
Subnets play a very important role in network management and improving performance in any network. Whether you are an IT professional, a student, or even just an interested learner who wants to know everything about computer network subnet in Cybersecurity Training Courses, it is essential to know subnets. In this blog post, let us introduce a subnet, how it works, and why it matters in modern networking.
Are you curious to know more about Cybersecurity ? Take advantage of our comprehensive online Cyber Security Online Training .
What is a Subnet?
A subnet, or subnetwork, is a logically visible portion of a greater network. Subnetting means splitting a large network into smaller, manageable pieces. In fact, each subnet constitutes a separate segment that can have its own set of rules and policies; this isolates traffic and improves overall Network Topology performance. A private subnet is defined by a network subnet mask that determines what portion of an IP address refers to the network and subnet and what part refers to the host. But it breaks down further to allow organizations to efficiently allocate their ip and subnet and gateway addressing and subnetting space, or ip address subnet, reduce network traffic, and improve security.
How Subnets Works
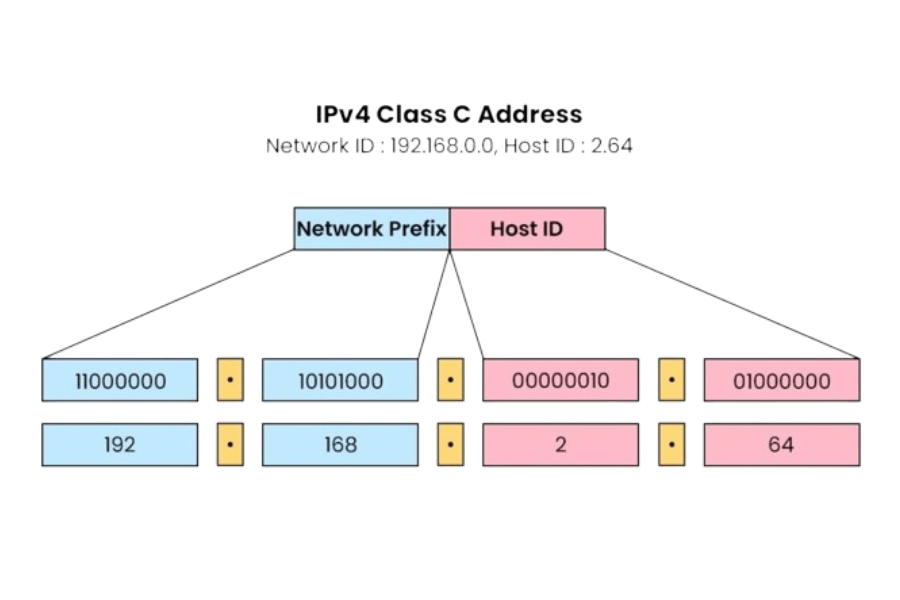
IP addressing and subnetting Masks:Understanding how ip addressing and subnetting works is key to understanding. An IP address has two fundamental parts: the network and host portions. A thirty-two-bit integer called a ip subnet mask divides an IP address into its network and subnet and host components. In the example ip addressing and private subnet of 192.168.1.10 using a network subnet mask of 255.255.255.0, the first three octets represent the Resolution Protocol , and the last octet represents the specific device.
CIDR Notation:Classless Inter-Domain Routing (CIDR) is one of the methods of distributing ip address subnet and routing the ip and subnet . It gives a better approach to define the ip subnet mask using notation like 192.168.1.0/24, where /24 shows the usage of the first 24 bits for the network and subnet and gateway part of IP while leaving room for 256 addresses ranging from 192.168.1.0 to 192.168.1.255
Sign up for ACTE Cyber Security Online Training and get a head start in your career cyber security.
Subnetting Process
Determine the Requirements:Consider what your network will require. How many devices will you connect? Will your network size likely increase in the future?
Select Private IP Range:Select an appropriate private IP range depending on your network’s size and scope. Some examples of a private subnet IP range are as follows:
- 10. x.x.x
- 172.16.x.x
- 192.168.x.x.
Use a Cybersecurity Training Courses mask to divide the block of IP addresses that you have chosen into smaller groups. For example, if you are using four ip subnet, you can use a network subnet mask of 255.255.255.192 to create four subgroups with 64 addresses for each.
Assign IP address:Assign specific ip address subnet to individual devices of each subgroup. This makes network management highly structured.
Want to Take the Lead in Cyber Security ? Enroll in ACTE’s Cybersecurity Expert Masters Program Training Course Program to Begin Your Adventure Now.
Importance of Subnets
Improved Network Performance:It will reduce broadcast traffic because it splits a very large network into smaller subnets, each subnet is independent in its workings. This reduces congestion on the network and enhances performance since devices work only in broadcast traffic inside theprivate subnet, improving overall efficiency in Web Security
Improved Security:It enhances security in a network because different parts of a network are isolated. For instance, you can use a network subnet for sensitive information and only grant the required users with authorized access to the data. Another function witnessed in this ip subnet level about security is firewalls and access control lists.
Simpler Management of a Network:Segmenting the network into Subnets makes its management easier. With broken-down groups, network administrators can easily monitor traffic, diagnose problems, and enforce policies more effectively. Can also be used to distribute ip and subnet addresses, avoid conflicts, and utilize them to the best efficiency.
Scalability:A network’s subnetting can only expand and keep up with changes. As the number of devices goes up, more subnets can be created without disrupting the network and subnet structure already in place. Scalability is also very important as businesses grow or network requirements may change.
Effective utilization of ip and subnet addresses:Because of the increasing scarcity of available IPv4 addresses, efficient usage of allocated ip address subnet is essential. Subnetting allows organizations to exploit their ip and subnet space more intensively with minimal waste and each assigned address accounted for.
Remote Work Affordability:Help to manage better classification of users and resources with remote work and distributed teams. In this way, different departments or teams can operate within their specific private subnet, which enables effective communication and cooperation while maintaining Database Security.
Preparing for Cyber Security job interviews? Check out our Cyber Security Interview Questions and Answers now!
Conclusion
Cybersecurity Training are among the most powerful tools in today’s networking. They easily bestow improved performance and enhanced security and provide simplification of management and scalability. Understanding the principles behind subnetting enables network professionals to optimize their networks for optimal interaction within today’s digital landscape. With technological innovation, ip subnet will only grow in importance. Mastery over the subnet and gateway would mean making more professional decisions with an efficient, secure network and scalable approach, whether managing a new network and subnet or an existing one. So, go ahead and discover the hidden wonders of subnets!





