
- Symmetric Cryptography Basics
- Types of Secret Key Cryptography
- Encryption and Decryption Process
- Common Algorithms in Symmetric Cryptography
- Key Management in Secret Key Cryptography
- Advantages and Disadvantages of Secret Key Cryptography
- Use Cases of Secret Key Cryptography
- Conclusion
Symmetric Cryptography Basics
Symmetric cryptography, also known as secret key cryptography, is a type of encryption where the same key is used for both encryption and decryption of the data. In this system, the sender and receiver must both possess the same key, which needs to be kept secret from any third parties. This type of encryption ensures that the data transmitted over insecure channels, such as the internet, remains confidential, emphasizing the importance of Cyber security training in maintaining safe communication practices. Symmetric cryptography is one of the oldest and most widely used forms of encryption. Its simplicity and efficiency make it suitable for protecting large amounts of data. However, one of the main challenges of symmetric cryptography is securely distributing the secret key between the communicating parties.
To become a certified cyber security, have a look at our Cyber Security Online Training right now.
Types of Secret Key Cryptography
Symmetric encryption, another name for secret key cryptography, is an encryption technique in which data is encrypted and decrypted using the same key. It is one of the fundamental ideas of cryptography and is mostly applied to communication systems to guarantee confidentiality. Secret key cryptography relies on a single shared secret between the sender and the recipient, in contrast to asymmetric cryptography, which employs two keys (public and private). There are several types of symmetric cryptography methods, including:
- The sender takes the plaintext (the original message).
- The sender applies an encryption algorithm using the secret key to convert the plaintext into ciphertext.
- The ciphertext is the encrypted message that is unreadable to anyone who does not possess the secret key, a concept that is also crucial in Fraud Detection Using Machine Learning , where encryption helps protect sensitive transaction data from unauthorized access. Decryption:
- The receiver, who possesses the same secret key as the sender, applies the decryption algorithm to the ciphertext.
- The decryption algorithm reverses the encryption process and converts the ciphertext back into the original plaintext.
- Only the receiver who has the secret key can decrypt the ciphertext correctly.
- AES (Advanced Encryption Standard): AES is one of the most widely used symmetric encryption algorithms. It is known for its strength and efficiency. AES supports key sizes of 128, 192, and 256 bits, with 128-bit blocks. AES is used in a variety of applications, including securing sensitive data in government, financial, and enterprise systems.
- DES (Data Encryption Standard): DES was once a widely used symmetric encryption standard, but it has been deprecated due to vulnerabilities in its 56-bit key length. Despite its weaknesses, it remains an important historical algorithm in cryptography.
- 3DES (Triple DES): 3DES was developed as a more secure variant of DES by applying the DES algorithm three times with different keys. While stronger than DES, it is still considered less secure than AES, and its use has been phased out in favor of more modern algorithms, highlighting the role of Cyber security training in understanding and adopting up-to-date encryption standards.
- RC4: RC4 is a stream cipher that was widely used in protocols like SSL/TLS. However, it is now considered insecure due to vulnerabilities in its design, and it is no longer recommended for use in modern cryptographic systems.
- Blowfish: Blowfish is a block cipher that operates on 64-bit blocks and supports key sizes ranging from 32 to 448 bits. It is a fast and efficient algorithm, but it is now less popular than AES due to its relatively smaller block size.
- Twofish: Twofish is a successor to Blowfish and is a block cipher that operates on 128-bit blocks. It supports key sizes of 128, 192, and 256 bits. While it is not as widely used as AES, it is still considered a strong and secure algorithm.
- Key Generation: The secret key must be randomly generated and kept secure. The randomness of the key is crucial to ensuring its strength against brute-force attacks.
- Key Distribution: The secret key must be securely shared between the sender and receiver. This can be done using secure key exchange protocols such as Diffie-Hellman or RSA, which are often explored in Cybersecurity Project Ideas to demonstrate practical implementations of secure communication methods.
- Key Storage: Secret keys should be stored securely, either in hardware security modules (HSMs) or in encrypted databases, to prevent unauthorized access.
- Key Rotation: Regularly rotating the secret key helps mitigate the risk of key compromise. In case a key is suspected to be compromised, it should be immediately replaced with a new key.
- Key Expiry: Secret keys should have an expiration date to limit their lifespan. Once a key expires, it should no longer be used, and a new key should be generated and distributed.
- Speed and Efficiency: Symmetric cryptography is generally faster and more efficient than asymmetric cryptography, especially when processing large amounts of data.
- Simple to Implement: Secret key cryptography is relatively straightforward to implement compared to public-key systems, as it requires only a single key for encryption and decryption.
- Low Computational Overhead: Since symmetric algorithms are typically less computationally intensive than asymmetric algorithms, they are better suited for resource-constrained environments, such as mobile devices or embedded systems.
- Key Distribution Problem: The major drawback of symmetric cryptography is the challenge of securely distributing and managing the secret key. If the key is intercepted during transmission, the entire security of the system is compromised, which relates closely to concepts like What is Ransomware Attack , where attackers exploit weak encryption practices to gain unauthorized access and hold data hostage.
- Scalability Issues: In systems with a large number of users, maintaining a secure key for each pair of users becomes increasingly difficult. For n users, n(n-1)/2 keys may be needed, making key management complex in large systems.
- Lack of Non-repudiation: Unlike asymmetric cryptography, symmetric cryptography does not provide non-repudiation. Since both the sender and receiver share the same key, they cannot prove to a third party who sent the message.
- Data Encryption: Symmetric cryptography is commonly used for encrypting large volumes of data, such as files, databases, and network traffic. It is widely used in protocols like SSL/TLS (though SSL/TLS typically uses hybrid encryption, combining both asymmetric and symmetric encryption).
- Disk Encryption: Full disk encryption tools, such as BitLocker and FileVault, use symmetric cryptography to encrypt the data stored on a disk, ensuring that data remains secure even if the physical device is lost or stolen.
- Virtual Private Networks (VPNs): VPN protocols, such as IPSec, rely on symmetric cryptography to secure communications over the internet, allowing users to establish encrypted connections to private networks remotely while protecting data from Hackers And Crackers who attempt to intercept or manipulate network traffic.
- Secure Messaging: Applications that offer end-to-end encrypted messaging, such as WhatsApp and Signal, use symmetric cryptography to ensure that messages are only readable by the intended recipients.
- Data Backup and Archiving: Symmetric cryptography is often used to protect backup data from unauthorized access, ensuring that sensitive information remains confidential even if the backup media is lost or stolen.
Stream Ciphers: Stream ciphers encrypt plaintext data one bit or byte at a time. The encryption is done by combining the plaintext with a keystream, which is generated from the secret key, and its effectiveness can be evaluated using concepts such as the Receiver Operating Characteristic (ROC) to measure performance and reliability in detection systems. Stream ciphers are fast and efficient, making them suitable for encrypting real-time data such as audio or video streams. An example of a stream cipher is RC4.
Block Ciphers: Block ciphers encrypt data in fixed-size blocks, typically 64 or 128 bits at a time. Each block is processed independently, and the same key is applied to each block of data. Block ciphers are more commonly used in modern cryptographic systems for their robustness and flexibility. Examples of block ciphers include AES (Advanced Encryption Standard) and DES (Data Encryption Standard).
Hybrid Ciphers: In some systems, both stream and block ciphers are used together in a hybrid approach. For example, a stream cipher might be used to generate a key for a block cipher, combining the strengths of both encryption methods.
Encryption and Decryption Process
The encryption and decryption process in symmetric cryptography works as follows:
- Encryption:
Since the same key is used for both encryption and decryption, it is critical to keep the secret key safe and secure from unauthorized access.
Are you curious to know more about Cybersecurity ? Take advantage of our comprehensive online Cyber Security Online Training
Common Algorithms in Symmetric Cryptography
There are several widely used symmetric encryption algorithms. Here are some of the most common ones:
Transform Your Career with Cyber Security Knowledge Enroll in ACTE’s Cyber Security Expert Masters Program Training Course Today!
Key Management in Secret Key Cryptography
Key management is one of the most critical aspects of symmetric cryptography. Since the same key is used for both encryption and decryption, it is essential to securely distribute, store, and rotate the key to ensure the integrity and confidentiality of the encrypted data. Key management involves several steps:
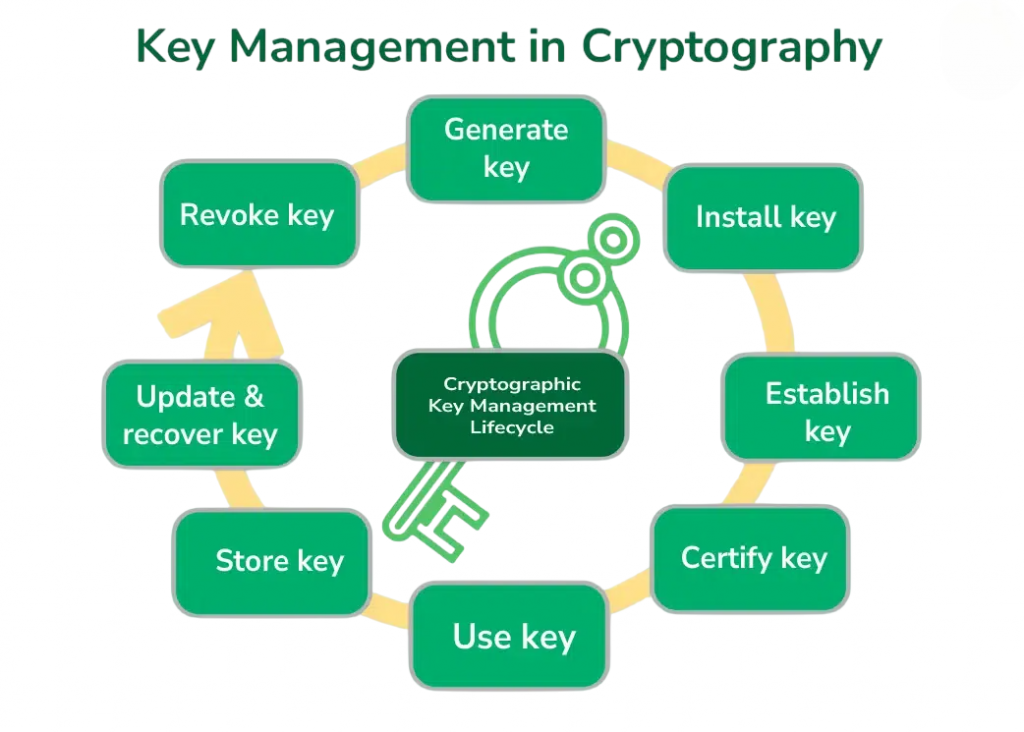
Proper key management is vital for maintaining the security of a cryptographic system, and failure to manage keys appropriately can lead to vulnerabilities and data breaches.
Advantages and Disadvantages of Secret Key Cryptography
- Advantages:
- Disadvantages:
Preparing for a job interview in cybersecurity ? Examine our blog post about Cybersecurity Interview Questions and Answers to get the most of your employment experience!
Use Cases of Secret Key Cryptography
Conclusion
Symmetric encryption, often known as secret key cryptography, is still a mainstay of contemporary data security because of its ease of use, speed, and effectiveness in safeguarding data. Particularly in large-scale data transfers, it maintains excellent efficiency while guaranteeing anonymity by using the same key for both encryption and decryption. Secure key distribution and management, however, are important issues that need to be resolved through effective Cyber security training and best practices in order to stop unwanted access. Even though asymmetric techniques are becoming more popular, symmetric encryption is still essential for hybrid systems and practical uses, serving as the foundation for safe digital communication in the modern era. Symmetric encryption, sometimes referred to as secret key cryptography, is still an essential part of contemporary cybersecurity. It is quick, effective, and ideal for encrypting big amounts of data because it only requires one common key for encryption and decoding. Symmetric encryption is now the recommended option for protecting files, communications, and network traffic due to its effectiveness.





