
- Introduction to AWS Network Load Balancer
- Key Features of AWS Network Load Balancer
- What is AWS Network Load Balancer?
- Benefits of Network Load Balancer
- How AWS Network Load Balancer Works
- Configuring AWS Network Load Balance
- Troubleshooting and Best Practices
- Conclusion
Introduction to AWS Network Load Balancer
AWS Network Load Balancer (NLB) is a high-performance, fully managed load balancing service designed to handle millions of requests per second while maintaining ultra-low latency. It operates at Layer 4 (Transport Layer) of the OSI model, efficiently distributing TCP, UDP, and TLS traffic across multiple Amazon EC2 instances, containers, and IP addresses. Unlike Application Load Balancers (ALB), which operate at Layer 7, NLB focuses on managing network traffic at the connection level, making it ideal for applications requiring high throughput, low latency, and seamless failover. One of the key advantages of NLB is its ability to support static IP addresses for improved accessibility and simplified DNS configurations, a concept that is thoroughly covered in the Amazon Web Service Training. Additionally, it enables zonal isolation, ensuring that even if an availability zone (AZ) experiences issues, the load balancer can still operate efficiently across remaining zones. With connection tracking and preserving client IP addresses, NLB provides better control and visibility over incoming traffic, making it a preferred choice for financial services, gaming applications, and real-time communication platforms.
Are You Interested in Learning More About AWS? Sign Up For Our AWS Course Today!
Key Features of AWS Network Load Balancer
- High Scalability : AWS Network Load Balancer (NLB) is designed to handle millions of requests per second while maintaining high throughput. It efficiently distributes traffic to backend instances without compromising performance, making it suitable for handling sudden spikes in demand.
- Low Latency : NLB operates with ultra-low latency, ensuring minimal delays in processing requests. This makes it ideal for latency-sensitive applications such as gaming, financial services, and real-time communications where every millisecond matters.
- Static IP Support : Unlike other load balancers, NLB allows users to associate a static IP address with the load balancer, ensuring a fixed endpoint for applications. This simplifies DNS configurations and improves network stability, making it an ideal solution for Future-Ready SaaS for Your Business.
- Zonal Isolation : Each Availability Zone operates independently, meaning that failures in one zone do not impact load balancing in others. This design enhances fault tolerance and improves application resilience.
- Preserve Source IP : NLB forwards traffic to backend instances while preserving the original client IP address. This is essential for applications that rely on IP-based security controls or logging for analytics and monitoring.
- Integration with AWS Services : NLB seamlessly integrates with other AWS services such as EC2 Auto Scaling, AWS Global Accelerator, AWS WAF (Web Application Firewall), and AWS Security Groups, ensuring enhanced security, availability, and performance optimization.
- TLS Termination : NLB supports SSL/TLS offloading, allowing it to handle encryption and decryption of requests. This reduces the computational load on backend instances, freeing up resources for application processing and improving overall efficiency.
- Cross-Zone Load Balancing : Users can enable cross-zone load balancing to distribute incoming traffic evenly across multiple Availability Zones, ensuring better resource utilization and fault tolerance.
- Health Checks and Monitoring : NLB performs continuous health checks on registered instances, automatically directing traffic only to healthy targets. This ensures high availability and minimizes downtime. AWS CloudWatch integration allows users to monitor performance metrics and set up alerts for proactive management.
- Security and Compliance : NLB works with AWS PrivateLink, allowing private connectivity to services without exposing traffic to the public internet. It also supports DDoS protection through AWS Shield, ensuring a secure networking environment.
What is the AWS Network Load Balancer
AWS Network Load Balancer (NLB) is a high-performance Layer 4 load balancing service designed to manage extreme levels of traffic with ultra-low latency. It is optimized for handling millions of requests per second, making it a suitable choice for applications that require high throughput, such as real-time analytics, IoT (Internet of Things), gaming, and financial transactions. Unlike the Application Load Balancer (ALB), which operates at Layer 7 (application layer) and makes routing decisions based on HTTP/S requests, the NLB works at Layer 4 (transport layer) and directs traffic based on TCP/UDP connections.One of the key benefits of an NLB is its ability to preserve the source IP address of incoming requests, which allows backend servers to identify and process client requests more effectively, especially when considering the differences between Containers Vs Virtual Machines. This is particularly useful for applications that require IP-based security policies or compliance with regulatory requirements. Additionally, NLB supports static IP addresses and integrates seamlessly with Amazon Virtual Private Cloud (VPC), making it an ideal choice for applications needing low-latency, high-availability network traffic management. The auto-scaling capability of NLB ensures that it can dynamically scale to accommodate fluctuating traffic loads without manual intervention. It efficiently distributes incoming requests across multiple Amazon EC2 instances, containers, or on-premises servers to maintain availability and performance.
To Earn Your AWS Certification, Gain Insights From Leading AWS Experts And Advance Your Career With ACTE’s AWS Course Today!
Benefits of AWS Network Load Balancer
- Improved Performance : AWS EC2, combined with Elastic Load Balancing (ELB), ensures fast and reliable traffic distribution for high-demand applications. By balancing the workload across multiple instances, ELB prevents performance bottlenecks, reducing latency and improving response times. It optimally routes requests to healthy instances, ensuring smooth and efficient application delivery, even during peak traffic periods.
- Enhanced Security : Security is a top priority for AWS EC2 and ELB. ELB works seamlessly with AWS WAF (Web Application Firewall), security groups, and network ACLs (Access Control Lists) to provide multiple layers of protection. These security features help safeguard applications from threats like DDoS attacks, unauthorized access, and malicious traffic. Additionally, ELB supports SSL/TLS encryption, ensuring secure communication between clients and instances.
- Highly Available and Fault-Tolerant : ELB automatically distributes incoming traffic across multiple EC2 instances located in different Availability Zones (AZs). This ensures redundancy, minimizing the impact of instance failures and improving overall system reliability, as highlighted in the Introduction To Docker Networking. With health checks, ELB continuously monitors instance health and reroutes traffic to healthy instances if any become unavailable, guaranteeing uninterrupted service.
- Cost-Effective : AWS EC2 and ELB follow a pay-as-you-go pricing model, where users only pay for the resources they consume. With no upfront costs, organizations can efficiently scale their infrastructure without over-provisioning. Additionally, features like Spot Instances, Reserved Instances, and Savings Plans help further optimize costs for predictable and variable workloads.
- Automatic Scaling : ELB integrates seamlessly with EC2 Auto Scaling, allowing automatic instance provisioning based on traffic demand. This eliminates the need for manual intervention while ensuring optimal performance and cost-efficiency. Applications can handle traffic spikes dynamically without overloading any single instance, improving the overall user experience.
- Ease of Use : AWS EC2 and ELB are designed for simplicity and ease of deployment. Users can configure them through the AWS Management Console, AWS CLI (Command Line Interface), or SDKs (Software Development Kits). Predefined templates, automation scripts, and seamless integration with other AWS services make setup and management straightforward, even for teams with limited cloud experience.
How AWS Network Load Balancer Works
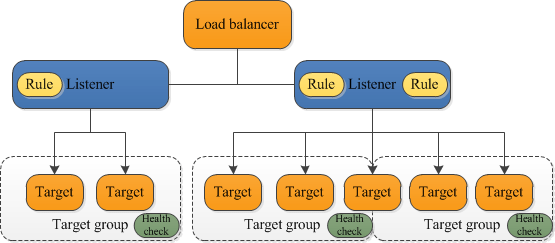
AWS Network Load Balancer (NLB) efficiently distributes incoming TCP/UDP traffic to backend targets, including EC2 instances, containers, and on-premises servers. It operates using a flow hash algorithm, ensuring session persistence while balancing connections across multiple targets. When a client initiates a request, NLB intelligently routes it to a registered target within a specified target group based on pre-configured health checks. If a target becomes unhealthy, NLB automatically detects the failure and redirects traffic to healthy instances, maintaining high availability and reliability.NLB supports listener rules, which define how incoming traffic is processed based on protocol (TCP, UDP, or TLS) and port configuration. Each listener inspects inbound connections and forwards them to the appropriate target group, ensuring seamless application performance, as explained in the AWS Training. Additionally, NLB offers TLS offloading, which offloads encryption and decryption tasks from backend servers, reducing computational overhead and improving efficiency. With its low latency, high scalability, and ability to handle millions of requests per second, AWS NLB is ideal for applications requiring ultra-fast response times and seamless failover mechanisms.
Gain Your Master’s Certification in AWS by Enrolling in Our AWS Masters Course.
Configuring AWS Network Load Balancer
- Create an NLB: To set up a Network Load Balancer (NLB) in AWS, begin by navigating to the AWS Management Console. In the EC2 dashboard, select “Load Balancers” from the left-hand menu and click “Create Load Balancer” to initiate the setup process. AWS provides different types of load balancers, including Application Load Balancer (ALB), Network Load Balancer (NLB), and Gateway Load Balancer (GWLB). For high-performance applications requiring ultra-low latency and handling millions of requests per second, select Network Load Balancer.
- Define Load Balancer Details: After selecting the Network Load Balancer, the next step is to configure its details. Provide a unique and descriptive name that reflects its purpose, such as prod-nlb-webapp or finance-nlb-api. Next, choose the scheme either Internet-facing or Internal. An Internet-facing NLB assigns a public IP address, making it accessible from the Internet, a concept explored in AWS Journey 10 Beginner-Friendly Projects. It is ideal for applications that serve external users. An Internal NLB, on the other hand, assigns a private IP address and is used for internal services within a Virtual Private Cloud (VPC).
- Configure Listeners: Listeners define how the NLB receives and forwards incoming traffic to registered targets. In this step, select protocols (TCP, UDP, or TLS) and listening ports for incoming traffic. TCP is the most commonly used protocol for general applications, while UDP is ideal for low-latency applications such as VoIP, gaming, and streaming. TLS (Transport Layer Security) enhances security by encrypting traffic before forwarding it to backend servers.
- Enable Health Checks: To ensure that only healthy backend instances receive traffic, enable health checks and define appropriate parameters. Health checks regularly monitor the status of targets and automatically remove unhealthy instances from the load-balancing rotation. Key parameters include health check protocol (TCP, HTTP, HTTPS), port number, check interval, timeout duration, success thresholds, and failure thresholds. The interval defines how frequently AWS probes targets for health, while the timeout determines how long AWS waits for a response before marking an instance as unhealthy.
- Create a Target Group: A target group is required to register backend instances or services that will handle the forwarded traffic. Choose the target type either EC2 Instances, IP Addresses, or AWS Lambda functions. For EC2 instances, manually select instances running in the configured VPC, ensuring they are correctly tagged for easier management. When using IP addresses, specify external IPs or private addresses of instances located outside the AWS environment. AWS Lambda functions can also be configured as targets to execute serverless applications when specific traffic conditions are met.
- Select Availability Zones: For high availability and redundancy, it is essential to select at least two Availability Zones (AZs) when deploying the NLB. AWS recommends distributing instances across multiple AZs to ensure uninterrupted service in case of failures. Each AZ represents a physically separated data center with independent infrastructure, reducing the risk of single-point failures, a concept that is key in understanding What Is Azure Site Recovery. By deploying the NLB across multiple subnets in different AZs, traffic can be dynamically routed to the nearest healthy instance, ensuring a seamless user experience.
- Assign Security Groups and Permissions: To control access to the NLB and backend instances, configure security groups and network ACLs (Access Control Lists). Security groups act as virtual firewalls, defining rules for inbound and outbound traffic. Allow only necessary ports (e.g., port 80 for HTTP, port 443 for HTTPS, and port 22 for SSH) to minimize the attack surface. Additionally, for TLS listeners, ensure that proper SSL/TLS encryption policies are applied.
- Review and Deploy: After configuring all required settings, review the NLB setup before deployment. Carefully verify the listener configurations, target group settings, security policies, and health check parameters. Ensure that instances are correctly registered, and security groups allow expected inbound/outbound traffic. Once confirmed, click “Create Load Balancer” to deploy the NLB. AWS provisions the NLB within minutes, assigning a DNS name for routing traffic.
Troubleshooting and Best Practices
To ensure optimal performance and reliability, it is essential to follow several best practices when configuring and managing a Network Load Balancer (NLB) in AWS. Monitoring health metrics is a critical step, and Amazon CloudWatch should be used to track instance health, request latency, and response codes. These insights help in identifying performance bottlenecks and detecting potential failures before they impact users. Another key best practice is enabling cross-zone load balancing, which ensures that traffic is evenly distributed across all available instances, preventing the overloading of specific instances in a single availability zone. This approach improves resource utilization and enhances the overall system stability, as discussed in the Introduction to Azure Arc. Additionally, it is important to optimize health check configurations by adjusting thresholds carefully to avoid false positives or delayed failover. Proper health check settings ensure that only healthy instances receive traffic, reducing downtime and enhancing reliability. Security is another crucial aspect of managing an NLB. Implementing AWS security best practices such as using AWS WAF (Web Application Firewall), configuring appropriate security groups, and applying IAM policies helps protect resources from unauthorized access and cyber threats. Security measures should be regularly reviewed and updated to adapt to emerging threats.
Preparing for a AWS Job Interview? Check Out Our Blog on AWS Interview Questions & Answer
Conclusion
AWS Network Load Balancer (NLB) is a powerful and scalable solution designed to efficiently handle high volumes of traffic with ultra-low latency. It ensures seamless traffic distribution across multiple EC2 instances, improving both performance and fault tolerance. By leveraging cross-zone load balancing, optimized health checks, and Auto Scaling, organizations can achieve high availability and reliability for their applications. Security is a crucial aspect of managing an NLB, and implementing AWS WAF, security groups, and IAM policies helps protect backend resources from cyber threats, as covered in the AWS Training. Additionally, monitoring health metrics with Amazon CloudWatch allows administrators to track performance and identify potential issues before they impact users. Testing failover scenarios and properly configuring network ACLs further enhances resilience and security. By following best practices such as right-sizing instances, configuring listeners correctly, and planning for redundancy across multiple Availability Zones, businesses can maximize the benefits of AWS NLB.





