
- What is Digital Signatures
- Purpose and Advantages
- How Digital Signatures Work
- Key Components (Hash, Private Key, Public Key)
- Algorithms Used (RSA, DSA, ECDSA)
- Verification Process
- Legal Validity and Regulations
- Comparison with Electronic Signatures
- Future Trends
- Conclusion
What is Digital Signatures
A digital signature is a cryptographic mechanism used to validate the authenticity and integrity of digital messages, documents, or software. Much like a handwritten signature or a stamped seal, a digital signature binds a signer’s identity to a digital file, ensuring that the file was created by the stated sender and has not been altered in transit. As a vital component of modern cybersecurity, digital signatures help prevent tampering, fraud, and impersonation in digital communications, particularly in sensitive operations like financial transactions, contract management, and government records. The rise of digital communications brought with it new security challenges, particularly concerning identity verification and data integrity. Strengthen your understanding of these evolving risks and learn how to safeguard digital interactions through Cyber Security Training. Traditional methods of authentication and verification were insufficient for the digital era. This led to the development of digital signatures, a form of electronic signature that is grounded in cryptographic principles. Unlike basic electronic signatures, which might simply be a scanned image of a signature or a typed name, digital signatures offer a far higher level of security and trustworthiness. They are widely used in cryptographic protocols, especially in public key infrastructure (PKI).
Interested in Obtaining Your Cyber Security Certificate? View The Cyber Security Online Training Offered By ACTE Right Now!
Purpose and Advantages
Digital signatures serve several important purposes in modern communication and data management: Trojan Horse Viruses have changed the way we communicate securely online. While they often masquerade as legitimate software, their impact can be devastating compromising identity, data integrity, and system security. Learn how to detect, prevent, and respond to these threats with Trojan Horse Viruses. By using strong encryption methods, these electronic signatures confirm the sender’s identity, confirming where messages and documents come from. They make sure that the content has not been altered since it was signed. They also create a legal agreement that stops signers from denying their role in a transaction. Digital signatures make electronic verification quick and easy. This improves processes in many industries and removes the delays caused by traditional paper methods. With strong security features to guard against tampering and unauthorized access, digital signatures are now a vital tool in today’s digital communications especially in situations where high trust and authenticity are needed.
How Digital Signatures Work
Digital signatures are created and verified using public key cryptography, also known as asymmetric encryption. Here’s a simplified overview of how it works:
- Hash Creation: The sender creates a hash (a fixed-length string of characters) of the message.
- Digital Signature Generation: The sender encrypts the hash with their private key to generate the digital signature.
- Transmission: The signed document and digital signature are sent to the recipient.
- Signature Verification: The recipient uses the sender’s public key to decrypt the signature and obtain the original hash.
- Integrity Check: The recipient computes a new hash of the received message and compares it with the decrypted hash.
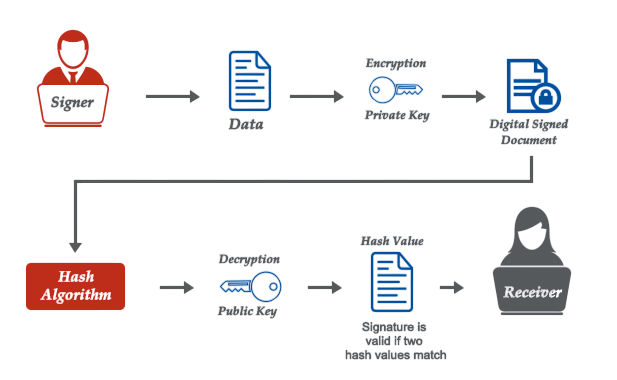
This process ensures that any modification to the message will result in a different hash, making tampering immediately detectable.
To Explore Cybersecurity in Depth, Check Out Our Comprehensive Cyber Security Online Training To Gain Insights From Our Experts!
Key Components (Hash, Private Key, Public Key)
Digital signatures rely on several key cryptographic elements to ensure authenticity and integrity. However, these technologies can be misused in cybercrime. Learn how attackers exploit digital tools to harass, monitor, or impersonate individuals online through Cyberstalking.
- Hash Function: A mathematical algorithm that converts input data into a fixed-length string. Popular hashing algorithms include SHA-256 and SHA-3.
- Private Key: A secret key held by the sender that is used to sign the data.
- Public Key: A corresponding key that is publicly available and used by recipients to verify the signature.
The strength and trust of digital signatures stem from the difficulty of reversing the hash function and the secure management of private keys.
Algorithms Used (RSA, DSA, ECDSA)
Digital signatures can be implemented using various cryptographic algorithms, including: In the field of cryptographic algorithms, three main digital signature and encryption methods stand out: RSA, DSA, and ECDSA. RSA, developed by Rivest, Shamir, and Adleman, is a key public algorithm known for its strong encryption and digital signature features. It is widely trusted for its reliability and security. To build your expertise in safeguarding systems and data, explore Cyber Security Training. The Digital Signature Algorithm (DSA) is a U.S. federal standard that uses discrete logarithms to provide secure digital signatures. ECDSA offers a different approach. It uses elliptic curve cryptography to achieve similar security with much shorter key lengths. This results in faster processing and smaller file sizes. Together, these algorithms are essential to modern cryptographic systems, each providing unique benefits for protecting digital communications and ensuring data integrity. Each algorithm has different computational efficiencies and use cases. For example, ECDSA is commonly used in mobile and blockchain applications.
Looking to Master Cybersecurity? Discover the Cyber Security Expert Masters Program Training Course Available at ACTE Now!
Verification Process
The verification of a digital signature involves several steps: In the digital signature verification process, the recipient first obtains the digital signature and signed message. They use the sender’s public key to decrypt the signature and extract the original hash. Then, the recipient generates a hash of the received message using the same hash function. Next, they compare the decrypted original hash with the newly computed hash. This process helps verify data integrity and detect tampering. To explore how such techniques fit into broader security practices, check out Cybersecurity Vulnerabilities: Key Concepts and Mitigation. If these hashes match perfectly, the message is verified, confirming its integrity and authenticity. If the hashes differ, it suggests that the message may have been tampered with or the signature is invalid, indicating a potential security issue in the communication. This process provides assurance that the message came from the expected sender and that it was not altered.
Legal Validity and Regulations
Digital signatures are recognized as legally binding in many countries. Their legal acceptance has been bolstered by international and national regulations:
- ESIGN Act (USA): Grants legal recognition to electronic signatures and digital records.
- eIDAS Regulation (EU): Provides a regulatory framework for electronic identification and trust services.
- IT Act (India): Recognizes digital signatures and provides legal support for electronic documents.
In many jurisdictions, digital signatures that are created and managed in accordance with a PKI framework are considered as valid as traditional handwritten signatures.
Certificate Authorities and PKI
Digital signatures rely on a Public Key Infrastructure (PKI), a framework that manages keys and certificates. The key components include secure key generation, certificate authorities, and validation protocols all of which play a vital role in protecting financial transactions. To understand how these technologies support secure banking operations, explore Cybersecurity in Banking.
- Certificate Authority (CA): A trusted entity that issues digital certificates binding public keys to individuals or organizations.
- Registration Authority (RA): Verifies identities before certificates are issued.
- Digital Certificate: Contains the public key, identity details, and CA signature.
PKI ensures trust and authenticity by allowing users to verify that public keys truly belong to the entities they claim to represent. Without PKI, verifying the legitimacy of public keys would be unreliable.
Preparing for Cyber Security Job Interviews? Have a Look at Our Blog on Cyber Security Interview Questions and Answers To Ace Your Interview!
Comparison with Electronic Signatures
Though often used interchangeably, electronic signatures and digital signatures are not the same:
- Electronic Signature: A broad term that refers to any electronic process indicating acceptance, such as typing a name or clicking “I agree.”
- Digital Signature: A specific type of electronic signature that uses cryptography for security.
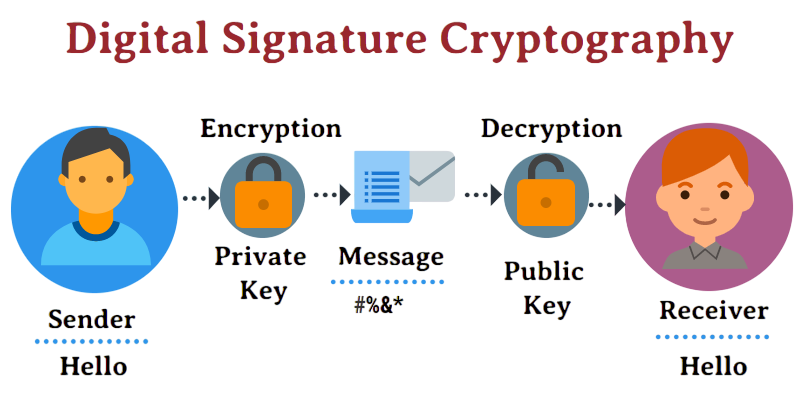
Digital signatures offer far greater authenticity, integrity, and non-repudiation. Electronic signatures, while legally recognized, may lack these advanced features unless supported by secure systems.
Future Trends
The field of digital signatures continues to evolve. Some emerging trends include: Our cybersecurity strategy is leading the way in digital signature protection with a multi-layered approach. We are developing quantum-resistant algorithms to protect against possible quantum computer attacks while also using blockchain technology for decentralized signature validation. By combining biometric verification with digital signatures, we are building a stronger authentication system that greatly improves security protocols. However, even advanced systems can be vulnerable to malicious software. Learn how threats like Computer Virus can compromise authentication and what steps you can take to defend against them. Our new approach uses artificial intelligence to regularly assess and manage trust within public key infrastructure (PKI) systems, allowing for flexible and smart security measures. Additionally, we are working with international partners to promote global standardization, making sure our solutions comply with strict legal and technical standards across different technological environments. As digital transformation accelerates, the demand for secure and scalable digital signature solutions will only grow.
Conclusion
Digital signatures have revolutionized how individuals and organizations authenticate information and conduct secure digital transactions. By leveraging cryptographic principles, they provide a robust, legally recognized method for ensuring data integrity and origin authentication. Whether used in e-governance, business, healthcare, or legal processes, digital signatures offer efficiency, trust, and security. As technology advances and new threats emerge, the continued development and refinement of digital signature technologies will remain critical to securing the digital future. Strengthen your understanding of these innovations and their role in authentication and data integrity through Cyber Security Training. However, new technology also brings new problems. Hackers are always searching for ways to bypass security measures. That’s why it’s crucial to continually update digital signature systems and stay ahead of potential threats. Experts agree that ongoing research and new solutions are important for keeping digital signatures reliable in the future.




