
- Introduction
- IPSec: What it is
- Role of Firewalls in Network Security
- How Firewalls Utilize IP Security (IPSec)
- Advantages of IP Security in Firewalls
- Configuring IPSec in Firewalls
- Challenges of Implementing IPSec in Firewalls
- Best Practices for Utilizing IPSec with Firewalls
- Conclusion
In today’s increasingly connected world, securing network traffic is paramount for organizations to safeguard their data and systems from unauthorized access. Firewalls play a central role in network security by monitoring and controlling traffic based on security policies. Integrating IP Security (IPSec) with an internet firewall adds an extra layer of network firewall protection by ensuring data transmission across networks’ encryption and authentication. Cybersecurity Training Courses blog explores how IPSec enhances network firewall security, its configuration, and the best practices for implementing it effectively to safeguard network communications.
Want to learn more about Cybersecurity ? Enroll in our Complete Cyber Security Online Training Online!
Introduction
As threats in cyberspace become more common and the importance of secure communication increases with time, safeguarding data flowing through networks becomes essential. Any setup of cyber network security would use a firewall as its first barrier at the entrance or exit from a network. Firewalls may permit only trusted traffic to cross the boundary. However, ensuring the confidentiality and integrity of transmitted data is impossible by merely deploying a firewall. That is why IP Subnets becomes essential here. IPSec is a protocol suite that secures IP communications by authenticating and encrypting each IP packet in a communication session. When combined with IPSec, firewalls provide an enhanced level of protection, ensuring that even if unauthorized parties attempt to intercept data, they cannot read or alter the information. This integration is particularly important to VPNs and remote access communications, which need data transmitted over untrusted networks like the internet. The blog looks at how IPSec works within the firewalls, its advantages and disadvantages, and the configuration process to maximize network security.
IPSec: What it is
IPSec is a comprehensive suite of protocols designed to secure IP communications by encrypting and authenticating data packets. It operates at the network layer (Layer 3) of the OSI model, which means it can secure almost all types of network traffic, Access Control List including TCP/IP, UDP, and ICMP.
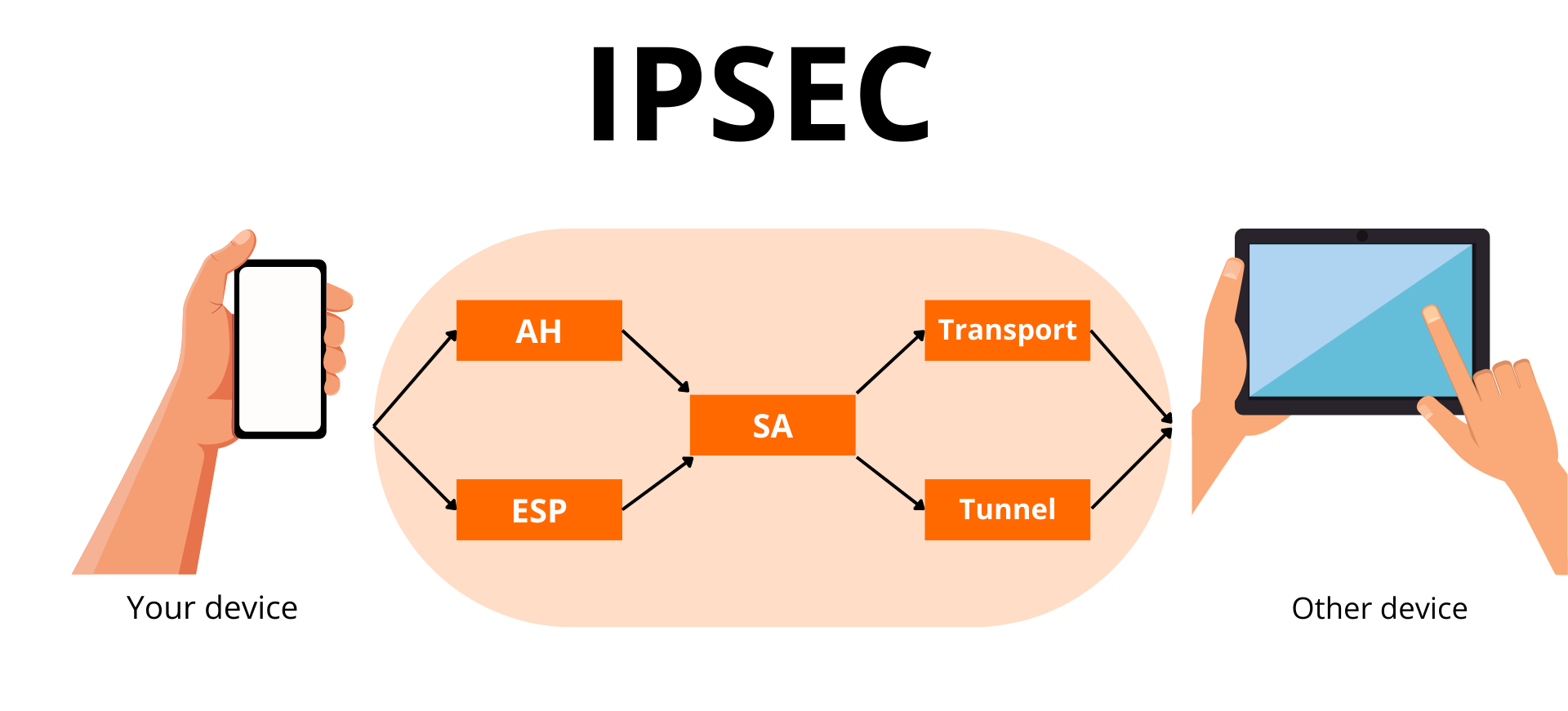
- Transport Mode: In this mode, the IP packet only encrypts and/or authenticates the data portion of the packet. The header is left intact, which may be useful for securing end-to-end communications between two hosts.
- Tunnel Mode: In tunnel mode, the header and data of the IP packet are encrypted and authenticated. This mode is used in VPNs, where one secure tunnel is established between gateways, and the whole original packet is encapsulated in a new IP packet. Key features of IPSec include:
- Authentication: Verifying the identity of the sender of the data packet, preventing impersonation.
- Encryption: Data is converted to an unreadable format, hence the data is kept confidential.
- Integrity: Data is not modified during its transfer.
- Packet-Filtering Firewalls: This is the most basic form of firewalls. These types of firewalls inspect the network packets and allow or block them based on the defined rules. They are relatively fast but provide minimal protection.
- Stateful Inspection Firewalls: This firewall tracks the state of active connections and makes decisions based on the state of the connection as well as the defined rules. This is a more thorough form of security than simple packet filters.
- Confidentiality: For data to be encrypted, IPSec renders this data unreadable for a third party in unauthorized transmission. This is because, in various cases, untrusted networks transport sensitive information, such as financial reports or personal records.
- Data Integrity: IPSec’s guarantee lies in the non-man-in-the-middle, unalterable data throughout transmission based on authentication and hashing algorithms. As a result, modification of transmitted data by an attacker fails.
- Authentication: IPSec provides mechanisms to authenticate the sender’s identity and ensure that only authorized devices can communicate securely. This prevents spoofing or impersonation attacks.
- Non-repudiation: Strong encryption and authentication methods ensure that the sender cannot deny sending the data, which is important for legal and compliance purposes.
- Support for Remote Access: With IPSec integrated into firewalls, Two Factor Authentication remote users can securely access the corporate network through VPNs, ensuring the communication is encrypted and protected from eavesdropping.
- Enhanced Security for Site-to-Site Communication: IPSec allows organizations with multiple branch offices or remote locations to securely exchange data over the internet, minimizing the risks associated with unencrypted traffic.
- Configuration can be highly complex, especially for remote access VPNs and site-to-site connections. Understanding the encryption protocol, method of key exchange, and firewall policies has to be accurate.
- The overhead of Performance overheads for encrypting and decrypting processes tend to delay and increase the computation load on the nodes. The impact can be substantial in networks where devices suffer high traffic loads.
- Compatibility Issues Different firewall vendors may implement IPSec slightly differently, leading to compatibility issues when establishing secure connections between devices from different manufacturers.
- Management and Key Distribution of encryption keys securely and efficiently is a challenge. If keys are not rotated or distributed properly, the security of the communication channel could be compromised.
- Managing the IPSec configurations for many devices and users can become increasingly difficult as the network grows in Cyber Space. The complexity of scaling the deployment to handle numerous remote users or site-to-site connections without compromising security or performance can be a significant challenge.
- Diagnosing issues within an IPSec-secured environment can be complicated due to the layered nature of encryption and authentication processes. If a VPN tunnel fails or a firewall misconfigures an IPSec rule, pinpointing the exact issue can require detailed knowledge of both the IPSec protocols and the underlying network infrastructure.
- Use Strong Encryption Algorithms: Always select the most secure encryption algorithms, such as AES-256, to ensure the highest level of data confidentiality.
- Rotate Keys: Rotate encryption keys periodically to minimize the risk of key compromise.
- Implement Multi-Factor Authentication: Implement multi-factor authentication for VPN users for added security. This will guarantee that the network can only be accessed by authorized users.
- Monitor IPSec Traffic: IPSec traffic continuously for any signs of attacks or configuration anomalies.
- Ensure Proper Configuration: Be sure to have the two firewalls and IPSec settings well configured so as not to result in tunnel failure or poor performance.
Role of Firewalls in Network Security
A firewall is a security device that monitors and filters incoming and outgoing network traffic based on security rules. It serves as a partition between untrusted external networks (such as the internet) and trusted internal networks. Firewalls are designed to prevent unauthorized access to systems, protect against threats like malware, and enforce network security policies.
To Earn Your Cyber Security Certification, Gain Insights From Leading Cyber Security Experts And Advance Your Career With ACTE’s Cyber Security Online Training Today!
How Firewalls Utilize IP Security (IPSec)
Firewalls alone will not necessarily support confidential data transference when using third parties over untrusted networks. IPSec secures the flow of traffic through Enron and authentication mechanisms, especially for remote sites. Firewalls protect data in transit by implementing IPSec in several configurations. Integrating IPSec into firewalls improves the ability to filter, encrypt, and authenticate data. Virtual Private Network (VPN) tunnels are protected by firewalls using IPSec. While allowing remote users or offices to connect to the central corporate network, firewalls possessing support for IPSec establish an encrypted tunnel over the internet that can’t be intercepted easily. Firewalls at different sites can use IPSec to establish a secure communication link. Data passing between these firewalls will be encrypted and authenticated, ensuring secure data exchange even if the packets traverse untrusted networks. Firewalls can enforce IPSec policies to encrypt data end-to-end in Cybersecurity Training Courses , ensuring that sensitive data is protected from when it leaves the sender’s device until it reaches the recipient. By supporting IPSec, firewalls ensure that the data transmitted between networks or devices cannot be intercepted, altered, or tampered with during transit.
Advantages of IP Security in Firewalls
Configuring IPSec in Firewalls
IPSec configuration involves several critical components to ensure secure communication. One of the essential elements is Security Associations, which provide parameters for the secure link between two devices. Each security association contains the encryption and authentication methods and an identifier for different security relationships. Key management is another important aspect, where Internet key exchange protocols handle the negotiation process for the encryption keys of the devices. IKE takes a two-phase approach, which divides its phases into two categories. Phase 1 is where an encrypted channel is established among devices, and Phase 2 is where encryption keys for transferring the data are negotiated. In addition, an appropriate choice of encryption and hash algorithms is required to secure communication in Privileged Access Management. Among the commonly used ones are AES for encryption and SHA (Secure Hash Algorithm) for integrity checking. These algorithms are then selected based on the need for communication security. For instance, if the two branch offices must communicate securely across the internet, their firewalls are configured to create an IPSec VPN tunnel. This would include defining the Security Association for the tunnel, selecting appropriate encryption and hashing algorithms, configuring IKE for secure key exchange, and setting up firewall rules to permit only encrypted IPSec traffic. Once the tunnel is established, any data exchanged between the sites will be fully encrypted and authenticated, ensuring secure communication.
Preparing for Cyber Security job interviews? Check out our Cyber Security Interview Questions and Answers now!
Challenges of Implementing IPSec in Firewalls
Ready to pass the interview for cybersecurity ? Learn how to answer Cybersecurity Interview Questions and Answers
Best Practices for Utilizing IPSec with Firewalls
Conclusion
The incorporation of IPSec with the firewalls ensures network communication security. IPSec has ensured protection for the transmitted data across firewalls by adding encryption and authentication. Though implementation of IPSec may come with challenges, its advantages in terms of sec, integrity, and data privacy far outweigh its potential complexity. Therefore, understanding the major components of IPSec will be beneficial to ensure that your networks are safely protected from many different types of cyber threats according to best practices. Apart from its contribution to the security and confidentiality of network communications, using IPSec with firewalls provides organizations with an efficient framework for protecting their sensitive data during transmission across networks they do not trust. Cybersecurity Training is because encryption prevents unauthorized access; authentication also prevents other kinds of cyberattacks, known to cause man-in-the-middle and data tampering. Configuring IPSec demands meticulous detail and comprehension, but the payoff regarding secure remote access, site-to-site connectivity, and data integrity makes it a valuable addition to the cybersecurity toolbox. Business networks can stay robust against constantly evolving threats properly implemented and monitored.





