutation function before being XORed with the left half. The halves are then swapped as part of the encryption round, and the process continues. Despite vulnerabilities to modern threats like Brute Force Attack, some legacy systems still use DES, making it a continued topic of concern in cybersecurity. After the 16 rounds, the two halves are combined and passed through a final permutation to produce the ciphertext. Decryption is essentially the reverse of the encryption process, using the same key schedule in reverse order.
Looking to Master Cybersecurity? Discover the Cyber Security Expert Masters Program Training Course Available at ACTE Now!
Modes of Operation (ECB, CBC, etc.)
- Electronic Codebook (ECB): Each block is encrypted independently. Simple but vulnerable to pattern recognition.
- Cipher Block Chaining (CBC): Each block of plaintext is XOR operations. with the previous ciphertext block before encryption. Provides better security than ECB.
- Cipher Feedback (CFB): Converts DES into a self-synchronizing stream cipher.
- Output Feedback (OFB): Turns DES into a synchronous stream cipher.
- Counter (CTR): Uses a counter value and encrypts it to produce a keystream for XOR operations with plaintext.
Strengths of DES
In its early years, DES was regarded as a strong and efficient encryption standard. Its structured design,Modes of Operation and Feistel network approach made it a robust tool against many types of attacks at the time. It provided a practical method for implementing symmetric encryption in both hardware and software. DES’s widespread adoption also led to increased awareness and advancement in cryptographic research, influencing modern tools like Security Information and Event Management systems that rely on strong encryption standards for secure data collection and analysis. The use of substitution and permutation functions contributed to its resistance against linear and differential cryptanalysis, especially during its early deployment years.
Weaknesses and Vulnerabilities
Despite its initial success, DES eventually became vulnerable to brute-force attacks due to its short 56-bit key length. In 1998, the Electronic Frontier Foundation built a machine called the DES cracker that could break DES encryption in less than 24 hours. Other weaknesses include its susceptibility to differential and linear cryptanalysis. The availability of more powerful computing hardware and sophisticated cryptographic techniques has rendered DES obsolete for most applications. Additionally, the deterministic nature of ECB mode can leak data patterns, Modes of Operation further compromising security.
Preparing for Cyber Security Job Interviews? Have a Look at Our Blog on Cyber Security Interview Questions and Answers To Ace Your Interview!
DES vs AES
The Advanced Encryption Standard (AES) was introduced as the successor to DES in 2001. While DES uses a 56-bit key and 64-bit blocks, AES supports key lengths of 128, 192, and 256 bits and operates on 128-bit blocks.
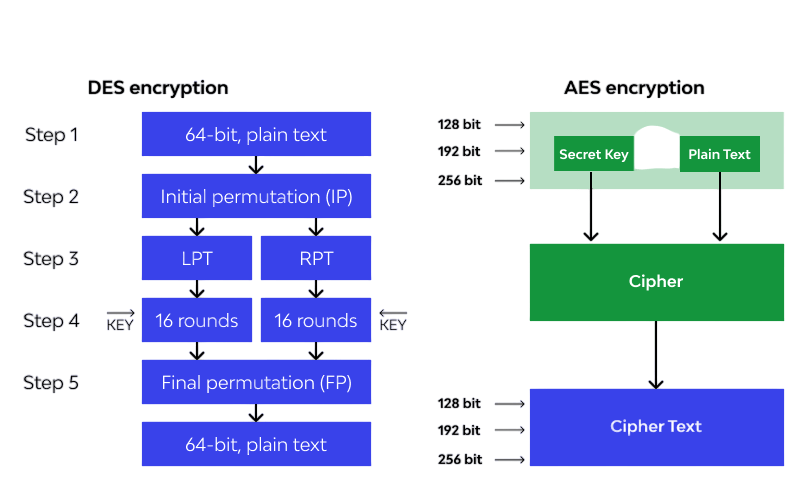
AES employs a substitution-permutation network instead of a Feistel structure, Legacy Systems Still Using DES offering better security and performance. AES is resistant to all known practical attacks and is the standard used today for encrypting sensitive data globally. The transition from DES to AES marked a significant advancement in cryptographic security, addressing the limitations of DES while maintaining performance across diverse platforms.
Practical Applications
Although DES is now largely considered insecure, It played a crucial role in the development of encryption technologies and was widely used in financial institutions and government agencies. While DES protected data confidentiality, organizations also had to address other threats like DDoS Attacks, which target system availability rather than data encryption. cryptanalysis and secure communications. Examples of DES usage include encrypting ATM PINs, securing emails, and protecting data in early digital networks. Some applications, especially legacy systems, may still rely on DES due to constraints in upgrading software or hardware. Understanding DES provides a historical context for encryption practices and helps appreciate the evolution of secure systems
Legacy Systems Still Using DES
- Despite being deprecated, some legacy systems continue to use DES, particularly in embedded systems or specialized industrial equipment where updating encryption algorithms is challenging.
- These systems often rely on hardware implementations that are difficult to replace.
- In such cases, security measures like using DES in triple encryption mode (Triple DES or 3DES) are employed.
- 3DES applies DES encryption three times with different keys, significantly improving security but at the cost of performance.
- However, even 3DES is now considered insecure and is being phased out.
Summary
The data encryption standard algorithm represents a pivotal moment in the history of cryptography, providing a standardized method of encryption that influenced decades of research and development. While its key size and vulnerabilities have led to its obsolescence, Cyber Security Training, DES remains a foundational concept in symmetric-key cryptography. Its structure, including the Feistel network and XOR operations, is essential for understanding how classical encryption algorithms function. and historical significance continue to be studied in academic and professional settings. Understanding DES helps in grasping the principles behind modern encryption techniques and emphasizes the importance of evolving cryptographic standards to meet emerging security challenges.




