
- Introduction to AWS SSO
- Setting Up and Configuring AWS SSO
- Integrating AWS SSO with Active Directory
- Managing Users and Permissions
- AWS SSO Best Practices for Enterprise Security
- Troubleshooting AWS SSO Issues
- In conclusion
Introduction to AWS SSO
AWS Single Sign-On (SSO) is a cloud-based service that enables businesses to manage access to multiple AWS accounts and business applications from a centralized location. With AWS SSO, users can access all their applications and AWS resources with a single set of credentials, making AWS Training to manage identity and authentication across the organization. AWS SSO supports integration with various identity providers, including Microsoft Active Directory and third-party identity providers that support SAML 2.0, which makes it an ideal choice for organizations looking to simplify their identity management process. It provides an efficient way to control who has access to AWS resources, significantly improving security and user management.
Setting Up and Configuring AWS SSO
Setting up AWS SSO involves several steps, from enabling the service in the AWS Management Console to configuring user access to AWS accounts and applications.
Enable AWS SSO:
- First, go to the AWS SSO section in the AWS Management Console and enable the service for your organization.
- Once enabled, you can manage AWS SSO settings and configure linked identity sources.
Configure Identity Sources:
- AWS SSO allows you to configure multiple identity sources, including:
- AWS SSO as the identity store: Store user data directly in AWS SSO.
- Active Directory (AD): Integrate AWS SSO with your existing Active Directory instance.
- External Identity Providers: You can also use third-party identity providers that support SAML 2.0 for authentication.
Set Up Permission Sets:
- Once the identity store is configured, the next step is creating Permission Sets that define the permissions for users across different Security Challenges in Cloud Computing. A permission set is essentially a collection of policies that control what a user can access.
Assign Access to Users:
- After defining permission sets, you can assign users and groups to AWS accounts and applications. This simplifies managing access control, allowing you to easily grant or revoke permissions as needed.
Dive into AWS by enrolling in this AWS Certification Training today.
Integrating AWS SSO with Active Directory
AWS SSO can be integrated with Active Directory (AD) to provide a seamless experience for organizations already using AD for managing their user identities. This integration allows you to use your existing Active Directory to authenticate users for AWS resources. To integrate with Active Directory, AWS SSO supports AD Connector, which acts as a bridge between AWS SSO and your on-premises Active Directory. During setup, you need to configure the AD Connector settings, such as the domain name and credentials, to establish a connection between AWS SSO and your Active Directory. Once integrated, users and groups from Active Directory are automatically available in AWS SSO. You can then assign permission sets and AWS resources to these AD users and groups, allowing them to access AWS resources using their AD credentials. Overview of AWS Transcribe will sync with AD periodically to ensure that any changes in Active Directory, such as new users or updated group memberships, are reflected in AWS SSO automatically.
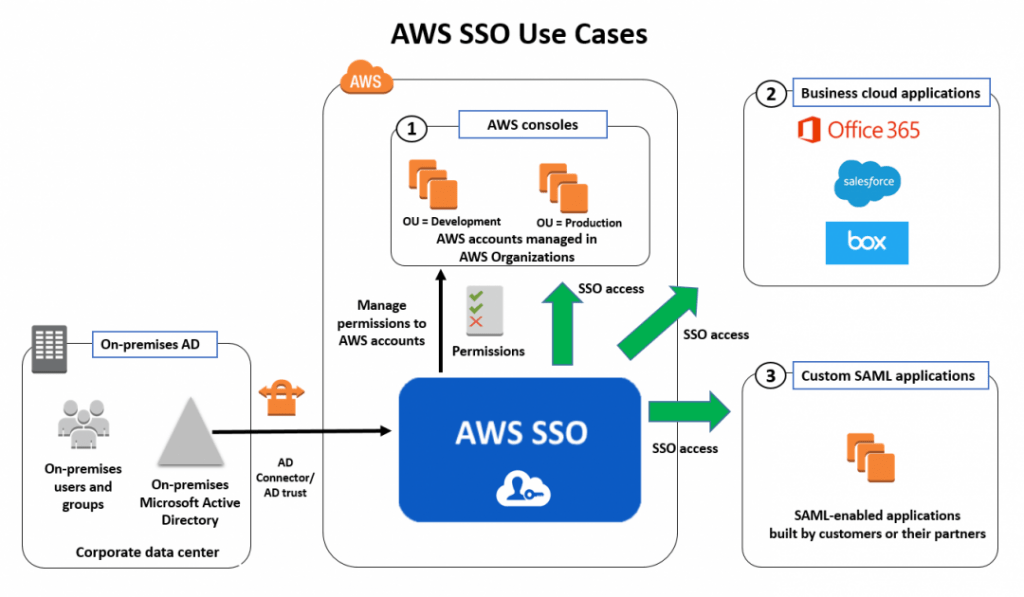
After integration, users can log into AWS and associated applications using their AD credentials. This ensures a smooth experience for users without the need to manage separate login credentials for AWS and Active Directory. Additionally, organizations can leverage AD’s existing security policies, such as multi-factor authentication (MFA), to further enhance the security of AWS access. This integration helps maintain consistency across on-premises and cloud environments, reducing the administrative overhead of managing separate identity systems. By using Active Directory as the central authentication source, businesses can enforce standardized access control and simplify user provisioning and deprovisioning. Furthermore, AD integration with AWS SSO helps streamline compliance management by aligning with existing enterprise security and governance frameworks.
Learn the fundamentals of AWS with this AWS Certification Training .
Managing Users and Permissions
With AWS SSO, you can efficiently manage users, roles, and permissions across your AWS environment. This includes defining who can access AWS resources, what actions they can perform, and which applications they can use.
- Creating Users and Groups: In AWS SSO, users can be manually added, or automatically imported from Active Directory or other identity sources. After adding users, you can group them based on roles or responsibilities, making it easier to manage permissions.
- Assigning Permission Sets: Permission sets in AWS SSO allow you to define specific permissions for users. These permissions are then applied to AWS accounts or business applications. You can create permission sets for different roles (e.g., Admin, Developer, Read-Only), and assign them to users or groups to control access.
- Managing Access to AWS Accounts and Applications: After defining user groups and permission sets, you can assign access to AWS accounts and cloud-based applications. For example, you can provide developers with access to specific AWS resources, while restricting other users from accessing sensitive data.
- Audit and Monitor User Activity: AWS SSO integrates with AWS CloudTrail, allowing you to monitor and audit user activity. This helps to ensure compliance and track access to AWS resources.
- Automated User Provisioning: Understanding Google Cloud Platform can be integrated with identity providers such as Active Directory or other external sources to automate the user provisioning process. This reduces manual administrative tasks and ensures that user accounts are created and updated in real time based on changes in the source directory.
- Granular Access Control: By leveraging fine-grained permission sets, you can enforce more precise access controls for different job functions. This ensures that users only have the minimum permissions required to perform their tasks, reducing the risk of unauthorized access.
- Multi-Factor Authentication (MFA): AWS SSO supports MFA, adding an extra layer of security. By requiring users to authenticate with a second factor (e.g., mobile device or hardware token), organizations can protect access to sensitive AWS resources and ensure stronger user verification.
- User Lifecycle Management: AWS SSO simplifies user lifecycle management, including onboarding, role changes, and offboarding. When a user leaves the organization, their access can be easily revoked by disabling their account or removing them from user groups, ensuring that they no longer have access to AWS resources.
- Customizing User Experiences: AWS SSO allows organizations to customize the user login portal with their branding. This personalized experience ensures that employees are presented with a familiar interface while accessing AWS accounts, applications, and other resources, improving user satisfaction and adoption rates.
AWS SSO Best Practices for Enterprise Security
AWS SSO offers many security features that help enterprises maintain a high level of security while managing access to AWS accounts and applications. To enhance the security of your AWS SSO deployment, it is crucial to implement best practices. First, enable Multi-Factor Authentication (MFA) for all users to add an extra layer of security. Ensuring that even if an attacker compromises a user’s credentials, AWS Training cannot access the account without the second factor. Next, implement Role-Based Access Control (RBAC) to restrict user permissions based on their role within the organization, minimizing the risk of unauthorized access. Additionally, follow the principle of least privilege, granting users and groups only the permissions necessary for their job functions. Regularly review and audit user access to ensure permissions remain appropriate and adjust them for users whose roles have changed or no longer require certain accesses. Lastly, leverage Attribute-Based Access Control (ABAC) to manage permissions based on user attributes such as department or team, providing finer-grained control over access to resources. By adhering to these best practices, enterprises can significantly reduce their exposure to security threats while ensuring compliance and operational efficiency.
Take charge of your AWS career by enrolling in ACTE’s AWS Master Training Course today!
Troubleshooting AWS SSO Issues
While AWS SSO simplifies identity and access management, issues can arise during configuration or while managing users and permissions. Below are common troubleshooting steps to resolve AWS SSO issues:
Authentication Failures:
- Check IAM Roles and Policies: Ensure that the appropriate IAM roles and policies are assigned to users and groups in AWS SSO, and that users are permitted to access the resources they need.
- Review Identity Source Configuration: If you are using Active Directory or an external identity provider, verify that the connection is correctly configured, and check for any synchronization issues.
Permission Issues:
- Review Permission Sets: Ensure that the correct permission sets are assigned to users. If a user cannot access a particular AWS resource, verify that their permission set includes the required permissions.
- Check Account Assignments: Make sure that the user is Understanding Docker to the correct AWS account or application with the proper permissions.
Preparing for Cloud Computing interviews? Visit our blog for the bestAWS Interview Questions and Answers!
Access Denied Errors:
- Configuration: Check the AWS SSO configuration to ensure that users are properly assigned to the appropriate AWS accounts and applications.
- Check Role Mappings: If using a third-party identity provider, ensure that the roles are mapped correctly to users in AWS SSO.
Service Limits and API Errors:
- AWS SSO has service limits for the number of users, groups, and permission sets that can be created. If you hit any limits, review the AWS documentation and request increases if necessary.
Troubleshoot Network and Connectivity Issues:
- If users are unable to access the Unlocking Scalability with Cloud Native Tech or applications, verify that there are no network issues, such as DNS or proxy problems, preventing communication between AWS SSO and the identity provider.
In conclusion
AWS SSO also enables seamless user experience with Single Sign-On (SSO) functionality, allowing users to access multiple applications with a single set of credentials. Additionally, it provides centralized user management, simplifying the process of granting and revoking access across all integrated AWS services and third-party applications. By integrating with AWS Identity and Access Management (IAM), AWS SSO enhances security through fine-grained access controls and user role assignment. Monitoring and auditing features help organizations track access and maintain compliance with regulatory requirements. Overall, AWS SSO improves operational efficiency and enhances security posture for enterprises leveraging cloud technologies. AWS SSO also supports multi-factor authentication (MFA), further enhancing the security of user logins and access to sensitive data. AWS Training integrates seamlessly with Active Directory, allowing organizations to leverage their existing identity management systems for authentication. The solution is highly scalable, enabling enterprises to manage user access across a wide range of cloud and on-premises applications. AWS SSO’s user-friendly interface simplifies access management for administrators, reducing administrative overhead. With support for customizable user permission sets, AWS SSO ensures that users only have access to the resources they need, aligning with the principle of least privilege.





