
- Overview of AWS Inspector
- Features and Capabilities of AWS Inspector
- How AWS Inspector Works
- Installing and Configuring AWS Inspector
- Types of Security Assessments Performed
- Integrating AWS Inspector with Other AWS Security Services
- Best Practices for Security Audits with AWS Inspector
- Understanding AWS Inspector Reports and Findings
- Automating Security Checks with AWS Inspector
- Compliance and Regulatory Benefits
- Limitations and Considerations
- Future Developments in AWS Inspector
- Conclusion
Overview of AWS Inspector
Amazon Web Services (AWS) offers security and compliance services that help businesses protect their cloud infrastructure. One of these services is AWS Inspector, a security assessment service designed to help identify vulnerabilities and security best practice violations in AWS environments. It automates evaluating the security state of applications deployed in AWS, making it easier for organizations to detect, manage, and resolve potential security issues, a critical skill taught in Amazon Web Service Training. By leveraging AWS Inspector, companies can improve their security posture, mitigate risks, and comply with security and regulatory standards. This article will explore the features, capabilities, workings, and best practices for using AWS Inspector, its integration with other AWS security services, compliance benefits, and future developments.
Features and Capabilities of AWS Inspector
- Automated Vulnerability Scanning: AWS Inspector automatically performs security assessments on your AWS resources, such as EC2 instances, and analyzes network traffic and configurations to identify common vulnerabilities and exposures (CVEs).
- Security Best Practices Checks: AWS Inspector performs checks to ensure that your systems adhere to security best practices, including ensuring proper configurations of security groups and IAM roles.
- Comprehensive Security Assessments: The service provides deep analysis and insights into your infrastructure’s security and compliance posture, including scanning for vulnerabilities, misconfigurations, and compliance violations.
AWS Inspector provides a range of features and capabilities for assessing the security of your AWS workloads, both at the application and infrastructure levels. It enables developers, security teams, and IT professionals to efficiently identify and mitigate vulnerabilities in their environments.
Explore AWS in Depth, Check Out Our Comprehensive AWS Course To Gain Insights From Our Experts!
- Customizable Assessment Templates: AWS Inspector allows users to create customized security assessment templates tailored to their needs. You can define what type of vulnerabilities to assess and how frequently assessments should be performed.
- Integration with AWS CloudWatch and SNS: AWS Inspector integrates with AWS CloudWatch to collect logs and monitor assessment results, a feature that complements practices in Agile vs. DevOps, where continuous monitoring and feedback loops are essential for improving development and operational efficiency. It also integrates with Amazon SNS (Simple Notification Service) to alert users when detecting vulnerabilities or violations.
- Automatic Remediation Recommendations: AWS Inspector provides actionable recommendations to help resolve security issues after identifying vulnerabilities or misconfigurations. It highlights critical vulnerabilities, reducing the time needed to respond.
- Detailed Reports: AWS Inspector generates detailed reports on the findings of each security assessment, including the severity of the issues detected, which enables teams to prioritize remediation efforts based on the risk to the organization. Capabilities:
- Network Reachability Analysis: AWS Inspector assesses the reachability of your instances within your network and suggests security improvements to minimize the attack surface.
- Compliance Checks: It helps users ensure that their AWS environment meets key regulatory standards such as PCI-DSS, HIPAA, SOC 2, and others.
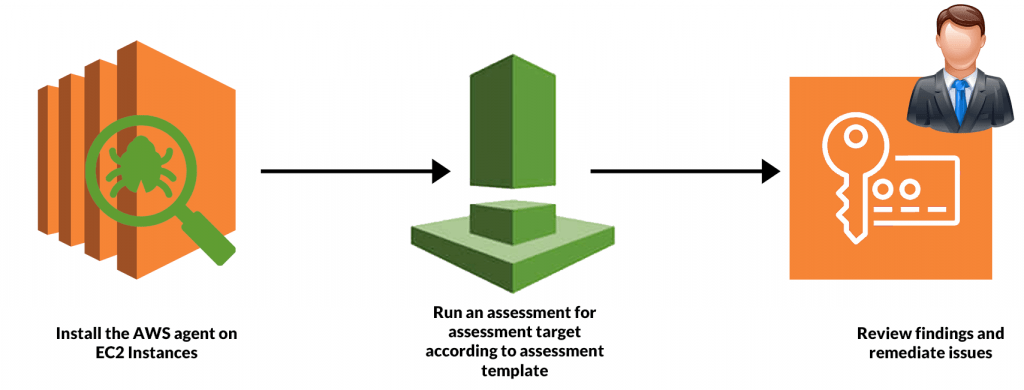
How AWS Inspector Works
- Set Up AWS Inspector: Enable Inspector Go to the AWS Management Console, navigate to the AWS Inspector service, and follow the prompts to enable it for your account. Configure Permissions AWS Inspector requires specific IAM roles and policies to interact with your resources. You must configure the appropriate permissions for your AWS account and instances.
- Create Assessment Targets: Assessment targets define which resources AWS Inspector should scan. You can specify EC2 instances, VPCs, or any other AWS resources you want to assess, similar to how GCP Security ensures the scanning and security of resources within the Google Cloud Platform to maintain robust security practices.
- Create Assessment Templates: Once the assessment target is defined, create a security assessment template. Select the security checks you want AWS Inspector to run (e.g., network reachability, security best practices, vulnerability scans). You can also set the frequency of assessments and configure any custom rules.
- Run Security Assessments: After configuring the assessment target and template, run the security assessment. You can either run it immediately or schedule it for a later time.
- Review Findings and Reports: Once the assessment is complete, the AWS Inspector will generate detailed findings and reports. Review these findings to determine the severity of issues and take action based on the recommendations.
- Vulnerability Scanning: It checks your EC2 instances for known vulnerabilities by scanning the underlying operating systems and installing software for unpatched CVEs (Common Vulnerabilities and Exposures).
- Best Practice Violations: AWS Inspector evaluates your resources against security best practices, such as misconfigurations in security groups, IAM policies, EC2 instance configurations, etc.
- Network Reachability: This feature helps assess which EC2 instances are exposed to the public internet and ensures no unnecessary network access is available, reducing the attack surface.
- Compliance Violations: AWS Inspector checks your resources against common compliance frameworks (PCI-DSS, HIPAA, SOC 2, etc.) to ensure your infrastructure meets regulatory requirements, while AWS Network Load Balancer helps distribute traffic efficiently across your resources to maintain high availability and scalability in compliance with these standards.
- Automate Regular Assessments: Schedule periodic security assessments to monitor your resources and detect vulnerabilities as they emerge continuously.
- Use Multiple Assessment Templates: Customize templates to fit specific workloads. For example, have different templates for web applications, databases, and critical infrastructure to tailor the security checks to their needs, a practice that is covered in-depth in AWS Training to enhance security management across diverse AWS environments.
- Prioritize Remediation: Classify findings by severity and prioritize remediation efforts based on the risk posed by each issue. Critical and high-severity matters should be addressed immediately, while low-severity topics can be tracked for later resolution.
- Review Reports Frequently: Regularly review AWS Inspector reports to ensure you promptly address any vulnerabilities and misconfigurations.
- Integrate with Automated Response Systems: Incorporate AWS Inspector findings with automated security response tools, such as Lambda or Systems Manager, to initiate remediation actions directly from findings.
- After each security assessment, AWS Inspector generates detailed reports and findings that provide crucial insights into the security posture of cloud workloads. These findings are categorized by severity levels, enabling security teams to prioritize and address the most critical issues first. The severity levels are classified as critical, high, medium, or low, with critical issues representing the most urgent threats that need immediate attention, while low-level findings may not require immediate remediation but should still be addressed over time.
- The Issue Description provides a comprehensive explanation of the identified issue. It typically includes information such as the Common Vulnerabilities and Exposures (CVE) identifiers for known vulnerabilities or references to specific compliance violations, which can directly impact the security of your AWS EC2 instances and other cloud resources.
- In addition to the issue description, AWS Inspector provides Remediation Recommendations to guide users on how to fix or mitigate the identified vulnerabilities or misconfigurations. These recommendations are tailored to the specific issue and provide actionable steps, such as applying security patches, updating configurations, or changing access permissions. Following these remediation steps helps minimize the risk of exploitation and ensures that the affected systems are returned to a secure state.
- The Resource Affected section identifies the specific EC2 instance, resource, or service impacted by the security issue. This granular information allows security teams to quickly locate and address the affected resources within their AWS environment. By understanding which resource is vulnerable, users can prioritize actions based on the criticality of the resource, such as addressing issues on production servers before non-production environments.
- Together, these detailed reports and findings help organizations to not only detect security vulnerabilities but also to understand their impact and take the necessary actions to mitigate risks and enhance the overall security of their cloud infrastructure.
- Limited to AWS Resources: AWS Inspector is designed specifically to assess the security of AWS resources, such as EC2 instances, Amazon S3 buckets, and other AWS services. This means it does not have the capability to evaluate security configurations or vulnerabilities within on-premises infrastructure or hybrid environments. Organizations that operate in a multi-cloud or on-premises setup may need to use additional security assessment tools to cover those areas outside of AWS.
- Limited Customization for Complex Applications: AWS Inspector provides automated security assessments based on predefined templates and compliance frameworks. However, highly specialized or custom applications that don’t fit neatly into the standard AWS Inspector frameworks may require additional configuration or customization beyond what AWS Inspector offers. This could involve creating custom rules, extending the service, or using other specialized tools to ensure thorough security assessments for these complex applications.
- Dependency on AWS Config: To fully utilize AWS Inspector’s compliance capabilities, it requires integration with AWS Config, which helps track changes in your AWS resources and provides a history of configuration states. Without AWS Config, AWS Inspector’s ability to assess and ensure compliance with regulatory standards, such as PCI-DSS, HIPAA, or SOC 2, may be limited. This integration ensures continuous monitoring of resource configurations and allows AWS Inspector to automatically detect misconfigurations that may lead to compliance violations.
- Broader Coverage: AWS Inspector is likely to expand its coverage to include more AWS resources and hybrid environments. As businesses increasingly adopt complex cloud infrastructures, including hybrid and multi-cloud setups, the need for comprehensive security assessments grows, which aligns with practices from the DevOps Periodic Table, where continuous integration, security, and testing are key to maintaining secure and efficient cloud environments. By extending support to a broader range of AWS services and integrating with on-premises systems, AWS Inspector will provide a more holistic view of an organization’s security posture, ensuring that all components of the infrastructure, whether in the cloud or on-premises, are continuously monitored and assessed for vulnerabilities.
- Enhanced Automation: The future of AWS Inspector will see increased automation, reducing the manual effort required to ensure compliance and security. Tighter integrations with other AWS services such as AWS Config, AWS CloudTrail, and AWS CloudWatch will enable seamless, end-to-end security management. This means that security assessments can be automated across an organization’s entire AWS infrastructure, from initial deployment to continuous monitoring. Additionally, automated remediation workflows could be introduced, allowing organizations to address vulnerabilities more swiftly and efficiently without manual intervention, ensuring faster compliance and a more proactive security stance.
- AI and ML Enhancements: Advanced machine learning (ML) algorithms are expected to play a key role in the future of AWS Inspector. With the integration of AI and ML, the service will be able to predict and detect new vulnerabilities more proactively. These enhancements will allow AWS Inspector to learn from historical data and identify potential security risks before they manifest. By continuously analyzing vast amounts of data, AI and ML can also help in classifying vulnerabilities based on their severity and potential impact, offering organizations more precise and actionable insights. This forward-looking approach will not only make security assessments more accurate but will also help in keeping pace with evolving threats in the cybersecurity landscape.
AWS Inspector is a powerful tool that continuously scans your AWS resources to assess security based on predefined rules and custom configurations. The process begins by defining the “assessment target,” where you specify the AWS resources to be included, such as EC2 instances or entire VPCs. Next, you create the “assessment template,” which outlines the types of security assessments to be run, such as checking for network reachability or common vulnerabilities. AWS Inspector then performs a thorough security assessment of the selected resources, analyzing various components like operating system and application configurations to identify CVEs, network configurations to ensure security groups and firewall rules are correctly set, and IAM roles and policies to enforce least-privilege principles, a process that is essential in Understanding Private Cloud Computing, where security management and proper configurations are critical for maintaining secure cloud environments. After scanning, AWS Inspector generates a detailed report that highlights vulnerabilities, misconfigurations, and policy violations, categorized by severity and accompanied by remediation recommendations. To ensure continuous security, AWS Inspector allows you to schedule recurring assessments and set up alerts through Amazon SNS, notifying team members whenever new vulnerabilities are discovered or when there are changes in the security posture of your resources. This continuous monitoring helps maintain a robust security framework within AWS environments.
Installing and Configuring AWS Inspector
Starting with AWS Inspector involves setting up the service within your AWS environment. Here are the basic steps for installation and configuration:
Interested in Obtaining Your AWS Certificate? View The AWS Course Offered By ACTE Right Now!
Types of Security Assessments Performed
AWS Inspector offers a variety of security assessments that cater to different aspects of your AWS environment:
Integrating AWS Inspector with Other AWS Security Services
AWS Inspector integrates seamlessly with other AWS security services to provide a comprehensive security solution for cloud workloads. By leveraging AWS CloudWatch, users can monitor the status of assessments and capture logs related to security findings, ensuring that they are aware of any potential issues in real time. Additionally, AWS Inspector integrates with AWS Security Hub, centralizing its findings along with results from other AWS security services, offering a unified view of an organization’s security posture. This centralization allows for easier tracking and management of security issues across all services. AWS Config further enhances this integration by allowing users to monitor and assess compliance of their AWS resources against configuration best practices and predefined rules, helping organizations stay aligned with industry standards. Lastly, Amazon SNS (Simple Notification Service) enables automated notifications, ensuring that users are promptly alerted about security findings and vulnerabilities. This ensures that organizations can take timely and effective action to mitigate risks and maintain a secure cloud environment. These integrations collectively enable organizations to create a more streamlined and responsive security framework, strengthening overall cloud security management.
Best Practices for Security Audits with AWS Inspector
To get the most out of AWS Inspector and ensure a comprehensive security audit, consider the following best practices:
Looking to Master AWS? Discover the AWS Masters Course Available at ACTE Now!
Understanding AWS Inspector Reports and Findings
Automating Security Checks with AWS Inspector
To maintain continuous security within your AWS environment, it’s essential to automate security checks by integrating AWS Inspector with other AWS services such as AWS Lambda and Amazon CloudWatch Events. AWS Inspector is a powerful service that automatically assesses your applications for vulnerabilities and security risks, and by combining it with AWS Lambda, you can create automated workflows to quickly remediate issues. For instance, when AWS Inspector identifies a security vulnerability, Lambda functions can be triggered to apply predefined remediation steps, ensuring a fast and efficient response, which is crucial for the Future of Mobile Cloud Computing, where quick security responses are vital for maintaining mobile application performance and user trust. Additionally, by using Amazon CloudWatch Events, you can monitor real-time security findings and set up event-driven alerts or actions, further enhancing the speed and accuracy of your security operations. This seamless automation of security processes not only reduces manual intervention but also improves your organization’s ability to rapidly respond to threats, ensuring that security vulnerabilities are addressed promptly and efficiently. Implementing automated remediation workflows significantly strengthens your AWS security posture, reducing the risk of potential breaches and enhancing overall system reliability.
Compliance and Regulatory Benefits
AWS Inspector is a powerful automated security assessment service that helps organizations ensure their infrastructure adheres to regulatory compliance requirements and industry standards. By continuously scanning and evaluating resources, AWS Inspector identifies potential vulnerabilities and security issues within an organization’s environment. It automates compliance checks against widely recognized frameworks such as PCI-DSS, HIPAA, and SOC 2, enabling businesses to streamline their compliance efforts. AWS Inspector not only improves the overall security posture of the infrastructure but also simplifies the process of maintaining compliance over time, an essential part of Advanced Infrastructure as a Service in Cloud Computing, where ongoing security assessments and compliance management are critical for maintaining robust cloud infrastructures. With automated reports and actionable insights, it helps businesses meet regulatory standards, reduce manual efforts, and stay aligned with evolving industry requirements. This makes it easier for organizations to focus on their core business while maintaining a high level of security and compliance across their AWS environments. By leveraging AWS Inspector, organizations can ensure that their systems are continuously evaluated, minimizing risks and achieving peace of mind regarding data security and regulatory adherence.
Limitations and Considerations
While AWS Inspector is a powerful tool, there are certain limitations to keep in mind:
Go Through These AWS Interview Questions & Answer to Excel in Your Upcoming Interview.
Future Developments in AWS Inspector
As AWS continues to enhance its security services, AWS Inspector is expected to evolve with new features that will further strengthen the security and compliance capabilities for organizations. Future developments may include:
Conclusion
In conclusion, AWS Inspector serves as a crucial tool for organizations striving to enhance the security of their AWS infrastructure while ensuring compliance with industry standards and best practices. By automating the process of security assessments, AWS Inspector enables businesses to continuously evaluate their cloud environments for vulnerabilities, misconfigurations, and compliance gaps, a crucial aspect of ensuring security best practices, often emphasized in AWS Training. This automation helps reduce the manual effort required for security audits and provides a more efficient approach to identifying and mitigating risks. Furthermore, the seamless integration of AWS Inspector with other AWS services such as AWS CloudTrail, AWS Config, and AWS Security Hub allows organizations to build a comprehensive security framework that is scalable and adaptive to changing threat landscapes. With its powerful capabilities for monitoring and enforcing security best practices, AWS Inspector empowers organizations to proactively safeguard their cloud environments, protect sensitive data, and ensure long-term operational resilience.





