
- Introduction to AWS GuardDuty
- How GuardDuty Works
- How GuardDuty Detects Threats
- Key Features and Benefits
- Threat Detection and Use Cases
- Integration with Other AWS Security Service
- Managing GuardDuty Findings
- Cost and Pricing Considerations
- Best Practices for Using AWS GuardDuty
- Conclusion
Introduction to AWS GuardDuty
AWS GuardDuty is a threat detection service offered by Amazon Web Services (AWS) designed to continuously monitor and analyze your AWS environment for malicious activities, unauthorized behavior, and security threats. With the increasing complexity of cloud environments and the growing sophistication of cyber-attacks, organizations need robust tools to ensure that their infrastructure remains secure. Amazon Web Service Training covers how AWS GuardDuty provides an intelligent, scalable, and cost-effective way to detect security threats in real time and protect AWS resources from a variety of potential threats. GuardDuty uses machine learning, anomaly detection, and integrated threat intelligence to identify potential security issues. This fully managed service requires minimal configuration and provides actionable security findings that are easy to interpret and act upon. It helps organizations detect unauthorized activity across their AWS accounts and workloads without the need for complex setup or management. With GuardDuty, AWS users can safeguard their environments against both known and unknown threats, making it an essential part of any cloud security strategy.
Want to Explore AWS in Depth, Check Out Our Comprehensive AWS Course To Gain Insights From Our Experts!
How GuardDuty Works
AWS GuardDuty continuously monitors your AWS environment by analyzing AWS CloudTrail event logs, Amazon VPC Flow Logs, and DNS logs to identify suspicious or anomalous behavior. It collects data from these sources, applies machine learning models, and uses known threat intelligence to evaluate the behavior and identify potential threats. When a potential threat is detected, GuardDuty generates a security finding, which includes details such as the type of threat, affected resources, and the severity of the issue. The findings are then made available through the AWS Management Console, CloudWatch Events, or via AWS Security Hub. AWS GuardDuty also provides detailed remediation recommendations to help you mitigate identified threats. It seamlessly integrates with other AWS security services, such as AWS Security Hub and AWS Lambda, to automate response actions. GuardDuty’s continuous monitoring ensures that new and evolving threats are detected in real-time.
Key Components of GuardDuty
Data Sources: GuardDuty primarily analyzes the following data sources:
- AWS CloudTrail Logs: Docker Pull can be used alongside AWS services, as it records API calls made within your AWS environment, including activities like creating or deleting resources, accessing services, and modifying settings. GuardDuty uses these logs to detect unauthorized activity, such as the use of compromised credentials.
- VPC Flow Logs: Captures IP traffic information that flows to and from network interfaces in your Amazon Virtual Private Cloud (VPC). GuardDuty uses flow logs to detect anomalies in traffic patterns, such as unusual data transfers or connections to suspicious IP addresses.
- DNS Logs: GuardDuty monitors DNS queries to identify potentially malicious or unauthorized domains that may indicate phishing attempts, C2 (command-and-control) server communications, or attempts to connect to known malicious resources.
- Threat Intelligence: GuardDuty integrates threat intelligence feeds from various reputable sources, including AWS and third-party providers. These feeds contain known malicious IP addresses, domains, and other indicators of compromise (IOCs). By integrating this threat intelligence, GuardDuty can quickly identify threats that have been previously identified and cataloged.
- Machine Learning and Anomaly Detection: In addition to threat intelligence feeds, GuardDuty leverages machine learning algorithms to detect anomalies in your environment. These models analyze historical behavior within your AWS environment and flag any deviations from normal activity as potential threats.
How GuardDuty Detects Threats
GuardDuty leverages anomaly detection models to identify unusual behavior, such as abnormal network traffic or unauthorized access attempts. It also integrates with known threat intelligence sources, including AWS’s own threat data and third-party feeds, to detect well-known malicious actors and indicators of compromise. The service provides real-time alerts and security findings to help you quickly identify and respond to potential threats. GuardDuty’s machine learning models are continuously updated to improve accuracy and reduce false positives. By analyzing vast amounts of data, GuardDuty ensures proactive security monitoring, helping you maintain a secure AWS environment, while also integrating with AWS Global Accelerator to optimize the performance and availability of your applications.
- Suspicious API activity: GuardDuty may flag an unusual API request or a rapid series of requests that deviate from typical patterns, such as a sudden increase in API calls or an unexpected service being accessed.
- Compromised instances: If GuardDuty detects that an instance is trying to communicate with known malicious IP addresses or making unusual outbound network connections, it can flag that instance as potentially compromised.
- Malicious domain activity: If GuardDuty identifies that an instance is trying to resolve DNS queries to known malicious domains, it can generate a finding indicating that the instance might be communicating with a command-and-control server.
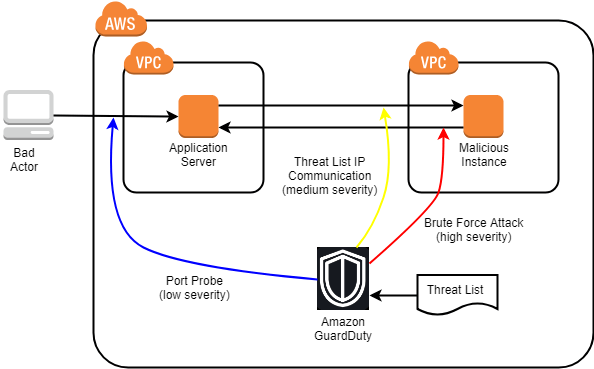
These findings provide detailed context, such as the type of threat, the source of the suspicious activity, and the specific AWS services involved. Each finding is categorized by severity, allowing security teams to prioritize their response based on the potential impact. GuardDuty also includes actionable recommendations for remediation, helping users mitigate the risk swiftly. Findings are displayed in the AWS Management Console and can be integrated with other services like CloudWatch or Security Hub for better visibility. This structured approach enables security teams to respond quickly, reducing the window of exposure to threats.
Interested in Obtaining Your AWS Certificate? View The AWS Course Offered By ACTE Right Now!
Key Features and Benefits
- Fully Managed and Automated: AWS GuardDuty is fully managed, meaning it doesn’t require users to configure or maintain any infrastructure for threat detection. It automatically ingests and analyzes data from multiple AWS services such as CloudTrail, VPC Flow Logs, and DNS logs. Since GuardDuty operates as a fully managed service, it automatically scales to accommodate the growing volume of security data without requiring manual intervention. This reduces the operational overhead of setting up and maintaining threat detection systems.
- Continuous Monitoring and Real-Time Threat Detection: GuardDuty operates 24/7, continuously analyzing AWS data streams for signs of security threats. The service alerts you in real-time to any suspicious or malicious activity detected in your environment, allowing you to act quickly and mitigate risks before they escalate. Unlike periodic security scans, GuardDuty’s constant vigilance ensures that potential threats are detected promptly.
- Easy Integration with AWS Ecosystem: GuardDuty integrates seamlessly with other AWS security services like AWS Security Hub, AWS Lambda, AWS CloudWatch Events, and AWS Identity and Access Management (IAM), while also allowing you to manage containerized workflows using Docker Push for deploying images to registries. For example, security findings from GuardDuty can be sent to AWS Security Hub for centralized management of security alerts. This integration simplifies the process of automating incident response and incorporating GuardDuty findings into an existing security workflow.
- Machine Learning-Driven Detection: GuardDuty leverages machine learning models to identify patterns of normal activity within your AWS environment and flag anomalies as potential threats. These models are continually updated and trained based on new data and emerging threat intelligence, which ensures that GuardDuty remains effective at detecting new and evolving security threats.
- Actionable and Detailed Findings: GuardDuty provides highly detailed and actionable security findings, which include information such as the type of threat, affected resources, IP addresses involved, and the severity of the threat. This enables security teams to quickly understand the scope of an issue and take the appropriate remediation steps.
- Cost-Effective: GuardDuty offers a pay-as-you-go pricing model, meaning that customers only pay for the data processed by the service, and there are no upfront costs. This pricing structure makes GuardDuty an affordable solution for organizations of all sizes, from startups to large enterprises.
Threat Detection and Use Cases
AWS GuardDuty can detect a wide range of security threats across your AWS environment, including but not limited to, GuardDuty can identify suspicious API calls that may indicate a compromised account or malicious activity. For example, if an attacker gains access to an account and attempts to delete critical resources or modify configurations, GuardDuty can detect these changes and generate a finding. GuardDuty can detect when an EC2 instance is compromised and being used to perform malicious actions, such as connecting to known malicious IP addresses or engaging in unusual outbound traffic patterns, while also supporting GraphQL APIs for AWS AppSync to enable real-time data synchronization and management. By detecting these anomalies, GuardDuty helps prevent further exploitation of compromised instances. GuardDuty can identify if there is any unusual data exfiltration or large-scale data transfers from an EC2 instance, S3 bucket, or other resources. This can help prevent sensitive data from being leaked or stolen. GuardDuty can detect DNS queries that are attempting to resolve domains associated with known malicious activity, such as phishing, malware, or command-and-control servers. By identifying these attempts, GuardDuty can help prevent malware from communicating with external attackers.
Gain Your Master’s Certification in AWS by Enrolling in Our AWS Masters Course.
Integration with Other AWS Security Services
One of the key strengths of AWS GuardDuty is its ability to integrate with other AWS security services. By integrating GuardDuty with these services, you can enhance your overall security posture and streamline your response to threats.
- AWS Security Hub: Security Hub acts as a central hub for managing security findings across your AWS environment. GuardDuty findings can be automatically sent to Security Hub, where they are consolidated with findings from other AWS security services. This allows for easier monitoring and management of security issues across multiple services.
- AWS Lambda: GuardDuty findings can be used to trigger automated responses through AWS Lambda, while also integrating with tools like Azure Sandbox for testing and experimenting with cloud environments securely. For example, you could set up a Lambda function to automatically isolate a compromised EC2 instance or revoke suspicious IAM credentials when GuardDuty generates a finding.
- AWS CloudWatch Events: GuardDuty integrates with CloudWatch Events to allow for the creation of custom workflows and automated responses based on security findings. For instance, you could configure CloudWatch Events to send notifications or trigger remediation actions when certain high-severity threats are detected.
- The affected resource (e.g., an EC2 instance or S3 bucket)
- The type of threat (e.g., API call anomaly, compromised instance, or malicious domain)
- A description of the event
- A recommendation for remediation
- S3 Data Events: The volume of S3 data events monitored by GuardDuty to detect suspicious access or potential misuse of your Amazon S3 buckets.
- EC2 Instance Metadata: The number of EC2 instance metadata requests processed by GuardDuty to identify potential misuse or unauthorized access can also be monitored in conjunction with Docker Port Mapping to manage and secure containerized applications.
- IAM Activity: The number of Identity and Access Management (IAM) activities analyzed by GuardDuty to detect unusual or risky user permissions or behavior.
- Network Traffic: The volume of network traffic analyzed, including connections between resources in your VPC, to identify unusual patterns that may indicate a threat.
- Threat Intelligence Feed: The number of threat intelligence data sources integrated, helping GuardDuty identify known malicious IP addresses, domains, or indicators of compromise.
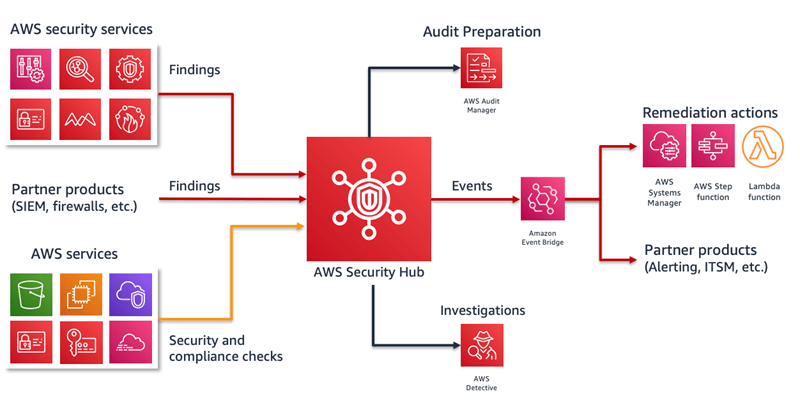
Managing GuardDuty Findings
GuardDuty findings can be accessed through the AWS Management Console, and they are categorized by severity Low, Medium, and High. Each finding provides detailed information about the potential threat, the affected resources, the type of threat detected, and recommended remediation steps, all of which are covered in AWS Training to help users effectively manage security incidents. Findings also include relevant context, such as the source IP address, affected region, and the specific event that triggered the alert. You can use this detailed information to prioritize response actions based on the severity level. GuardDuty allows you to configure custom actions for specific findings, enabling automated workflows to address security issues efficiently. These insights help security teams to make informed decisions and respond quickly to mitigate potential risks. including:
Security teams can use these findings to investigate and respond to potential threats. You can also integrate GuardDuty with third-party SIEM (Security Information and Event Management) solutions to centralize your security monitoring. Additionally, GuardDuty findings can be used to trigger automated response actions using AWS Lambda or AWS Systems Manager. This helps reduce response times and ensures swift mitigation of threats. Security teams can configure GuardDuty to send alerts via Amazon CloudWatch, allowing for seamless monitoring and incident response. The integration with AWS Security Hub enables a unified view of security across your AWS environment. By continuously analyzing data from multiple sources, GuardDuty helps maintain a proactive security posture and minimizes the risk of security breaches.
Cost and Pricing Considerations
AWS GuardDuty uses a pay-as-you-go pricing model based on the volume of data processed. Pricing is divided into two categories:
Are You Preparing for AWS Jobs? Check Out ACTE’s AWS Interview Questions & Answer to Boost Your Preparation!
Best Practices for Using AWS GuardDuty
To effectively manage security across your AWS environment, enable GuardDuty across all AWS accounts, including those within AWS Organizations, providing a unified view of threats. Integrate GuardDuty with AWS Security Hub to aggregate findings from multiple AWS security services, making it easier to monitor and respond to potential threats. Set up automated responses using AWS Lambda and CloudWatch Events to trigger remediation actions based on GuardDuty findings, minimizing response time. Regularly review GuardDuty findings, prioritize high-severity issues, and use them to guide your security efforts. Additionally, monitor your GuardDuty billing and usage to optimize costs and avoid unnecessary charges, ensuring an efficient and cost-effective security strategy, as emphasized in AWS Training. To further enhance your security posture, ensure that GuardDuty is configured to continuously monitor new and evolving resources within your environment. Regularly update your threat intelligence feeds to keep GuardDuty’s detection capabilities current with emerging threats. Establish clear workflows and assign responsibilities to security teams for investigating and addressing findings promptly. Utilize GuardDuty’s integration with Amazon CloudWatch to set up custom metrics and alarms, enabling proactive detection of anomalies.
Conclusion
AWS GuardDuty provides a robust, fully managed solution for detecting and responding to security threats in your AWS environment. With its integration of machine learning, threat intelligence, and real-time monitoring, GuardDuty enables organizations to identify and mitigate threats quickly and efficiently. By leveraging GuardDuty alongside other AWS security services, organizations can build a strong, scalable security posture that adapts to the evolving threat landscape. Whether you’re looking to protect a small workload or a complex multi-account AWS infrastructure, GuardDuty offers the tools and capabilities to keep your AWS environment secure.





