
- Introduction to AWS IAM
- Why AWS IAM is Essential for Cloud Security
- How AWS IAM Works
- Key Components of AWS IAM
- Setting Up AWS IAM
- IAM and Multi-Factor Authentication (MFA)
- AWS IAM Best Practices for Security
- Conclusion
Excited to Achieve Your AWS Certification? View The AWS Course Offered By ACTE Right Now!
Introduction to AWS IAM
Amazon Web Services (AWS) provides a comprehensive suite of cloud services, allowing organizations to scale and manage infrastructure without needing physical hardware. A crucial aspect of managing this cloud infrastructure securely is controlling who can access AWS resources. AWS Identity and Access Management (IAM) is the service that enables you to manage users, roles, and permissions to control access to resources securely. IAM offers granular control, allowing organizations to define permissions at a very detailed level. This ensures that users or systems only have access to the resources necessary for their function. With IAM, you can ensure compliance with security best practices, mitigate risks, and manage access rights efficiently. Enrolling in Amzon Web Services Training helps professionals gain expertise in IAM and cloud security management.
Why AWS IAM is Essential for Cloud Security
The primary purpose of AWS IAM is to ensure that only authorized users and services can access specific resources. Cloud environments like AWS, with their dynamic scalability, require highly flexible access controls. Without an efficient identity management system, there is a risk of unauthorized access, data breaches, and potential misuse of resources. AWS IAM allows administrators to define fine-grained permissions, ensuring that users and applications only have access to the resources necessary for their tasks. By implementing the principle of IAM least privilege, organizations can minimize security risks by restricting unnecessary access. IAM policies, roles, and groups help structure permissions in a way that enhances security while maintaining operational efficiency. Multi-Factor Authentication (MFA) further strengthens security by adding an additional layer of verification. Enforcing strong password policies and rotating IAM access keys regularly helps protect credentials from being compromised. Following a guide for AWS Security certification ensures best practices in credential management and cloud security.
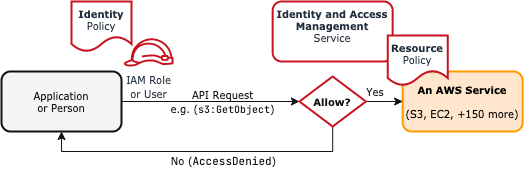
IAM also integrates with AWS CloudTrail to log user activities, enabling real-time monitoring and auditing of access patterns. By leveraging IAM Role Trust Policy effectively, organizations can secure their cloud infrastructure, protect sensitive data, and ensure compliance with security best practices. A well-implemented IAM strategy is crucial for maintaining a secure and resilient cloud environment. IAM helps in Creating unique permissions for users, services, and applications. You can specify who can do what on which resources within your AWS environment. Many industries have strict regulations about access controls and auditing; IAM ensures these can be easily managed.
How AWS IAM Works
IAM operates on users, groups, roles, and permissions. At its core, IAM enables you to create identities (users and roles) and assign permissions that specify what resources those identities can access. This system allows administrators to implement the principle of IAM least privilege (PoLP), ensuring that users and systems only have the minimum permissions necessary to perform their tasks. Enrolling in AWS Training helps professionals master IAM best practices for secure access management.
IAM works through the following mechanism:
- Authentication: Verifying the identity of users or systems attempting to access AWS resources. This ensures that only legitimate users can log in and interact with AWS services.
- Authorization: Determining whether the authenticated entity is allowed to access the requested resource. IAM policies define permissions that specify what actions users or services can perform.
- IAM Policies and Permissions: IAM uses policies to define and enforce access control rules. Policies can be attached to users, groups, or roles to specify what actions they can perform on AWS resources.
- Role-Based Access Control (RBAC): IAM enables administrators to assign roles to users or services, granting temporary permissions based on their needs. Roles help manage access without sharing long-term credentials.
- Multi-Factor Authentication (MFA): Enhancing security by requiring users to provide a second factor, such as a one-time code from a mobile app, in addition to their password. This prevents unauthorized access even if credentials are compromised.
- Logging and Monitoring: AWS CloudTrail and IAM Access Analyzer provide visibility into IAM-related activities, helping organizations detect and respond to unauthorized access attempts or policy violations.
- Use Case: A developer in your organization may have an IAM user who can access only the necessary resources for development purposes. Groups:
- Use Case: A group called “Admins” could have permission to access and manage all AWS resources, while a “Developers” group might have more restricted access. Roles
- Use Case: An EC2 instance might assume a role that permits it to access a specific S3 bucket. Policies
- Use Case: You can create a policy that only allows read access to a specific S3 bucket for a particular group of users.
- Create IAM Users: Each individual or service that needs access to AWS resources requires an IAM user. Assign unique credentials to ensure accountability and better security.
- Create IAM Groups: Group users with similar access needs and apply permissions to the group. This simplifies permission management and ensures consistency across users with similar roles.
- Define IAM Roles: Create roles for services or temporary users that require specific access levels. Roles prevent the need for long-term credentials and enable secure cross-account access.
- Write IAM Policies: Require MFA for all IAM users, especially those with administrative privileges, to add an extra layer of security. Implementing AWS disaster recovery strategies ensures business continuity by protecting critical resources against security threats and failures.
- Assign Permissions: Attach the relevant policies to users, groups, or roles. This ensures that access is granted only to those who require it for their tasks.
- Enable Multi-Factor Authentication (MFA): Require MFA for all IAM users, especially those with administrative privileges, to add an extra layer of security.
- Use IAM Access Analyzer: Regularly review access patterns with IAM Access Analyzer to identify overly permissive policies and refine permissions accordingly.
- Monitor with AWS CloudTrail: Enable AWS CloudTrail to log all IAM activity and detect unauthorized or suspicious access attempts.
- Rotate and Manage Credentials: Implement a strong password policy and regularly rotate IAM credentials, such as IAM access keys, to reduce security risks.
- Limit Root Account Usage: Use the root account only for essential tasks and create separate IAM users with administrative privileges for daily operations.
- Enable MFA (Multi-Factor Authentication): Use MFA to add an extra layer of security, especially for privileged accounts.
- Regularly Rotate Access Keys: To reduce the risk of compromised credentials, routinely change IAM access keys and passwords.
- Use IAM Roles for Applications: Allow applications and EC2 instances to assume roles rather than using static credentials.
- Monitor and Audit IAM Activity: Use AWS Cloudtrail track user to log and monitor API calls to detect unauthorized access or misconfigurations.
- Implement Strong Password Policies: Enforce password complexity requirements and set expiration policies to enhance security.
- Restrict Root Account: Usage Avoid using the root account for daily operations.
- Review and Update IAM Policies: Regularly Periodically review IAM policies to ensure they align with business needs and security best practices.
To Earn Your AWS Certification, Gain Insights From Leading AWS Experts And Advance Your Career With ACTE’s AWS Online Training Today!
Key Components of AWS IAM
AWS IAM consists of several core components that are integral to managing identities and access control:
Users:A user in IAM represents a person or application that interacts with AWS. Each user has a set of security credentials (username/password, access keys) that allow them to sign in and access AWS services.
Groups are collections of users that share the same permissions. Instead of assigning permissions to each user individually, you can assign them to a group and add users. This simplifies access management when multiple users require similar permissions.
Roles are similar to users but are intended for AWS services or temporary users (like an external contractor). A role doesn’t attach permanent credentials; instead, an entity assumes the role and receives temporary security credentials to access resources. Mastering AWS sysops administrator helps professionals efficiently manage roles and security policies in AWS environments.
Policies are JSON documents that define permissions in AWS. Policies specify what actions are allowed or denied on specific AWS resources. IAM policies can be attached to users, groups, and roles to grant or restrict access.
Gain Your Master’s Certification in AWS by Enrolling in Our AWS Expert Masters Program Training Course.
Setting Up AWS IAM
IAM and Multi-Factor Authentication (MFA)
Multi factor authentication (MFA) is an essential security measure that strengthens user authentication by requiring multiple forms of verification. Instead of relying solely on a username and password, MFA mandates an additional step, such as entering a temporary code from a mobile authenticator app or using a hardware security device. This extra layer of protection helps mitigate the risk of unauthorized access, even if login credentials are compromised.One of the most critical applications of MFA in AWS is securing the root user account. Since the root account has full administrative control over all AWS services and configurations, unauthorized access can lead to severe security breaches, data loss, or service disruptions. Enabling MFA for the root account ensures that even if an attacker obtains the password, they cannot access the account without the second authentication factor. Additionally, MFA plays a crucial role in safeguarding sensitive operations within AWS. Administrators can configure AWS IAM to require MFA before performing high-risk actions, such as modifying security settings, deleting resources, or updating permissions. This precaution reduces the chances of accidental or malicious changes that could compromise system integrity. By implementing MFA across all IAM users, organizations can significantly enhance their cloud security posture, minimize risks, and protect critical resources from potential threats.
Preparing for AWS Job Interviews? Have a Look at Our Blog on AWS Interview Questions and Answers To Ace Your Interview!
AWS IAM Best Practices for Security
To ensure your AWS environment remains secure, it’s essential to follow IAM best practices:
Conclusion
AWS IAM is an essential tool for managing access to cloud resources in a secure, scalable, and efficient way. With IAM, businesses can ensure that users and systems only have access to the resources they need to do their jobs. By using IAM’s granular access controls, policies, roles, and best practices, organizations can maintain strict security over their AWS environment, comply with industry standards, and mitigate risks associated with unauthorized access. In summary, AWS IAM provides flexibility, robust security features, and scalability, allowing businesses to manage permissions in their cloud infrastructure efficiently. To optimize security, it’s crucial to regularly audit IAM configurations, implement MFA, and adhere to user and role management best practices. Enrolling in AWS Training helps professionals develop the skills needed to manage IAM security effectively.





