
- Introduction to Infrastructure as Code (IaC)
- What is Terraform?
- What is Ansible?
- Key Features of Terraform
- Key Features of Ansible
- Configuration Management vs. Orchestration
- How Terraform and Ansible Work Together
- Terraform vs. Ansible: Use Cases
- Performance Comparison
- Security Considerations
- Future Trends in IaC
Introduction to Infrastructure as Code (IaC)
Infrastructure as Code (IaC) is a key practice in modern DevOps and cloud-native environments, where infrastructure is provisioned, configured, and managed using code instead of manual processes. IaC allows teams to automate and replicate infrastructure setups consistently and efficiently. It provides the ability to define an application’s infrastructure needs in machine-readable files that can be versioned, shared, and reused. This practice minimizes human error, improves the reproducibility of environments, and accelerates development and deployment cycles. IaC has become a cornerstone of modern IT and cloud practices, significantly enhancing infrastructure provisioning efficiency, scalability, and consistency. Popular tools like Terraform and Ansible have emerged to streamline this process and offer different approaches to infrastructure management.
What is Terraform?
Terraform is an open-source tool developed by HashiCorp for provisioning and managing infrastructure. It lets users define infrastructure in a high-level configuration language called HCL (HashiCorp Configuration Language). With Terraform, you can provision resources on cloud platforms like AWS, Microsoft Azure, Google Cloud, and other providers. It supports managing cloud infrastructure and services like DNS, databases, and networking.
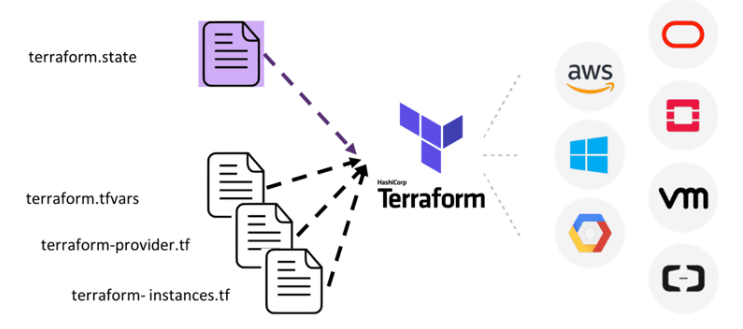
Terraform follows the principle of declarative configuration, meaning that you define the desired end state of the infrastructure, and Terraform automatically determines the steps needed to achieve that state. It then communicates with cloud providers’ APIs to manage resources, ensuring the environment matches the defined configuration.
Key Features of Terraform
- Multi-cloud Support: Terraform can manage resources across multiple cloud providers simultaneously.
- Declarative Configuration: Terraform allows you to define the infrastructure’s appearance and handles the underlying complexity of provisioning resources.
- State Management: Terraform tracks your infrastructure’s state to ensure that it is created, updated, or destroyed as necessary.
- Resource Graph: Terraform builds a graph of resources to understand dependencies and can parallelize resource creation, improving performance.
- Plan and Apply: Terraform has a two-step process: first, it generates an execution plan (showing the intended changes), and then it applies those changes to the infrastructure.
What is Ansible?
Ansible, an open-source automation tool developed by Red Hat, is used for configuration management, application deployment, and task automation. Unlike Terraform, Ansible primarily focuses on configuration management and orchestration. It enables you to automate software and services’ setup, configuration, and management across multiple systems.
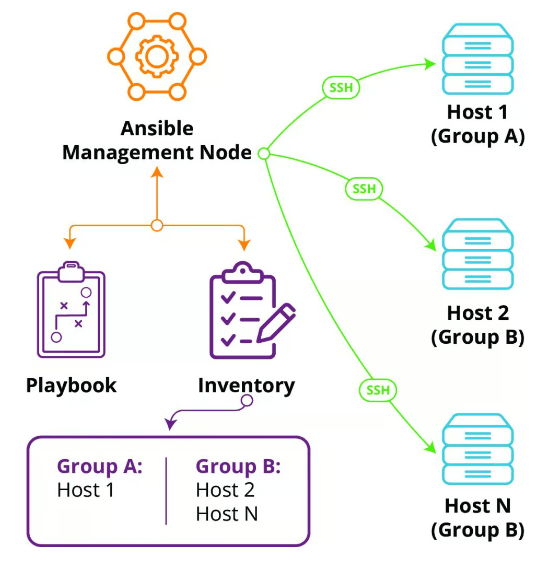
Ansible uses a push-based model, meaning that you define playbooks (sets of instructions) and push them to the managed systems for execution. Ansible can work on multiple environments, including Linux, Windows, and cloud infrastructure, and is particularly well-known for its simplicity and ease of use.
Key Features of Ansible
- Agentless Architecture: Ansible doesn’t require agents to be installed on the managed systems. It uses SSH to communicate with Linux servers and WinRM with Windows systems.
- Idempotency: Ansible playbooks are idempotent, meaning that applying the same playbook multiple times will result in the same outcome, ensuring the system configuration is stable.
- Ease of Use: Ansible uses YAML for its playbooks, making the configuration files easy for technical and non-technical users to read and understand.
- Powerful Orchestration: Ansible executes complex workflows across multiple systems, including services, networks, and databases.
- Extensive Modules: Ansible offers a vast library of pre-built modules for managing various systems, services, and applications.
Configuration Management vs. Orchestration
- Before comparing Terraform and Ansible, it’s essential to understand the difference between configuration management and orchestration.
- Configuration management tools, like Ansible, focus on maintaining the state of systems and software over time.
- Configuration Management focuses on configuring systems and software. It ensures the systems have the right configurations, software packages, or security settings.
- Orchestration involves automating the provisioning and management of infrastructure, especially across multiple platforms and services.
- Orchestration tools like Terraform focus on provisioning resources in a cloud environment, ensuring that infrastructure is created, updated, and managed in an automated and repeatable manner.
- Terraform is generally used for infrastructure provisioning and orchestration, while Ansible is commonly used for configuration management and orchestration of the software layer.
How Terraform and Ansible Work Together
While Terraform and Ansible serve distinct purposes, they can complement each other to provide a comprehensive infrastructure management solution. Terraform is primarily used for provisioning infrastructure, such as creating virtual machines, networks, and storage resources. On the other hand, Ansible is responsible for configuring the systems once they are provisioned, handling tasks like software installation, database configuration, or application deployment. A typical workflow involves using Terraform to provision the cloud infrastructure such as creating a virtual machine or network followed by using Ansible to configure the virtual machine, which may include tasks like installing Apache, setting up a web application, or configuring monitoring. In essence, Terraform is focused on defining the infrastructure, while Ansible is centered on defining and managing the software and system configuration.
Terraform vs. Ansible: Use Cases
Terraform Use Cases:
- Provisioning Cloud Resources: Terraform is ideal for automating the provisioning of resources on public or private clouds, including virtual machines, networking, storage, and databases.
- Multi-cloud Infrastructure: Terraform can manage infrastructure across multiple clouds simultaneously, making it suitable for hybrid or multi-cloud environments.
- Creating Complex Infrastructure: With Terraform, you can automate the creation of complex cloud environments, such as multi-tier applications or serverless infrastructures.
- Managing State: Terraform’s state management feature ensures that you always have an up-to-date record of your infrastructure, which makes it easier to track changes and perform rollbacks.
Ansible Use Cases:
- Configuration Management: Ansible is excellent for automating software and system configuration tasks, such as installing packages, configuring web servers, and managing firewalls.
- Application Deployment: Ansible excels in deploying applications across multiple servers. It’s often used for rolling deployments and scaling applications.
- Server and Service Orchestration: Ansible is ideal for orchestrating complex tasks, like configuring an entire environment with the right software, dependencies, and network configurations.
- Infrastructure Automation: While Terraform is the go-to for provisioning, Ansible can also handle provisioning and configuration of infrastructure, especially when you need a quick, ad-hoc setup.
Performance Comparison
When comparing the performance of Terraform and Ansible, it’s essential to recognize that each tool serves a different purpose and is optimized for distinct tasks. Terraform is designed for infrastructure provisioning, and it excels at managing large-scale environments. Its strength lies in its ability to create and manage resources in parallel, allowing for efficient and fast provisioning of infrastructure. The planning and application processes in Terraform are optimized to handle large-scale environments with ease, making it ideal for managing complex infrastructure at scale, such as cloud resources, networking, and storage. On the other hand, Ansible focuses on configuration management, software deployment, and orchestration. While it is highly effective for managing smaller-scale tasks, such as configuring systems or deploying applications, it may not perform as efficiently when scaling to a large number of nodes. Without optimizations like parallel execution, Ansible can experience slower performance in more extensive environments. However, for tasks like installing software, configuring databases, or orchestrating processes across servers, Ansible excels at ensuring systems are configured correctly and efficiently. In conclusion, Terraform is more efficient for provisioning infrastructure at scale, while Ansible is better suited for configuration management and orchestration, particularly for smaller to medium-sized tasks or environments.
Security Considerations
Terraform Security Considerations:
- Sensitive Data: Terraform allows you to manage sensitive information (like API keys or credentials) using tools such as Vault. It’s essential to ensure that the state files containing information about your infrastructure are securely stored and encrypted.
- Access Control: Using IAM roles and policies on cloud platforms, ensure that users have appropriate permissions for managing resources through Terraform.
- Auditing: Terraform maintains a state file that contains sensitive information about the infrastructure, so care must be taken to avoid exposing this data.
Ansible Security Considerations:
- Secure SSH Communication: Ansible uses SSH to communicate with Linux machines and WinRM for Windows, ensuring that the data in transit is encrypted. Strong encryption keys and the security of the authentication process are important.
- Sensitive Variables: When dealing with sensitive data (like passwords), Ansible supports Vault in encrypting sensitive variables, making storing credentials and secrets in playbooks safe.
- Role-Based Access Control: Use Ansible’s role-based access control (RBAC) and Ansible Tower to manage and control who can access playbooks and inventory.
Future Trends in IaC
The future of Infrastructure as Code looks promising, with trends that include:
- Serverless IaC: More tools and providers are embracing serverless computing, where developers no longer need to manage servers but can still use IaC principles to manage cloud functions and resources.
- GitOps: This practice combines Git workflows with IaC, allowing all infrastructure management through Git repositories, leading to more automation and collaboration.
- Multi-Cloud IaC: As organizations use multiple cloud providers, IaC tools will evolve to manage complex multi-cloud infrastructures more seamlessly.
- Security Automation: Integrating security within the IaC workflow will become more prevalent, allowing organizations to ensure secure and compliant infrastructure from the outset.





