
- DoS and DDoS Attack
- What is DoS Attack?
- What is a DDoS Attack?
- History of Major Attacks
- How DoS/DDoS Attacks Work
- Differences Between DoS and DDoS
- Tools Used in DoS/DDoS
- Types of DDoS Attacks
- Preventive Measures
- Conclusion
DoS and DDoS Attack
In the digital era, where businesses, governments, and individuals rely heavily on the internet for communication, transactions, and information exchange, cyberattacks have become one of the most pressing security challenges. Among these threats, Denial of Service (DoS) and Distributed Denial of Service (DDoS) attacks are particularly dangerous because they do not necessarily aim to steal data but instead disrupt the availability of online services. To learn how to detect, mitigate, and prevent such disruptions, explore Cyber Security Training a specialized program that covers network defense strategies, traffic analysis, incident response, and hands-on labs focused on countering DoS and DDoS attacks in real-world environments. These attacks can cripple websites, delay operations, and even cause millions of dollars in financial losses within hours. Understanding DoS and DDoS attacks is critical not only for cybersecurity professionals but also for enterprises, internet service providers (ISPs), and end users who depend on digital services.
What is DoS Attack?
A Denial of Service (DoS) attack is a malicious attempt to make a machine, network, or website unavailable to its intended users by overwhelming it with a flood of traffic or by exploiting vulnerabilities that consume system resources. In simple terms, it is like a single person continuously dialing a company’s customer care number and not allowing legitimate customers to get through. DoS attacks generally originate from a single system or attacker. The main goal is disruption rather than data theft. To understand how such disruptive tactics evolve into financially motivated threats, explore Cyber Extortion Explained a strategic guide that examines how attackers leverage denial-of-service, ransomware, and data leaks to pressure victims into paying for restored access or confidentiality. These attacks may cause the target server to crash, slow down drastically, or become unresponsive. Although less powerful compared to DDoS, DoS attacks remain dangerous because they can take down smaller networks and applications. Attackers often use scripts, automated tools, or custom code to launch DoS attacks, making it relatively easy for even novice hackers to execute them.
Interested in Obtaining Your Cyber Security Certificate? View The Cyber Security Online Training Offered By ACTE Right Now!
What is a DDoS Attack?
A Distributed Denial of Service (DDoS) attack is an advanced and more powerful version of a DoS attack. Instead of a single system, it leverages multiple compromised devices (often called a botnet) to flood a target with enormous amounts of traffic. To understand how endpoint protection tools help detect and block such malicious activity, explore Antivirus Software Explained a practical guide that covers malware detection techniques, real-time scanning, and behavioral analysis used to defend systems against botnet infections and coordinated attacks.
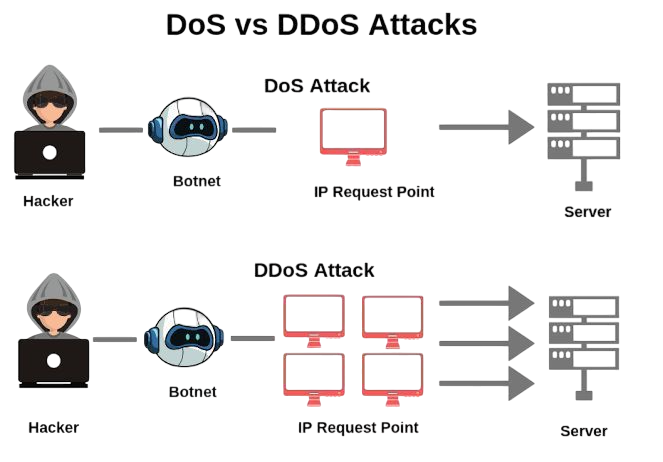
These devices may include computers, servers, or even IoT devices like cameras and routers that have been infected with malware. In this case, the attack is “distributed,” meaning thousands or millions of requests hit the target simultaneously, making it nearly impossible for the victim to differentiate between malicious and legitimate traffic. DDoS attacks are more difficult to mitigate compared to DoS attacks because they come from numerous sources worldwide. Hackers often use large-scale botnets such as the Mirai botnet, which hijacked IoT devices globally, to amplify their attacks.
To Explore Cybersecurity in Depth, Check Out Our Comprehensive Cyber Security Online Training To Gain Insights From Our Experts!
History of Major Attacks
DDoS attacks have been around since the early days of the internet, but they have evolved in scale and complexity over the years. To understand how these and other malicious techniques disrupt systems, steal data, or extort victims, explore Types of Malware Attacks a comprehensive guide that breaks down viruses, worms, trojans, ransomware, and botnets, highlighting their behavior, impact, and prevention strategies.
- 1996 – The First DoS Attack: The first documented DoS attack was against Panix, one of the oldest internet service providers, using a SYN flood that kept their services offline for several days.
- 2000 – MafiaBoy Attack: A 15-year-old hacker named MafiaBoy launched DDoS attacks against major companies like Yahoo, Amazon, eBay, and CNN, causing widespread panic and losses worth millions.
- 2016 – Dyn DDoS Attack: The Mirai botnet carried out one of the largest DDoS attacks against Dyn, a DNS provider, which led to the temporary shutdown of major platforms like Twitter, Netflix, Reddit, and Spotify.
- 2020 – AWS Attack: Amazon Web Services (AWS) mitigated one of the largest DDoS attacks ever recorded, peaking at 2.3 Tbps of traffic.
These attacks highlight how DDoS has grown from simple disruptions to global-scale cyber warfare tactics.
How DoS/DDoS Attacks Work
The functioning of these attacks depends on exploiting the vulnerabilities of networks and systems. Common working mechanisms include:
- Flooding the Bandwidth: Sending excessive traffic that exhausts the network’s bandwidth, leaving no room for legitimate requests.
- Resource Exhaustion: Overloading servers with fake requests that consume CPU and memory resources until the system crashes.
- Exploiting Protocol Weaknesses: Manipulating protocols like TCP, UDP, and ICMP to generate traffic storms.
- Botnet Amplification: Using thousands of compromised devices to amplify the impact of the attack.
Attackers often automate these processes using specialized tools and scripts, making them quick and effective.
Looking to Master Cybersecurity? Discover the Cyber Security Expert Masters Program Training Course Available at ACTE Now!
Differences Between DoS and DDoS
Both Denial of Service (DoS) and Distributed Denial of Service (DDoS) attacks try to make a service unavailable, but they do it differently and have different results. A DoS attack comes from one device or person, so it’s not as big and it’s easier to spot. A DDoS attack, on the other hand, comes from many devices in different places, making it harder to detect and mitigate. To learn how to defend against both types of attacks using real-world tools and techniques, explore Cyber Security Training a practical course that covers threat detection, traffic filtering, incident response, and hands-on labs focused on DoS and DDoS mitigation strategies. This makes it a bigger, coordinated attack that’s much harder to stop. The result of these attacks also differ. DoS attacks usually cause short-term issues for smaller systems. DDoS attacks, though, can stop big companies, Internet Service Providers (ISPs), and even a country’s whole internet system from working. Also, the ways to stop these attacks are not the same. You can usually block a DoS attack by finding and isolating the single IP address involved.
Preparing for Cyber Security Job Interviews? Have a Look at Our Blog on Cyber Security Interview Questions and Answers To Ace Your Interview!
Tools Used in DoS/DDoS
Hackers rely on a variety of tools to launch attacks. Some popular tools include password crackers, network sniffers, vulnerability scanners, and exploit frameworks. To understand how these tools are used to systematically guess credentials and gain unauthorized access, explore Brute Force Attacks a focused guide that explains the mechanics, automation techniques, and defense strategies behind one of the most persistent forms of cyber intrusion.
- LOIC (Low Orbit Ion Cannon): Widely used for DoS attacks, it sends massive requests to overwhelm servers.
- HOIC (High Orbit Ion Cannon): An advanced version of LOIC, capable of launching simultaneous attacks.
- Hping: A command-line tool used for packet crafting and DoS testing.
- Botnets (Mirai, Zeus): Networks of infected devices used to generate large-scale DDoS attacks.
- Slowloris: A tool that sends partial HTTP requests to exhaust server connections.
While these tools were initially created for testing and research, attackers often misuse them for malicious purposes.
Types of DDoS Attacks
DDoS (Distributed Denial of Service) attacks fall into three main types, each with its own challenges for network security. First, volume-based attacks try to flood the target with traffic using methods like UDP floods, ICMP floods, and amplification attacks. These attacks aim to use up bandwidth and stop service.
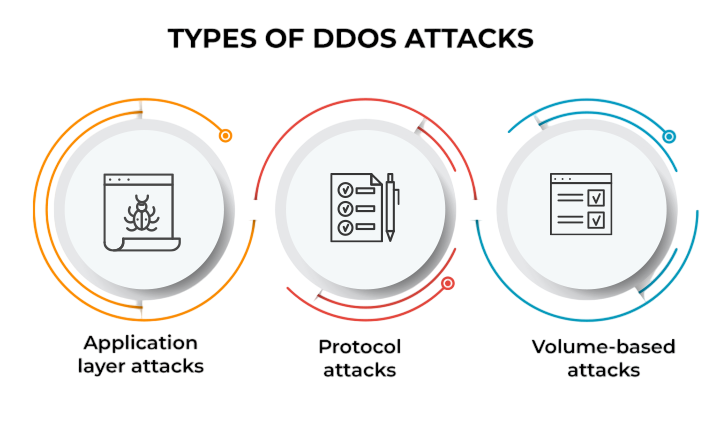
Second, protocol attacks take advantage of weaknesses in network protocols. Examples include SYN floods, the Ping of Death, and Smurf attacks. By targeting protocols, these attacks can disrupt how devices communicate. Third, application layer attacks target certain apps and services. They are dangerous because they can imitate normal user actions. Examples are HTTP floods, Slowloris attacks, and DNS query floods. These attacks are hard to spot and filter. Because they are sneaky, application-layer DDoS attacks are a threat, as they can get around normal security, showing the need for strong and flexible defense plans.
Preventive Measures
Preventing DoS and DDoS attacks requires a combination of strategies at the user, enterprise, and ISP levels: deploying firewalls, rate-limiting traffic, using intrusion detection systems, and maintaining secure configurations. To understand how device-level vulnerabilities can bypass these defenses, explore Jailbreaking in Cyber Security a technical guide that explains how unauthorized modifications to operating systems expose systems to exploitation.
- Firewalls and Intrusion Detection Systems: Filtering traffic and blocking suspicious IPs.
- Load Balancers: Distributing incoming traffic across multiple servers to reduce overload.
- Rate Limiting: Restricting the number of requests a user can send.
- Anti-DDoS Services: Specialized services like Cloudflare, Akamai, and AWS Shield protect against large-scale attacks.
- Network Redundancy: Having backup servers and multiple data centers ensures uptime even during an attack.
Conclusion
DoS and DDoS attacks remain some of the most disruptive and costly threats in cybersecurity. While DoS is simpler and easier to manage, DDoS has evolved into a weapon capable of disabling entire networks and services at a global scale. The rise of IoT devices and increasing reliance on digital platforms only make these attacks more frequent and severe. To build the expertise needed to defend against this expanding threat landscape, explore Cyber Security Training a future-ready program that equips learners with skills in IoT security, threat detection, and real-time incident response to protect modern digital ecosystems. To combat them, individuals, enterprises, and ISPs must adopt layered defense strategies, from firewalls and rate limiting to advanced detection tools and cloud-based anti-DDoS services. Moreover, global cooperation and strict cybersecurity regulations are essential to reduce the risks. As cybercriminals continue to innovate, understanding the nature of DoS and DDoS attacks is the first step toward building resilient defense systems and ensuring digital safety.




