
- Introduction to Azure SSO
- Configuring Azure AD for SSO
- Integrating SSO with Third-Party Applications
- Security and Compliance Considerations
- Monitoring and Managing SSO Access
- Troubleshooting Azure SSO Issues
- Conclusion
The blog “Azure SSO to Secure and Scalable Authentication” explores how implementing Azure Single Sign-On (SSO) enhances security and scalability for organizations, a concept that is further elaborated in Microsoft Azure Training to help professionals understand and implement secure authentication solutions in the cloud. It highlights the benefits of simplifying user access across multiple applications while ensuring robust security measures like multi-factor authentication. The blog also delves into the seamless integration of Azure SSO with various enterprise systems, offering a unified, scalable solution for secure authentication across diverse platforms and devices.
To Explore Azure in Depth, Check Out Our Comprehensive Azure Training To Gain Insights From Our Experts!
Introduction to Azure SSO
Azure Single Sign-On (SSO) is a cloud-based identity and access management solution that enables users to securely access multiple applications with a single set of credentials. Azure SSO simplifies the user experience by allowing them to log in once to Azure Active Directory (AD) and seamlessly access a range of cloud and on-premises applications without needing to remember multiple usernames and passwords. Azure SSO supports various authentication protocols such as SAML, OAuth, and OpenID Connect, making it highly adaptable to different environments, and can be seamlessly integrated with Azure DNS Management to ensure secure and reliable domain name resolution for authentication processes. By integrating with Azure AD, Azure SSO provides robust security features, such as multi-factor authentication (MFA) and conditional access, which further enhance the security of user logins. This solution helps organizations reduce the risk of password fatigue, improve productivity, and ensure centralized access management across their entire application ecosystem.
Configuring Azure AD for SSO
Setting up Azure Active Directory (Azure AD) for SSO involves several steps to ensure seamless authentication for users and secure access to applications. Before configuring SSO, an organization needs to set up an Azure AD tenant. This involves creating an Azure AD instance within your Azure portal, which will serve as the central repository for user identities and authentication policies. To enable SSO for an application, it needs to be registered in Azure AD. Navigate to the Azure portal, select Azure Active Directory, and choose Enterprise Applications. Here, you can add either a Pre-integrated Application or Custom Application. For each application, Azure AD allows you to configure different SSO methods, including SAML-based SSO, OAuth/OIDC, or Password-based SSO. The configuration method will depend on the supported authentication protocol of the target application, with recommendations and best practices available through Azure Advisor to optimize the authentication setup and ensure a secure and efficient configuration. After selecting the SSO method, you’ll need to configure the settings for authentication. For SAML-based SSO, this will involve entering details like SAML Sign-on URL, Issuer, and Certificate. For OAuth or OpenID Connect, you’ll configure details like client ID and client secret.
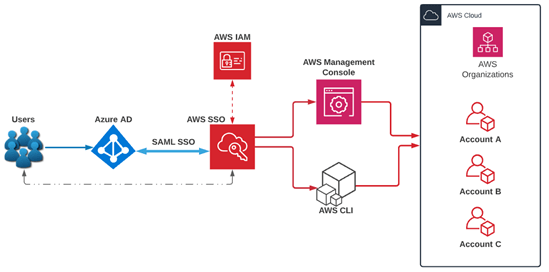
Once the application is configured for SSO, assign the appropriate users and groups to ensure that only authorized individuals can access the application. This can be done by navigating to Users and Groups within the Azure AD settings for the app. Before deploying the SSO configuration to production, conduct thorough testing to ensure users can authenticate successfully and seamlessly access the application. After successful testing, make sure to monitor the application’s sign-ins and access logs to ensure everything is functioning as expected. You can use Azure AD’s built-in monitoring tools to track user activities and identify any unusual patterns. Set up alerts for any sign-in failures or anomalies to stay ahead of potential issues. If needed, update the configuration based on feedback and testing results. Finally, maintain an ongoing review of your SSO setup, especially when new applications are added or existing ones undergo updates, to ensure that security policies remain consistent and effective.
Interested in Obtaining Your Azure Certificate? View The Azure Training Offered By ACTE Right Now!
Integrating SSO with Third-Party Applications
Integrating SSO with third-party applications can streamline access management and enhance security. Many third-party applications (cloud-based or on-premises) support SSO integration via popular protocols such as SAML, OAuth, or OpenID Connect. Here’s how to integrate Azure AD SSO with third-party applications:
- Select the Application in Azure AD:Navigate to the Azure AD portal and select Enterprise Applications. From there, you can search for the third-party application you want to integrate. If the application is pre-integrated with Azure AD, you can configure SSO directly by selecting it from the list.
- Use SAML or OAuth for Authentication:For SSO, the integration will often use SAML 2.0 or OAuth 2.0 protocols. If using SAML, you’ll configure the relevant parameters such as Issuer, SAML Assertion Consumer Service (ACS) URL, and Sign-on URL. For OAuth/OIDC, you’ll set up client ID and client secret details.
- Configure Third-Party Application:In the third-party application’s settings, you’ll typically need to provide the SAML endpoint or OAuth callback URL from Azure AD, while also considering MAC Addresses Functions, Risks, and Operation to ensure that device-level security is not compromised during the authentication process. This ensures that the application can communicate securely with Azure AD for authentication.
- Test and Verify Integration: After configuring the application, perform testing to confirm that users can log in using their Azure AD credentials and gain access to the third-party application without additional authentication prompts.
- Ongoing Management: Continuously monitor user access and update SSO settings when necessary, especially when third-party applications update their integration requirements.
- Sign-in Logs:Use Azure AD Sign-in Logs to monitor and review SSO access activity. These logs provide detailed information about user sign-ins, including the success or failure of authentication attempts, the source IP address, and any errors encountered.
- Azure AD Insights:Azure AD offers insights into user activity, sign-ins, and security risks. You can use Azure AD Identity Protection to detect and respond to potentially risky sign-ins, such as those originating from unusual locations or devices.
- Access Reviews:Regularly perform access reviews in Azure AD to ensure that users still require access to applications and that permissions are up to date, which can be streamlined with insights from the Guide to GitLab Features & Setup for Development to maintain secure and efficient development workflows. Automated reviews can be set up to streamline this process.
- Alerts and Notifications:Set up alerts to notify administrators of suspicious sign-in attempts or unauthorized access. These alerts can help identify security incidents early and ensure a rapid response.
- Integration with SIEM Tools:For more advanced monitoring and analysis, integrate Azure AD with Security Information and Event Management (SIEM) tools such as Azure Sentinel. This allows you to correlate SSO events with other security data for more comprehensive threat detection.
- Despite its reliability, SSO issues can occasionally arise, typically during configuration or integration.
- Ensure that the user has the correct Azure AD credentials and is part of the appropriate group with access to the application.
- Check if the account is disabled or locked in Azure AD. Double-check the SSO configuration in Azure AD, including the SAML settings or OAuth tokens.
- A mismatch in configuration between Azure AD and the target application can prevent successful sign-ins.
- Review the Sign-in Logs in Azure AD to identify the root cause of any errors. Logs will often provide error codes and messages that can guide troubleshooting.
- Ensure that there is no network issue preventing Azure AD from communicating with the application. Check if there are any firewall or proxy settings that may be blocking the SSO flow, and consider leveraging Docker Containers on AWS to isolate and manage network settings for secure, scalable application deployments.
- Sometimes, browser cache and cookies can cause SSO issues. Clearing them and trying the login process again can resolve minor authentication problems.
- Check the permissions assigned to the user and ensure they have the correct role or access level for the application. Misconfigured permissions can result in denied access.
- Ensure that the domain settings for both Azure AD and the target application are properly configured. Incorrect domain or DNS settings can cause authentication failures or prevent the SSO flow from completing.
- Double-check that the application is properly registered in Azure AD, with the correct redirect URI and other necessary configurations. Missing or incorrect configurations in the app registration can block the SSO process.
- Try using different user accounts to identify if the issue is user-specific or a broader problem with the SSO configuration. This can help determine if the issue is related to a particular user’s permissions or a general configuration error.
Security and Compliance Considerations
When implementing Azure SSO, security and compliance considerations are essential to ensure that users and data remain secure. Use MFA as an additional layer of security for users accessing critical applications. Enforcing MFA can help protect against unauthorized access, even if a user’s credentials are compromised.Implement Conditional Access policies in Azure AD to enforce rules based on the user’s location, device compliance, or risk level. For example, you can require users to authenticate via MFA if they are logging in from an untrusted location or device, a critical security measure often covered in Microsoft Azure Training to help professionals understand how to implement multi-factor authentication in cloud environments. Enable auditing and logging features in Azure AD to track and monitor SSO sign-ins. These logs can help detect suspicious activities or potential security breaches in real time.Regularly conduct access reviews to ensure that only the appropriate users and groups have access to critical applications. Azure AD provides a feature that automates access reviews for users and groups.

Ensure that your SSO solution complies with industry-specific regulations such as GDPR, HIPAA, and SOC 2. Azure AD offers compliance certifications to help you meet regulatory requirements and best practices. To further strengthen security, consider implementing role-based access control (RBAC) to assign permissions based on a user’s role within the organization. This minimizes the risk of unauthorized access by limiting user privileges to only what is necessary. Leverage Azure Identity Protection to detect and respond to risky sign-ins, such as those originating from unfamiliar locations or devices. Regularly update and patch your applications and systems to address any vulnerabilities that could be exploited by attackers. Use security alerts and automated workflows to respond promptly to security incidents and prevent potential breaches. Lastly, implement a strong password policy and enforce its use across all user accounts to further protect sensitive data.
Are You Considering Pursuing a Cloud Computing Master’s Degree? Enroll For Cloud Computing Masters Course Today!
Monitoring and Managing SSO Access
To maintain optimal security and performance for your SSO solution, monitoring and managing access is crucial. Here’s how to do so:
Troubleshooting Azure SSO Issues
Want to Learn About Azure? Explore Our Azure Interview Questions And Answers Featuring the Most Frequently Asked Questions in Job Interviews.
Conclusion
Azure Single Sign-On (SSO) offers a streamlined and secure way for users to access multiple applications using a single set of credentials. By integrating Azure AD, organizations can simplify user authentication while improving security through features such as multi-factor authentication and conditional access. Proper configuration, integration with third-party applications, and continuous monitoring are key to ensuring a seamless and secure SSO experience. While troubleshooting SSO issues can sometimes be challenging, Azure AD provides robust tools to identify and resolve common issues quickly, a topic that is often covered in Microsoft Azure Training to help professionals understand and manage identity and access management in cloud environments. Implementing best practices for security, compliance, and access management ensures that your SSO solution remains secure, efficient, and reliable. Azure SSO not only enhances user productivity but also enables organizations to scale securely in the cloud. By leveraging these features and tools, businesses can optimize their identity and access management processes for the long term.





