
- Introduction to the Shared Responsibility Model
- AWS Responsibilities vs. Customer Responsibilities
- Security Best Practices for AWS Customers
- Compliance and Regulatory Considerations
- Shared Responsibility Model for Different AWS Services
- Common Misconceptions and Clarifications
- Conclusion
Introduction to the Shared Responsibility Model
The Shared Responsibility Model is a foundational concept in cloud computing, particularly for services offered by Amazon Web Services (AWS). This model clearly defines the division of responsibilities between AWS and the customer to ensure the security, compliance and overall management of services in the cloud it emphasizes the critical idea that while AWS provides a secure and compliant infrastructure, customers are responsible for securing their own data, applications and usage within the AWS environment. AWS Training division helps mitigate security risks by ensuring that each party understands their role in safeguarding the cloud environment. Understanding this model is crucial not only for AWS customers but also for cloud service providers in general helps avoid security gaps reduce potential vulnerabilities and ensure that both parties fulfill their respective responsibilities. The AWS Shared Responsibility Model provides clear boundaries for who is responsible for managing which aspects of the cloud environment, such as infrastructure, data and application security.
AWS Responsibilities vs. Customer Responsibilities
In the Shared Responsibility Model the division of responsibilities is often categorized as follows:
-
AWS Responsibilities:
- Infrastructure Security: Understanding arns in AWS responsible for securing the infrastructure that supports services offered by AWS, including the physical hardware, data centers, and network architecture.
- Global Security Compliance: AWS manages the compliance of their physical infrastructure and foundational services with various certifications, such as ISO 27001, SOC 2, PCI DSS, and HIPAA.
- Hardware Security: AWS ensures the physical security of its data centers, including facility access, surveillance, and hardware management.
- Network and Hypervisor Security: AWS manages the security of the underlying network infrastructure and the hypervisor layer, which isolates and manages virtualized resources.
- Data Security: Customers are responsible for securing their own data within the AWS environment. This includes encryption of data at rest and in transit, managing access controls and implementing effective data protection measures.
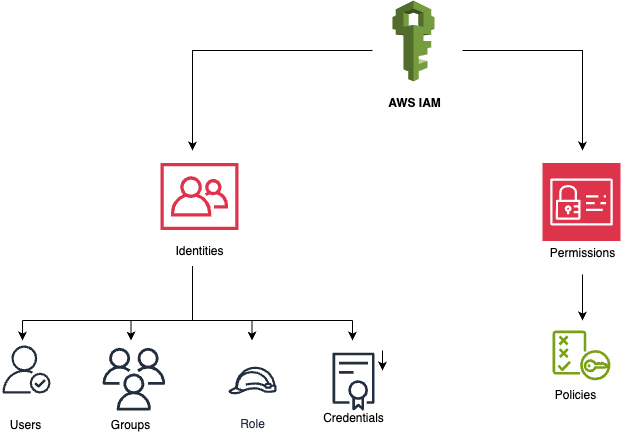
- Identity and Access Management (IAM): Customers must manage their IAM policies, roles and permissions to control who has access to their resources in AWS. This includes user authentication and authorization.
- Application Security: Customers are responsible for securing the applications they deploy on AWS, including patch management, vulnerability assessment, and ensuring their code is secure.
- Operating System and Network Configuration: Customers must manage the security settings of their operating systems, network configurations and any software they install on AWS infrastructure (such as updates and patching).
- Enable Encryption: Always use encryption for sensitive data, both at rest and in transit. AWS provides various encryption services such as AWS Key Management Service (KMS), to help you secure data. Additionally, AWS Security Token Service, RDS and EBS provide native encryption options.
- Implement Multi-Factor Authentication (MFA): Enabling MFA for user accounts especially for AWS root accounts, is essential to protect against unauthorized access. MFA requires users to provide an additional verification factor (like a one-time code) to enhance login security.
- Regularly Review IAM Policies and Permissions: Use principle of least privilege (PoLP) when granting permissions. Regularly audit and review IAM policies to ensure that users and applications only have access to the resources they absolutely need.
- Monitor and Audit Resources: Utilize AWS CloudTrail and Amazon CloudWatch to track API calls, monitor security incidents, and set up alarms for unusual activity or unauthorized access. CloudTrail provides detailed logs of AWS account activity, and CloudWatch helps you monitor your AWS resources in real-time.
- Patch Management and Vulnerability Scanning: Apply security fixes on a regular basis to your AWS-deployed OS systems and apps. To check for vulnerabilities and make sure your instances are secure use tools such as Amazon Inspector.
- Secure Networking: Use Amazon VPC Virtual Private Cloud to isolate your AWS resources and control network traffic. Implement Security Groups and Network Access Control Lists to define inbound and outbound traffic rules for your instances.
- Backups and Disaster Recovery: To guarantee business continuity test your disaster recovery plans and regularly backup your important data Make use of services like Building Scalable and Secure Microservices on AWS for centralised backup management and Amazon S3 for backup storage.
- AWS Responsibility: Securing the hypervisor, the physical hardware and network.
- Customer Responsibility: Configuring the operating system, patching software, managing network traffic (via security groups) and securing data. Amazon S3:
- AWS Responsibility: Protecting the physical infrastructure and providing access control tools.
- Customer Responsibility:Encrypting data, configuring S3 bucket policies, setting up access controls and monitoring usage.
- AWS Responsibility: Managing the database engine, operating system and infrastructure.
- Customer Responsibility: Configuring database access, encryption, backups, and database management (e.g., choosing the instance type and configuring parameter groups). AWS Lambda:
- AWS Responsibility: Managing the infrastructure and execution environment for running Lambda functions.
- Customer Responsibility: Writing secure code, ensuring proper IAM role configurations, and handling event source security.
- AWS Responsibility: Providing the underlying network infrastructure.
- Customer Responsibility: Configuring network components like subnets, route tables, NACLs and Security Groups.
- Misconception: AWS handles all aspects of security, so customers don’t need to worry about it.
- Clarification: While Azure Availability Sets vs Zones Article the infrastructure, customers are responsible for securing their own data, applications, and access controls within AWS services. Compliance is Solely AWS’s Responsibility:
- Misconception: AWS takes care of all compliance-related matters, so customers don’t need to worry about meeting regulations.
- Clarification:AWS provides compliant infrastructure, but customers must configure services to comply with specific regulations. AWS offers tools, but it’s up to customers to implement them.
- Misconception: The responsibilities for security and compliance are the same for every AWS service.
- Clarification:The responsibilities vary based on the service. For example, EC2 requires more customer involvement in managing the operating system and security than services like Lambda, which abstracts much of the underlying infrastructure. Security of the AWS Environment Guarantees Security for My Data:
- Misconception: Since Understanding AWS NAT Gateway its environment, customers don’t need to worry about securing their own data.
- Clarification: Customers are responsible for securing their own data, including encryption, access management and application-level security.
Dive into AWS by enrolling in this AWS Certification Training today.
Customer Responsibilities:By clearly defining these roles the Shared Responsibility Model ensures that both parties understand their obligations and the necessary steps to achieve a secure and compliant AWS environment.
Security Best Practices for AWS Customers
While AWS handles the security of its infrastructure, customers must implement a range of security best practices to protect their data, applications and services. Here are some key security best practices:
Learn the fundamentals of AWS with this AWS Certification Training .
Compliance and Regulatory Considerations
Compliance with industry regulations and data protection law is another key aspect of the Shared Responsibility Model. While AWS manages the compliance of its infrastructure customers are responsible for ensuring that their use of AWS services complies with relevant laws and regulations such as General Data Protection Regulation Customers using AWS to store and process personal data of EU citizens must ensure that AWS Training comply with the GDPR. AWS provides tools and features that help customers meet GDPR obligations, such as data encryption, access controls, and audit logs. Health Insurance Portability and Accountability Act (HIPAA) AWS offers services that can help customers comply with HIPAA for storing, processing and transmitting protected health information. Customers must configure AWS services in compliance with HIPAA requirements. AWS enables customers to meet PCI DSS requirements for handling cardholder data. Customers must ensure that they implement the necessary controls for securing cardholder data such as using encryption and maintaining access log. AWS undergoes regular SOC 2 and SOC 3 audits to ensure that it maintains controls related to security, availability, processing integrity, confidentiality and privacy. However, customers must also follow best practices to ensure their applications meet compliance requirements. Data Residency and Local Regulations Depending on the region AWS customers must consider local data residency requirements. AWS provides a variety of regions around the world allowing customers to choose where their data is stored and processed to comply with local laws.
Shared Responsibility Model for Different AWS Services
The division of responsibility may vary slightly depending on the AWS service in use. Here’s how the responsibility model applies to some common AWS services:
Amazon EC2:Take charge of your AWS career by enrolling in ACTE’s AWS Master Training Course today!
Amazon RDS: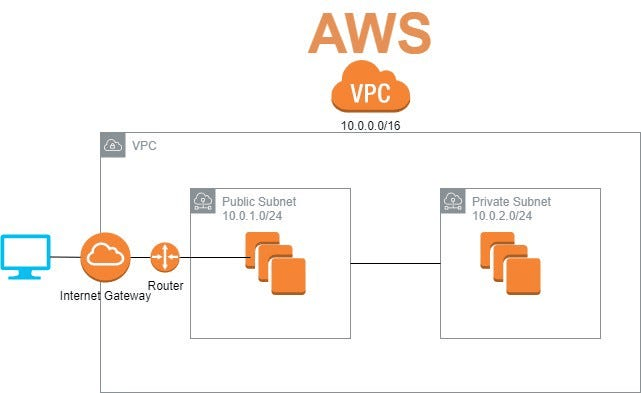
By understanding how the shared responsibility model applies to different services customers can ensure that they meet their security and compliance obligations effectively.
Common Misconceptions and Clarifications
There are several common misconceptions about the AWS Shared Responsibility Model. Here are some clarifications:
AWS is Fully Responsible for Security:Want to ace your AWS interview? Read our blog on AWS Interview Questions and Answers now!
The Shared Responsibility Model is the Same for All AWS Services:Understanding the Shared Responsibility Model is essential for customers to effectively manage their AWS workloads, ensure compliance with regulations and implement proper security controls by understanding both AWS’s responsibilities and their own, customers can build and operate secure, compliant and efficient systems in the cloud.
Conclusion
In conclusion, the AWS Shared Responsibility Model plays a pivotal role in clarifying the division of security and compliance tasks between AWS and its customers. While AWS takes responsibility for securing the underlying infrastructure, including the physical hardware, network, and foundational services, customers are tasked with securing their own data, applications, and access controls within the cloud environment. AWS Training distinction of responsibilities is essential for organizations to manage security effectively, mitigate potential vulnerabilities, and ensure compliance with industry regulations. By fully understanding the scope of these responsibilities, organizations can develop robust security strategies, proactively address risks and implement the necessary controls to safeguard their resources customers should adopt best practices such as encryption for data protection, strong access controls to restrict unauthorized access and conduct regular audit to monitor potential vulnerabilities and track compliance.





