
- What is Azure?
- Azure Network Security Group: What is it
- Azure Network Security – How it works?
- How do you create a Network Security Group in Azure?
- Azure Network Security Group Rules
- Azure Network Security Group Best Practices
- Conclusion
What is Azure?
Azure is a cloud computing platform and an internet portal that allows you to apply and organize Microsoft’s cloud offerings and sources. Those offerings and sources include gathering and transforming your information based entirely on your needs. All you need to access those sources and offerings is an active net connection and the ability to connect to the Azure portal. Microsoft Azure is a cloud computing platform and carrier offered by Microsoft, offering a wide range of cloud-based solutions, including computing, storage,Azure Administrator Networking, databases, artificial intelligence, and security. Azure allows organizations to develop, deploy, and manage applications across multiple cloud environments, including public, private, and hybrid clouds. It supports many programming languages, frameworks, and tools, thus becoming a flexible choice for businesses and developers. It has a global network of data centers to ensure excessive availability, scalability, and security to users. Its pay-as-you-cross pricing model allows companies to control prices even while taking advantage of efficient cloud capabilities. Azure is widely employed across industries for internet applications, information analytics, device learning, and organization IT infrastructure.
Did you recognize that Microsoft Azure and other public clouds transform how agencies deploy and stabilize assigned offerings?
The reason is to instantly connect clients or apps from anywhere within the globe to your carrier, providing them with a scalable and reasonably available digital networking infrastructure. These networks are the first line of defense against attacks, and they should best be assigned visitors from specially accepted users, programs, or protocols. Keeping those networks stable might be challenging, but it’s essential.
Azure Network Security Group: What is it?
An Azure community security organization is not more than a set of get admission to manage rules that may be utilized to stabilize a subnet or a virtual community; such rules examine incoming and outgoing visitors to determine whether or not to accept or reject a package. The VM-stage Network safety organization and the subnet-stage Network safety organization are the two levels that constitute Azure community safety.
Microsoft’s controlled solution, Azure Network Security Groups, allows the filtering of site visitors to and from Azure VNet. Any broad range of safety guidelines that constitute the Cloud Architect Azure NSG can be turned on or off by users.A five-tuple hash is used to evaluate those guidelines` effectiveness.The 5-tuple hash uses the vacation spot IP to cope with port-wide variety, supply port-wide variety, IP addresses, and different factors.You can quickly hyperlink Network Security Groups with a VNet or VM community interface to its OSI layer three and layer four functionality.
Azure Network Security Groups (NSGs) provide fine-grained control over network traffic, enabling users to define inbound and outbound rules based on specific conditions. These rules can be applied to virtual machines (VMs), subnets, or network interfaces, enhancing the security of the network architecture. NSGs MicroSoft Azure Training also support both allow and deny rules, which gives flexibility in controlling access to resources. In addition, the rules can be prioritized using rule numbers, allowing more granular control over traffic filtering. The integration with Azure’s monitoring and logging capabilities ensures that network activity can be tracked and analyzed, helping to detect potential security threats and ensure compliance with organizational security policies.
Are You Interested in Learning More About MicroSoft Azure? Sign Up For Our AWS Online Training Today!
Azure Network Security-How it works?
- An excellent choice for protecting digital networks is Microsoft’s Azure Network Security Group (NSG).
- Through this software, community managers can rapidly organize, filter, route, and alter outstanding community visitors’ streams.
- When building Azure NSG, you could set many incoming and outgoing policies to permit or prohibit specific types of visitors.
- If you must use Azure Network Security Groups, you should build and set up man or woman policies.
- Several Azure services` properties may be guarded within an Azure digital community.
- The entire listing is available underneath Services, which can be located in a digital community.
- There could be zero or a single Azure Data Engineer community safety institution designed for each digital community subnet and community interface on a digital machine.
- Any number of subnets and community interfaces could be attached to the same equal community safety institution.
- NSGs allow you to apply different security rules to different network segments, enabling segmentation and isolation of resources within your virtual network.
- You can use NSG flow logs to track network traffic and analyze the effectiveness of your security rules, providing insights for further refinement.
- Azure NSGs support integration with Azure Firewall and other security solutions to enhance the overall network security posture and provide advanced protection features.
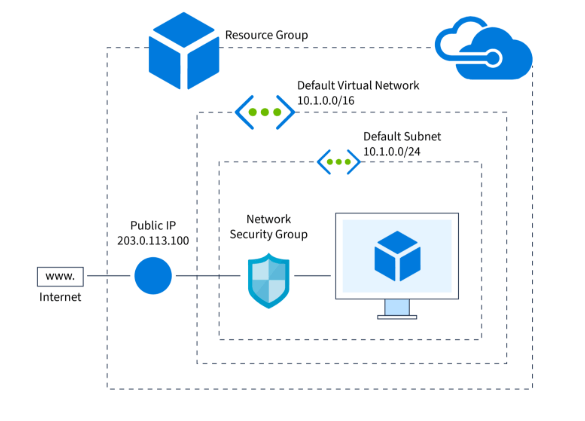
How do you create a Network Security Group in Azure?
At the top of the Azure interface. You may also select Create an aid from the Home web page. Next, select Networking. Then, select the Network safety institution from the dropdown menu. Input values for the following options in the basic tab of the Create Network Security Group web page by selecting Review + Create. Choose the Create option after noticing that the message has passed validation. For every Azure region and subscription, a set of positive community safety companies can be created. You can obtain extra information from Azure subscription and provider constraints, limits, and policies. Once you create the Network Security Group (NSG), Azure Data Factory you can start adding inbound and outbound security rules to control traffic flow. You can associate the NSG with subnets or network interfaces within your virtual network to enforce the defined policies. Azure provides an option to manage NSG rules through the Azure portal, PowerShell, or Azure CLI, offering flexibility in configuration.
To ensure security compliance, it’s essential to monitor the effectiveness of the rules using Azure Monitor and Network Watcher. Regular auditing and testing of NSG rules help maintain a secure network environment and prevent unauthorized access. Additionally, you can use tags to help organize and manage your NSGs across different environments or subscriptions. NSGs can be configured to integrate with other Azure security services, such as Azure Firewall, for enhanced protection. Finally, implementing automated rule updates and applying NSGs to new resources through templates or Azure DevOps pipelines can streamline ongoing security management.
To Earn Your End to End Encryption Certification, Gain Insights From Leading End to End Encryption Experts And Advance Your Career With ACTE’s MicroSoft Azure Online Training Today!
Azure Network Security Group Rules
- Allow Vnet InBound—This policy permits all hosts within the digital community (e.g., subnets) to communicate without being hindered. Allow Azure LoadBalancer InBound – This rule permits an Azure load balancer to communicate with each other and your virtual device and transmit heartbeats.
- Deny All InBound – This is the deny-all rule, which, with the help of default, blocks all the inbound traffic to the VM and secures it from malicious access outside the Azure Vnet (logging degree) is obtainable inside the Azure community observer for NSGs. Logs are uploaded to the garage server you certain some time of use.
- Allow VirtualNetwork InBound – This rule permits traffic from resources within the same virtual network to pass through the NSG, ensuring communication between Azure Cosmos DB VMs and other resources within the same VNet.
- Allow Internet OutBound – This rule enables outbound traffic from the virtual machine to the internet, allowing the VM to access external resources or services on the internet while keeping it secure from incoming threats.
- Deny All OutBound – This rule blocks all outbound traffic from the virtual machine, restricting access to the internet or other external resources, useful for scenarios where outgoing traffic must be tightly controlled.
- Allow AzureServiceInBound – This rule allows Azure services to communicate with resources in the virtual network, which can be essential for services such as Azure Backup or Azure Monitoring.
- Custom Rules – In addition to predefined rules, Azure NSGs also allow the creation of custom inbound and outbound rules based on specific IP addresses, port ranges, and protocols to meet unique security requirements.
Looking to Master Cloud Computing? Discover the Cloud Computing Master Program Available at ACTE Now!
Azure Network Security Group Best Practices
NSG Flow Logging: A feature called flow logging is available once flow logging is enabled for a network interface. The flow log’s data is presented in JSON format, with the results showing traffic for both incoming and outgoing data on a per-rule basis.
NSG Rule Priority: Prioritizing NSG policies is crucial for Microsoft Azure Course network security. Each rule is added incrementally, with NSG policies applied in a priority range from 100 to 4097. At the micro level, policies are evaluated, and additional rules are added as necessary. If multiple policies overlap, it’s important to review the impact.
Naming convention: Having a consistent naming convention from the beginning can streamline management, whether or not it seems trivial. Each rule’s invocation should align with MicroSoft Azure Course NSG best practices, such as naming rules meaningfully(e.g.,”WebServerProduction-to-DatabaseProduction-SQLConnection” vs. generic names like “Rule36-SQL”). When deploying rules, think about parameters: do you know the rule’s requirements? Consider using IP ranges instead of sequential IP addresses (e.g., 182.164.1.0/26 instead of individual addresses). Similarly, using port ranges like 70-72 rather than listening ports individually (70,71,72) can reduce the scope of NSG rules.
One National Security Group to rule them all: In most cases, you can apply one NSG across multiple NICs, Subnets, or VNets, avoiding the need for a separate NSG for each subnet. An NSG can have up to 1000 rules, with a default of 100 policies, and it’s crucial to avoid exceeding this threshold.
Want to Learn About Microsoft Azure? Explore Our Microsoft Azure Interview Questions And Answers Featuring the Most Frequently Asked Questions in Job Interviews.
Conclusion
Azure network security groups are well known for helping you control network security faster and better. Service tags and application security groups can help, even though initially setting them up could appear time-consuming. IntegratTo help secure and protect your Microsoft cloud infrastructure, make NSG planning and administration into your regular Azure working procedures in the future to assist with security and safeguarding. Azure Network Security Groups (NSGs) are essential security features that control incoming and outgoing community traffic to and from Azure assets. They function as firewalls online by establishing rules that allow or reject site visitors mostly based completely on factors like supply and destination IP addresses, ports, and protocols.
NSGs are commonly installed in subnets and network interfaces (NICs) of virtual machines (VMs) to enhance security and restrict unauthorized entry. They facilitate every stateful inspection, ensuring responses to permitted site visitors are mechanically authorized and priority-based complete rule evaluation, where lower-numbered policies have precedence. NSGs aid organizations in enforcing stringent protection policies, protecting workloads against cyber assaults, and ensuring compliance with business standards. Continuous monitoring and NSG policy updates are crucial to maintaining a consistent and green Azure community infrastructure.





