Azure Active Directory B2C (Azure AD B2C) is an identity management service that enables custom control of how your customers sign up, sign in, and manage their profiles when using your iOS, Android, . NET, single-page (SPA), and other applications.
- Introduction to Azure Active Directory B2C
- Who uses Azure AD B2C?
- Custom-branded identity solution
- Single sign-on access with a user-provided identity
- Integrate with external user stores
- Progressive profiling
- Third-party identity verification and proofing
- Example: WoodGrove Groceries
- Authenticate individual customers
- Authenticate business customers
- Authenticate partners
- Azure AD B2C tenant
- Accounts in Azure AD B2C
- Protocols and tokens
- Conclusion
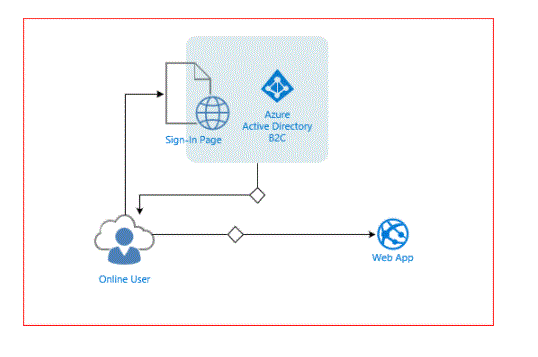
- Azure Active Directory B2C provides business-to-customer identity as a service. Your customers use their preferred social, enterprise or local account identity to gain single sign-on access to your Applications and APIs.
- Infographic of Azure AD B2C Identity Providers and Downstream Applications.
- Azure AD B2C is a Customer Identity Access Management (CIAM) solution capable of supporting millions of users and billions of authentications per day. It takes care of scaling and security of the authentication platform, monitors, and automatically deals with threats such as denial-of-service, password spray, or brute force attacks.
- Azure AD B2C is a separate service from Azure Active Directory (Azure AD). It is built on the same technology as Azure AD but for a different purpose. It allows businesses to build customer-facing applications, and then allows anyone to sign up to those applications, with no restrictions on user accounts.
Introduction to Azure Active Directory B2C:
Who uses Azure AD B2C?
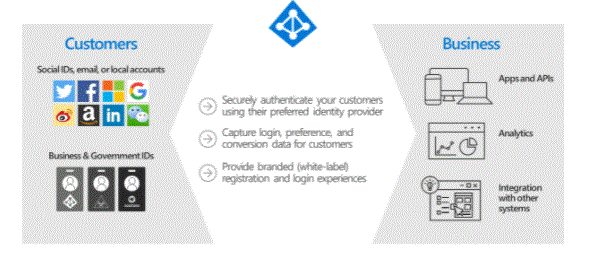
Any business or individual who wants to authenticate end users for their web/mobile applications using white-label authentication solutions. In addition to authentication, the Azure AD B2C service is used for authorization such as access to API resources by authenticated users. Azure AD B2C is intended to be used by IT administrators and developers.
Custom-branded identity solution:
Azure AD B2C is a white-label authentication solution. You can customise the entire user experience with your brand so that it blends seamlessly with your web and mobile applications.
Customise every page displayed by Azure AD B2C when your users sign up, sign in, and modify their profile information. Optimise HTML, CSS, and JavaScript in your user journey so that the Azure AD B2C experience looks and feels like it’s a core part of your application.
Single sign-on access with a user-provided identity:
Azure AD uses B2C standards-based authentication protocols, including OpenID Connect, OAuth 2.0, and Security Assertion Markup Language (SAML). It integrates with most modern applications and commercial off-the-shelf software.
By serving as the central certification authority for your web applications, mobile apps and APIs, Azure AD B2C enables you to build a single sign-on (SSO) solution for all of them. Centralise the collection of user profile and preference information, and get detailed analytics about sign-in behaviour and sign-up conversions.
- Azure AD B2C provides a directory that can contain up to 100 custom attributes per user. However, you can integrate with external systems as well. For example, use Azure AD B2C for authentication, but entrust an external customer relationship management (CRM) or customer loyalty database as the source of truth for customer data.
- Another external user store scenario is that Azure AD B2C handles the authentication of your application, but integrates with an external system that stores user profiles or personal data. For example, to meet data residency requirements such as regional or on-premises data collection policies. However, the Azure AD B2C service itself is worldwide via the Azure public cloud.
- Azure AD can facilitate collecting information from the user during B2C registration or profile editing, then handing that data to external systems via APIs. Then, during future authentication, Azure AD B2C can retrieve data from external systems and, if necessary, include it as part of the authentication token response that it sends to your application.
Integrate with external user stores:
Progressive profiling:
Another user journey option involves progressive profiling. Progressive profiling allows your customers to complete their first transaction quickly by collecting a minimal amount of information. Then, gradually collect more profile data from the customer at future sign-ins.
- Use Azure AD B2C to facilitate identity verification and proofing by collecting user data, then passing it to a third-party system to be approved for verification, trust scoring, and user account creation.
- You’ve learned a few things you can do with Azure AD B2C as your business-to-customer identity platform. The following sections of this overview walk you through a demo application that uses Azure AD B2C. You are welcome to move on to a more in-depth technical overview of Azure AD B2C.
Third-party identity verification and proofing:
Example: WoodGrove Groceries:
Business Overview
Woodgrove is an online grocery store that sells groceries to both individual consumers and business customers. Their business customers buy groceries on behalf of their company, or the businesses they manage.
sign-in options
Woodgrove Grocery offers several sign-in options based on the relationship its customers have with the store.
Individual customers may sign up or sign in with different accounts, such as with a social identity provider or email address and password.
Business customers can sign up or sign in with their enterprise credentials. Partners and suppliers are individuals who supply products for the grocery store to sell. Partner Identity Azure Active Directory B2B . is provided by
- When a customer selects to sign in with your personal account, they are redirected to a customised sign-in page hosted by Azure AD B2C. You can see in the following image that we have optimised the User Interface (UI) to make it look and feel like the Woodgrove Grocery website. Woodgrove customers should be unaware that the authentication experience is hosted and secured by Azure AD B2C.
- Woodgrove allows its customers to sign up and sign in using their Google, Facebook or Microsoft accounts as their identity provider. Or, they can sign up using their email address and password to create a local account.
- When a customer selects sign up with your personal account and then signs up now, they are presented with a custom sign-up page.
- After entering the email address and selecting Send Verification Code, Azure AD B2C sends them the code. Once they enter their code, select Verify Code, and then enter other information on the form, they will also need to agree to the terms of service.
- Clicking the Create button redirects the Azure AD B2C user back to the WoodGrove grocery website. When this redirect occurs, Azure AD passes an OpenID Connect authentication token to the B2C Woodgrove web application. The user is now signed-in and ready to go, with their display name shown in the top-right corner to indicate that they are signed in.
Authenticate individual customers:
- When a customer selects one of the options under Business Customers, the Woodgrove Grocery website applies a different Azure AD B2C policy to individual customers. You learn what a B2C policy is in the technical overview of Azure AD B2C.
- This policy provides the user with the option to use their corporate credentials for sign-up and sign-in. In the Woodgrove example, users are asked to sign in with either a work or school account. This policy uses a multi-tenant Azure AD application and /common Azure AD endpoint to federate Azure AD B2C with any Microsoft 365 customer in the world.
Authenticate business customers:
Authenticate partners:
The sign in link with your supplier account uses the collaboration functionality of Azure Active Directory B2B. Azure AD B2B is a family of features in Azure Active Directory for managing partner identities. Those identities can be federated from Azure Active Directory for access in Azure AD B2C-protected applications.
Azure AD B2C tenant:
In Azure Active Directory B2C (Azure AD B2C), a tenant represents your organisation and is a directory of users. Each Azure AD B2C tenant is separate and separate from other Azure AD B2C tenants. An Azure AD B2C tenant is different from an Azure Active Directory tenant that you may already have.
The primary resources you work with in an Azure AD B2C tenant are:
TDirectory – The directory is where Azure AD B2C stores your users’ credentials, profile data, and your application registrations.
TApplication Registration – Register your web, mobile and native applications with Azure AD B2C to enable identity management. You can register any API you want to secure with Azure AD B2C.
TUser Flows and Custom Policies – Create an identity experience for your applications with built-in user flows and fully configurable custom policies:
TSign-in options – Azure AD B2C provides various sign-up and sign-in options for users of your application: Username, email, and phone sign-in – Configure your Azure AD B2C local accounts to allow sign-up and sign-in with a username, email address, phone number, or combination of methods.
TSocial Identity Providers – Associations with social providers such as Facebook, LinkedIn, or Twitter.
TExternal Identity Provider – Federated with standard identity protocols such as OAuth 2.0, OpenID Connect, and more.
TKeys – Add and manage encryption keys for signing and verification of tokens, client secrets, certificates and passwords.
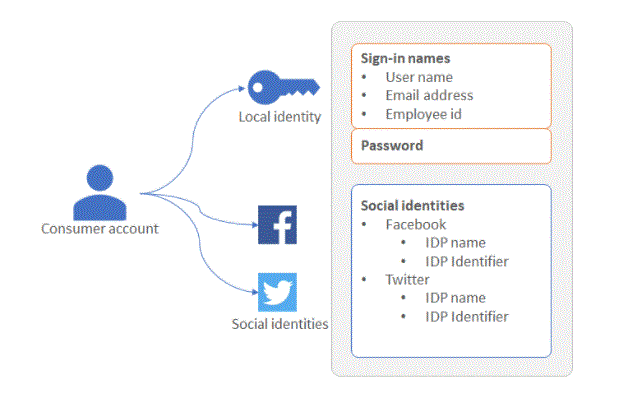
Accounts in Azure AD B2C:
Azure AD B2C defines several types of user accounts. Azure Active Directory, Azure Active Directory B2B, and Azure Active Directory B2C share these account types.
Work account – Users with a work account can manage resources in the tenant, and with the administrator role, can also manage the tenant. Users with work accounts can create new user accounts, reset passwords, block/unblock accounts, and set permissions or assign an account to a security group.
Guest Account – External users that you invite to your tenant as a guest. A typical scenario for inviting a guest user to your Azure AD B2C tenant is to share admin responsibilities.
Consumer Account – Accounts that are managed by Azure AD B2C user flows and custom policies. Azure AD B2C User Management page in Azure Portal.
Image: User directory within an Azure AD B2C tenant in the Azure portal.
consumer accounts
With a consumer account, users can sign in to applications that you have secured with Azure AD B2C. Users with consumer accounts, however, cannot access Azure resources, for example the Azure Portal.
A consumer account can be associated with these identity types:
Locally stored in Azure AD B2C directory with local identity, username and password. We often refer to these identities as “local accounts”. Social or enterprise identity, where the user’s identity is managed by a federated identity provider. For example, Facebook, Google, Microsoft, ADFS, or Salesforce. A user with a consumer account can sign in with multiple identities. For example username, email, employee id, government id, and others. A single account can have multiple identities, both local and social.
Local account sign-in option
Azure AD B2C provides various ways that users can authenticate a user. Users can sign-in to a local account using a username and password, phone verification (also known as password-less authentication). Email sign-up is enabled by default in your local account identity provider settings
User Profile Attributes
Azure AD B2C lets you manage common features of consumer account profiles. For example display name, surname, given name, city and so on. You can also extend the Azure AD schema to store additional information about your users. For example, their country/region of residence, preferred language, and preferences such as whether they wish to subscribe to newsletters or enable multi-factor authentication.
Sign-in with external identity providers
You can configure Azure AD B2C so that users can sign in to your application with credentials from social and enterprise identity providers. Azure AD B2C can be federated with identity providers that support the OAuth 1.0, OAuth 2.0, OpenID Connect, and SAML protocols. For example, Facebook, Microsoft Account, Google, Twitter and AD-FS.
- For external identities, Azure AD B2C supports federation with any OAuth 1.0, OAuth 2.0, OpenID Connect and SAML identity providers.
- The trusted party application initiates an authorization request to Azure AD B2C using OpenID Connect.
- When a user of the application chooses to sign in using an external identity provider that uses the SAML protocol, Azure AD B2C implements the SAML protocol to communicate with that identity provider.
- After the user completes the sign-in operation with an external identity provider, Azure AD B2C then returns the token to the dependent party application using OpenID Connect.
Protocols and tokens:
For applications, Azure AD supports OAuth 2.0, OpenID Connect and SAML protocols for the B2C user journey. Your application starts the user journey by issuing an authentication request to Azure AD B2C. The result of a request to Azure AD B2C is a security token, such as an ID token, access token, or SAML token. This security token defines the identity of the user within the application.
Conclusion:
Azure AD is an identity as a service provider that aims to provide and control access to cloud resources to the users of the organisation. Azure AD B2B is not a separate service but a feature in Azure AD. It allows cross-organization collaboration across applications from an identity standpoint.
Azure AD B2C is a free service for creating consumer application identity repositories. If you need a service to handle email or Facebook login – This is for you.
Azure Active Directory B2C is a comprehensive identity management solution. It is a reliable service for authentication and identity management in consumer-facing apps as it provides easy access and security to users.