
- Introduction to GCP Security
- Key Security Features in GCP
- Identity and Access Management (IAM) in GCP
- Network Security in GCP
- Data Protection in GCP
- Best Practices for GCP Security
- Conclusion
Google Cloud Platform (GCP) offers robust security features to protect data, applications, and infrastructure. Key features include Identity and Access Management (IAM) for granular control over user permissions, encryption at rest and in transit, and the Google Cloud Security Command Center for threat detection also provides Virtual Private Cloud (VPC) for secure networking and Cloud Armor for DDoS protection. Security logging and monitoring are integrated Google Cloud Platform with Cloud Audit Logs and Cloud Monitoring. Best practices include regularly reviewing IAM roles and permissions, using multi-factor authentication (MFA), and enabling encryption for sensitive data. Implementing least-privilege access, securing APIs, and conducting vulnerability assessments help maintain a secure environment. Additionally, automating security updates and adopting a shared responsibility model ensures strong defenses against evolving threats.
Enhance your knowledge in Google Cloud. Join this Google Cloud Training now.
Introduction to GCP Security
Google Cloud Platform (GCP) offers a suite of robust security features designed to protect your cloud resources, applications, and data. Security in GCP is built with the principle of defense in depth, ensuring that multiple layers of protection are in place to secure both cloud infrastructure and sensitive information. These layers range from the physical security of data centers, to encryption for data both at rest and in transit, and comprehensive identity and access management (IAM) tools. GCP ensures that security is integrated into the platform from the ground up, offering organizations a wide range of tools to manage, monitor, and protect their cloud resources while meeting critical compliance and regulatory requirements. One of the key strengths of Understanding AWS Data Pipeline strong focus on security and privacy, leveraging Google’s vast global infrastructure and decades of expertise in managing sensitive data. The platform adheres to rigorous industry standards and certifications such as ISO 27001, SOC 2, SOC 3, and GDPR, providing enterprises with assurance in its security practices and commitment to safeguarding data. With constant updates, audits, and innovation, GCP is dedicated to staying ahead of emerging threats, giving businesses confidence that their data is secure, protected, and compliant within the cloud environment.
Key Security Features in GCP
- Encryption by Default: GCP automatically encrypts all data at rest and in transit. This ensures that your data is protected without requiring additional setup or configurations. The encryption keys are managed by Google or can be managed by the user using Cloud Key Management Service (KMS).
- Virtual Private Cloud (VPC): GCP’s VPC allows users to configure isolated virtual networks, control traffic flows, and apply network security policies. The VPC’s robust features support private IP address ranges, VPN connections, and inter-region connectivity, which ensures network isolation and security.
- Security Command Center: This tool allows users to gain visibility into the security state of their GCP environment. It provides real-time alerts, identifies vulnerabilities, and offers recommendations to improve security across projects and resources.
- Cloud Armor: This service offers DDoS protection and web application firewall (WAF) features. Google Cloud Armor helps protect against malicious traffic by filtering and blocking unwanted requests before they reach your applications.
- Audit Logs: GCP provides Cloud Audit Logs that track user activities and API calls. These logs offer a detailed record of what actions have been performed, by whom, and when, helping organizations monitor and investigate Guide to Cloud Security.
- AI and Machine Learning Security: GCP integrates machine learning models to detect unusual activities, potential threats, and anomalies in data. These tools, such as Google Cloud Security Command Center, help organizations proactively identify risks.
- Virtual Private Cloud (VPC): GCP VPC is a customizable, private network within the Google Cloud environment. With VPC, users can define subnets, set up firewall rules, and control traffic between instances. The VPC allows users to create isolated environments for their applications while still enabling connectivity to other GCP services. Additionally, VPC provides granular control over network traffic and resource isolation, making it easier to maintain security boundaries.
- Firewall Rules: GCP enables users to configure firewall rules to control incoming and outgoing traffic to instances in their VPC. These rules can be defined based on IP ranges, ports, and protocols, and are highly customizable to match specific network security requirements. Users can also apply these rules to specific instances, ensuring tailored security measures for each resource.
- Cloud VPN and Interconnect: GCP provides Cloud VPN to securely connect on-premises networks to Google Cloud. This service establishes an encrypted tunnel between a private network and the cloud. Additionally, Azure Boards With Devops offers high-bandwidth and low-latency connectivity between on-premises data centers and Google’s network. These solutions provide secure, high-performance connections that are essential for hybrid cloud deployments.
- Cloud Load Balancing: Google’s Cloud Load Balancing distributes incoming traffic to virtual machines based on traffic demand. It ensures optimal resource utilization and provides built-in DDoS protection. It also allows for automatic failover in case of server failure, ensuring high availability. This service is designed for scalability, automatically adjusting to accommodate changes in traffic load.
- Private Google Access: Private Google Access allows instances in a VPC to access Google services (such as GCS, BigQuery) without routing traffic over the public internet. This enhances security by preventing data from traversing public networks. It also improves performance by reducing the risk of network bottlenecks or latency issues due to external traffic.
- Cloud Armor: Google Cloud Armor provides protection against Distributed Denial-of-Service (DDoS) attacks. It uses Google’s global infrastructure to absorb large-scale attacks and ensures high availability for critical services. Cloud Armor also includes customizable security policies, enabling users to define their specific attack mitigation strategies.
- Use IAM to Enforce Least Privilege: Always apply the principle of least privilege by granting the minimum permissions necessary to users and service accounts. Regularly review and audit IAM roles to ensure proper access control.
- Regularly Monitor and Audit Logs: Enable logging through Cloud Audit Logs and use tools like Cloud Security Command Center to monitor security-related events and incidents in real time. Regularly review logs for unusual activities and potential vulnerabilities.
- Encrypt Data: Ensure that sensitive data is encrypted at Integrating Power BI with Azure , both at rest and in transit. Use GCP’s built-in encryption capabilities and consider managing your own encryption keys if additional control is required.
- Implement Multi-Factor Authentication (MFA): Enable Multi-Factor Authentication (MFA) for all users to add an additional layer of security when accessing GCP resources.
- Use Network Segmentation: Implement VPC to create isolated network environments for different applications and services. Use firewall rules and private access options to control and secure traffic.
- Automate Security Management: Leverage tools like Google Cloud Security Command Center, Cloud Identity-Aware Proxy, and Cloud DLP to automate security assessments, identify risks, and protect against potential threats.
- Implement Backup and Disaster Recovery: Regularly back up critical data and configurations using GCP’s backup services. Implement a disaster recovery plan to ensure business continuity in case of data loss or service outages.
Master Google Cloud skills by enrolling in this Google Cloud Training today.
Identity and Access Management (IAM) in GCP
Identity and Access Management (IAM) in GCP enables administrators to control access to cloud resources by defining roles and permissions, ensuring that only authorized users or services can access sensitive data or perform critical actions. IAM is crucial for enforcing the principle of least privilege. It operates based on three core components: Identity, which includes users, service accounts, groups, or applications that require access to GCP resources; Roles, which define a collection of permissions granting access to specific resources, and come in three types: predefined roles (Google-managed), custom roles (user-defined), and basic roles (Owner, Editor, Viewer); and Policies, which determine who can access which resources and under what conditions, by attaching policies to resources to control access. Additionally, Google Cloud Platform includes Resource Hierarchy, which allows permissions to be granted at the organization, folder, project, or resource level, providing granular control over access. With IAM, administrators can ensure the security of GCP environments while maintaining flexibility and scalability. Properly managing roles and policies is essential to minimizing risks and ensuring compliance.
Want to lead in Cloud Computing? Enroll in ACTE’s Cloud Computing Master Program Training Course and start your journey today!
Network Security in GCP:
GCP provides several features to ensure network security, enabling organizations to safeguard their applications from malicious traffic, data breaches, and unauthorized access:
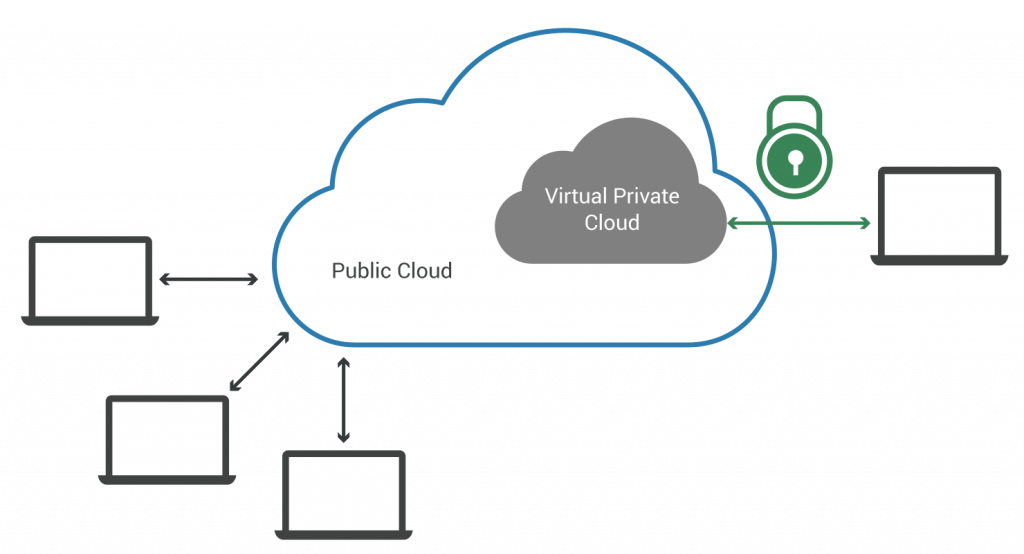
Data Protection in GCP
Data protection in GCP focuses on ensuring the confidentiality, integrity, and availability of data across the platform. GCP uses a variety of tools and services to achieve robust data protection. By default, GCP automatically encrypts data both in transit and at rest, with the option for users to manage their own encryption keys through Cloud Key Management Service (KMS). Additionally, Google Cloud Data Loss Prevention (DLP) allows users to Azure arc Explained , classify, and redact sensitive information, such as personally identifiable information (PII), ensuring compliance with regulations like GDPR and HIPAA. For backup and recovery, GCP offers services like Cloud Storage and Cloud Spanner, enabling organizations to implement effective strategies with data replication across multiple locations for resilience against hardware failure.
Google’s Cloud HSM provides a dedicated physical device for securely storing and managing cryptographic keys, enhancing key management security. Furthermore, GCP complies with various industry standards and regulations, such as GDPR, HIPAA, PCI DSS, and ISO/IEC 27001, offering Compliance Reports to help organizations meet their regulatory obligations. GCP’s robust data protection mechanisms provide peace of mind to organizations by ensuring that sensitive data is always secure and readily available. With a focus on encryption, DLP, and compliance, GCP enables businesses to confidently meet privacy requirements. These features ensure that enterprises can operate in a secure cloud environment while maintaining regulatory adherence.
Preparing for a job interview? Explore our blog on Cloud Computing Interview Questions and Answers!
Best Practices for GCP Security:
To maximize security in GCP, organizations should follow best practices that include the following:
By following these practices, organizations can strengthen their GCP security posture, protect their applications and data, and ensure compliance with industry regulations.
Conclusion:
In conclusion, Google Cloud Platform (GCP) provides a comprehensive suite of security features designed to protect data, applications, and infrastructure. From encryption and IAM to network security and compliance tools, GCP empowers organizations to secure their cloud environments with a multi-layered approach. By adhering to best practices, such as enforcing least privilege, enabling multi-factor authentication, and implementing robust backup strategies, businesses can significantly reduce security risks. With its built-in tools and continuous focus on privacy and protection, Google Cloud Platform enables enterprises to meet compliance requirements while safeguarding their sensitive data and applications in the cloud. By leveraging GCP’s security offerings, organizations can confidently embrace the cloud while maintaining a strong security posture. As cloud adoption continues to grow, ensuring a secure environment on GCP will be critical in protecting against evolving threats. GCP’s innovative security features are designed to stay ahead of emerging risks, offering businesses the flexibility to scale securely. Ultimately, GCP’s integrated security tools give organizations peace of mind as they operate in the cloud.





