
- Introduction
- What is DevSecOps?
- Key Principles of DevSecOps
- How DevSecOps Integrates Security into DevOps
- Benefits of DevSecOps
- DevSecOps Tools and Technologies
- Implementing DevSecOps in an Organization
- Conclusion
Introduction
In today’s fast-paced software development landscape, security is no longer an afterthought but a fundamental necessity. DevSecOps short for Development, Security, and Operations is an extension of DevOps that integrates security into every phase of the software development lifecycle. Unlike traditional security practices that are often applied late in the development process, Devops Training ensures security is embedded from the start, fostering a proactive approach to identifying and mitigating vulnerabilities. By automating security checks and promoting collaboration between development, security, and operations teams, DevSecOps enables organizations to build secure applications without compromising speed or agility.
Become a Devops expert by enrolling in this Devops Online Course today.
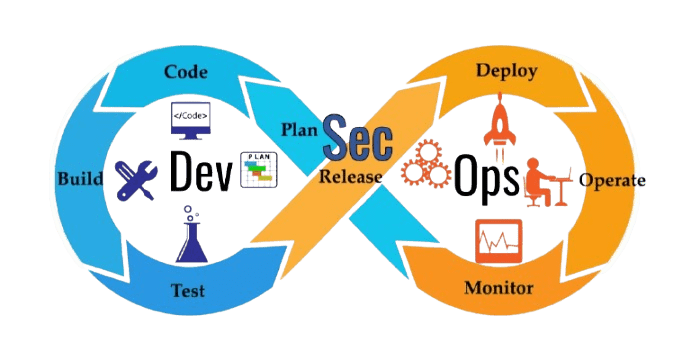
What is DevSecOps?
DevSecOps is an extension of DevOps that integrates security into every phase of the DevOps lifecycle. The term stands for Development, Security, and Operations, emphasizing the need for security to be integrated early and throughout the development pipeline. Unlike traditional approaches where security is often treated as a separate function that happens late in the development process, Devops Testing Strategy Guide seeks to build security into the fabric of the development and deployment lifecycle. The primary objective is to ensure that security is an integral part of every stage, from planning through development, testing, and deployment, without slowing down the agility and speed that DevOps aims to achieve.
In DevSecOps, security becomes a shared responsibility across the entire team—developers, operations, and security professionals—rather than relying solely on security teams to address vulnerabilities after the software is developed. By integrating security into DevOps practices, teams can identify, address, and fix security issues more quickly and proactively, rather than waiting until later stages of development or production.
Key Principles of DevSecOps
- Shift Left Security: One of the core principles of DevSecOps is the concept of “shifting left,” meaning incorporating security at the earliest stages of the software development lifecycle (SDLC). In traditional development models, security is often an afterthought and typically becomes a focus only once the software is developed. In DevSecOps, security is integrated early during the design and coding phases, allowing for the detection and remediation of vulnerabilities before they escalate.
- Automation: DevSecOps encourages automation to ensure consistent security checks and tests throughout the development pipeline. Automated security tools can be integrated into CI/CD pipelines to conduct static code analysis, vulnerability scanning, and penetration testing, ensuring that security is continuously monitored. This minimizes human error and ensures that security testing is as fast and Azure Boards with Devops .
- Continuous Monitoring and Feedback: In DevSecOps, continuous monitoring of applications and systems in production is essential to identify potential security threats and vulnerabilities as they arise. This practice allows security teams to respond proactively and rapidly to security incidents. Feedback loops are also integrated so that any security concerns identified in production can be addressed promptly, improving the overall security posture.
- Collaboration Across Teams: A key tenet of DevSecOps is the collaboration between development, security, and operations teams. Security should not be siloed within a specific team but should be everyone’s responsibility. Developers need to write secure code, operations need to ensure that security is maintained during deployment and monitoring, and security professionals need to provide expertise on securing the infrastructure and ensuring compliance.
- Security as Code: DevSecOps incorporates the principle of treating security as code, meaning that security policies, rules, and configurations are defined in code and stored in version control systems alongside the application code. This allows teams to automate security policy enforcement and ensures that security is maintained consistently across the development pipeline.
- Compliance as Code: With the increasing focus on regulatory compliance, DevSecOps emphasizes automating compliance checks. Organizations can embed compliance requirements directly into their DevSecOps pipeline, ensuring that regulatory standards are continuously met and monitored throughout the development and deployment process.
- Improved Security Posture: By embedding security at every stage of development, from planning to production, DevSecOps ensures that vulnerabilities are identified and addressed early, reducing the likelihood of security breaches in production. Continuous security testing and automated monitoring allow organizations to detect and respond to threats in real time.
- Faster Time to Market: DevSecOps enables development teams to continue delivering software at high speed while ensuring security. By automating security testing and integrating it into CI/CD pipelines, security issues are identified early and remediated quickly, preventing delays and enabling faster releases without sacrificing security.
- Reduced Risk of Breaches: With continuous security testing and monitoring, the risk of security breaches is significantly reduced. DevSecOps fosters a proactive security mindset, which helps teams to identify vulnerabilities before they can be exploited by attackers. This minimizes the potential damage caused by security incidents.
- Regulatory Compliance: DevSecOps integrates security and compliance requirements into the software development pipeline, ensuring that the application is compliant with regulatory standards throughout Kubernetes and Devops for Streamlined Operations lifecycle. Automated compliance checks ensure that security policies and regulations are continuously met without manual intervention.
- Cost-Effective: By shifting security left and automating security testing, organizations can reduce the cost associated with finding and fixing vulnerabilities in later stages of development or after deployment. Early detection of vulnerabilities reduces the need for expensive post-release fixes and minimizes the financial impact of security breaches.
- Tools: Checkmarx, Fortify, SonarQube
- These tools analyze source code for vulnerabilities and coding mistakes that may lead to security flaws.
- Tools: OWASP ZAP, Burp Suite
- DAST tools test running applications for vulnerabilities, including issues related to authentication, access control, and Understanding the Devops Periodic Table .
- Tools: Black Duck, WhiteSource
- These tools help to identify vulnerabilities in open-source libraries and third-party dependencies, which are often an attack vector.
- Tools: Terraform, Ansible, Chef, Puppet
- IaC tools ensure that infrastructure is defined, deployed, and secured automatically, with configuration files under version control.
- Tools: Aqua Security, Twistlock, Sysdig
- Container security tools monitor and secure containerized environments, ensuring that containers are configured and deployed securely.
- Tools: Splunk, ELK Stack, Datadog
- These tools provide real-time monitoring, logging, and analysis to detect security incidents and vulnerabilities in production environments.
- Train Teams on Secure Coding Practices: Developers need to be trained in secure coding techniques and familiar with common security vulnerabilities (e.g., SQL injection, XSS). Security training should be an ongoing process and integrated into daily development activities.
- Integrate Security into CI/CD Pipelines: Security tools should be integrated into the CI/CD pipeline to automate testing, scanning, and deployment. This ensures that security checks are conducted at every stage of the Understanding Python in Devops delivery process.
- Automate Security and Compliance Checks: Implement automation to continuously test for security vulnerabilities, compliance requirements, and configuration management across the pipeline. This ensures that security and compliance are continuously enforced without manual intervention.
- Collaborate Across Teams: Encourage collaboration between developers, security professionals, and operations teams to ensure that everyone is involved in maintaining a secure development process. Foster a culture of shared responsibility for security.
- Focus on Incident Response: Establish a well-defined incident response process, including automated alerting, immediate remediation, and post-incident reviews. This will help the organization react quickly to security incidents and continuously improve its security posture.
Advance your Devops career by joining this Devops Online Course now.
How DevSecOps Integrates Security into DevOps
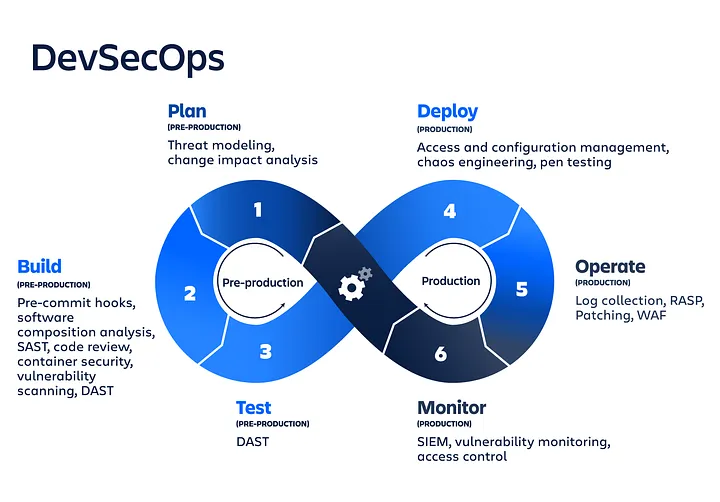
DevSecOps integrates security at every stage of the DevOps lifecycle, creating a security-driven culture while maintaining the speed and efficiency that DevOps aims for. Here’s how security is integrated throughout the stages of DevOps:
Planning and Design:
Security teams participate early in the planning and design phase to assess potential risks and define security requirements for the project. Security considerations are added to user stories, sprints, and backlogs. Devops Training includes threat modeling, risk analysis, and defining security objectives, which are embedded into the agile planning process. Security architects and developers collaborate to establish secure design principles.During the development phase, developers are trained to write secure code, leveraging secure coding guidelines and frameworks. Static application security testing (SAST) tools can be integrated into the Integrated Development Environment (IDE) to identify vulnerabilities in code as it is written. Security is embedded in code through features like encryption, access controls, input validation, and secure APIs.Security testing is automated and embedded into the continuous integration/continuous delivery (CI/CD) pipeline. Tools like dynamic application security testing (DAST) and software composition analysis (SCA) are used to identify vulnerabilities and insecure dependencies. Automated testing tools conduct security scans on every build to detect potential issues such as SQL injection, cross-site scripting (XSS), and other common vulnerabilities. Security checks continue into the deployment stage. Infrastructure as Code (IaC) tools like Terraform and Ansible are used to define and automate infrastructure securely. Continuous Delivery/Continuous Deployment (CD) pipelines ensure that security policies are applied before the deployment of applications to production environments. Automated security controls such as firewalls, intrusion detection systems, and encryption are configured in deployment pipelines. Once the application is live, continuous monitoring of the application and the infrastructure is essential to identify potential threats and vulnerabilities in real-time. Security Information and Event Management (SIEM) systems like Splunk and ELK Stack provide visibility into potential security incidents. Logging, intrusion detection systems (IDS), and security monitoring tools are integrated into the operational phase, enabling proactive threat detection. DevSecOps incorporates automated alerting and incident response capabilities, enabling teams to detect security issues quickly and take immediate action. Automated response mechanisms can be integrated with security monitoring tools to mitigate threats before they escalate. In the event of a breach, the response process is streamlined to reduce the impact and recovery time.
Benefits of DevSecOps
Ready to excel in Cloud Computing? Enroll in ACTE’s Devops Master Program Training Course and begin your journey today!
DevSecOps Tools and Technologies
DevSecOps relies on a range of tools and technologies to integrate security across the DevOps pipeline. Some popular tools include:
Static Application Security Testing (SAST):
Dynamic Application Security Testing (DAST):
Software Composition Analysis (SCA):
Infrastructure as Code (IaC):
Container Security:
Are you getting ready for your Devops interview? Check out our blog on Devops Interview Questions and Answers!
Continuous Monitoring and SIEM:
Implementing DevSecOps in an Organization
By integrating security into the DevOps pipeline with DevSecOps practices, organizations can accelerate software development while ensuring that their systems are secure, compliant, and resilient against threats.
Conclusion
Implementing DevSecOps is crucial for modern organizations aiming to balance security, speed, and agility in software development. By integrating security into the DevOps pipeline, teams can identify, address, and remediate vulnerabilities early, reducing risks and enhancing overall security posture. Devops Training of security testing, continuous monitoring, and collaboration among teams ensures that security is a shared responsibility rather than an isolated function. As cyber threats continue to evolve, adopting DevSecOps not only improves compliance and risk management but also ensures the development of resilient, high-quality software that can withstand security challenges in today’s digital landscape.





