
- Authentication Basics
- What is SAML?
- What is OAuth?
- Key Features of SAML
- Key Features of OAuth
- Comparing SAML and OAuth: Key Differences
- Use Cases of SAML
- Use Cases of OAuth
- Security Considerations
- Advantages and Disadvantages
- Real-world Examples
- Choosing the Right Protocol
Authentication Basics
In today’s digital-first world, where users frequently interact with multiple web and mobile applications, authentication and authorization protocols play a critical role in safeguarding sensitive information. These protocols define how users prove their identity and how systems grant them appropriate levels of access. As businesses increasingly rely on cloud services, single sign-on (SSO), and APIs, the need for secure and efficient authentication frameworks has grown significantly a focus often emphasized in Microsoft Azure Training programs. Two widely adopted standards in this field are Security Assertion Markup Language (SAML) and OAuth (Open Authorization). While both aim to enhance security and user experience, they were built for different purposes and thrive in distinct environments. Understanding their features, differences, and applications is essential for organizations to make the right choice when implementing secure access solutions.
To Explore Azure in Depth, Check Out Our Comprehensive Azure Training To Gain Insights From Our Experts!
What is SAML?
Security Assertion Markup Language (SAML) is an XML-based open standard for exchanging authentication and authorization data between identity providers (IdPs) and service providers (SPs). Developed by OASIS in the early 2000s, SAML was primarily designed to support Single Sign-On (SSO) across enterprise applications. The basic premise of SAML is that a user can authenticate with one identity provider (such as a corporate directory) and then gain seamless access to multiple applications without logging in repeatedly. For example, an employee logging into a company portal can automatically access tools like Salesforce, Office 365, or Dropbox without having to enter credentials again. SAML achieves this by using assertions structured XML documents that carry authentication, attribute, and authorization information. Its design makes it especially suitable for web-based enterprise environments where employees use multiple business applications, often integrated with cloud services and databases such as Amazon DynamoDB for secure and scalable data management.
What is OAuth?
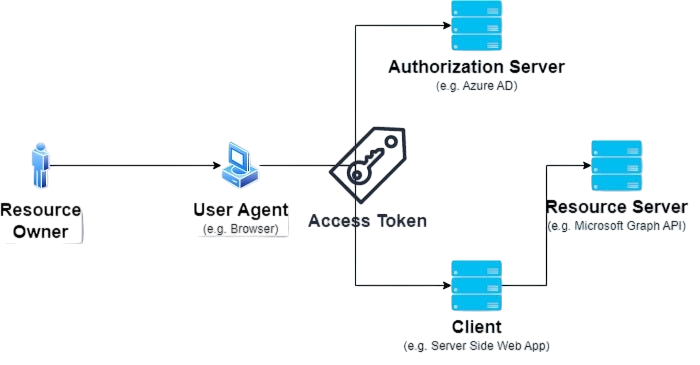
OAuth (Open Authorization), on the other hand, is a token-based open standard that focuses on authorization rather than authentication. Initially developed in 2006 for API access delegation, OAuth enables third-party applications to access user resources without exposing their actual credentials.
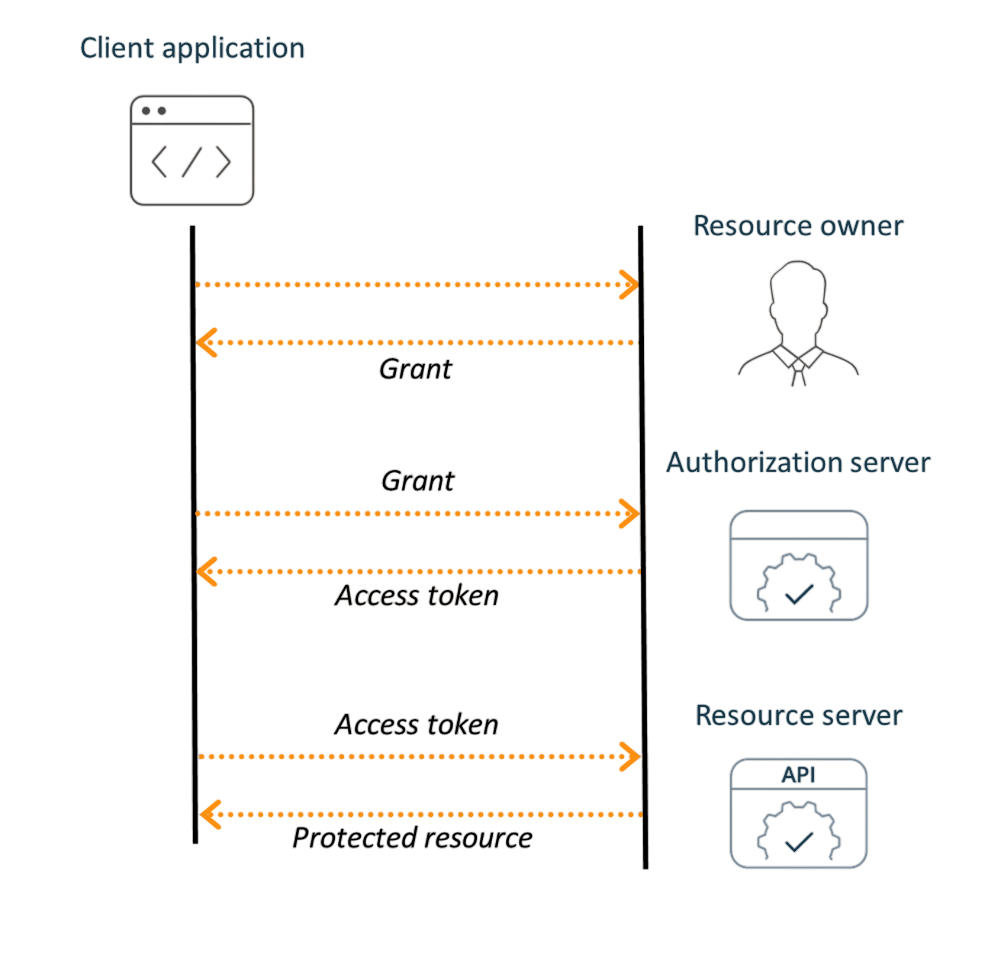
- Unlike SAML, which relies heavily on XML, OAuth leverages lightweight JSON structures, making it better suited for modern web and mobile applications.
- A common example is when you use your Google or Facebook account to log into a third-party app.
Instead of sharing your username and password with the app, OAuth issues an access token that grants limited access to your data for specific actions and timeframes. This design allows developers to build applications that integrate with external platforms while keeping user credentials secure. OAuth has evolved significantly, with OAuth 2.0 becoming the industry standard for delegated authorization in cloud and API-driven ecosystems.
Key Features of SAML
SAML comes with several defining characteristics that make it ideal for enterprise-level authentication:
- Single Sign-On (SSO): SAML’s primary feature is enabling users to authenticate once and access multiple applications seamlessly.
- XML-Based Assertions: Authentication and authorization information is exchanged in XML format, ensuring structured and detailed communication.
- Enterprise-Focused: Built with organizations in mind, SAML supports integration with corporate directories like Active Directory or LDAP.
- Federated Identity Management: It enables secure identity sharing across different domains, which is crucial for enterprises working with multiple SaaS vendors.
- Web-Centric Design:SAML was optimized for browser-based access to applications, making it less ideal for mobile or API-driven use cases a limitation often discussed in An Overview of Service Mesh , where modern architectures focus on secure, scalable communication between services.
- Token-Based Authorization: OAuth uses access tokens and refresh tokens to manage user sessions and permissions without exposing credentials.
- Granular Permissions: Users can grant limited access to applications, such as giving Spotify permission to read your playlist but not access your email.
- JSON-Friendly: OAuth relies on lightweight JSON structures, making it compatible with modern REST APIs and mobile environments.
- Wide Adoption in Consumer Apps: Popular platforms like Google, Facebook, Twitter, and GitHub extensively use OAuth for secure access delegation.
- API-Centric: OAuth was built for resource access in API-driven applications rather than traditional enterprise SSO.
- Corporate SSO: Employees log in once to access multiple workplace tools.
- Educational Institutions: Universities provide students with one set of credentials for various academic and administrative applications.
- Government Agencies: Secure access across multiple applications and agencies.
- B2B Collaborations: Federated identity allows partner organizations to securely share access to joint platforms.
- Social Media Integration: Third-party apps accessing your Google, Facebook, or Twitter accounts without storing passwords.
- Cloud Services: Granting Dropbox access to a photo editing app to retrieve and save files.
- IoT Devices: Smart home devices connecting to central apps with token-based authorization.
- API Economy: Businesses exposing APIs to developers while maintaining strict control over access permissions.
- SAML Security: Relies heavily on XML signatures and encryption. Vulnerabilities like XML injection or misconfigured identity providers can pose risks.
- OAuth Security: The biggest challenge is token leakage or improper implementation, which can allow unauthorized access. OAuth 2.0 also lacks strict standardization, so implementations may vary widely.
- Shared Risks: Both require careful handling of credentials, secure communication channels (HTTPS), and proper session management.
- SAML Example: A large enterprise integrates Active Directory with applications like Salesforce, enabling employees to log in once and access multiple apps without re-entering credentials.
- OAuth Example: A user grants a fitness tracking app permission to access their Google account data, such as calendar events, without sharing their Google password.
- Choose SAML if you are an enterprise managing employee access to multiple web-based applications and need robust single sign-on functionality.
- Choose OAuth if you are developing consumer applications, mobile apps, or APIs that require flexible, token-based authorization with granular control.
Key Features of OAuth
OAuth, particularly in its 2.0 version, has gained widespread adoption due to its versatility:
Interested in Obtaining Your Azure Certificate? View The Azure Training Offered By ACTE Right Now!
Comparing SAML and OAuth: Key Differences
Although they both deal with identity and access management, SAML and OAuth have different functions. Single Sign-On (SSO) and authentication are the main goals of SAML, which allows users to access numerous enterprise apps with a single set of login credentials.OAuth, on the other hand, is made for delegated access and authorization, enabling users to provide third-party apps with specific permissions without disclosing their passwords a concept thoroughly covered in Microsoft Azure Training to help professionals implement secure access control. OAuth is more contemporary and developer-friendly because it uses lightweight JSON tokens, while SAML depends on XML-based assertions. OAuth is best suited for mobile applications, APIs, and customer-facing services, whereas SAML is best suited for web-based and enterprise settings. From the standpoint of the user experience, OAuth gives users the ability to manage and share their data in a selected manner, while SAML offers a smooth login process across corporate resources. OAuth provides developers with a more straightforward and adaptable configuration, but SAML implementations are typically more complicated due to XML processing and corporate integration needs.
Gain Your Master’s Certification in Azure by Enrolling in Our Azure Training.
Use Cases of SAML
SAML is widely adopted in enterprise ecosystems where centralized identity management is critical:
Use Cases of OAuth
OAuth dominates consumer and mobile environments where flexible authorization is required a principle often highlighted in Optimizing AWS Performance & Costs , as secure and efficient access control contributes to better resource utilization and system scalability.
Security Considerations
Both SAML and OAuth enhance security but also come with risks:
Although SAML and OAuth both improve authorization and authentication, improper implementation can pose security threats a concern that becomes especially important during Cloud Migration , when sensitive data and access controls are being transitioned to cloud environments. Token leakage, XML vulnerabilities, setup errors, and insecure communication are among the main issues. Maintaining system integrity and preventing unwanted access requires using HTTPS, secure token handling, appropriate encryption, and frequent audits.
Preparing for Microsoft Azure interviews? Visit our blog for the best Azure Interview Questions and Answers!
Advantages and Disadvantages
Security Assertion Markup Language, or SAML, is a popular option for commercial settings due to its many benefits. Users can access numerous systems with a single set of credentials thanks to its comprehensive single sign-on (SSO) capabilities, business acceptance, and support for federated identity. SAML does, however, have several disadvantages. Because it is XML-based, it is more complicated and heavier than alternatives that are JSON-based, which makes maintenance and deployment more difficult. Furthermore, SAML’s poor support for API-first architectures and mobile applications may hinder its adaptability in contemporary development environments. OAuth, on the other hand, is a lightweight, developer-friendly protocol that focuses mostly on permission. It is ideal for consumer-facing apps, mobile apps, and APIs and provides granular access control using tokens. OAuth has significant drawbacks in addition to its benefits. Since it focuses more on authorisation than authentication, further steps are required to confirm the identity of the user. If not handled correctly, OAuth’s flexibility could result in unsafe implementations, and token management can be difficult, necessitating cautious handling to maintain security as explained in Azure Traffic Manager: A Complete Guide to Traffic Routing , proper configuration and management are crucial for ensuring secure and efficient system performance. Both SAML and OAuth have advantages and disadvantages, and an organization’s architecture and particular requirements will frequently determine which option is best.
Real-world Examples
Choosing the Right Protocol
The decision between SAML and OAuth depends on the use case:
In many cases, organizations use both protocols together SAML for employee authentication across enterprise systems, and OAuth for API authorization in customer-facing apps. Additionally, newer frameworks like OpenID Connect (OIDC) build on OAuth 2.0 to provide authentication features, bridging the gap between SAML and OAuth. Your authentication and authorization requirements will determine whether you choose SAML or OAuth a decision often explored in Microsoft Azure Training to help professionals design secure and scalable identity solutions. OAuth is perfect for contemporary consumer apps, mobile platforms, and APIs that require flexible, token-based access, whereas SAML is best suited for enterprise settings that demand secure single sign-on across internal applications. To ensure a balanced and safe access strategy, many organisations use both OAuth (or OpenID Connect) for external or customer-facing connections and SAML for internal identity management.





