
- Introduction to Podman and Docker
- Podman: What is it?
- Podman’s operation
- Docker Installation on Ubuntu
- Docker: What is it?
- Docker’s Operation
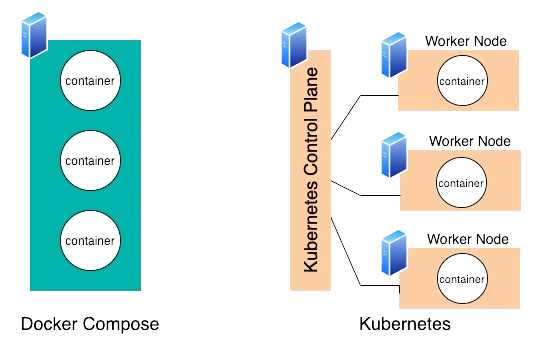
- Disparities Between Podman and Docker
- Conclusion
Introduction to Podman and Docker
Two of the most widely used containerization technologies, Podman and Docker, each provide unique methods for handling containers and images. Docker is well-known for its client-server architecture, extensive ecosystem, and ease of use, making it ideal for large-scale production environments. With built-in orchestration support and seamless integration with Docker Compose and Docker Swarm, Docker Training remains a dominant choice for developers. Conversely, Podman prioritizes security and adaptability, functioning in a daemonless rootless setup that reduces the need for privileged access. Unlike Docker, Podman does not require a background service, enhancing security by mitigating potential daemon-related vulnerabilities. Podman offers a more secure, modular approach, but Docker leads in terms of usability, tooling support, and widespread adoption.By understanding the key features and differences of both technologies, you can make an informed decision and choose the best tool for your containerization needs, whether it’s security-focused development with Podman or effortless container management with Docker.
Podman: What is it?
With the help of the open-source containerization application Podman, users can efficiently manage containers and container images. Podman is more secure and resource-efficient than Docker because it does not require a persistent background service to run, as it operates without a centralized daemon. This architecture eliminates a single point of failure and enhances system stability. Azure Active Directory of its complete compatibility with Docker commands, Docker users can easily switch between the two tools or use them interchangeably without modifying their workflows. Podman’s architecture supports both local and cloud-based systems, enabling containers to be managed as separate processes, which improves security and performance. Additionally, its rootless container support allows containers to run without requiring elevated privileges, further reducing security risks. Podman’s modular design makes it highly adaptable to different container management needs, whether for microservices, Kubernetes integration, or enterprise-scale deployments. It is a powerful tool for developers and DevOps teams looking for a flexible and efficient containerization solution.
Unlock your potential in Docker with this Docker Training Course.
Podman’s Operation
The following highlights the main features of Podman’s architecture and how it differs from other containerization solutions like Docker:
-
Daemoness Architecture:
- Podman functions without a persistent background process, in contrast to Docker
- Which manages containers via a centralized daemon.
- With Podman, every container functions as a separate process, providing a more secure and decentralized method of container administration.
-
Enhanced Security:
- Podman does not require a background process that needs elevated privileges (root access) because it does not have a persistent daemon.
- By eliminating a possible avenue for privilege escalation or Enhancing Data Security With AWS Macie, this approach lowers the attack surface and increases Podman’s security for developers and system administrators. Greater Flexibility:
- Podman enables users to communicate directly with containers without the need for a centralized daemon.
- There is greater freedom in handling containers since they can be independently managed without depending on a central provider.
- Podman’s usability in safe contexts is further improved by the fact that non-root users can run it. Local Execution and Image Building:
- Podman provides a flexible toolkit for development and system administration by supporting both local container execution and container image generation.
- Workflows are made simpler for developers by the ability to construct, execute, and maintain containers without the need for an extra tool or service.
- With Podman’s direct integration with Kubernetes, customers can easily manage containers in orchestration settings.
- Because of this integration, Podman is a useful tool for production-grade and cloud-native deployments, where Kubernetes orchestration is frequently essential. Lightweight and Resource-Efficient:
- Because Podman doesn’t require a persistent daemon process, its design is lighter than Docker’s.
- Because of this, Podman can function with fewer system resources, which makes it appropriate for settings that need little overhead or have limited computational power. Improved Container Lifecycle Management:
- Because users may start, stop, and manage containers without depending on a live service, Podman streamlines container lifecycle management.
- The effectiveness of container AWS Management Console is improved by this autonomous process paradigm. Rootless Containerization:
- Rootless container management, made possible by Podman, improves security and eliminates the need for intricate permission configurations by enabling non-root users to execute containers without needing elevated capabilities. Compatibility with Docker:
- Because Podman is Docker-compatible, developers who are already familiar with Docker can switch to Podman with little difficulty.
- Its compatibility with the same command-line interface (CLI) syntax and ability to use Docker-formatted images make it simple to include into current workflows. Versatility in Use Cases:
- Podman is a flexible solution for a variety of use cases from development to production because it can manage both local container operations and image generation in addition to orchestration support.
- Docker Training Works well in settings like edge computing or cloud-native apps where safe and lightweight containers are crucial.
Advance your Docker career by joining this Docker Training Course now.
Seamless Kubernetes Integration:Docker: What is it?
Docker employs a client-server architecture to manage containers and images, where the client interacts with a centralized daemon running as a background service. Since the daemon requires elevated privileges, security concerns may arise, making proper access control essential. However, Docker ensures consistency across environments by enabling developers to create, package, and execute applications within isolated containers, eliminating dependency conflicts. Docker’s rich ecosystem includes Docker Hub, a vast repository for pre-built images, and Docker Compose, which simplifies the orchestration of multiple containers. Additionally, Docker supports efficient container management, image versioning, and automated workflows for Docker in Linux Software Development . Its lightweight design enhances resource efficiency and portability, making it an ideal choice for modern development workflows. For large-scale deployment and container scaling in production environments, Docker Swarm provides built-in orchestration, load balancing, and high availability features. With Docker, organizations can streamline development, optimize infrastructure, and enhance deployment efficiency in cloud and on-premise environments.
Take charge of your Cloud Computing career by enrolling in ACTE’s Cloud Computing Master Program Training Course today!
Docker’s Operation
The following highlights Docker’s daemon architecture and its function in container lifecycle management:
-
Docker Daemon (Docker Engine):
- The main component that manages the lifespan of containers, images, networks, and volumes while operating in the background is the Docker daemon.
- It controls the creation, launching, pausing, and monitoring of containers while listening for commands from the Docker client. Client-Server Interaction:
- In order to carry out container activities, the Docker client (CLI) submits requests to the Docker daemon via a client-server architecture.
- It is versatile for distributed systems since the client can be local or remote, enabling users to communicate with the daemon via a network. Container Lifecycle Management:
- The entire container lifespan is managed by the Docker daemon. Pulling container images, building containers, executing them, and making sure they are terminated or destroyed when no longer required are among the duties it manages.
- In order to guarantee that containers operate at their best, it also controls container resources like CPU, memory, and storage. Handling Complex Workflows:
- Because of its ability to handle intricate operations, Docker’s daemon is ideally suited for large-scale production settings that require container management, scaling, and load balancing.
- It easily interfaces with orchestration systems like Kubernetes and Docker Swarm to automate networking, scaling, and container deployment across numerous computers. CLI Commands and Docker API:
- Simple commands (such as docker run, docker ps, and docker stop) can be used to communicate with the daemon through Docker’s command-line interface (CLI).
- Additionally, programmatic access to the daemon is made possible by the Master Docker Entrypoint, facilitating automation and integration with other services and tools. Security and Privileges:
- The Docker daemon usually runs with elevated privileges, frequently as the root user, because it must access system resources in order to manage containers.
- Accordingly, Docker’s security model needs to be carefully configured to reduce potential dangers, and using appropriate access restrictions is crucial to protecting the daemon from unwanted use.
These points describe how Docker’s daemon is a potent tool for container orchestration in production situations because it facilitates effective container management and supports intricate workflows.
Preparing for a job interview? Explore our blog onDocker Interview Questions and Answers!
Disparities Between Podman and Docker
- Daemonless vs. Daemon-Based: Because Podman is daemonless, it operates as a direct process, providing less overhead and improved security. Docker is more resource-intensive since it needs a running daemon to manage containers.
- Rootless Containers: By enabling rootless container management, Podman improves security by enabling containers to run without root access. In order to function, Docker typically needs root access.
- Compatibility: Similar command syntaxes are provided by Podman and Docker; however, Podman does not require a daemon, which can increase security and facilitate use in settings with more stringent security regulations.
- Ecosystem: With features like Docker Compose, Docker Swarm, and third-party service integrations, Docker boasts a more comprehensive ecosystem. Although it has not been accepted as much, Podman’s ecology is expanding.
Conclusion
Both Docker and Podman provide distinct benefits in container management. By eliminating the requirement for a central daemon and enabling users to operate containers without root capabilities, Podman’s daemonless and rootless architecture stands out, enhancing security. Docker Training Course makes it the perfect option for environments like multi-user systems where security is a top concern. Additionally, Podman seamlessly integrates with systemd, enabling better automation and container lifecycle management. However, because of its strong ecosystem, sophisticated tools, extensive documentation, and broad industry adoption, Docker continues to be the preferred choice for production environments. It offers seamless CI/CD integration, enterprise support, and a vast library of pre-built images on Docker Hub, making development and deployment more efficient. The choice between the two frequently comes down to particular considerations, like deployment scale, ecosystem integration, team expertise, and security requirements. Ultimately, both tools empower developers with efficient containerization solutions tailored to different use cases.





