
- Introduction to MAC Addresses
- How MAC Addresses Work in Networking
- Differences Between MAC and IP Addresses
- MAC Address Spoofing and Security Risks
- Finding and Managing MAC Addresses in Devices
- Role of MAC Addresses in Network Security
- Conclusion
Introduction to MAC Addresses
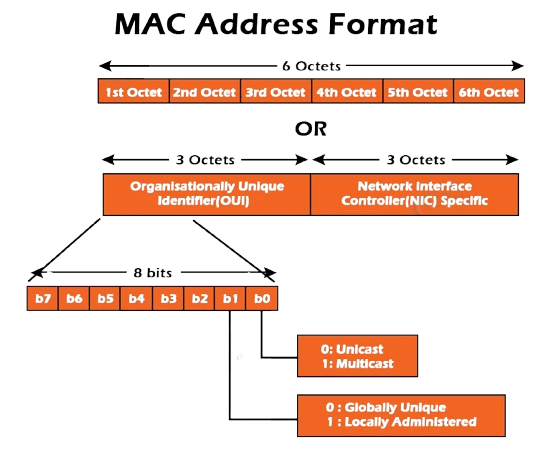
A MAC (Media Access Control) address is a unique identifier assigned to network interfaces for communications on the physical network segment. Cloud Computing Course is a hardware address that is used to identify devices in a local area network (LAN) or other network environments. MAC addresses operate at the Data Link Layer (Layer 2) of the OSI model, which is responsible for node-to-node data transfer. Each MAC address is assigned by the manufacturer and is embedded into the network interface card (NIC) of devices such as computers, routers, switches, and printers. Typically, a MAC address is composed of six pairs of hexadecimal digits (e.g., 00:1A:2B:3C:4D:5E), where the first half represents the manufacturer’s unique identifier, and the second half is the serial number of the device.
How MAC Addresses Work in Networking
In networking, the MAC address plays a critical role in ensuring that data packets are correctly delivered within a local network. Here’s how it works:
- Data Link Layer Operation:When a device wants to send data over a network, it packages the data into frames. Each frame contains both the source and destination MAC addresses.
- Frame Transmission: Devices on the same network segment (such as a LAN) use MAC addresses to Azure Data Studio A Complete Guide. When a device sends data, it looks up the MAC address of the target device within its local network.
- Switching: Network switches use MAC addresses to forward data frames. Switches keep a table of MAC addresses (called a MAC table or forwarding table) that maps MAC addresses to specific physical ports. This allows switches to forward traffic only to the appropriate device, rather than broadcasting to all devices on the network.
Advance your Cloud Computing career by joining this Cloud Computing Online Course now.
- ARP and IP Resolution: Although MAC addresses operate at Layer 2, they are often used in conjunction with Layer 3 (IP) addresses. The ARP (Address Resolution Protocol) is used to map an IP address to a MAC address, allowing devices to communicate across networks. When a device needs to send data to an IP address, it uses ARP to discover the corresponding MAC address.
- Unicast Communication: MAC addresses are essential for unicast communication, where data is sent from one device to another. By identifying the destination device’s unique MAC address, the data is directed accurately to the correct device, ensuring efficient and direct communication.
- Broadcast and Multicast Transmission: MAC addresses also play a role in broadcast and multicast communication. In these scenarios, data is sent to all devices on a network (broadcast) or a specific group of devices (multicast). These types of communication rely on special MAC addresses to ensure data is received by the correct devices.
- Collision Detection: MAC addresses are integral to the process of collision detection in older networking protocols like Ethernet. Devices on a network segment detect collisions by monitoring the MAC addresses of devices trying to communicate simultaneously, helping to manage data transmission effectively.
- Security and Authentication: Some networks use MAC addresses for authentication, allowing only devices with specific MAC addresses to connect to a network. This is commonly seen in wireless networks, where routers or access points can be configured to permit only registered MAC addresses to A Comprehensive AWS Deepracer.
- Network Troubleshooting: MAC addresses are valuable in network troubleshooting. By monitoring the MAC addresses of devices communicating on the network, network administrators can identify misconfigurations, unauthorized devices, or network issues like bandwidth bottlenecks, leading to quicker resolution of connectivity problems.
- Some networks use Building Scalable and Secure Microservices on AWS to control access to the network. By spoofing a legitimate MAC address, unauthorized devices can gain access to the network, bypassing security restrictions.
- Attackers can spoof a MAC address to impersonate a trusted device on the network. This can be used to intercept data or launch man-in-the-middle attacks.
- By spoofing MAC addresses, attackers can flood the network with fake devices, overwhelming network resources and disrupting normal operations.
- Spoofing a MAC address can also be used to hijack active network sessions, redirecting traffic intended for another device to the attacker’s device, thus enabling data theft or modification.
- Attackers can combine MAC address spoofing with IP address spoofing to bypass security systems that rely on IP filtering. This allows malicious devices to gain unauthorized access or manipulate data flows undetected by traditional security mechanisms.
- In environments using Dynamic Host Configuration Protocol (DHCP), attackers can spoof a MAC address to impersonate an authorized device and receive a valid IP address from the DHCP server. Cloud Computing Course can lead to unauthorized access to network resources or data interception.
- Networks that use MAC address-based device tracking (e.g., to monitor users or devices) can be circumvented by spoofing the MAC address, allowing attackers to hide their presence and actions on the network.
- MAC address spoofing can undermine the effectiveness of intrusion detection systems (IDS) or intrusion prevention systems (IPS), which often rely on identifying devices based on their MAC addresses to detect and respond to malicious activities.
- When a trusted device’s MAC address is spoofed, attackers may be able to intercept encrypted communication between devices or between a device and a server. By impersonating a trusted device, they can monitor network traffic or attempt to decrypt the data being exchanged.
- On Windows: Open the Command Prompt and run the command ipconfig /all. The MAC address will be listed as the Physical Address.
- On MacOS: Open System Preferences > Network > Advanced, and the MAC address will be displayed under Wi-Fi or Ethernet settings.
- On Linux: Use the command ifconfig or ip addr show to find the MAC address of the network interface.
- Managing MAC Addresses:Network administrators can configure static MAC address entries in switches or routers to ensure that specific devices are always mapped to the same port. This improves security and network management.
- Dynamic MAC learning: Switches automatically learn MAC addresses from incoming traffic, but administrators can configure MAC address tables to prevent spoofing by limiting changes.
- Changing MAC Address:Devices can change their MAC address through software tools. While this is commonly done in testing or Azure Portal Guide to Cloud Management , it is generally discouraged for regular use due to the security risks associated with MAC address spoofing.
- Port Security: Network administrators can configure port security on switches to bind specific MAC addresses to particular ports, preventing unauthorized devices from accessing the network.
- Privacy and Security: Changing a MAC address can be used for privacy purposes, allowing users to prevent tracking on public networks.
- MAC Spoofing Risks: Changing a MAC address to impersonate another device can be illegal in certain regions, especially if used to bypass security measures or restrictions.
Become a Cloud Computing expert by enrolling in this Cloud Computing Online Course today.
Differences Between MAC and IP Addresses
| Aspect | MAC Address | IP Address |
|---|---|---|
| Layer of Operation | Operates at the Data Link Layer (Layer 2), used for communication within the same local network segment. | Operates at the Network Layer (Layer 3), used for routing data across different networks. |
| Uniqueness | Typically globally unique and assigned to the network interface card (NIC) by the manufacturer. | Assigned by a network administrator or dynamically by a DHCP server; can change over time. |
| Purpose | Used to identify devices on the same local network, ensuring data frames are delivered to the correct device. | Used to route data between different networks and devices over the internet or intranets. |
| Persistence | Generally permanent and fixed, tied to the hardware of the device. | Can be reassigned, especially in dynamic IP environments using DHCP. |
| Format | 12-character hexadecimal string (e.g., 00:14:22:01:23:45), with the first 6 digits representing the manufacturer’s OUI. | IPv4 format (e.g., 192.168.1.1) or IPv6 format (e.g., 2001:0db8:85a3:0000:0000:8a2e:0370:7334). |
| Scope of Use | Used for communication within the same local area network (LAN) or broadcast domain. | Used to route data across the internet or between different networks, enabling both local and global communication. |
| Address Type | Physical address tied to the hardware of the network interface card (NIC). | Logical address assigned to a device in a network, not tied to hardware. |
| Broadcast Communication | Can send broadcast messages to all devices in the local network using the MAC broadcast address (FF:FF:FF:FF:FF:FF). | Broadcast communication is limited to a local subnet, and routers do not forward broadcast traffic. |
| Role in Networking Protocols | Used in protocols like Ethernet and Wi-Fi to deliver data at the Data Link Layer. | Used in routing protocols (e.g., RIP, OSPF, BGP) to determine the best path for data between networks. |
MAC Address Spoofing and Security Risks
MAC address spoofing is the practice of changing the MAC address of a device to impersonate another device on the network. This can have significant security implications, including:
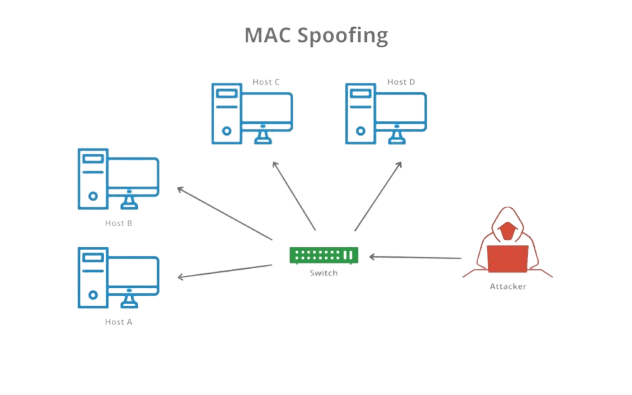
To mitigate MAC address spoofing, network administrators can implement port security on switches, using techniques like sticky MAC addresses or 802.1X authentication to ensure that only authorized devices can access the network.
Finding and Managing MAC Addresses in Devices
There are several methods for finding and managing MAC addresses in devices:
Finding MAC Address on a Computer:
Ready to excel in Cloud Computing? Enroll in ACTE’s Cloud Computing Master Program Training Course and begin your journey today!
Managing MAC Addresses:
Changing MAC Address:
Legal Implications:
Are you getting ready for your Cloud Computing interview? Check out our blog on Cloud Computing Interview Questions and Answers!
Role of MAC Addresses in Network Security
MAC addresses play an important role in network security, as they help identify devices and control network access. Some key security functions related to MAC addresses.MAC addresses are used in network access control mechanisms, such as MAC filtering, which allows only devices with specific MAC addresses to access a network. This is commonly used in Wi-Fi routers to secure home networks. Security tools like Intrusion Detection Systems (IDS) may use Reliable Scalable AWS Codedeploy for CI CDto detect unauthorized or suspicious devices on the network. By comparing incoming traffic with known MAC address patterns, the IDS can flag potential intrusions.
MAC addresses are often used in network monitoring tools to track devices and detect unusual activity. Changes in a device’s MAC address or unauthorized devices appearing on the network can trigger alerts for network administrators.While MAC addresses themselves are not encrypted, MAC address randomization is used by some operating systems and network devices to enhance privacy and prevent tracking by attackers. For example, some mobile devices randomize their MAC addresses when scanning for Wi-Fi networks to protect user privacy.MAC addresses can also play a role in network segmentation. Administrators may define policies where devices with specific MAC addresses can only communicate within a designated segment, isolating sensitive devices from general network traffic.
Conclusion
In conclusion, MAC addresses are essential components in network communications, playing a crucial role in ensuring that data is correctly routed within a local network. They are unique identifiers for devices, helping network switches efficiently direct traffic and enabling devices to communicate with each other. However, Cloud Computing Course implications of MAC address spoofing pose significant risks, such as unauthorized access, data interception, and potential network disruptions. To mitigate these risks, network administrators must implement proper security measures like port security, MAC address filtering, and network monitoring. By understanding the critical function and potential vulnerabilities of MAC addresses, organizations can better protect their networks from malicious activities and ensure a secure and efficient network environment.





