
- Introduction to AWS ECR
- Setting Up Private and Public Repositories
- Integration with AWS ECS and EKS
- Pushing and Pulling Docker Images
- Security Best Practices for ECR
- IAM Roles and Access Control in ECR
- Conclusion
Amazon Elastic Container Registry (ECR) is a secure, fully managed container registry that enables developers to store, manage, and deploy container images seamlessly. It plays a crucial role in modern DevOps workflows by ensuring efficient image versioning, access control, and high availability for containerized applications.This blog will explore AWS ECR, its significance, and how Cloud Computing Course streamlines container management. We will also cover key features, security mechanisms, and integration with AWS services to optimize your containerized workloads.
Enhance your knowledge in AWS. Join this AWS Certification Training now.
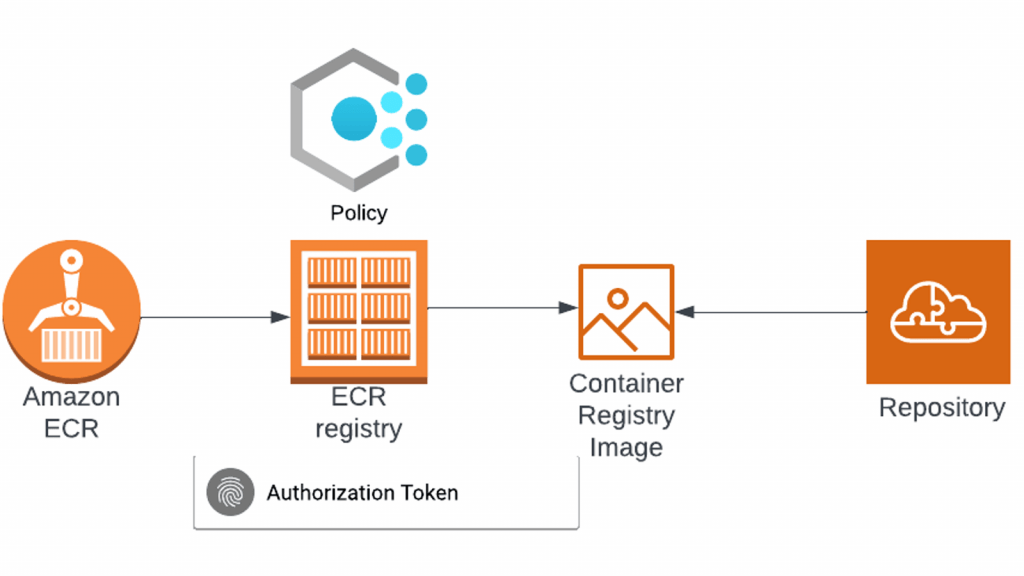
Introduction to AWS ECR
Amazon Elastic Container Registry (ECR) is a fully managed Docker container registry service provided by AWS. It allows developers to store, manage, and deploy Docker container images securely and at scale. ECR integrates seamlessly with other AWS services, providing a centralized platform for container image storage that enhances the ease of deployment and scaling across AWS Outposts Powering Hybrid Cloud.ECR enables organizations to store both private and public Docker images for use with Amazon ECS, Amazon EKS, and AWS Fargate. With built-in security features, automatic scaling, and integration with various CI/CD tools, AWS ECR provides a reliable and efficient solution for managing containerized applications.ECR is designed to provide high-performance, secure image storage with minimal overhead. Whether you are running microservices on ECS, Kubernetes clusters on EKS, or using Fargate, ECR helps streamline the containerization process, making it easier to manage container images for modern applications.
Setting Up Private and Public Repositories
AWS ECR supports both private and public repositories for storing Docker images, each with its own set of use cases and security considerations.
Private Repositories:Private repositories are designed for secure storage of Docker images. These repositories are only accessible to authorized users and services within an AWS account or across multiple accounts with appropriate IAM permissions.
- Creating the repository via the AWS SWF Scalable Workflow Automation, CLI, or SDK.
- Configuring access control using IAM policies to define which users or roles can push or pull images.
- Enabling lifecycle policies to automate the management of images, such as deleting outdated versions to save storage costs.
Public repositories allow you to share your container images with the broader community. These repositories can be accessed by anyone and are useful for distributing public Docker images, open-source projects, or reusable software components.
Setting up a public repository in ECR involves:
- Enabling a public registry option when creating the repository.
- Configuring repository settings such as image versioning and lifecycle policies.
- Setting proper access controls to manage who can push images to the repository.
The primary distinction between private and public repositories in ECR lies in access control. Private repositories offer stricter access management, making them ideal for proprietary images, whereas public repositories provide global access for sharing container images with a wider audience.
Master AWS skills by enrolling in this AWS Certification Training today.
Integration with AWS ECS and EKS
AWS ECR is tightly integrated with Amazon Elastic Container Service (ECS) and Amazon Elastic Kubernetes Service (EKS), making it easy to deploy and manage Docker containers in production. ECS tasks and services can pull container images directly from ECR repositories. You can configure ECS to use a particular image version stored in ECR when launching containers.ECS integrates with ECR to simplify the process of deploying Docker containers, providing features like auto-scaling, load balancing, and simplified container management.EKS clusters use Kubernetes to manage containerized applications. ECR integrates with EKS for container image storage, enabling Kubernetes pods to pull images from ECR directly.Kubernetes manifests, such as Deployment configurations, can reference Docker images stored in Azure Sandbox all the Information you need deployment to EKS clusters.AWS ECR enhances containerized application deployment by offering seamless integration with ECS and EKS. This allows organizations to efficiently manage and scale their container workloads with high reliability. ECS leverages ECR for simplified container management, enabling smooth image retrieval and deployment.Similarly, EKS utilizes Kubernetes to orchestrate applications, with ECR serving as a secure and scalable container image storage solution. By leveraging Kubernetes manifests, teams can automate deployments and streamline CI/CD pipelines. With ECR’s robust security, scalability, and automation, businesses can optimize containerized workflows while ensuring performance and compliance across cloud environments.
Want to lead in Cloud Computing? Enroll in ACTE’s AWS Master Training Course and start your journey today!
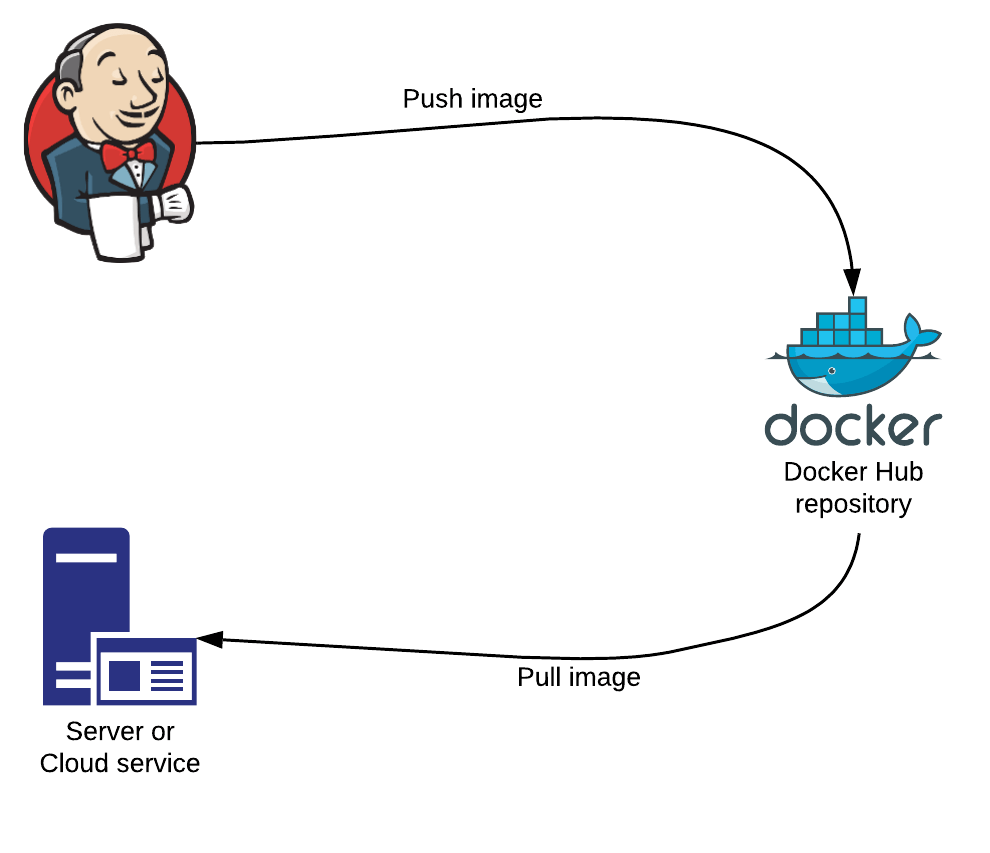
Pushing and Pulling Docker Images
The core functionality of AWS ECR revolves around the ability to push Docker images (upload) to and pull Docker images (download) from the repository. Here’s how this works:
Pushing Docker Images:- Before pushing a Docker image to AWS ECR, ensure that you have the AWS CLI installed and configured, and that you’re authenticated with ECR using the aws ecr get-login-password command.
- To push an image:
- Build the Docker image: Create your Docker image using a Dockerfile and the docker build command.
- Tag the image: Use the docker tag command to tag your local image with the full ECR repository URI.
- Push the image: Use the docker push command to upload the tagged image to your ECR repository.
- Example:
- docker tag my-image:latest 123456789012.dkr.ecr.us-west-2.amazonaws.com/my-repository:latest
- docker push 123456789012.dkr.ecr.us-west-2.amazonaws.com/my-repository:latest
- Example:
- # docker pull #123456789012.dkr.ecr.us-west-2.amazonaws.com/my-repository:latest
The process of pulling images is similar to pushing but in reverse. After pulling, the image is available locally for use in containerized applications or further processing.
Security Best Practices for ECR
Security is a top priority when storing Docker images, especially for production environments. Here are some best practices to enhance the security of your ECR repositories:Enable Encryption:Encryption at rest: ECR automatically encrypts images at rest using AWS Key Management Service (KMS). Ensure that AWS Training best practices for managing and rotating encryption keys. Encryption in transit: ECR uses SSL/TLS to encrypt data in transit, preventing unauthorized access during image upload or download. Use Fine-Grained IAM Policies. Apply the principle of least privilege when assigning IAM roles and policies to users and services. Only grant the necessary permissions for accessing or managing ECR resources. AWS ECR integrates with Amazon ECR Image Scanning to scan Docker images for vulnerabilities. Enable image scanning on your repositories to detect common security issues, such as known vulnerabilities in dependencies. Use AWS CloudTrail and Amazon CloudWatch to monitor API calls and track user activity within ECR. Set up alerts for any suspicious or unauthorized access attempts. Use Private Repositories for Sensitive Images. Store sensitive or proprietary Docker images in private repositories to ensure they are only accessible by authorized users and services. Implement lifecycle policies to automatically delete outdated or unused images. This helps reduce the risk of accidentally using stale or insecure images in your applications.Consider using image signing to verify the integrity and authenticity of the Docker images before they are deployed in production environments. Securing containerized applications is crucial for maintaining a robust cloud environment. AWS ECR offers built-in security features to protect your Docker images while ensuring compliance with best practices. By implementing strong IAM policies, continuous vulnerability scanning, and encrypted data transfer, organizations can minimize security risks and unauthorized access. Additionally, monitoring ECR activities through AWS CloudTrail and CloudWatch enhances visibility, enabling quick threat detection and response. Using private repositories for sensitive images, enforcing lifecycle policies to remove obsolete images, and leveraging image signing further strengthen container security. These proactive measures help organizations maintain a secure, efficient, and well-managed container registry.
Preparing for a job interview? Explore our blog on AWS Interview Questions and Answers!
IAM Roles and Access Control in ECR
AWS Identity and Access Management (IAM) plays a critical role in securing and controlling access to ECR repositories. You can manage access control at multiple levels, ensuring that only authorized users or services can push or pull Docker images.
IAM Policies:IAM policies define permissions for users, groups, or roles, dictating what actions they can perform within ECR. For example, permissions can be granted to allow Exploring Elastic Network Interfaces in AWS and pulling images from specific repositories.
- ecr:BatchCheckLayerAvailability: Allows checking the availability of image layers in the repository.
- ecr:PutImage: Allows pushing an image to a repository.
- ecr:GetAuthorizationToken: Allows authentication to ECR.
- When using services like Amazon ECS or EKS, create IAM roles for your services that grant them the necessary permissions to interact with ECR.
- Example: An ECS task role would require
- ecr:GetAuthorizationToken and ecr:PullImage permissions to pull images from ECR.
You can set up cross-account access for ECR repositories using resource-based policies. AWS Transit Gateway Simplifying Network Connectivity allows a user or service in one AWS account to access a repository in another account.
Access Control Using Policies:Implement fine-grained access control by attaching IAM policies that restrict access to specific repositories or actions, such as limiting push access to administrators and pull access to developers.
Conclusion
By following these best practices, you can ensure that your Docker images stored in AWS ECR are secure, reliable, and compliant with your organization’s security policies.In summary, AWS Elastic Container Registry (ECR) provides a robust, scalable, and secure solution for managing Docker container images. With its seamless integration into AWS services like ECS and EKS, and AWS Training focus on security, ECR is an essential component for modern containerized application deployments. By understanding its key features and best practices, you can efficiently use ECR to manage and scale your containerized workloads.





