
- Introduction to AWS Secrets Manager
- Why Use AWS Secrets Manager?
- Storing and Retrieving Secrets
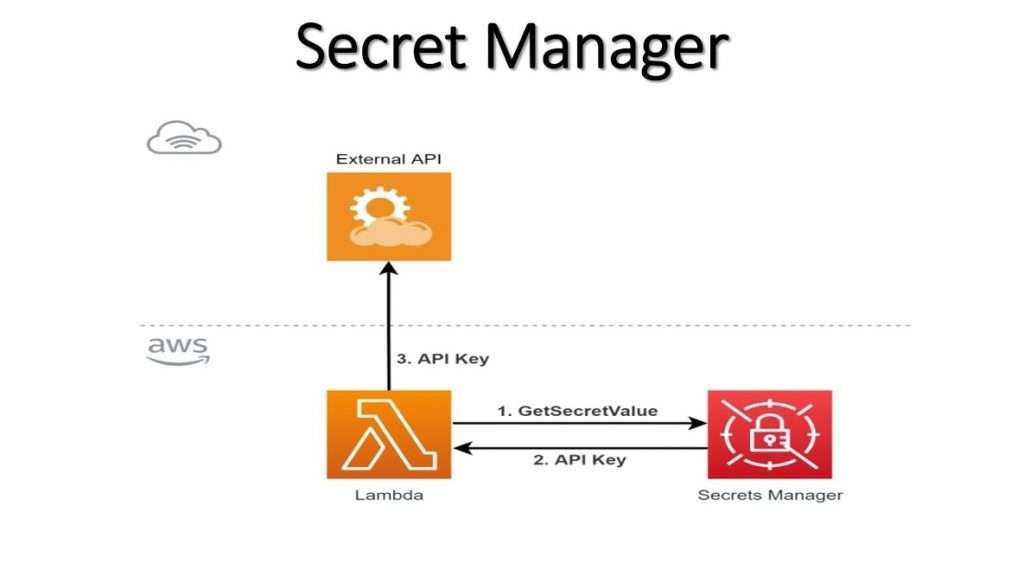
- How AWS Secrets Manager Works
- Integrating with AWS IAM and Other Services
- Security and Encryption Features
- Cost and Pricing Structure
- Best Practices for Secrets Management
- Conclusion
Introduction to AWS Secrets Manager
Modern application development and cloud computing depend on the secure management of sensitive data. This involves tracking and maintaining credentials such as database passwords, encryption keys, and API keys, all of which are necessary for applications to operate but need to be protected from unwanted access. Amazon Web Services (AWS) offers a fully managed solution called AWS Secrets Manager to assist you in safely storing, managing, and retrieving private data, including database credentials, API keys, secrets, and passwords, as covered in Amazon Web Service Training. AWS Secrets Manager provides a centralized approach to managing secrets, eliminating the need to hardcode secrets in your application code or store them in files on servers. The service is designed to streamline the management of secrets, minimize the risk of security breaches, and improve your overall security posture by allowing you to rotate, audit, and control access to secrets in a secure and automated manner. It is highly integrated with other AWS services, making it an essential tool for enterprises and developers building cloud-native applications.
Earn Your AWS Certification, Gain Insights From Leading AWS Experts And Advance Your Career With ACTE’s AWS Course Today!
Why Use AWS Secrets Manager?
AWS Secrets Manager provides several compelling reasons organizations adopt it to manage sensitive data. Here’s why you should consider using AWS Secrets Manager in your organization.
- Security and Compliance : Secrets Manager helps you securely store and manage sensitive information in compliance with security standards and best practices. It uses advanced encryption algorithms to ensure that secrets are encrypted in transit and at r st. This makes it a trusted solution for managing secrets that must comply with regulatory standards such as GDPR, HIPAA, and PCI DSS.
- Seamless Integration with AWS Services : One key advantage of AWS Secrets Manager is its integration with other AWS services, as well as its compatibility with Efficient Automation in Jenkins With Docker for streamlined CI/CD pipelines and secure secret management. Whether using Amazon RDS for your database or Amazon EC2 for hosting your applications, Secrets Manager can seamlessly integrate these services to manage database credentials and other sensitive data. Furthermore, the Secrets Manager integrates with IAM (Identity and Access Management) to control the fine-grained access to secrets.
- Automated Secrets Rotation : With AWS Secrets Manager, you can automate the rotation of secrets at regular intervals, which helps you maintain a secure environment by minimizing the risk of key compromises. For example, you can configure Secrets Manager to rotate database credentials automatically without downtime for your application. The service supports several popular applications and databases for automated rotation, such as MySQL, PostgreSQL, and Amazon RDS.
- Cost-Effective: AWS Secrets Manager is a pay-as-you-go service, so you only pay for the secrets you store and the number of requests you make to retrieve them. This model makes it affordable for organizations of all sizes, from startups to large enterprises.
- Access Control and Auditing: AWS Secrets Manager integrates with AWS IAM, enabling you to control who can access specific secrets. Additionally, the service provides detailed logging and auditing capabilities through AWS CloudTrail, allowing you to track access to secrets and monitor changes over time.
- Centralized Management: Managing secrets centrally allows for easier maintenance and better security hygiene. Secrets Manager will enable you to store multiple secrets in one location and access them programmatically or through the AWS Management Console. This centralization makes maintaining secrets across different environments easier, reducing complexity and administrative overhead.
Storing and Retrieving Secrets
In AWS Secrets Manager, secrets can be stored as key-value pairs, allowing efficient organization, such as storing a database password with “username” and “password” or an API key as a single pair. Secrets Manager provides an interface to store secrets via the AWS Management Console, AWS CLI, and SDKs, with secret values encrypted using encryption keys managed by AWS Key Management Service (KMS) to ensure high-level security. When storing a secret, Secrets Manager automatically encrypts it before saving. For example, to store a secret using the AWS CLI, you can use the command: AWS secrets manager create-secret –name MyDatabaseSecret –secret-string ‘{“username”: “admin”, “password”: “example password”}’, which creates a new secret with a JSON string containing the credentials. Retrieving secrets is also straightforward using the AWS CLI or programmatically via AWS SDKs, with Secrets Manager decrypting the secret on the fly for the requesting service, which can be seamlessly integrated with Managing Docker Containers on AWS for secure containerized application management. For example, using the AWS CLI: aws secrets manager get-secret-value –secret-id MyDatabaseSecret retrieves the secret in JSON format.
This allows applications that need sensitive credentials, such as for connecting to a database, to securely access these secrets programmatically using AWS SDKs available for multiple programming languages like Python, Java, and Node.js. In addition to providing a simple interface for storing and retrieving secrets, AWS Secrets Manager also allows you to configure automatic rotation of secrets, enhancing security by periodically updating credentials without manual intervention. This feature can be integrated with AWS Lambda functions to automatically rotate secrets for supported services, such as databases or API keys. Furthermore, Secrets Manager offers detailed access control through AWS Identity and Access Management (IAM) policies, ensuring that only authorized users or applications can access or modify specific secrets. To improve audit capabilities, AWS Secrets Manager integrates with AWS CloudTrail, enabling you to monitor and log all access and changes made to your secrets. This ensures full transparency and traceability of sensitive data management activities. Additionally, AWS Secrets Manager provides cross-region replication of secrets, allowing businesses to securely store and retrieve secrets across multiple AWS regions for high availability and disaster recovery scenarios.
Interested in Learning More About AWS? Sign Up For Our AWS Course Today!
How AWS Secrets Manager Works
AWS Secrets Manager integrates several key components and services to store, manage, and retrieve secrets securely. Here’s a breakdown of how it works.
- Encryption at Rest and in Transit : AWS Secrets Manager safeguards secrets using encryption. The service uses AWS KMS to encrypt secret values at rest, and all communication between your application and Secrets Manager is secured via HTTPS. When a secret is retrieved, it is decrypted in memory and sent back to the requesting application, ensuring that your secrets are always encrypted during transit and storage.
- Automated Secrets Rotation: With AWS Secrets Manager, as explained in AWS Training, secrets such as database credentials can be automatically rotated on a schedule to enhance security and reduce the risk of exposure. This ensures that your secrets are regularly updated and reduces the chances of a key being compromised. You can set up Lambda functions to define the process for rotating secret ts. When Secrets Manager rotates a secret, it updates the corresponding application or service with the new credentials without downtime.
- Access Control and Authentication : AWS Secrets Manager integrates with AWS IAM, allowing you to define who can access secrets and under what conditions. You can set up policies to restrict access based on roles, users, and specific conditions like the source IP address or time of day. Additionally, Secrets Manager supports fine-grained access control, which enables organizations to grant secure access to secrets based on least-privilege principles.
- Versioning and Audit Logging : Each secret stored in Secrets Manager is versioned, meaning you can track and retrieve previous versions of a secret if necessary. This versioning helps maintain historical credentials or configuration data records, which can help debug or comply with ts. Additionally, all actions related to secrets are logged in AWS CloudTrail, which provides a detailed audit trail for access and management of secrets.
Integrating with AWS IAM and Other Services
IAM also allows you to define fine-grained access controls, ensuring that only authorized entities can perform specific actions, such as creating, retrieving, or deleting secrets. By using IAM roles, you can assign permissions to AWS services or EC2 instances, allowing them to access secrets without needing hardcoded credentials, enhancing security. Additionally, IAM enables the use of Multi-Factor Authentication (MFA), which adds an extra layer of protection when accessing secrets, ensuring only authorized users with proper authentication can interact with sensitive data, a concept also explored in Mastering Docker ENTRYPOINT to define how containers should run securely. For compliance and auditing purposes, IAM integrates with AWS CloudTrail, providing logs of all actions performed on secrets, making it easier to track and review access history. Combining IAM policies with AWS Secrets Manager ensures that sensitive information is managed and accessed according to your organization’s security and compliance requirements.
Example IAM Policy for Secrets Manager Access:
- {
- “Version”: “2012-10-17”,
- “Statement”: [
- {
- “Effect”: “Allow”,
- “Action”: “secrets manager: GetSecretValue,”
- “Resource”: “arn:aws: secrets manager:us-west-2:123456789012:secret:
- MyDatabaseSecret-ABCDEF”
- }
- ]
- }
This IAM policy grants permission to retrieve the value of MyDatabaseSecret for the specified resource.
AWS Lambda
These Lambda functions can be set up to run automatically at defined intervals or in response to specific triggers, ensuring that secrets are rotated regularly without manual intervention. For instance, you can configure Lambda to rotate database credentials every 30 days or to update application configurations when secrets are modified. By automating these processes, you reduce the risk of human error, improve security by ensuring up-to-date credentials, and maintain compliance with best practices for secret management. Additionally, AWS Secrets Manager provides built-in integration with AWS Lambda to simplify the creation and management of secret rotation tasks, while also supporting AWS SWF Scalable Workflow Automation for automating and scaling complex workflows securely. This allows you to streamline operations and ensure that your applications always have access to the most current and secure secrets.
Integration with AWS RDS and Other AWS Services
This integration eliminates the need for manual credential management, reducing the risk of using outdated or compromised passwords. Secrets Manager can automatically update the credentials in your RDS or Aurora instances without downtime, providing a seamless experience for your applications. Additionally, this integration helps maintain compliance with security standards by ensuring that credentials are rotated regularly and securely, reducing the potential attack surface.
Are You Considering Pursuing a Master’s Degree in AWS? Enroll in the AWS Masters Course Today!
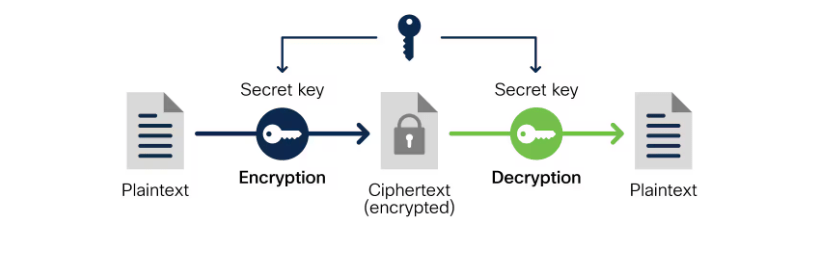
Security and Encryption Features
- End-to-End Encryption: AWS Secrets Manager uses AWS KMS to encrypt secrets while they are at rest. Although AWS offers a default KMS key, you can generate and utilize your own customer-managed KMS keys. This gives you more control over key rotation and encryption settings.
- Access Control with IAM Policies: By using IAM policies, you can define specific permissions at the resource level, such as granting access to a particular secret or allowing actions like retrieving or updating secrets only under certain conditions, all while exploring Exploring Elastic Network Interfaces in AWS to manage network connectivity and security for your resources.
- S cure Retrieval: Secrets Manager also ensures that the communication between your application and the service is encrypted using SSL/TLS, preventing unauthorized access during transmission. Additionally, the service supports automatic retries for secure retrieval in case of network interruptions, ensuring high availability and reliability. This further enhances the security of sensitive data by minimizing the risk of exposure during transit.
Cost and Pricing Structure
AWS Secrets Manager offers a pay-as-you-go pricing model, meaning you only pay for the secrets you store and the number of API calls you make. Here’s a breakdown of the pricing structure:
- Storage Costs: You pay a monthly fee for each secret stored. The pricing depends on the region where the secret is stored.
- API Calls: You pay for each API call to Secrets Manager, including calls to create, retrieve, delete, and list secrets, which can be integrated with services like AWS Neptune and Graph Databases for secure management of sensitive data in graph-based applications.
- Secrets Rotation: There may be additional costs associated with custom Lambda functions used for automatic rotation, depending on the function’s execution time.
- Data Transfer Costs: If you transfer secrets between regions or outside of AWS, there may be additional data transfer costs based on the volume of data moved.
- Secret Versions: Storing multiple versions of a secret may incur additional charges, as each version is considered a separate stored entity.
- Lambda Function Execution: Besides the cost of using Lambda for secret rotation, any compute time or resources consumed by the Lambda function will be billed separately, based on execution duration and memory usage.
Want to Learn About AWS? Explore Our AWS Interview Questions & Answer Featuring the Most Frequently Asked Questions in Job Interviews.
Best Practices for Secrets Management
To ensure the security of your application and data, consider implementing these best practices when using AWS Secrets Manager, Automate the rotation of secrets, particularly for databases and API credentials, to reduce the chances of human error and prevent the compromise of long-lived credentials. Always follow the principle of least privilege when granting access to secrets. Ensure that IAM policies restrict access to only the necessary services and users. Leverage AWS loudTrail to monitor and audit all access to secrets. This ensures you can track unauthorized access and maintain a history of who accessed what secrets, a key feature covered in AWS Training for effective security management. Take advantage of AWS KMS to control encryption and key management. Use customer-managed keys (CMKs) to maintain greater control over how secrets are encrypted and decrypted. If your application spans multiple AWS regions, consider using Secrets Manager in each area to store and retrieve secrets locally. This will improve performance and ensure high availability.
Conclusion
AWS Secrets Manager offers a complete, safe, and expandable cloud-based sensitive data management solution. Your apps and services will have access to the required credentials without sacrificing security, thanks to its safe secret storage, rotation, and retrieval capabilities. While preserving strict access control, Secrets Manager provides developers a smooth experience through integration with AWS IAM, Lambda, and other AWS services. You can ensure your secrets are managed effectively and safely by adhering to best practices and using Secrets Manager’s sophisticated security features.





